What Is Cyber Threat Intelligence (CTI)?
Cyber threat intelligence (CTI) consists of information related to cyber threats and threat actors. It incorporates various sources to help identify and mitigate harmful events and potential attacks occurring in cyberspace.
CTI is commonly offered in the form of a threat intelligence platform or service, although some organizations have in-house CTI operations. CTI is a core part of advanced threat protection strategies that help organizations defend against sophisticated, organized cyber attacks.
CTI combines cyber intelligence sources into meaningful insights that can support security operations. Here are common cyber threat intelligence sources:
- Open source intelligence
- Human intelligence
- Social media intelligence
- Technical intelligence
- Forensically acquired data
- Device log files
- Intelligence from Internet traffic
- Data from the dark web and deep web
The Need for Cyber Threat Intelligence
Some threats can be automatically identified and mitigated using security tools. More severe or evasive threats are handled by human security and IT teams, who need to triage the threats, understand their modus of operation, and learn how to prevent them.
Both of these use cases are enabled by CTI:
- CTI provides data for cybersecurity tools to help them understand the threats that need attention and the tactics, techniques, and procedures (TTP) that can be used to mitigate them.
- CTI provides knowledge that can help security analysts and IT operations teams develop security plans and quickly act to protect networks from severe threats.
Investing in cyber threat intelligence gives businesses access to a threat database that contains technical information about a wide range of threats. Providing access to this knowledge by the security team or automated systems greatly improves the organization’s security posture. CTI is operational intelligence that provides analysts and security systems with actionable insights.
An effective CTI system makes a clear distinction between threat data collection and threat intelligence:
- Cyber threat data collection provides raw information, which is initially not useful until it is analyzed and packaged into a useful format for security investigation.
- Cyber threat intelligence builds on data collection and provides data that can be used to detect, block and mitigate threats. It leverages analysis to derive operational intelligence from raw security data—such as the types of threats that may be imminent, vulnerabilities in the network, identity of threat actors, and the root cause of each threat.
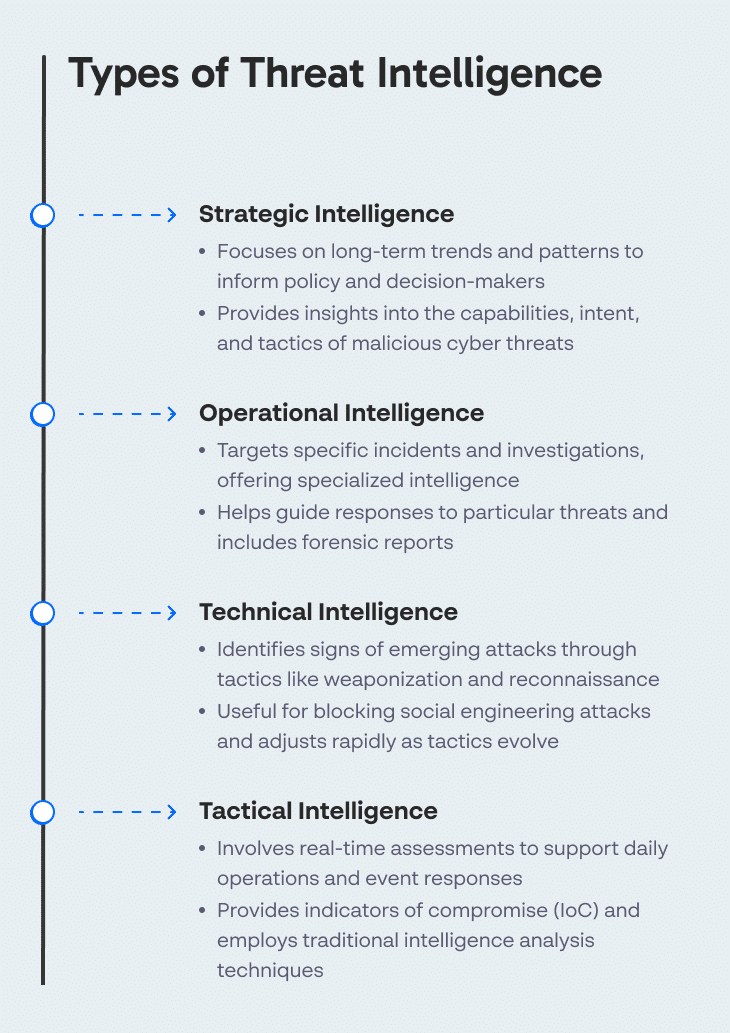
Types of Threat Intelligence
Cyber threat intelligence analysis involves studying actors and their intent, capability, motivations, access to targets, and their preferred tactics, techniques, and procedures (TTP). It helps make informed operational and tactical assessments.
Strategic Intelligence
Strategic intelligence involves assessing disparate information to create integrated views. The goal is to inform policy and decision-makers on long-term or broad issues and provide timely threat warnings. Strategic CTI provides a broad view of the capabilities and intent of malicious cyber threats, such as actors, TTP, and tools. This process involves identifying trends, emerging threats and risks, and patterns.
Operational Intelligence
Operational intelligence involves assessing potential incidents related to specific events, activities, and investigations. Operational CTI provides highly specialized intelligence to support and guide responses to specific incidents, supplied as forensic reports or other forms. This type of intelligence is typically related to campaigns, tools, and malware.
Technical Intelligence
Technical intelligence focuses primarily on identifying signs that indicate an emerging attack, such as weaponization, reconnaissance, and various delivery techniques like spear-phishing and baiting. It is particularly useful in blocking social engineering attacks. Technical intelligence may be grouped with operational threat intelligence. However, technical intelligence adjusts rapidly in cadence with actors as they update their tactics.
Tactical Intelligence
Tactical intelligence involves assessing real-time events, activities, and investigations to support daily operations and events. For example, tactical CTI can inform decision-makers on the development of indicators of compromise (IoC) and signatures. It typically employs traditional intelligence analysis techniques.
How Do Organizations Use a Cyber Threat Intelligence Framework?
Organizations implement a CTI framework to enhance the following capabilities.
Cyber Risk Management
IT and security teams use tactical threat intelligence to determine the security controls applied to an organization. The CTI data helps them prioritize the most relevant threats and understand how attackers might exploit system vulnerabilities. They also use operational threat intelligence to evaluate and adjust the controls.
Security Operations Center (SOC)
The SOC is usually responsible for processing cyber threat intelligence and adding threat context to the data sourced from monitoring tools and logs. SOC teams often use tools like SIEM to prioritize security data and help analyze large datasets. SOC operators leverage threat intelligence to identify suspicious activity and inform security teams of priority threats.
Vulnerability Management
Organizations typically have many vulnerabilities, making it difficult to identify and patch high-priority vulnerabilities. Vulnerability-specific threat intelligence helps vulnerability management teams determine the impact risk and likelihood of threats.
Incident Investigation and Response
Security analysts rely on CIT to investigate and respond to incidents. It allows them to hunt for threats proactively, anticipating the intent and techniques of attackers. Incident response teams can use threat intelligence to prepare for threats and practice response procedures before a real breach. The information is also useful for forensic investigation after a breach.
Security Compliance
CTI allows organizations to better comply with data security regulations like the GDPR. Compliance managers can implement a risk-based security strategy that incorporates regulatory requirements. In addition to helping identify potential threats in advance, the intelligence provides a useful record for audits and post-incident assessments.
Cyber Threat Intelligence Challenges
Successful network security goes beyond firewalls and antivirus software. Continuous detection and response must be combined with up-to-date, real-time threat intelligence. This is often beyond the scope of internal IT departments and security staff, requiring the hiring of external analysts or outsourced response teams.
Enterprise-grade tools for data collection are expensive to implement and maintain. Internal data collection and analysis often deploys security information and event management (SIEM) systems to collect and aggregate data from all areas of an organization. While this centralization is key to threat data analysis, it can be difficult for non-specialists to build on their own threat intelligence solution. Therefore, most organizations choose to incorporate threat intelligence platforms instead of building their own solutions based on SIEM data or independently sourced threat intelligence feeds.
Learn more in our detailed guide to threat detection.
Tips From Expert
In my experience, here are tips that can help you better implement and maximize the value of cyber threat intelligence (CTI):
- Leverage Real-Time Intelligence for Proactive Defense: Using CTI to anticipate attacks and identify emerging threats can help organizations stay ahead of the curve and mitigate risks.
- Integrate CTI with Existing Security Tools: Integrating CTI with your existing security tools creates a more comprehensive and effective security posture by enabling automation and enhancing threat detection and response.
- Use Threat Intelligence Feeds Tailored to Your Industry: Utilizing industry-specific threat feeds ensures that your CTI is focused on the most relevant threats to your organization.
- Create Intelligence-Sharing Partnerships: Collaborating with industry peers and government agencies can provide access to valuable intelligence and insights that may not be available through commercial feeds.
- Prioritize Threat Intelligence Based on Business Impact: Focusing on the threats that pose the greatest risk to your organization’s key assets and operations helps to optimize your security efforts and ensure that resources are allocated effectively.
Conclusion
In this article, we explained how cyber threat intelligence sources data from open source intelligence, social media, forensic data, device logs, the dark web, and many other sources, and repurposes it to serve these use cases:
- Cyber risk management – understanding risks facing the organization and the most appropriate controls to mitigate them.
- Security Operations Center (SOC) – providing SOC analysts with additional context about the threat actors operating in the environment.
- Vulnerability management – identifying vulnerabilities and prioritizing them according to business impact.
- Incident investigation and response – identifying the root cause of security incidents and responding more effectively.
- Security compliance – identifying risks that affect the organization’s compliance responsibilities and mitigating them to minimize compliance risk.
We hope this will be helpful as you augment your security operations with threat intelligence data.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response