Achieved 100% protection in 2024
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
Threat hunting is a method of actively searching for undiscovered network threats lurking in a network. Threat hunting goes deeper than other investigative techniques to find evasive malicious actors who have managed to bypass an organization’s defenses.
Once attackers have penetrated the network perimeter, they can quietly gather data, retrieve sensitive material, and obtain login credentials to move laterally across the environment. Attackers can operate secretly on a network for months.
Unfortunately, most organizations lack advanced threat protection capabilities to completely prevent advanced persistent threats (APTs). Attackers will inevitably penetrate your defenses, making threat hunting an essential part of any defense strategy.
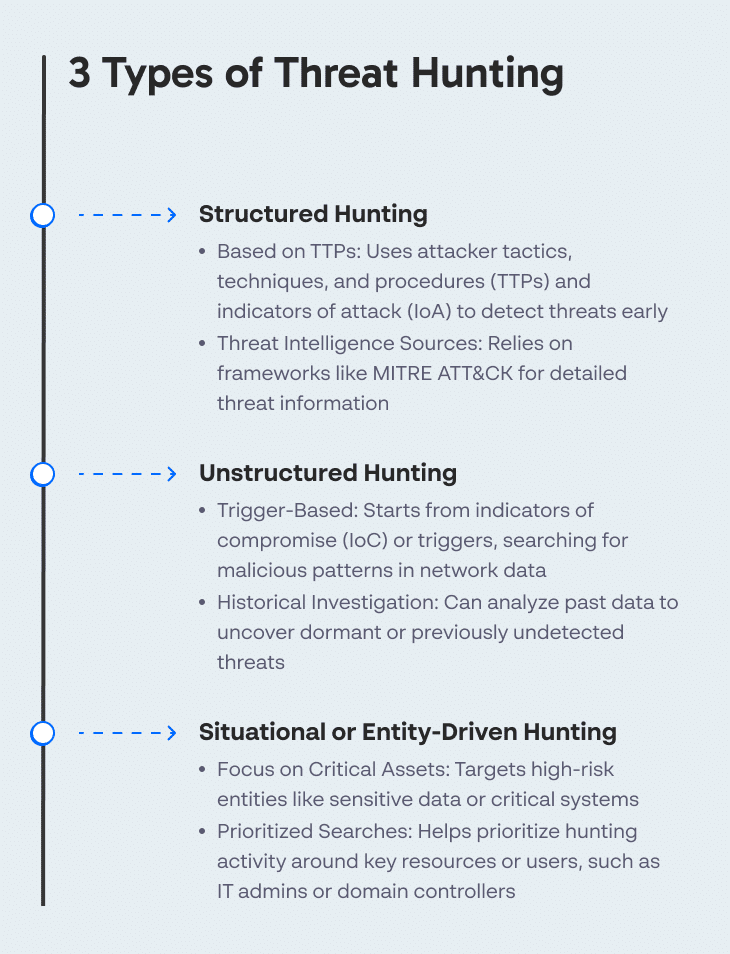
Threat hunters start with assumptions based on security data or triggers they receive from the environment. Based on these inputs, they further investigate potential risks. Let’s review a few possible styles of threat hunting investigations.
Structured threat hunting is based on indicators of attack (IoA) and the attacker’s tactics, techniques, and procedures (TTP). Threat hunts are coordinated based on the TTPs discovered on the network. Using TTPs, threat hunters can identify threat actors during early attack stages, before they do harm to the environment.
This type of threat hunting relies on threat intelligence sources such as the MITRE ATT&CK Framework, which provides detailed information about a wide variety of TTPs.
Unstructured threat hunting starts from a trigger or an indicator of compromise (IoC). The hunter searches the network for malicious patterns before and after the trigger or IoC. Threat hunters can investigate historical data as far as data retention limits permit. This type of threat hunting can discover new types of threats or threats that penetrated the environment in the past and are now dormant.
Situational or entity-driven threat hunting focuses on high-risk/high-value entities such as sensitive data or critical computing resources. Its main benefit is that it helps focus and prioritize threat hunting activity to improve its effectiveness.
Attackers commonly target specific high-value or high-risk assets or privileged users such as IT administrators, domain controllers, and development managers. Threat hunting helps identify these high-priority targets and conduct focused searches for relevant threats.
Related content: Read our guide to advanced threat detection
The following best practices can help you perform threat hunting more effectively.
To identify anomalies, hunters need to understand all aspects of their environment. This includes architecture, communication flows, and user rights. A threat hunter needs to identify high-value data that could be the focus of an attack. It is important that hunters understand business practices as well as employee and customer behavior.
The only way to identify an activity as abnormal is to know what is normal in the organization. It can be helpful to set standards or baselines of behavior. For example, if there are few customers using a specific product feature, but there is a lot of traffic to that feature, this could indicate an attack.
An important aspect of transparency is access to system data, usually in log format. Logs should be collected centrally for easy analysis and collection using modern security tools. Tools such as network filters, firewalls, and intrusion prevention and detection systems can all provide useful information.
To find attackers who have broken through security defenses, threat hunters need to understand the latest attack methods, tools, and processes. Relying on common knowledge or outdated threat information is not enough.
In the past, threat hunting could be as simple as recognizing a known malware hash or a simple indicator of compromise (IoC), but today these obvious threats are already being blocked by existing security solutions. Modern threat hunting must go beyond the obvious, such as discovering zero-day exploits, or attacks that cut across security silos, for example combining account compromise with injection attacks or network attacks.
Threat hunters do not need to replace the organization’s IT professionals or ongoing security teams. Security and IT experts can help them access and make effective use of cybersecurity tools and datasets. Threat hunters should have access to all the tools and processes already in use by the organization. They should also have access to all security datasets.
Threat hunting requires human creativity and intuition, but automated analytics capabilities can save manual work for threat hunters. Machine learning algorithms are currently inferior to humans in pattern recognition, but can process more data at a faster rate. Successful threat hunters combine human ingenuity with automated analysis.
User and Entity Behavior Analysis (UEBA) enables automated analysis of security data from SIEM, cloud systems, and security tools. UEBA solutions monitor the behavior of users, applications, and other entities on the network, analyzing their interactions with data and systems to identify anomalous behavior.
UEBA can complement signature-based and rule-based detection with behavioral analytics by examining the behavioral patterns of humans and machines. UEBA can more easily detect internal threats, targeted attacks, financial fraud, and other threats that do not match known attack patterns or malware signatures.
UEBA accelerates the threat hunter’s ability to identify suspicious and anomalous behavior and can also help threat hunters form hypotheses about the threat. Combined with threat Intelligence, UEBA can help threat hunters quickly initiate searches to see if anomalies on the network match up to known TTPs.
Tips From the Expert
In my experience, here are tips that can help you better adapt to effective threat hunting:
Cynet is a holistic security platform that provides advanced threat detection and prevention. The platform employs cutting-edge technologies to ensure advanced threats do not slip past your security perimeter. To achieve this goal, Cynet correlates data from endpoints, network analytics and behavioral analytics, and presents findings with near-zero false positives.
Block exploit-like behavior
Cynet monitors endpoints memory to identify behavioral patterns that are readily exploited, such as unusual process handle requests. These behavioral patterns lead to the vast majority of exploits, whether new or known. Cynet is able to provide effective protection against Advanced Persistent Threat (APT) attacks and more, by identifying such patterns.
Block exploit-derived malware
Cynet employs multi-layered malware protection, including sandboxing, process behavior monitoring, and ML-based static analysis. Cynet also offers fuzzy hashing and threat intelligence. This makes sure that even if an advanced threat establishes a connection with the attacker, and downloads additional malware, Cynet will stop this malware from running, thus preventing any harm from occurring.
User Behavior Rules
Cynet continuously monitors user behavior, generates a real-time behavioral baseline, and provides alerts when behavior deviation is identified. This deviation in behavior may indicate a compromised user account. Additionally, Cynet provides the ability to define user activity policies, triggering an alert in case of violation.
Deception
Cynet supports the use of decoy tokens—data files, passwords, network shares, RDP and others—planted on assets within the protected environment. APT actors are highly skilled and therefore might evade detection. Cynet’s decoys lure such attackers, prompting them to reach out and reveal their presence.
Uncover hidden threats
Cynet uses an adversary-centric methodology to pinpoint threats throughout the attack chain. Cynet thinks like an adversary, identifying indicators and behaviors across endpoints, users, files, and networks. They supply a holistic account of the attack process, regardless of where the attack may try to penetrate.
Accurate and precise
Cynet utilizes a powerful correlation engine and provides its attack findings free from excessive noise and with near-zero false positives. This makes the response for security teams easier so they can attend to pressing incidents.
Choose from manual or automatic remediation. This way, your security teams can have a highly effective yet straight-forward way to disrupt, detect, and respond to advanced threats before they have the chance to do damage.
Learn more about the Cynet cybersecurity platform.
Search results for: