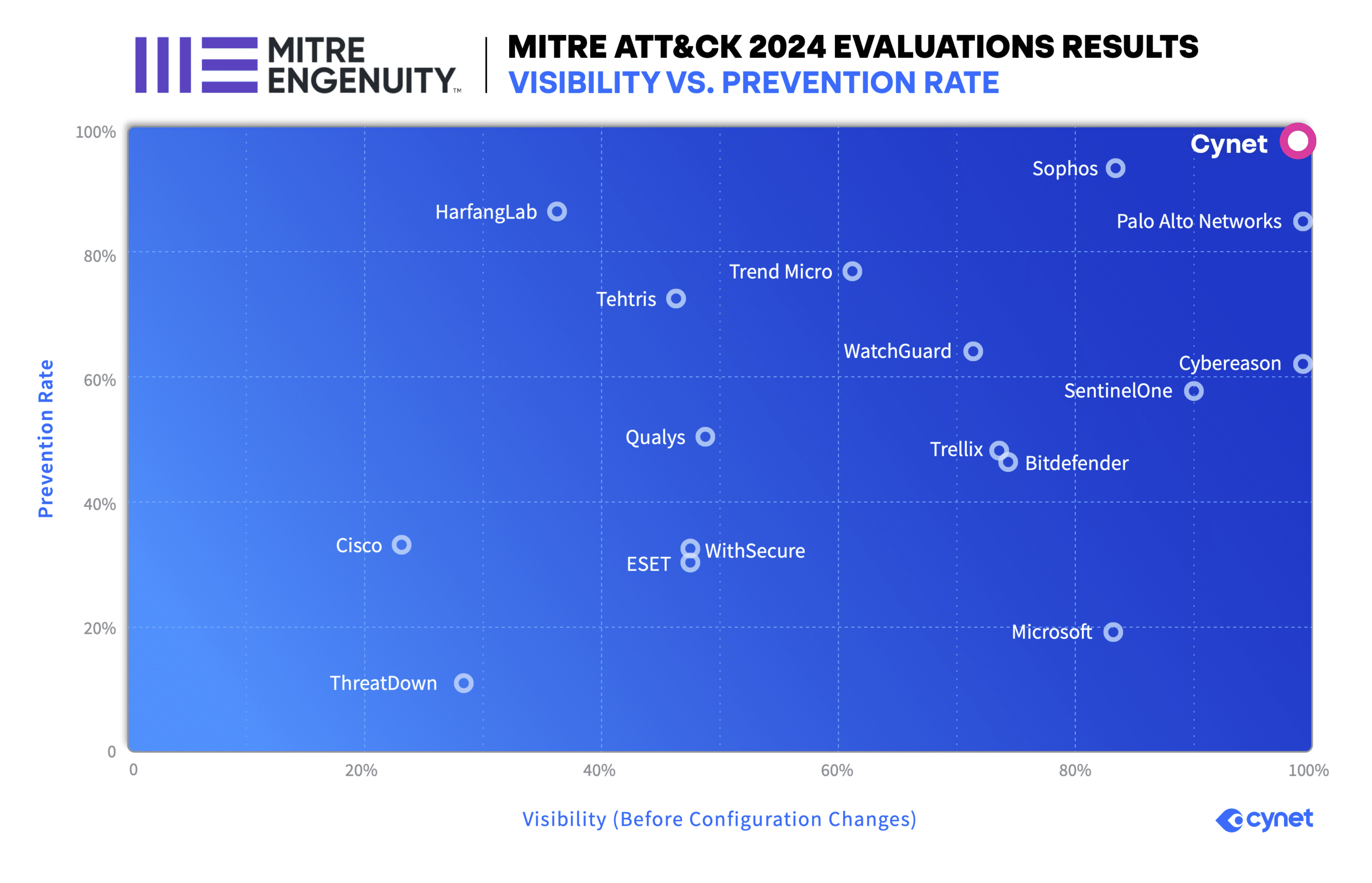
ONLY Cynet Delivers 100% Protection and 100% Detection Visibility in the 2024 MITRE ATT&CK Evaluation
Across small-to-medium enterprises (SMEs) and managed service providers (MSPs), the top priority for cybersecurity lea… Read More
ALL

Across small-to-medium enterprises (SMEs) and managed service providers (MSPs), the top priority for cybersecurity lea… Read More

What Are Exploit Kits? Exploit kits are a type of all-inclusive, automated, and rapidly deployable threa… Read More

What Is Incident Response? Being prepared is key to responding to security incidents in an accurate and… Read More

Like any other emergency situation, security incidents require swift, coordinated action. But operating i… Read More

What Is “Living off the Land?” The term “living off the land” (LOL) was coined by malware researc… Read More

Back in the early days of malware, scammers spread their wares around from user to user via infected flop… Read More

Endpoint – Where the Interesting Stuff Takes Place The endpoint has always been the ultimate attackers’… Read More

In mid-April 2019, a new and sophisticated malware threat began to appear on computers of home users and… Read More

What Is an Insider Threat? As the name plainly suggests, insider threats are risks caused by insiders who… Read More
Search results for: