By Ronen Ahdut – Sr. CyOps Analyst
The Darknet is home to many underground hacking forums. In these forums, cybercriminals talk freely: sharing stories, tactics, success stories, and failures.
Their conduct allows us to peek into the politics and ethics of those groups and actors, as they talk about recent activities.
CyOps Lighthouse aims to shed a light on those dark places. Apart from the underground forums, we will also provide information regarding ongoing ransomware groups’ publications and worthy mentions from the last month.
Malware-as-a-service – MaaS
Malware has been around for a very long time, with the first “Animal” trojan seen around 1978. Since then, a great deal has changed.
If once the main goal was to simply infect a host with your malware, today it is more of a tool for the next goal – whether the goal is to spread on a network like a worm, to steal credentials, or even to drop another malware – their goal has changed.
And as we saw in the previous Lighthouse post, some malware like Trickbot is used only in “inner circles,” and is not available for the public for sale.
Trickbot is only one tool in the arsenal of its operators. The strongest confirmation for this notion can also be seen in the leaks, as Trickbot operators have completely shut down its servers after the Conti group decided to focus on the “BazarLoader” malware instead.
But those inner circles are only a fraction of the attacks that take place today. So, where and how do threat actors gain access to malware?
Similar to our monthly ransomware reports, we will try to shed more light on the booming market for malware, with the main focus on:
- Clearnet malware – Sold on Telegram, Discord, and public forums.
- Underground forums – Most of today’s malware is sold in this method.
- Inner circles – similar to the usage of Trickbot by Conti and other threat actors.
Clearnet Malware
Malware is often sold and used in the “Clearnet,” meaning you don’t need to have access to an underground forum, nor be invited to a shady marketplace. This malware is sold on an everyday platforms like Telegram or on forums that do not require entry fees or reputation from other forums (common in registration).
Examples of this can be seen in one of the most common and notorious info-stealers available today.
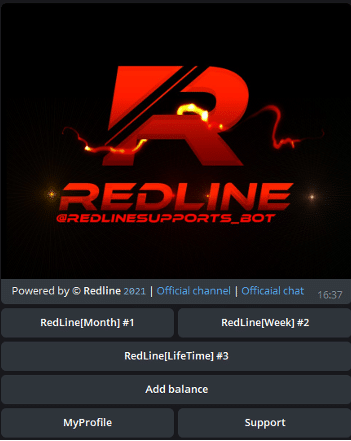
Redline Stealer
Redline can be purchased on forums, or directly via telegram, users will receive an executable to run their campaign, the service is sold as a subscription and the user is responsible for the distribution:
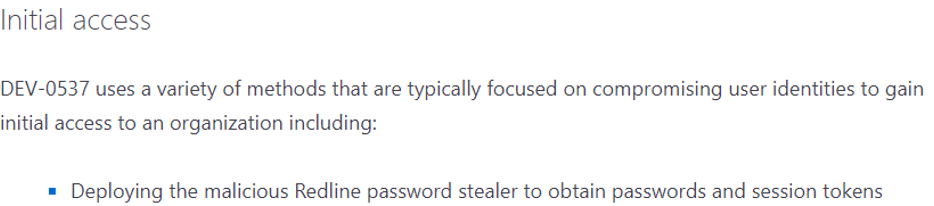
In a recent report from Microsoft regarding the breach by LAPSUS, Microsoft mentioned that LAPSUS used Redline stealer as an initial access vector:
See the entire post by Microsoft here.
CyOps’ Cyber Threat Intelligence (CTI) team has already covered Redline in the past, see our latest publication here.
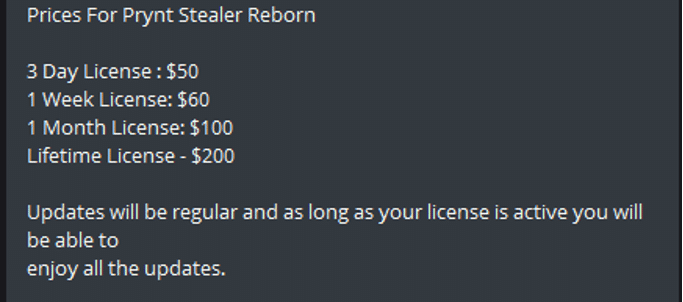
Apart from Redline, subscription-based malware is a relatively new but successful method. Here is another example from a new stealer called “Prynt Stealer Reborn” telegram channel:
Other malware is being sold in this method, but info stealers are probably the largest market at the moment.
Forums
Hacking forums are the main selling point for MaaS, but there is a difference from one to another, some are open for all, while other will require you to check your reputation in other notable forums, or pay a sum between 100 to 500 USD (registration alone).
Due to the fact that some of the forums are publicly online, and are hosted by legitimate companies, the activity on those forums is considered a bit “mild,” people do sell scamming and phishing tools, offer their coding abilities, but botnets and stealers are less common on them.
One of the most known forums was Raidforums. This forum had a vivid marketplace, and had one of the largest English-speaking communities.
The domain has been reportedly seized by the FBI, and the community now seeks alternatives.
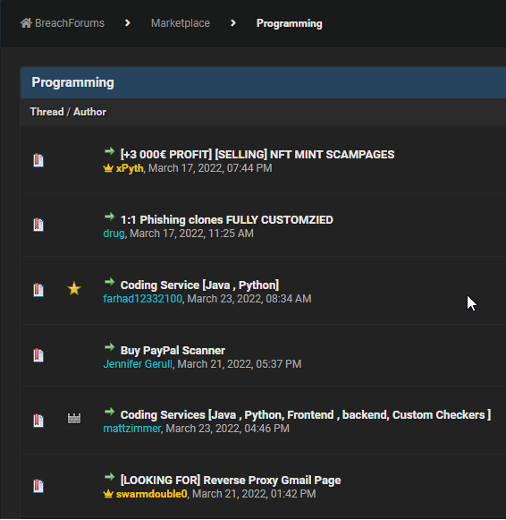
An example can be seen in the newly formed “Breached” forum, which aims to take the place of Raidforums. It is still new and not as well known as Raidforums.
Here is an example for a section in its marketplace:
Most of the “magic” happens on underground forums – ones that usually need Tor to connect to, and that registration is reviewed based on the user’s reputation, or on a crypto payment between 100 to 500 USD.
An example can be seen in XSS, a Russian-speaking forum where apart from ransomware, one can buy nearly every cybercrime-related necessity.
A note on Russian-speaking forums: the general conception is that as long as the activities are not aimed toward Russia, the government will (unofficially) turn a blind eye to these activities. This notion has been strengthened with the ties seen between Conti group and the FSB (the Russian equivalent of the FBI) in the recently seen Conti leaks.
This has led to a prospering market on those forums, which is less common on English-speaking ones. While many services are available, we will try to focus on Malware.
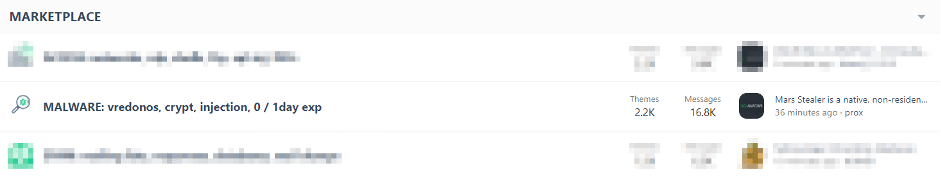
The XSS Marketplace offers a wide variety of malware, stealer, loaders, bankers, botnets – all can be found in the marketplace:
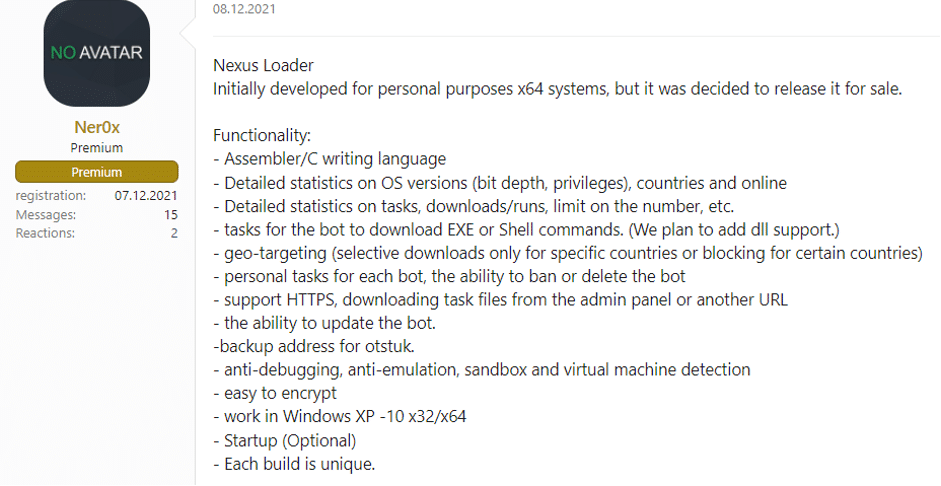
The seller will usually include the malware features and pictures like those in the examples below:
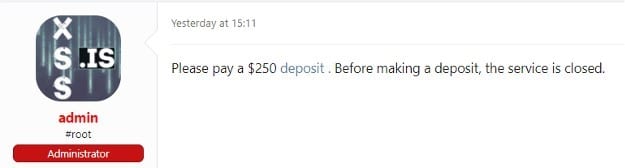
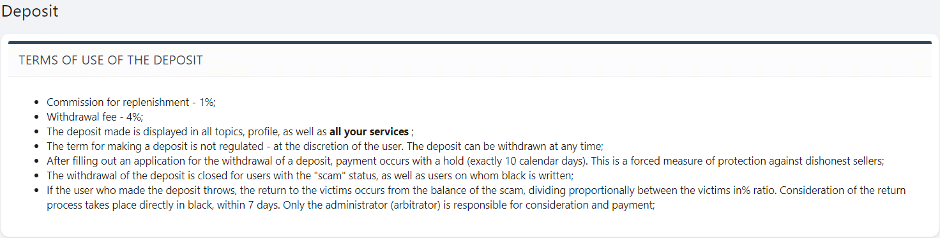
With all that it is for sellers to offer, how can one be sure that he will indeed receive what he paid for? Most forums will request the seller to issue a deposit for the forum before activating their service.
The deposit serves as a way to show that the seller is true to his intentions, and also if anything goes wrong, the admins could refund the buyer.
Here’s an example for a deposit section:
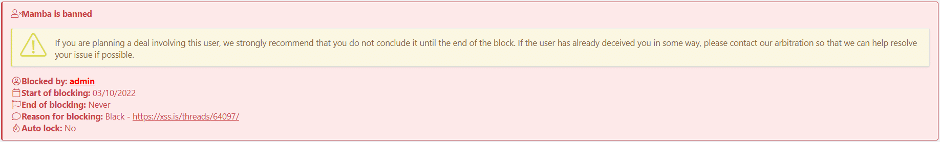
Forums have a section dedicated to these issues, where unsatisfied users try to solve their problem with the seller and forum admins. A seller that does not respond, or does not have a good argument, will be banned and a “scammer” tag will be added to their name, paid funds will be returned to the buyers:
There are more methods worthy of mentioning, like escrow service.
Escrow is a third party. The funds will be transferred to the escrow account and will be released once the goods are transferred to the customer’s satisfaction:
Another way will be that forum admins (or a known, trusted member) will vouch for the seller or the service:
Inner Circles
While many services and malware are available for purchase, some are reserved for the internal use of a threat actor, or they might be sold between them.
This has been previously seen with the resurfacing of Emotet with the help of Trickbot, the Conti group usage of BazarLoader, or either of them dropping different ransomware variants.
These are the top-tier malware, being constantly audited, upgraded, and serviced by entire teams. As shown in the previous Lighthouse post, they are being used only in those involving inner circles.
Conclusion
As we can see, many business models are available for the MaaS platforms.
While some choose to use Telegram for their distribution, others will publish their work in underground forums. Those forums show us a glimpse of a delicate world of underground commerce, in a world of anonymity where reputation is sometimes more important than actually having the funds.
The inner-circle malware world will remain, unfortunately, hidden. Only events like the Conti leaks or an arrest will show us how those groups connect and communicate.
MaaS has been on a constant rise. It offers the unexperienced “Skid” a step into what was once the world of experienced coders and underground hackers, and all this for a reasonable price.
Together with malware source codes constantly being leaked online, threat actors use them to create their variant and then offer it for sale on the platforms seen above.
Similar to RaaS, the profitability for both parties in the MaaS platform is what makes this market activity rise in recent years, and there does not seem to be a reason for it to decline soon.