9 Common Cyber Security Threats and 4 Defensive Measures
Cyber security threats are malicious acts designed to steal or destroy sensitive data, compromise computer systems or identities, disrupt or sabotage business operations, and in general, disrupt digital life. Common types of cyber threats include malware, ransomware, denial of service (DoS), and SQL injection attacks.
Another meaning of the term cyber threats refers to the potential for successful cyberattacks on organizations. This is also known as the attack surface. For example, any computing system that has a known security vulnerability is exposed to imminent cyber threats. To address threats and security weaknesses, both present and future, many organizations are adopting practices and technologies for advanced threat protection.
Cyber threats are performed by a variety of threat actors, both inside and outside an organization. Threat actors can include individual hackers, organized cybercrime groups, state sponsored hacks, hacktivists (who attack in the name of a social cause), and malicious insiders who abuse their privileges to access an organization’s computing systems.
9 Types of Cybersecurity Threats
1. Data Breach
A data breach occurs when protected data is accessed by threat actors that disclose or make any unauthorized use of this data. A data breach is typically the result of a successful cyberattack using some of the cybersecurity threats listed below. It can occur to organizations of all sizes, including small businesses and large enterprises.
Data breaches can put any type of information at risk, including personal health information (PHI), trade secrets, and personally identifiable information (PII). However, if the data breach results in a violation of industry standards or government regulations, the organization responsible for securing this information is held liable and may face litigation, fines, and reputation damages.
2. Zero-day Attack
Zero-day attacks exploit unknown flaws in software, firmware, or hardware. Since the parties affected by the flaw are unaware of it, they cannot patch or fix it. As a result, the threat actor is free to perform malicious actions as long as they remain undetected.
The term implies the first moment an attack against an unknown vulnerability is discovered, although threat actors could have been exploiting the vulnerability for some time. You can apply the term zero-day to a vulnerability, attack, or exploit kit. A zero-day vulnerability that has been made public is called a one-day or n-day vulnerability.
3. Malware
Malicious software (malware) is a program that performs malicious actions on a server, computer, or network. It is designed to spread by infecting networks and machines that come into contact with and perform a specific malicious action. For example, spyware can covertly listen in on communication while ransomware encrypts data to hold it hostage.
Malware presents itself differently to target users or endpoints according to the objective it is designed to achieve. It may cause relatively mild and benign issues or have a disastrous impact.
4. Ransomware
Ransomware is a type of malware that encrypts data and then displays a ransom note that demands payment in exchange for a decrypting key. The note usually comes with a threat to leak or destroy the data if the victim fails to pay the ransom. Typically, the decryption key is sometimes, but not always provided only after the victim pays the ransom.
The motive behind ransomware is to obtain monetary gains through extortion, and actors usually ask for payment in crypto coins like Bitcoin. Unlike other attacks, victims are usually notified by the actor that an exploit occurred, and if they pay the ransom they are given instructions on how to recover from the attack.
Threat actors can spread ransomware through various means. For example, they may add malicious attachments to phishing emails to trick users into downloading the ransomware or deliver it via malicious software applications, compromised websites, or infected external storage devices.
Ransomware attacks can have devastating consequences, making it critical to prepare for ransomware prevention and adopt ransomware protection technologies.
5. Denial of Service (DoS) Attack
DoS attacks flood servers, networks, or systems with traffic to overload bandwidth and resources. It prevents the system from processing and fulfilling legitimate requests. DoS attacks attempt to prevent the target from responding to service requests.
Distributed Denial-of-Service (DDoS) attacks are similar to DoS but employ several infected host machines. DDoS attacks aim to cause service denial and take the target completely offline. Actors often use DDoS to pave the way for another attack and breach the target environment.
6. SQL Injection
SQL injection (SQLi) is an attack vector threat actors employ to obtain unauthorized access to a web application database. It involves adding a string of malicious code to a database query, forcing the database to allow access to protected resources like sensitive data, intellectual property, administrative credentials, or customer data.
Threat actors can use SQL injection attacks to target applications using a SQL database, such as Oracle, SQL Server, and MySQL. The most common targets are websites.
7. Advanced Persistent Threat
An advanced persistent threat (APT) is an attack campaign that attempts to breach a network and establish a covert, long-term presence. The intruders, typically a team, stay in the network until they achieve their objective, usually mining highly sensitive data.
APT attacks carefully choose and research their target, usually governmental networks or large enterprises. Since APT attacks require many resources, they are usually backed by criminal syndicates looking to obtain massive profits or by governments as part of cyber warfare programs.
8. Supply Chain Attacks
A supply chain consists of all individuals, resources, organizations, technologies, and activities involved in creating and selling a product. It encompasses all components, including materials delivered from a supplier to a manufacturer and the final product’s delivery to end-users.
A supply chain attack targets the weaker links in an organization’s supply chain. Targeting the weak points in the supply chain increases the likelihood of a successful cyberattack. The threat actors achieve this by taking advantage of the established trust between the organization and its third-party partners and vendors.
Tips From Expert
In my experience, here are tips that can help you better adapt to protecting against modern cyber threats:
- Use Behavioral-Based Detection: Leveraging AI and machine learning to identify unusual behaviors can help detect new and unknown threats, such as zero-day attacks.
- Prioritize Patch Management: Quickly applying patches for known vulnerabilities is essential to minimize the attack surface and prevent exploitation by malicious actors.
- Layer Defense Strategies: Implementing a multi-layered approach to security, including firewalls, XDR, and endpoint security, provides a more robust defense against threats.
- Adopt Strong Data Encryption Practices: Encrypting data both at rest and in transit helps to prevent unauthorized access and data breaches.
- Regularly Back Up and Test Recovery: Implementing and frequently testing backups is crucial for ensuring a rapid recovery in the event of a ransomware attack or other data-loss event.
4 Ways to Protect Against Cybersecurity Attacks
Here are several important ways you can protect your organization about cyber threats.
Learn about additional ways to prevent cyber attacks in our guide to threat prevention
1. Create a Cybersecurity Awareness Training Program
Employees are the first line of defense against cyberattacks. They are constantly targeted by threat actors and can allow or prevent an attack. Employee training is critical to ensure the security of digital assets.
A cybersecurity awareness training program provides employees with the information needed to understand cyberattacks, the skills to identify attacks, and the instructions to follow when responding to suspicious activities. It helps promote a security-first culture that includes all types of employees, rather than just the security team.
2. Backup Your Data
A data backup strategy is critical to an overall security strategy and any disaster recovery and business continuity program. Data backups help protect the organization against data loss events, providing ways to restore deleted data and recover overwritten files.
You can use data backups to recover from ransomware attacks without paying the ransom and ensure business continuity during outages. You can set up many types of backup, depending on your business needs.
Here are several practices for your backup strategy:
- Define a process for backing up and recovering critical databases and any relevant line-of-business application.
- Create and enforce backup policies to govern the frequency of data backups, the number of required replicas, and the service-level agreements (SLAs) stipulating the required data restoration speed.
- Set up a full data backup at least once per week, ideally during non-business hours such as weekends and holidays.
- Supplement full backups with incremental or differential data backups to capture the changes since the latest full backup.
3. CVE Databases
Common Vulnerabilities and Exposures (CVEs) represent publicly available information about security vulnerabilities and exposures in specific systems. The CVE format is designed to provide standardized information about known vulnerabilities, and to allow organizations to easily update cybersecurity policies with the latest information about security issues.
CVEs generate standardized identifiers for specific vulnerabilities or exposures. CVE identifiers (names or numbers) allow security professionals to access specific cyberthreats from multiple sources of information using the same common name.
There are many CVE vulnerability databases available. Organizations can use a CVE database to establish criteria for evaluating the security risks. As part of the digital forensics process, security analysts can reference CVE vulnerability information, search for known attack signatures, and fix critical vulnerabilities.
4. Extended Detection and Response (XDR)
XDR solutions employ a proactive threat detection and response approach to holistically protect against unauthorized access, misuse, and various cyberattacks. It provides visibility across all data, including networks, cloud data, and endpoints, applying automation and analytics to address sophisticated threats.
XDR provides cybersecurity teams with capabilities to help proactively and quickly identify stealthy, sophisticated, and hidden threats. Teams can use XDR to track threats across various locations and sources within the organization and efficiently investigate threats. The automation functionality helps ensure operators strengthen security processes while improving their productivity.
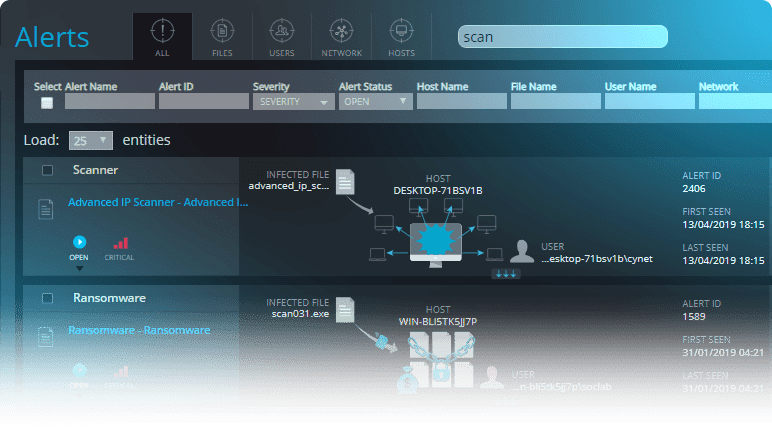
Advanced Threat Protection with Cynet
Cynet is a holistic security platform that provides advanced threat detection and prevention. The platform employs cutting-edge technologies to ensure advanced threats do not slip past your security perimeter. To achieve this goal, Cynet 360 correlates data from endpoints, network analytics and behavioral analytics, and presents findings with near-zero false positives.
Block exploit-like behavior
Cynet monitors endpoints memory to identify behavioral patterns that are readily exploited, such as unusual process handle requests. These behavioral patterns lead to the vast majority of exploits, whether new or known. Cynet is able to provide effective protection against Advanced Persistent Threat (APT) attacks and more, by identifying such patterns.
Block exploit-derived malware
Cynet employs multi-layered malware protection, including sandboxing, process behavior monitoring, and ML-based static analysis. Cynet also offers fuzzy hashing and threat intelligence. This makes sure that even if an advanced threat establishes a connection with the attacker, and downloads additional malware, Cynet will stop this malware from running, thus preventing any harm from occurring.
UBA
Cynet continuously monitors user behavior, generates a real-time behavioral baseline, and provides alerts when behavior deviation is identified. This deviation in behavior may indicate a compromised user account. Additionally, Cynet provides the ability to define user activity policies, triggering an alert in case of violation.
Deception
Cynet supports the use of decoy tokens—data files, passwords, network shares, RDP and others—planted on assets within the protected environment. APT actors are highly skilled and therefore might evade detection. Cynet’s decoys lure such attackers, prompting them to reach out and reveal their presence.
Uncover hidden threats
Cynet uses an adversary-centric methodology to pinpoint threats throughout the attack chain. Cynet thinks like an adversary, identifying indicators and behaviors across endpoints, users, files, and networks. They supply a holistic account of the attack process, regardless of where the attack may try to penetrate.
Accurate and precise
Cynet utilizes a powerful correlation engine and provides its attack findings free from excessive noise and with near-zero false positives. This makes the response for security teams easier so they can attend to pressing incidents.
Choose from manual or automatic remediation. This way, your security teams can have a highly effective yet straight-forward way to disrupt, detect, and respond to advanced threats before they have the chance to do damage.
Learn more about the Cynet cybersecurity platform.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response