Cyber Insurance: Policies, Coverage, Requirements, and More
What is Cyber Insurance?
Cyber insurance mitigates an organization’s financial risk in case of a data breach, ransomware attack, or other cyber security incident.
Early cyber insurance policies consisted of extra liability insurance added to a standard business policy, but the complexity of cyber-attacks made it necessary to create a specific policy. Modern agreements usually cover damage and recovery costs, but some extend to investigations, forensics, fines, lawsuits, and even ransomware payments.
In this article:
- How Does Cybersecurity Insurance Work?
- The Cyber Insurance Market
- Types of Cyber Insurance Policies
- What Cyber Insurance Covers
- What Are the Most Common Requirements for Cyber Insurance?
- Cyber Insurance FAQ
- Security tools like XDR cover what insurance doesn’t
Do You Need Cyber Insurance?
While all organizations may benefit from cyber insurance, some use cases need it more. How do you know if that’s you? If your organization falls into one of these categories, you need cyber insurance:
Case 1: Your org stores sensitive data online or on your servers
If your business stores personal information, such as credit card or social security numbers, attackers will be interested in it. If you store only your own financial information and some customer data, you should have first-party coverage.
Case 2: Your org has a large customer base
If you manage sensitive data from a large number of customers, get cyber insurance. Liability or data breach insurance may help cover the recovery costs and regulatory fines if your business is a victim of a data breach. First-party policies may cover notification costs.
Case 3: Your org has valuable assets and high revenue
Mature businesses with valuable assets may have considerable losses in a cyber incident. A cyber insurance policy can help cover loss of revenue as well as ransom costs.
This is part of a series of articles about Incident Response.
Learn more in our detailed guide to incident response policy.
How Does Cybersecurity Insurance Work?

Cybersecurity insurance works by providing financial protection to policyholders in the event of a cyber-related incident. It helps cover the costs associated with managing and recovering from such events. Here’s a brief overview of how it works:
- Risk assessment: Before issuing a policy, insurers assess the applicant’s cybersecurity posture to determine the level of risk. This includes evaluating the organization’s security policies, practices, and infrastructure.
- Tailored coverage: Based on the risk assessment, insurers offer customized policies that address the specific needs of the organization. Coverage may include liability for data breaches, network intrusions, ransomware attacks, business interruption, and more.
- Premiums: Policyholders pay regular premiums to maintain their coverage. The premium amount is typically determined by the organization’s size, industry, risk profile, and coverage limits.
- Incident response: In the event of a cyber incident, the policyholder reports the event to the insurer, who may assist with incident response, such as providing access to cybersecurity experts, legal counsel, and public relations support.
- Claims and compensation: Following an incident, the policyholder submits a claim detailing the financial losses and expenses incurred. The insurer then reviews the claim and, if approved, compensates the policyholder according to the policy’s terms and limits.
By transferring some of the financial risks associated with cyber threats to the insurer, cybersecurity insurance helps organizations manage and mitigate the impact of cyberattacks and other digital vulnerabilities.
The Cyber Insurance Market
The cyber insurance market is growing fast. During the pandemic, digital processes moved online, remote work increased—and so did cybercrime. Let’s review some statistics about the rise of cyber insurance:
Cyber insurance is expected to reach over $20 billion by 2025, an increase from $7 billion in 2020.
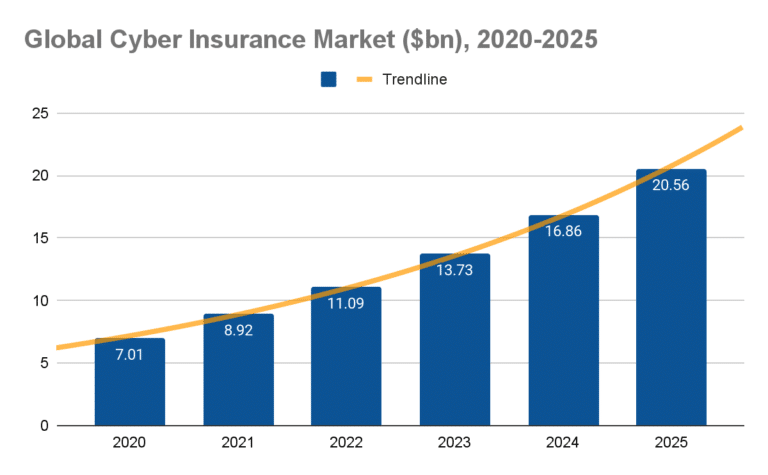
(Source: Global Data)
- The exponential rise in cyber-attacks, a 50% increase since 2020, drove the need for cyber insurance.
- The cost of cybercrime is expected to reach $10.5 trillion by 2025.
Types of Cyber Insurance Policies
Liability Coverage
If your customers’ information is compromised in a cyber attack, liability coverage protects you from their lawsuits and associated expenses, like:
- Attorney fees
- Settlements and court costs
- Non-compliance fines
First Party Coverage
This covers your org if it’s hacked, providing financial assistance for recovery costs of a cyber attack. First-party policies usually cover:
- Investigation of the incident
- Loss of revenue because of business interruption
- Ransomware payments according to coverage limits
- Customer notification and anti-fraud services
- Systems reparation
The most common first-party coverage is data breach insurance, which protects an organization financially if confidential information is stolen. Companies of all sizes can be victims of a data breach.
Technology Errors and Omissions
This type of policy, also known as “Technology E&O” is useful to protect IT businesses if one of their products is involved in a cyber incident. It’s similar to cyber security liability insurance in that it pays legal fees, court costs, and settlements, only in specific circumstances related to faulty products or services.
What Cyber Insurance Covers
Cyber insurance policies generally include two types of coverage: first-party coverage and third-party liability coverage. Each type addresses different aspects of cyber risks and their associated costs.
First-Party Coverage
First-party coverage focuses on the direct costs an organization incurs as a result of a cyber incident. This may include:
- Incident response and investigation: Covers expenses related to identifying, assessing, and mitigating a cyber incident, such as hiring cybersecurity experts, forensic specialists, and legal counsel.
- Business interruption: Compensates for lost income and increased operational costs due to network downtime or disruption caused by a cyber event.
- Data recovery: Covers the costs of restoring or recreating lost or damaged data, as well as repairing or replacing affected hardware and software.
- Cyber extortion: Addresses financial losses from ransomware attacks, including ransom payments (if allowed by law) and costs associated with negotiation and mitigation.
- Crisis management and public relations: Covers the expenses related to managing the organization’s reputation and communication efforts following a cyber incident.
- Notification and credit monitoring: Covers the costs of notifying affected customers, employees, or other stakeholders, as well as providing credit monitoring or identity theft protection services.
Third-Party Liability Coverage
Third-party liability coverage addresses the costs associated with legal claims and regulatory actions resulting from a cyber incident. This may include:
- Privacy liability: Covers costs associated with claims or lawsuits arising from unauthorized access, theft, or disclosure of personal or sensitive information.
- Regulatory fines and penalties: Addresses financial penalties imposed by regulatory agencies for non-compliance with data protection laws and regulations.
- Media liability: Covers claims related to intellectual property infringement, defamation, or other harms caused by an organization’s online content or media presence.
What Isn’t Covered By Cyber Insurance?
Cyber insurance policies generally do not cover:
- Physical damage or bodily injury resulting from a cyber event.
- Losses from unencrypted devices, if the organization has not implemented proper security measures.
- Losses due to war, terrorism, or government actions.
- Losses resulting from an organization’s intentional or malicious acts.
- Legacy systems or unsupported software that have not been properly updated or maintained.
It’s important to carefully review a policy’s terms, conditions, and exclusions to understand the full extent of the coverage provided.
What Are the Most Common Requirements for Cyber Insurance?
Cyber insurance providers typically require organizations to have certain cybersecurity measures in place as a precondition for coverage. These requirements help ensure that the organization has a baseline level of security to reduce the likelihood and impact of cyber incidents. Some of the most common requirements for cyber insurance include:
- Endpoint detection and response (EDR): Implemented on all endpoints to minimize the risk of unauthorized access and malware infections. Key capabilities include real-time monitoring, threat detection, prevention, and incident response.
- Multi-factor authentication (MFA): Adds an additional layer of protection by requiring users to provide multiple forms of identification. Common factors include knowledge, possession, and biometrics.
- Backup procedures: Regular, verified, encrypted backups of data and systems with multiple on-site and off-site copies. Offline or alternative backup solutions are often required to mitigate data loss risks.
- Identity and access management (IAM): Ensures only authorized users have access to sensitive systems and data. Key components include user provisioning, authentication, authorization, and auditing/monitoring.
- Good patch management: Addresses known vulnerabilities by identifying, acquiring, installing, and verifying security patches and updates. Key elements include inventory, vulnerability monitoring, prioritization, patch testing, deployment, verification, and reporting.
Cyber Insurance FAQ
What Do I Need to Look for in a Cyber Insurance Policy?
Every insurance vendor has a different combination of elements in their policies. However, there are seven basic elements you should look for in a cyber insurance policy:
- Notification expenses
- Legal expenses
- Regulatory fines
- Incident investigation expenses
- ID Theft Repair
- Liability costs
- Public relations expenses to repair reputation damage.
How Much Cyber Security Coverage Do You Need?
This would depend greatly on your business use case. Most small organizations use a standard $1 million cyber security coverage, but for a larger business, this would not be enough. An insurance agent can help determine the right level of coverage for your business.
Is Cyber Insurance Enough Coverage?
For all its benefits, cyber insurance is not enough protection against cyber attacks. Simply put, it acts to help repair the damage caused by an attack, but it won’t prevent you from getting attacked. You need a robust line of defense to prevent cyber attacks.
Learn more in our detailed guide to incident response management.
Security Tools Like XDR Cover What Insurance Doesn’t
Faced with the increase in data breaches, many organizations opt to expand their cyber insurance coverage. While doing so is smart, cyber insurance cannot take the place of defense tools.
Extended detection and response (XDR) is a cyber security approach that delivers holistic protection against cyber attacks. A robust XDR solution has the following capabilities:
- Identifies hidden threats
- Tracks threats across multiple components
- Increase the efficiency of threat investigation
- Detects and responds faster to active threats
- Provides full visibility of files, networks, hosts, and users
Using an XDR can even help reduce your insurance premium. The encompassing protection of an XDR solution significantly lowers the risk of a security incident, bringing a consequent reduction of legal claims. Other benefits of an XDR include:
- Improved prevention
- Granular visibility
- Greater control over access
- Increased alert accuracy
- Effective response
Check out Cynet 360 AutoXDR
Having a good insurance policy is important, but it can be costly. A robust security system that detects and prevents attacks can actually help reduce the cost of cyber insurance. Cynet 360 AutoXDR is the first autonomous, end-to-end, fully XDR platform. It integrates endpoint, network, and user attack prevention, providing a holistic and comprehensive defense solution.
Want to learn more about how Cynet can help you reduce your cybersecurity insurance premium? Let’s chat.