CyOps Lighthouse: Ransomware-as-a-Service (RaaS)
The Darknet is home to many underground hacking forums. In these forums Cybercriminals talk freely: Sharing stories, tactics, success stories, and failures.
Their conduct allows us to peek into the politics and ethics of those groups and actors, as they talk about recent activities.
Cyops Lighthouse aims to shed a light on those dark places. Apart from the underground forums, we will also provide information regarding ongoing ransomware groups publications and worthy mentions from the last month.
Ransomware-as-a-Service (RaaS)
When we hear about Ransomware, the first thing that comes to mind is an experienced attacker or APTs (black hoody optional), but the truth is far from it.
Ransomware has been offered for sale for several years now, with the first RaaS, “Ransom32”, dating back to 2015. Today, various models are offered to buyers.
The most common are:
- Buying a ready-made Ransomware on the Darknet. This leaves the attacker with the task of building infrastructure from scratch, which requires a lot of time and effort.
- “Renting” an already made operation and splitting the revenue based on income and activity.
Recent years have shown that the second option is far more preferable for threat actors, and it is one of the main reasons the activity of Ransomware groups has spiked.
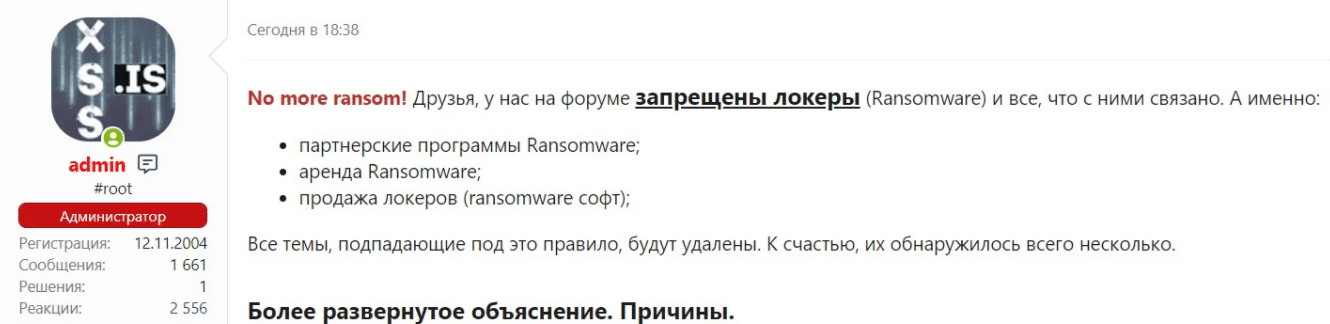
Ransomware operators are also called “affiliates”. They rent the services on underground forums such as XSS, Exploit and RAMP. While in the past, most of the activity was hosted on XSS and Exploit, following the REvil and Kaseya incident and due to high heat from law enforcement, both forums decided to ban RaaS activities in forums:
This does not mean banning the operator from the forums though, as they remain active on both XSS and Exploit. The activity probably remains in private messages and TOX (a secure chatting service).
As a result of these actions, a former REvil operator known by the nickname “Kajit” has opened a forum called “RAMP” that is hosted on the darknet. Activities on RAMP are taking place both in Russian and Chinese.
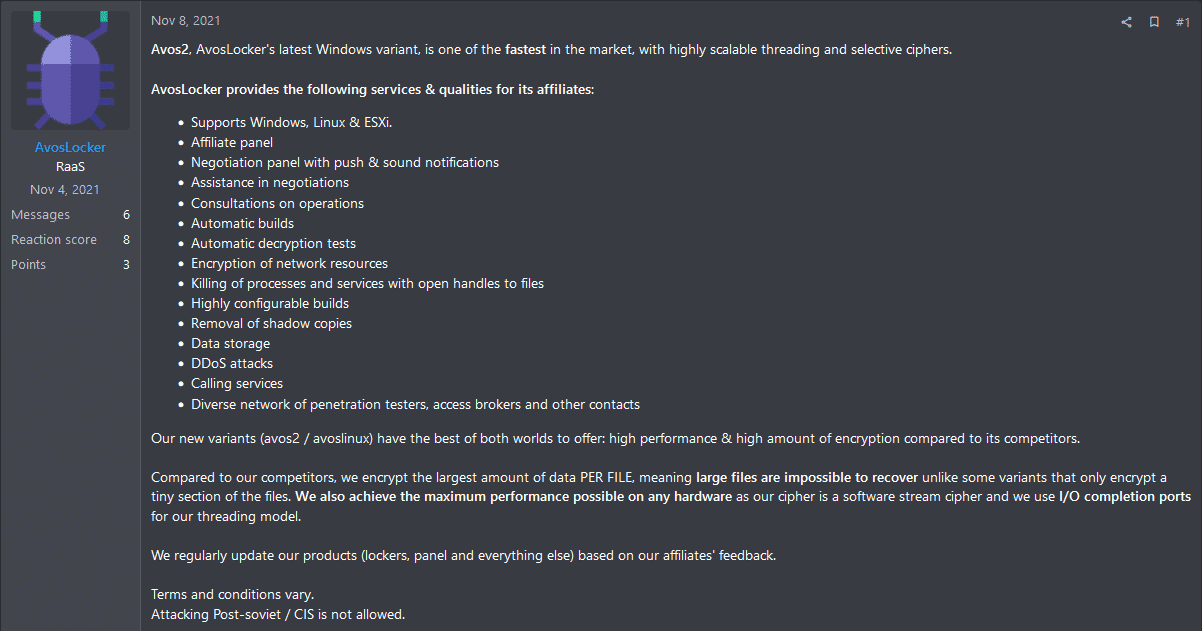
In a dedicated thread on the forum, those groups continue their activities and actively recruit new affiliates:
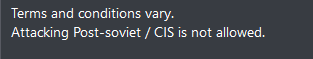
Above is an example of an “AvosLocker” group recruiting post. As you can see in the image, they offer a complete package for their affiliates and note that it is forbidden to attack post-Soviet/CIS countries. This prohibition is sometimes expanded into forbidding attacks on US GOV sites.
Also noted is the percentage taken by the Ransomware operators. For example, here are the details from the new ALPHV/BlackCat ransomware post:
Translation:
The rate is dynamic and depends on the amount of a single payment for each company, namely: – up to 1.5M$ – 80% – up to 3.0M$ – 85% – from 3.0M$ – 90%
*Noted is the percentage the affiliate gains, the operators rely on high activity volume.
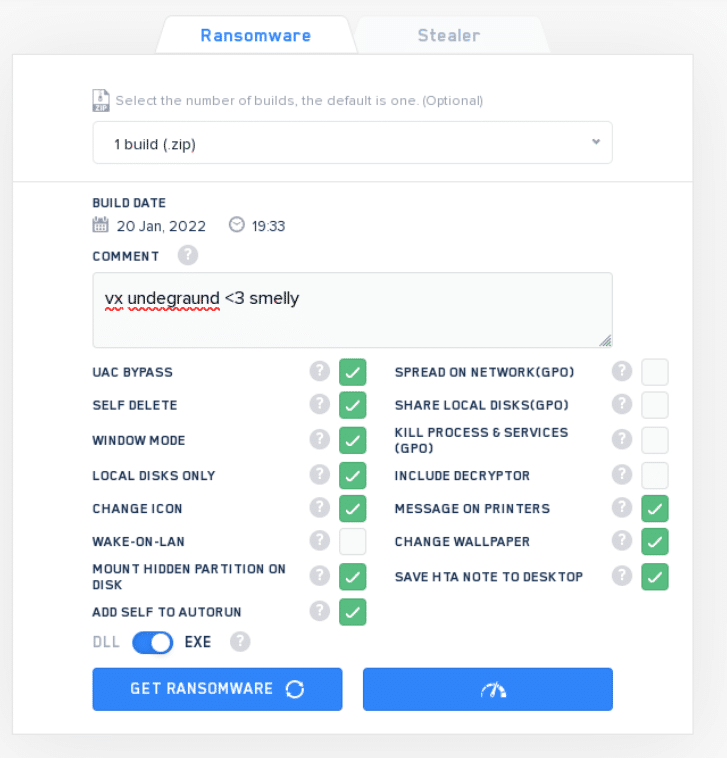
The “negotiation panel”, is either an executable or a webpage.
From the Panel, affiliates can manage an entire Ransomware operation by themselves, without the need for any external services.
The panel offers abilities as mentioned in the AvosLocker example above. Just recently VX underground (“The largest collection of malware source code, samples, and papers on the internet.”) published a photo of LockBit 2.0 Panel:
*Taken from VX underground’s Twitter account.
“Build” is the finished executable with the desired options chosen from the panel. It will be the payload affiliates distributes to its victims to spread the Ransomware.
Other groups like “Conti” go even further and will provide their affiliates with a penetration testing and post-exploitation guide. This guide has been previously leaked and is also available online.
While some will accept new affiliates, sometimes a candidate reputation is being valued, . Others will even require a guarantor- mostly someone who worked with the group in the past, or a known persona in the underground forums.
Targets can be received by the operators, but affiliates can also turn to “initial access brokers”- the name for the players who sell access to networks.
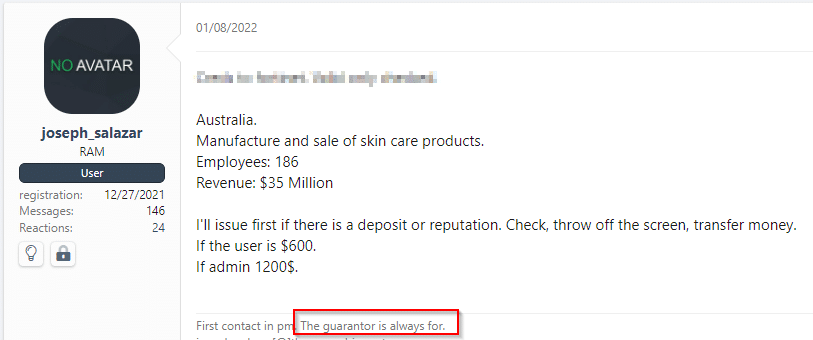
While Raas activity has been banned on several forums, the access market is flourishing. It offers affiliates a wide variety of target. Here’s an example for an access selling post on an XSS forum:
*Translated from Russian
As seen in the picture, the post usually details the region or country, the sector, company revenue, and prices for regular users or admin credentials.
Note that as mentioned before, the use of a guarantor is obligatory by the initial access broker.
Conclusion:
Ransomware As A Service (RaaS) is beneficial for both parties-affiliates and operators.
With RaaS, an inexperienced hacker can easily set up a fully running infrastructure, with a high-profit percentage. This gives him the ability to work alone or in a small group.
As for the Ransomware operator, if there are large scale sales, they benefit from minimizing the risk of exposure- and eventually getting caught. Their service is always provided in secure chats and mostly untraceable operations.
As we can see the activity spikes, new Ransomware groups are emerging once every few months, while others are starting to gather affiliates and build their infrastructure. These changes, coupled with the current ease of making Crypto payments, lead us to believe that RaaS will remain relevant in the threat landscape of the near future.