Cyber Attacks Overview
By: Asaf Perlman
Introduction
2020 was a unique year in many aspects, especially in the field of cyber-security.
The COVID-19 pandemic forced many organizations to start working from home and the challenge to stay safe in the field of cyber-security increased by many levels.
According to Ponemon Iinstitute, Tthe Chances of experiencing a cyber-attack are as high as 1 in 4.
Many well-known organizations were attacked in the last two months of the year, raising several questions:
- Was 2020 the year with the greatest number of cyber-attacks?
- How much money was lost by organizations across the world because of such attacks? What were the most common attack types?
- How can I stay out of the statistics?
This article will provide answers to these questions.
COVID-19 Pandemic VS Cyber Pandemic
Ask almost anyone what the main story was for 2020, and they will likely start with the COVID-19 pandemic. But there is much more to this story.
2020 will also be remembered as the year that security events exploded, and cyber incidents transformed society in numerous ways.
Defining a cyber pandemic is a bit like defining a “perfect storm” — only this storm is in cyberspace.
There are many moving parts, from ransomware to data breaches and from election security to unemployment fraud, COVID-19 has in many ways unleashed a new set of challenges and accelerated existing challenges within global enterprises.
What is clear is that in 2020, technology and security professionals struggled to respond to the changing environment as quickly as the bad actors unleashed attacks, taking advantage of unprecedented shifts in people, processes and technology within governments and worldwide companies.
2020 - Top Cyber Attacks
SolarWinds 
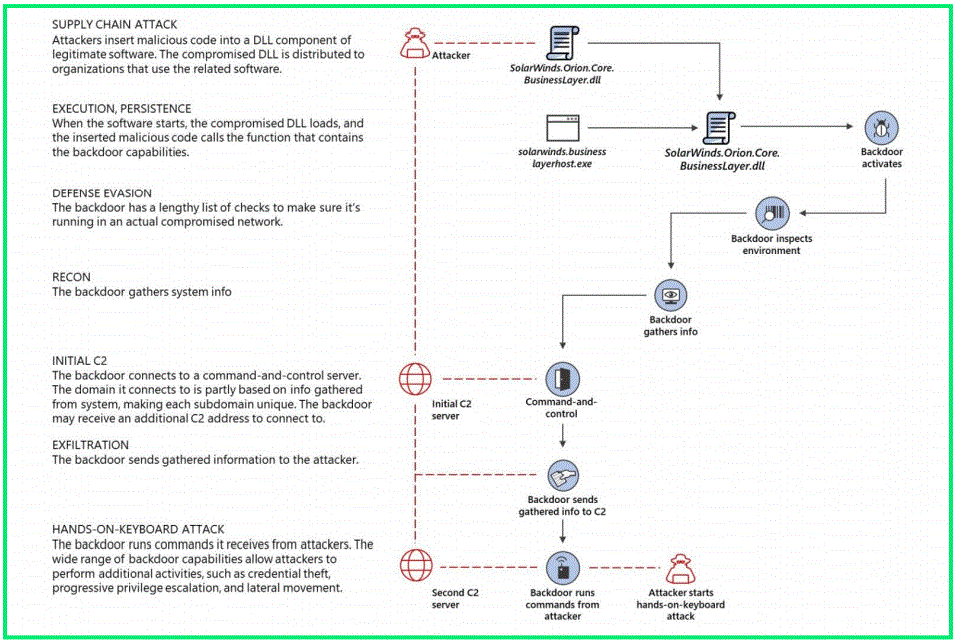
The attack involved hackers compromising the infrastructure of SolarWinds, a company that produces a network and application monitoring platform called Orion, and then using that access to produce and distribute trojanized updates to the software’s users.
On a page on its website that was taken down after news broke out, SolarWinds stated that its customers included 425 of the US Fortune 500, the top ten US telecommunications companies, the top five US accounting firms, all branches of the US Military, the Pentagon and the State Department, as well as hundreds of universities and colleges worldwide.
The malicious Orion updates
The software builds for Orion versions 2019.4 HF 5 through 2020.2.1 that were released between March 2020 and June 2020 contained a trojanized component.
The attackers managed to modify an Orion platform plug-in called SolarWinds.Orion.Core BusinessLayer.dll that was distributed as part of Orion platform updates. The trojanized component was digitally signed and contained a backdoor that communicated with third-party servers controlled by the attackers.
FireEye – The Stolen Red Team Tools
FireEye is one of the world’s top cybersecurity firms with major government and enterprise customers around the world. The company is known for its top-notch research on state-sponsored threat actors and its incident response capabilities. Over the years it was called in to investigate some of the most high-profile breaches in governments and organizations.
On August 12, 2020 FireEye announced that a sophisticated group of hackers, likely state-sponsored, broke into its network and stole tools that the company’s experts developed to simulate real attackers and test the security of its customers.
As FireEye began to look for the attackers and how the breach was accomplished, they discovered that the core issue was a malware-infected update to SolarWinds Orion, the company’s IT management software.
On December 13, 2020 FireEye published a threat research report “Highly Evasive Attacker Leverages SolarWinds Supply Chain to Compromise Multiple Global Victims With SUNBURST Backdoor”
Additional “Hands-On” information and details on Sunburst’s C2 (Command & Control) communications can be found in our article covering the SUNBURST malware.
Supernova – One Backdoor Is Not Enough
Intro
The investigation of the SolarWinds supply chain attack and the SUNBURST backdoor has led to the discovery of an additional malware that also uses the SolarWinds Orion product as its delivery method. but is unlikely to be related to the preceding unfolding event and is likely used by a different threat actor.
The malware dubbed SUPERNOVA consists of a small persistent backdoor in the form of a DLL file named: App_Web_logoimagehandler.ashx.b6031896.dll. The attackers cleverly injected malicious C# code into this file which appeared as if the actual SolarWinds developers have written it. This was done to avoid manual code review and automated tests to allow remote code execution through the SolarWinds web application server when triggered. The new malware consists of several sophisticated and novel TTP’s that imply the attackers are highly skilled.and contained a backdoor that communicated with third-party servers controlled by the attackers.
Attack Flow
- Infected .dll receives malicious C# code from C2 server.
- Infected .dll, sitting inside the Orion platform web interface functions as a backdoor for the hackers. Malicious C# is executed in memory (DynamicRun) to hinder DFIR attempts / EDR detections.
- The hackers can abuse all windows features on endpoints under Orion platform scope that can be modified using the .NET API.
- Further exploitation of endpoints inside the internal network.
Additional information and details can be found in our article covering the Supernova backdoor
No Easy Solution
Software supply-chain attacks are not a new development. Security experts have been warning for many years that they are some of the most difficult types of threats to prevent because they take advantage of trust relationships between vendors and customers and machine-to-machine communication channels, such as software update mechanisms that are inherently trusted by users.
Software AG – Clop Ransomware Attack
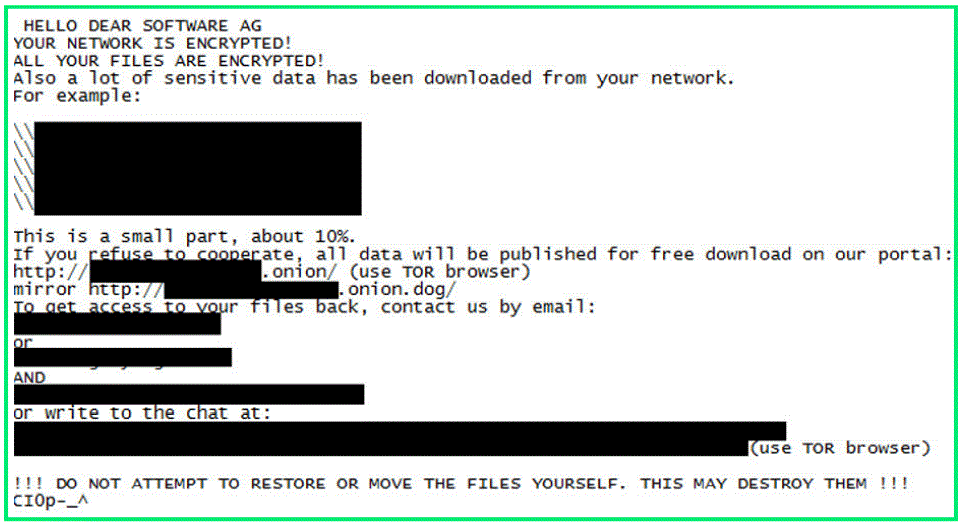
The second-largest software vendor in Germany and the seventh largest in Europe, Software AG was reportedly hit by a ransomware attack in October 2020. ZDNet reported that the German tech firm had been attacked by the Clop ransomware and that the cyber-criminal gang had demanded is $23 million ransom.
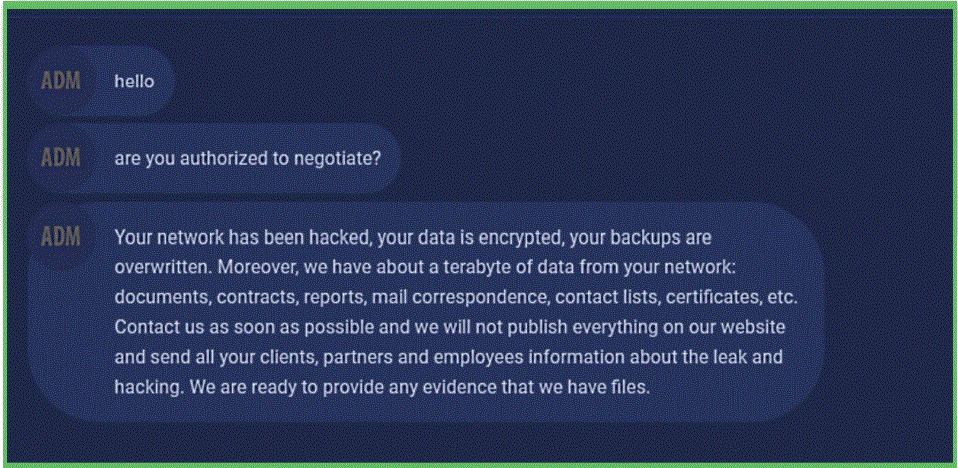
The report also stated that the company had still not completely recovered from the attack. The company disclosed that the ransomware attack disrupted a part of its internal network, but services to its customers, including cloud-based services, remained unaffected. The company also tried to negotiate with the attackers, but it those efforts were in vain.
As per the statement released by Software AG, the company is in the process of restoring its system and database for resuming orderly operation.
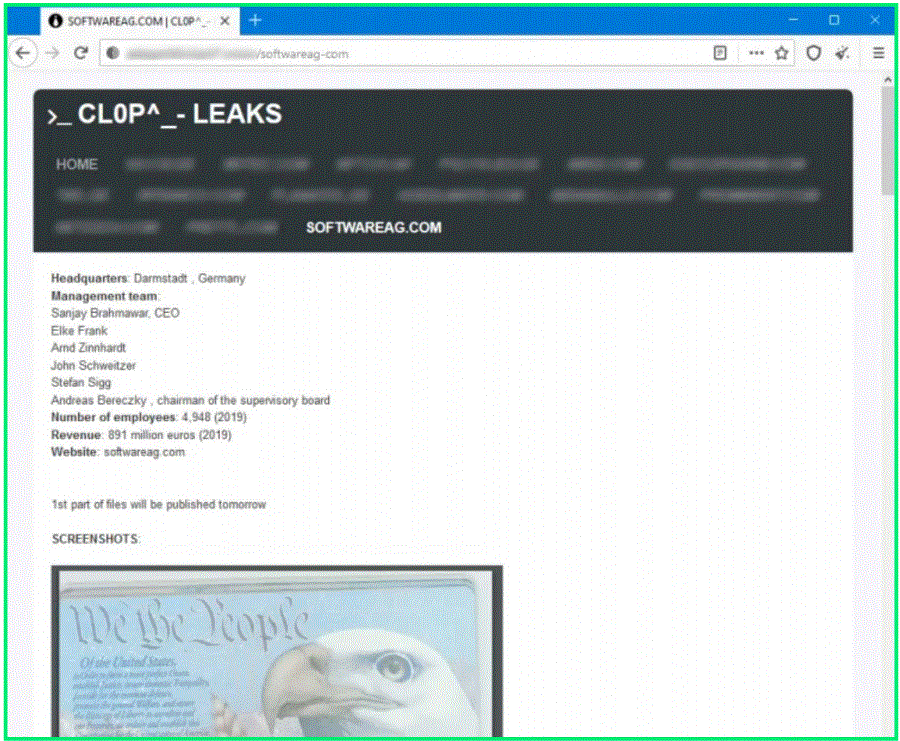
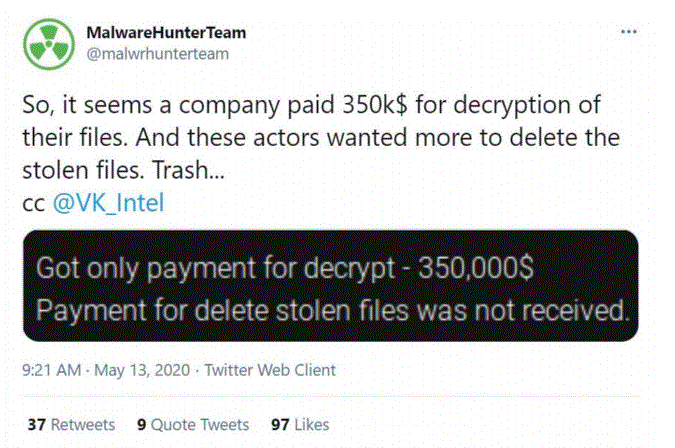
The ID provided in this ransom note allows security researchers to view the online chats between the Clop gang and Software AG on a web portal managed by the ransomware group. At the time of writing, there is no evidence the German company paid the ransom demand.
Clop has emerged as a potent ransomware threat, first discovered in February 2019 by the “MalwareHunterTeam”. The group behind Clop continues to terrorize companies with a tactic called “double extortion”, meaning it steals the data and if their ransom demands aren’tare not met, the data is dumped on a criminal website for anyone to access.
Sopra Steria – Ryuk Ransomware Attack
Sopra Steria is a European information technology firm with 46,000 employees in 25 countries, providing a large array of IT services, including consulting, systems integration, and software development.
On October 21, 2020, Sopra Steria announced it had detected a cyberattack the previous evening. The virus has been identified as a new version of the Ryuk ransomware, previously unknown to antivirus software providers and security agencies.
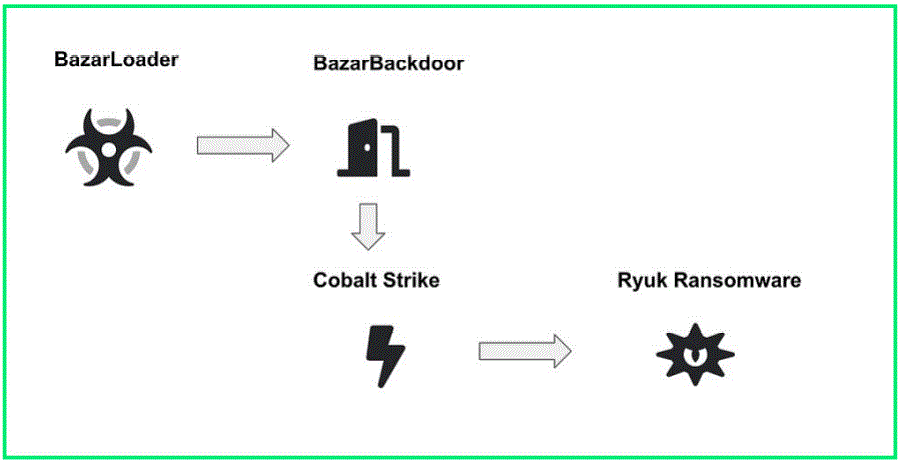
Sopra Steria issued a statement confirming that the company was hit with a Ryuk ransomware attack after previously being infected with either TrickBot or BazarLoader.
Both malware infections (TrickBot or BazarLoader) were created by the same hacking group and provide remote access to the threat actors behind Ryuk Ransomware. It was determined that the attackers compromised the network over the weekend and then deployed the ransomware on October 20th, so the cyberattack was discovered relatively quickly.
Sopra Steria’s investigation teams immediately provided the authorities with all information required. The company also made this new version of the virus signature available to all antivirus software providers.
Because the security measures were implemented immediately following the attack the virus was contained to a limited part of the Group’s infrastructure and enabled the company to protect its customers and partners.
To date, following in-depth investigation, Sopra Steria has not identified any leaked data or damage caused to its customers’ information systems. Having analyzed the attack and established a remediation plan, the Group is starting to reboot its information system and operations progressively and securely.
Telegram Hijack
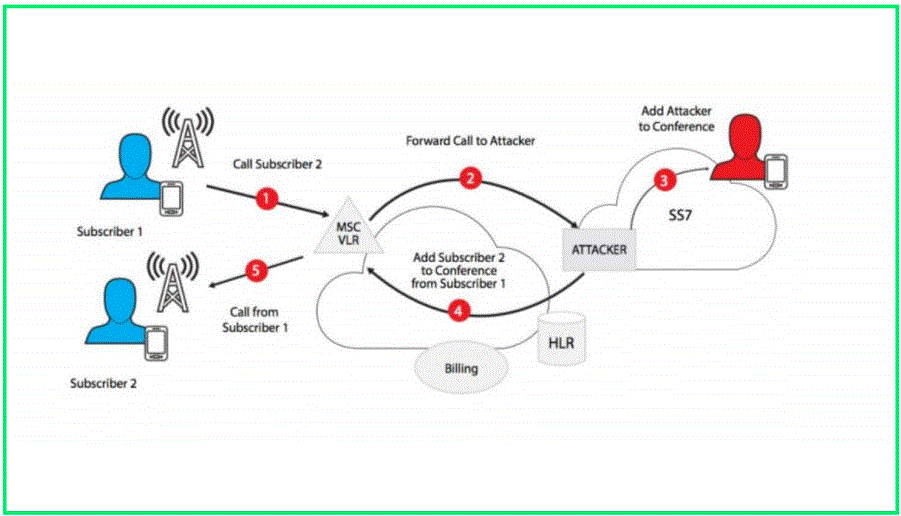
Hackers with access to the Signaling System 7 (SS7) used for connecting mobile networks
across the world were able to gain access to Telegram messenger and email data of high-profile individuals in the cryptocurrency business.
In what is believed to be a targeted attack, the hackers were after two-factor authentication (2FA) login codes delivered over the short messaging system of the victim’s mobile phone provider.
Hackers conducting pulling an SS7 attack can intercept text messages and calls of a legitimate recipient by updating the location of their device as if it registered to a different network (roaming scenario).
The attack occurred in September and targeted at least 20 subscribers of the Partner Communications Company (formerly known as Orange Israel), all of them CEOs and vice CEOs who run digital currency projects.
The hackers likely spoofed the short message service center (SMSC) of a mobile network operator to send an update location request for the targeted phone numbers to Partner (other providers may still be vulnerable to this type of attack).
This type of assault is quite rare. Essentially, the hackers sent a message from a foreign cell network to an Israeli one, updating the client’s location. For example, “The client has just landed in Madrid and has registered with our network. Please route his SMS messages via this network.”
This procedure is necessary for people entering a foreign country with cell phones in ‘roaming’ mode.
In some cases, the hackers posed as the victims in their Telegram accounts and wrote to some of their acquaintances, asking to exchange BTC for ETC and the like.
Why did this attack approach only occur in the accounts of Partner clients?
Other networks may have a firewall protection that Partner doesn’t to make sure this type of attack is detected. This could identify anomalies in the user’s behavior and block such communication.
Despite the breach, the hack ultimately failed because none of the victims, as far as anyone knows, fell for it and transferred money to the hackers. The original hackers’ identity remains unknown.
Although sending verification codes over SMS is widely regarded as insecure in the infosec community, for good reason, many services still rely on this practice, which puts users at risk.
Authentication methods that are better than SMS or call-based 2FA now exist. Apps specifically created for strong authentication or physical keys are among the solutions.
In addition, telecom standards need move away from legacy protocols like SS7 (developed in 1975), which cannot address modern issues.
BlackBaud - Ransomware Attack
Blackbaud, a cloud technology company used by colleges, universities, non-profits (and far-right organizations), was hit by a data-stealing ransomware attack earlier this year. The attack was one of the biggest of the year in terms of the number of organizations affected, with nearly 200 organizations and millions of individuals potentially impacted.
Blackbaud said in July that it paid the ransom — but also claimed they received “confirmation” that the stolen personal data “had been destroyed,” fooling absolutely nobody.
“After discovering the attack, our Cyber Security team—together with independent forensics experts and law enforcement—successfully prevented the cybercriminal from blocking our system access and fully encrypting files; and ultimately expelled them from our system. Prior to our locking the cybercriminal out, the cybercriminal removed a copy of a subset of data from our self-hosted (private cloud) environment. Because protecting our customers’ data is our top priority, we paid the cybercriminal’s demand with confirmation that the copy they removed had been destroyed.”
Blackbaud later confirmed in a regulatory filing that the stolen data also included bank account data and Social Security numbers — far more personally identifiable information than the company first thought. The company had originally claimed “In most cases, fields intended for sensitive information were encrypted and not accessible.”.
In many cases, ransomware groups have usually pursued one of the two ransom fees (for decrypting files or for not publishing the data), but the Asko gang is known for chasing both simultaneously.
Despite Blackbaud’s claim that the data was deleted, these are malicious hackers driven by financial reward. Hope for the best but assume the worst — Blackbaud’s data is still out there.
Emotet – The new wave
Over the last weeks of 2020, Cynet CyOps and Research teams have been engaged in another wave of the infamous Emotet trojan. This time, with some tweaks and changes under its belt, Emotet keeps reminding us that it is here to stay.
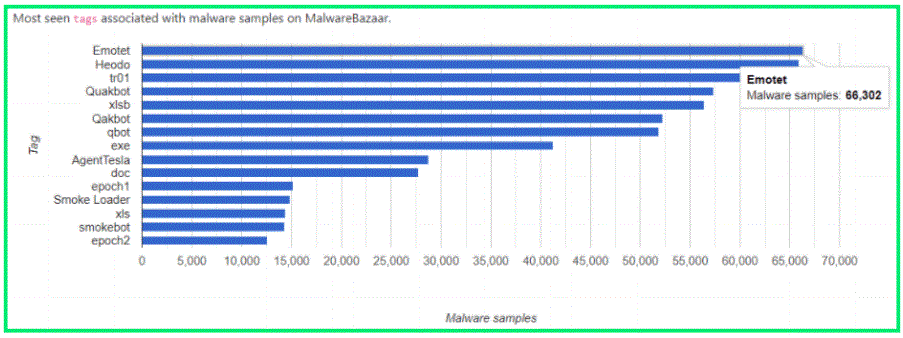
According to statistics provided by MalwareBazaar and ANY.RUN, Emotet banking trojan is now in the infamous first place of the most popular threats:
The first Emotet banking trojan sample was identified in 2014 and was classified as a trojan that steals banking credentials by hooking Internet traffic of the online banking sessions. Over the years, Emotet has upgraded its capabilities and modules.
Since 2017, Emotet has been observed as more than a banking trojan and seems to have evolved into the world’s most dangerous “Dropper.” Emotet packs some extremely sophisticated capabilities utilizing different tactics, techniques, and procedures (TTPs), which make it today’s “most serious” threat.
In 2019, Emotet became the most common module in the spread (botnet infrastructure) of banking trojans and ransomware such as Trickbot, Qbot, Ursnif, Ryuk, and Megacortex.
After a short period of time with little activity, a new wave of Emotet campaigns struck again. The new Emotet threat actor uses a new chain of execution that has evolved considerably, and also switched the EXE file of the Emotet binary to a DLL file, which is loaded through the Rundll32 process. In addition, Emotet has now added fake error messages to weaponized Microsoft Office documents.
You can get additional information and details in our article covering the new Emotet wave
What Can We Learn from These Cyber Attacks?
Businesses need to be diligent. Cyber security always needs to be top of mind and systems and setups need to be routinely assessed. Any organization can become the victim of phishing schemes, ransomware, DDoS, malware, and other attacks leading to data breaches. Stress to your customers that taking all necessary precautions is the best chance they have at staying secure. Along with detection and response tools, authentication protocols and ongoing employee security awareness training can make the biggest difference.
Must Follow Rules
- Conduct VAPT (vulnerability assessment and penetration testing) periodically to check for exploitable security vulnerabilities in the IT infrastructure of your organization
- Back up all the sensitive or confidential data and store it separately from time to time
- Keep all the systems, software, and applications up to date with the latest security patches
- Restrict employees from sharing passwords and encourage them to use unique and strong passwords
- Run a cyber attack simulation campaign to assess the level of cyber awareness among Then train them accordingly
- Make sure to implement the practice of using multi-factor authentication to maintain security and privacy
- Restrict IT admin and access rights to limited Ensure that they are adequately trained on the safe usage and encrypted storage of sensitive data
2020 Trends and numbers
Largest Data Breaches Statistics
During 2020, several organizations experienced a data breach, putting their business, reputation, customers, and partners at high risk. To keep your organization safe, it is important to understand the most common causes that lead to data breaches Infected .dll receives malicious C# code from C2 server.
Data Breach – Most Common Causes
- Weak and Stolen Credentials, a.k.a. Passwords
- Back Doors, Application Vulnerabilities
- Malware
- Social Engineering Too
- Many Permissions
- Insider Threat
- Improper Configuration and User Error
The growth of large-scale breaches represents a growing trend of security violations in both numbers and their severity. Data breaches expose sensitive information that often leaves users at risk for identity theft, ruin companies’ reputations and leave the company liable for compliance violations.
- Weak and Stolen Credentials, a.k.a. Passwords
- Back Doors, Application Vulnerabilities
- Malware
Cyber Crime by Attack Type
It is critical to understand that cybersecurity attacks in terms of their type and origins. Cyberattacks predominantly include:
- Malware
- attack DoS and DDoS
- MitM (Man in the middle)
- Phishing and spear-phishing attacks
- Drive-by attack
- Password attack
- SQL injection attack
- XSS
Data Breach – Most Common Causes
- 34% of data breaches involved internal actors.
- 69% of organizations don’t believe the threats they’re seeing can be blocked by their anti-virus software.
- The average cost of a ransomware attack on businesses is $133,000.
- 92% of malware is delivered by email.
- Ransomware detections have been more dominant in countries with higher numbers of internet-connected populations. The United States ranks highest with 18.2% of all ransomware attacks.
- 52% of breaches featured hacking, 28% involved malware and 32–33% included phishing or social engineering, respectively.
- 71% of breaches were financially motivated and 25% were motivated by espionage.
Industry-Specific Cyber Stats
Finance and Healthcare are the most popular targets among hackers. Sadly, in general, no one is safe nowadays.
- 43% of breach victims were small and medium businesses.
- 5% of breaches involved Healthcare organizations, 10% in the Financial industry and 16% in the Public Sector.
Security Spending and Costs
Cybersecurity budgeting has been increasing steadily as more decision-makers are realizing the value and importance of cybersecurity investments. According to the Cyber Security mid-year snapshot’19 report, Cybersecurity budgets have increased by almost 60%.
- By the end of 2020, security services are expected to account for 50% of cybersecurity budgets.
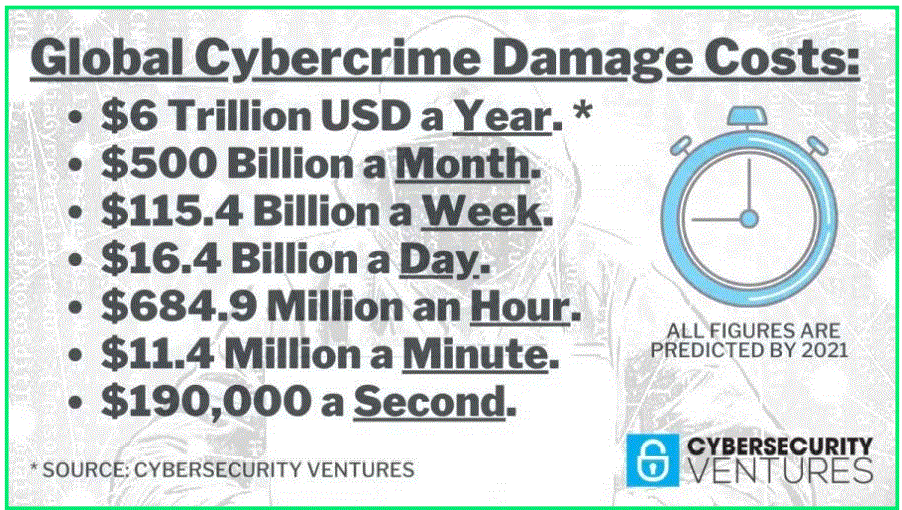
- The average cost of a malware attack on a company is $2.6 million.
- $3.9 million is the average cost of a data breach.
- The average cost in time of a malware attack is 50 days.
- The most expensive component of a cyber-attack is information loss at $5.9 million.
- Including turnover of customers, increased customer acquisition activities, reputation losses and diminished goodwill, the cost of lost business globally was highest for U.S. companies at $4.13 million per company.
Simple Guidelines
To improve and raise your Cybersecurity posture and awareness you don’t need to invest endlessly in new security tools. The truth is that 80% of data breaches can be prevented with basic actions, such as vulnerability assessments, raising employee awareness, patching, and proper configurations.
Although the reality is challenging, and a future is not promising to be better in terms of cybersecurity threats and malicious attacks, Cynet is here to address your challenges and to help you realize your cybersecurity status, its capabilities and provide you recommendations for improving overall cybersecurity coverage.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response