CyOps Lighthouse: Raccoon stealer
The Darknet is home to many underground hacking forums. In these forums, cybercriminals talk freely: Sharing stories, tactics, success stories, and failures.
Their conduct allows us to peek into the politics and ethics of those groups and actors, as they talk about recent activities.
CyOps Lighthouse aims to shed light on those dark places. Apart from the underground forums, we will also provide information regarding ongoing ransomware groups’ publications and worthy mentions from the last month.
Raccoon stealer – the end?
Executive summary:
Raccoon stealer is one of the most successful MAAS.
The malware is being offered for sale on underground forums as well as publicly in telegram/clear forums.
On October 25th the FBI published that it has issued an indictment for a 26 year old Ukrainian, thought to be one of the key developers of Raccoon stealer.
Introduction:
Raccoon has been introduced around April 2019 in multiple forums, is offers multiple info-stealing capabilities at a reasonable price:
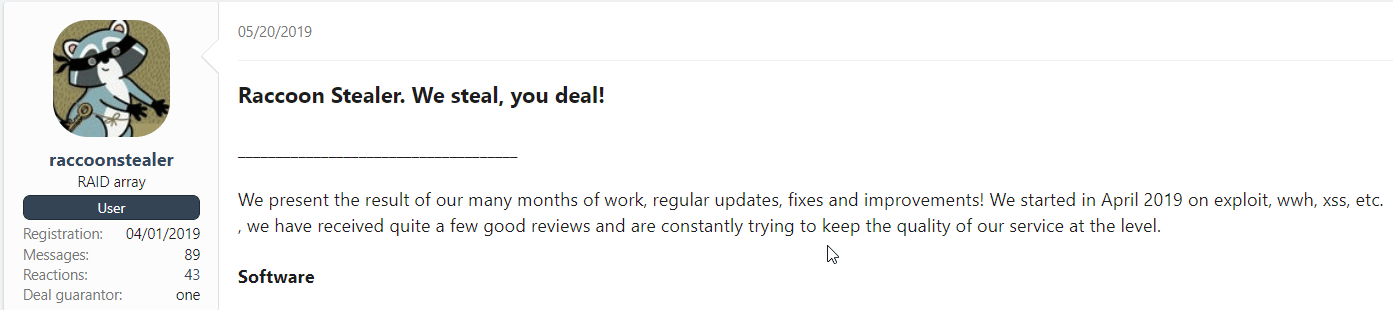
Since 2019, it has been updated multiple times, with the latest Raccoon V2 introduced on June 30th, 2022 (has also been updated since).
The group has disclosed that on March 2022, the project will be closed, this is due to the “Special operation” (Russia – Ukraine war) and to the fact that one of their developers is “no longer with us,” while all assumed this meant the operator has died in the war, a recent publication had shed more light on the situation.

In their official unsealed indictment charges, the FBI had related a 26-year-old Ukrainian in being one of the operators of Raccoon stealer, it is also noted that he has been arrested in the Netherlands since March 2022, the same date as the “unfortunate event” that led to the operation halt.
Raccoon V2:
Almost three months after Mark was arrested, Raccoon operators relaunched their activity:
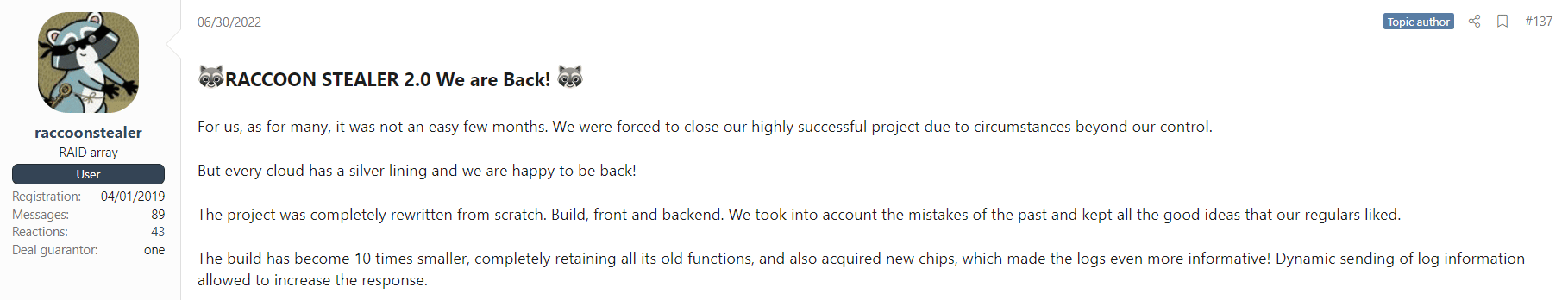
The group mentions a newly built malware with added capabilities and features, a new web panel, and everything the original stealer had- built from scratch.
We can now correlate the new version to the arrest, the regrouping and building all from scratch were probably not due to a lost computer, but an attempt to protect the project from the US authorities.
Conclusions:
The Department of Justice (DOJ) had also shared that Mr. Sokolovsky had over two million infected hosts, and more than five million credentials, all of the related findings are now available on a dedicated website the DOJ had built:
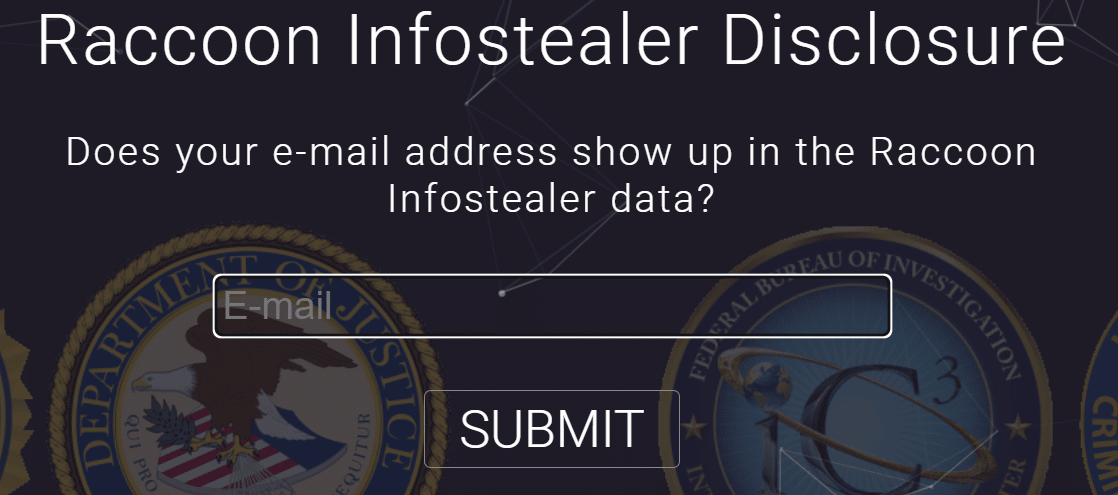
While the group has successfully recovered from the arrest in the form of Raccoon V2, it is unclear how the news will affect the team’s operations, we asses based on the popularity of the stealer, and ability to operate freely that this might have a short-term effect on the operation, but Raccoon will remain one of the most profitable, and prolific info stealer.
*Update – Raccoon group’s official response as shared in “Exploit” forum:
“The partner disappeared at the time of the start of the NWO. All they knew about him was that he lives in Kyiv and at the moment the ‘special operation’ began, the group lost contact with him.”
However, the team never claimed that he was killed.
The Raccoons are glad that everything is fine with him and at the same time they talk about the inability to confirm the identity of the guy who may be involved in the project.
The Raccoons also said that “Raccoon Stealer v1.0’ customers have nothing to worry about, since no one has stored data on the servers, and ‘Raccoon Stealer v2.0’ continues to work with new servers located in a safe place.”