Let’s get started!
Ready to extend visibility, threat detection and response?
Get a DemoAs part of our ongoing threat intelligence efforts to discover emerging threats and vulnerabilities, the CyOps team would like to bring a new risk to your attention. The risk is associated with a vulnerable file from Dell “dbutil_2_3.sys” along with 5 newly discovered vulnerabilities related to the file, a Dell driver that Dell machines install and load during the BIOS update process that is unloaded at the next reboot.
The vulnerabilities are collectively assigned to CVE-2021-21551:
CVE-2021-21551 Local Elevation of Privileges Memory corruption
CVE-2021-21551 Local Elevation of Privileges Memory corruption
CVE-2021-21551 Local Elevation of Privileges Lack of input validation
CVE-2021-21551 Local Elevation of Privileges Lack of input validation
CVE-2021-21551 Denial of Service Code logic issue
These types of vulnerabilities are not considered critical since an attacker exploiting them needs to have previously compromised the computer. However, when successful, it allows attackers to gain persistence on infected hosts.
Following Dell’s Instructions, below is a summary of steps to mitigate these vulnerabilities:
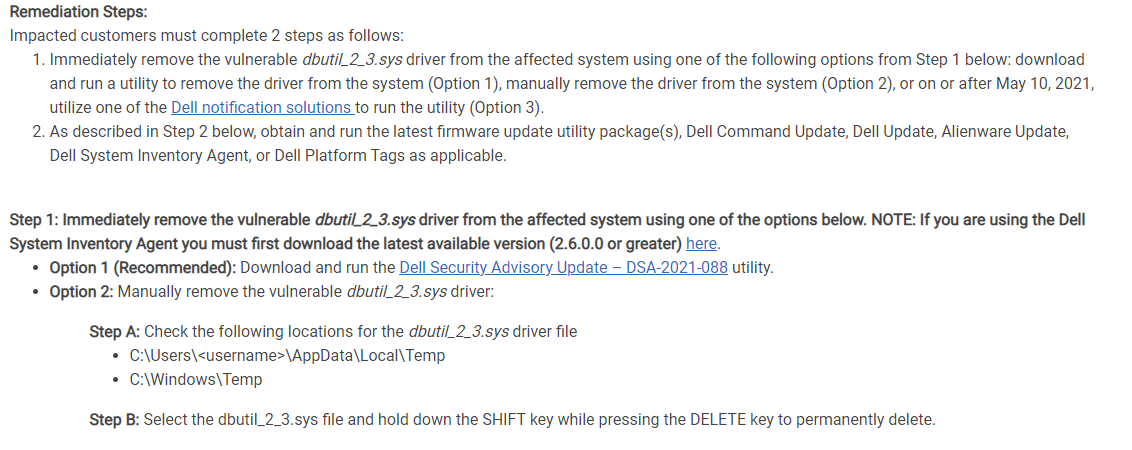
Cynet provides full visibility on Dell “.sys” drivers and enables security and IT personnel to remotely mitigate the vulnerability and delete the file via Cynet360 Console.
The following easy steps will assist in this task:
Figure 01: Enable the threat hunting module via the scan group settings
Figure 02: Using the threat hunting module to create a policy with the “dbutil_2_3.sys” value
Figure 03: An alert will be triggered upon detection by the threat hunting policy
Figure 04: Create an Auto-Remediation rule to delete the vulnerable driver.
As always, we are available for any question or concerns and in any case further assistance is required.
Search results for: