Monthly Ransomware activity – October 2021
Written by: Maor Huli
For October, we will introduce the following ransomware:
- Encriptar
- Apostle
- STOP
- JCrypt
- J3ster
- Foxxy
- Whitehorse
- Dharma
EXECUTIVE SUMMARY
Ransomware gangs and evolution
As we know, Ransomware is a type of malware that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid.
Many new ransomware variants that we are familiar with right now were less sophisticated in the past. As each is updated by its publisher, the name of the specific variant might change, but it is usually based on previous existing ransowmares.
Here are a few examples of ransomware evolution by variants:
| Ransomware name | Known names | Successor of | Ransomware group | Group Region |
| REvil | Sodinokibi | GandCrab | REvil | Russia |
| Grief | DoppelPaymer | BitPaymer | Evil Corp | Russia |
| Macaw | Hades & Phoenix | WastedLocker | Evil Corp | Russia |
| Egregor | Sekhmet | Maze\ChaCha | Maze | Unknown |
| BlackMatter | DarkSide | DarkSide | DarkSide | Russia |
| Groove | Payload | Babuk\Vasa Locker | Babyk | Russia |
| XingLocker | AstroLocker | MountLocker | Astro Locker | China |
| Karma | Nefilim | Nemty | Saffron-Wolf | Unkown |
| Conti | Ryuk | Ryuk | Wizard Spider | Russia |
We gathered a few articles about ransomware around the globe:
https://www.zdnet.com/article/fbi-cuba-ransomware-hit-49-critical-infrastructure-organizations/
- https://www.thesundaily.my/home/tackling-the-ransomware-risk-to-enterprises-in-malaysia-FC8631557
- https://www.infosecurity-magazine.com/news/ransomware-victims-pay-700k-extra/
- https://www.swissinfo.ch/eng/ransomware-attacks-on-the-rise-in-switzerland/47164950
Lately, more and more ransomware variants are using additional malware to help spread within the attacked organizations. Many of the additional malware are mostly Trojan bankers that help the exfiltration process, and some are used to spread additional attack campaigns. Overall, however, all of the attacks are being used for one main reason – money.
https://www.cynet.com/attack-techniques-hands-on/quakbot-strikes-with-quaknightmare-exploitation
- https://www.cynet.com/attack-techniques-hands-on/cynet-vs-hafnium/
- https://www.cynet.com/understanding-squirrelwaffle/
- https://www.cynet.com/attack-techniques-hands-on/into-the-cryptoverse-the-intersection-of-cryptocurrency-and-cybersecurity/
Bleeping Computer is the most up-to-date website that summarizes the newest ransomware variants. Cynet’s Orion Threat Research Team is an integral part of Cynet’s research efforts. The Orion team works around the clock to add more rules that help strengthen Cynet 360’s detection capabilities. Part of Orion team’s work involves following Bleeping Computer to scan for recent posts about new variant threats. Our goal is to detect every threat that emerges.
In this article, we have summarized ransomware variants from October based on Bleeping Computer. We will present recent ransomware and how Cynet 360 platform detects them via several mechanisms.
CYNET 360 VS RANSOMWARE
- Observed since: Late 2021
- Ransomware encryption method: AES + RSA.
- Ransomware extension: .solaso
- Ransomware note: _READ_ME_TO_RECOVER_YOUR_FILES.txt
- Sample hash: bd136b3fde933505cf3740c3800a5007e3a94a2d31f28416b04c212dcb0669b6
Cynet 360 Detections:
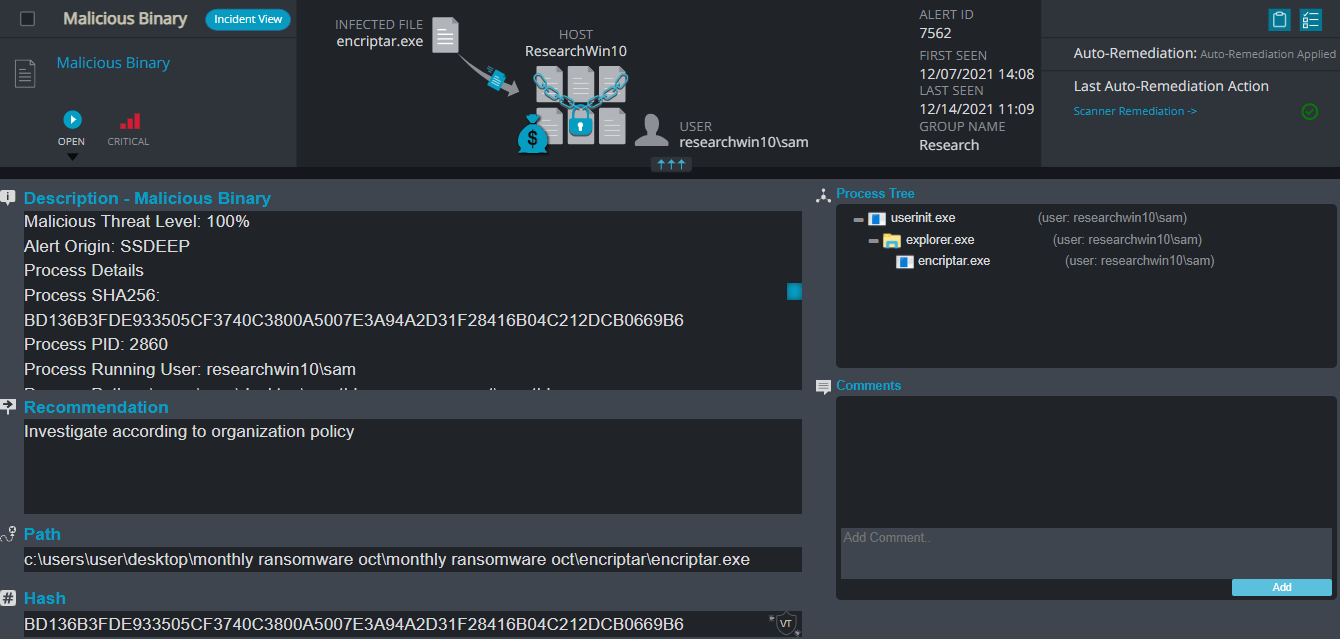
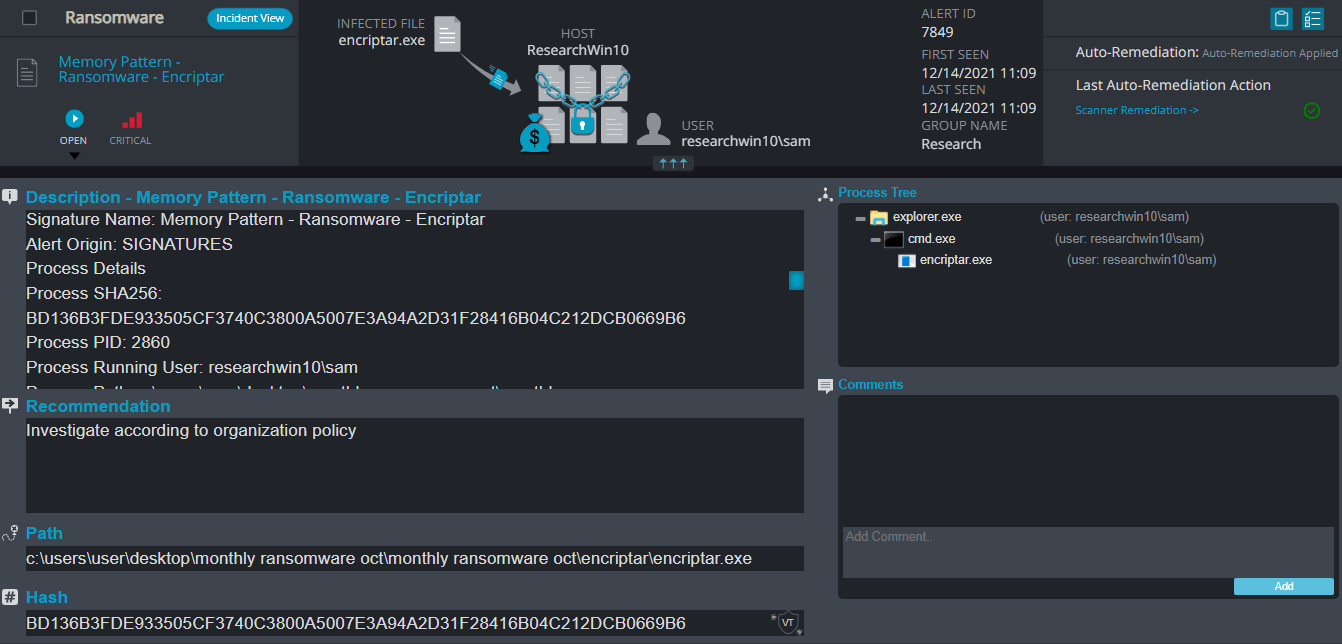
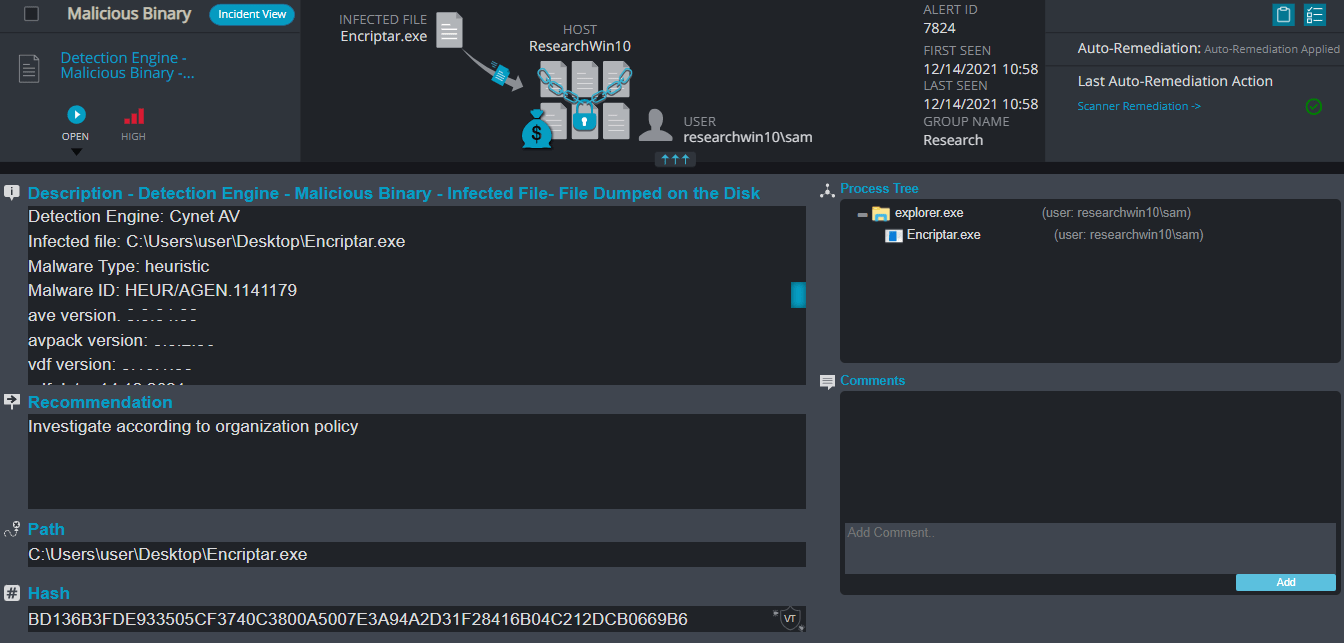
Encriptar ransomware renames the encrypted files with .solaso in the extension:
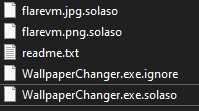
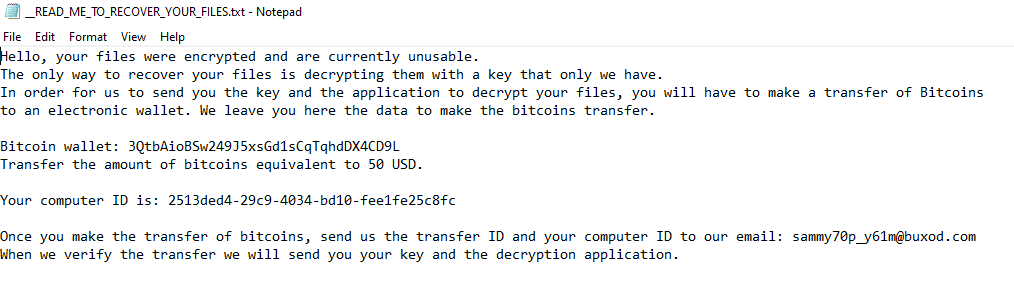
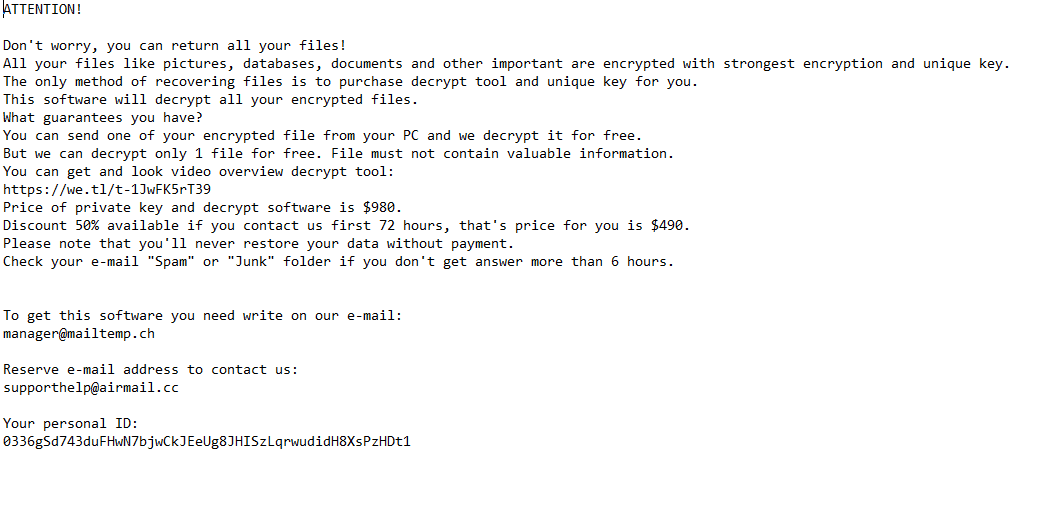
Once a computer’s files have been encrypted and renamed, it drops a note as: _READ_ME_TO_RECOVER_YOUR_FILES.txt.
Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note has the Bitcoin address and the threat actors’ email, the ransom demand and the instructions on how to pay it.

STOP Ransomware
- Observed since: December 2018
- Ransomware encryption method: AES + RSA.
- Ransomware extension: .tisc
- Ransomware note: _readme.txt
- Sample hash: c6f3fde5054f139837df405788d1d07473781ee1950e5f1e366b1fb0e7a4b867
Cynet 360 Detections:
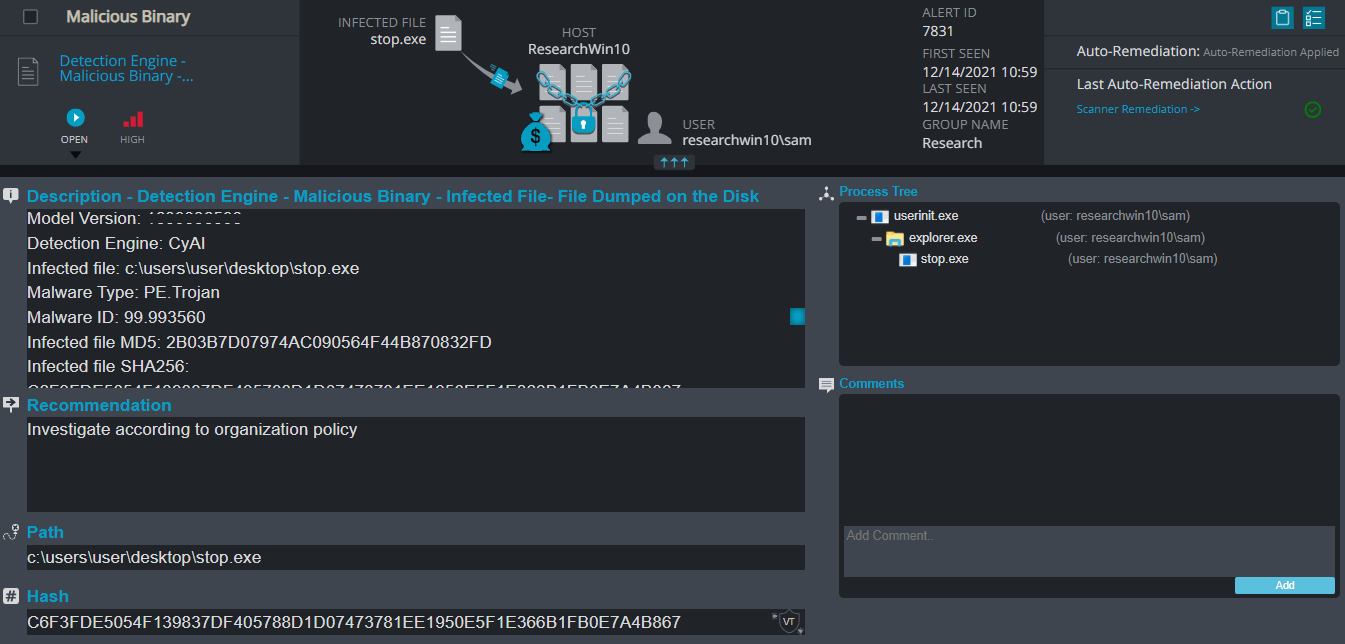
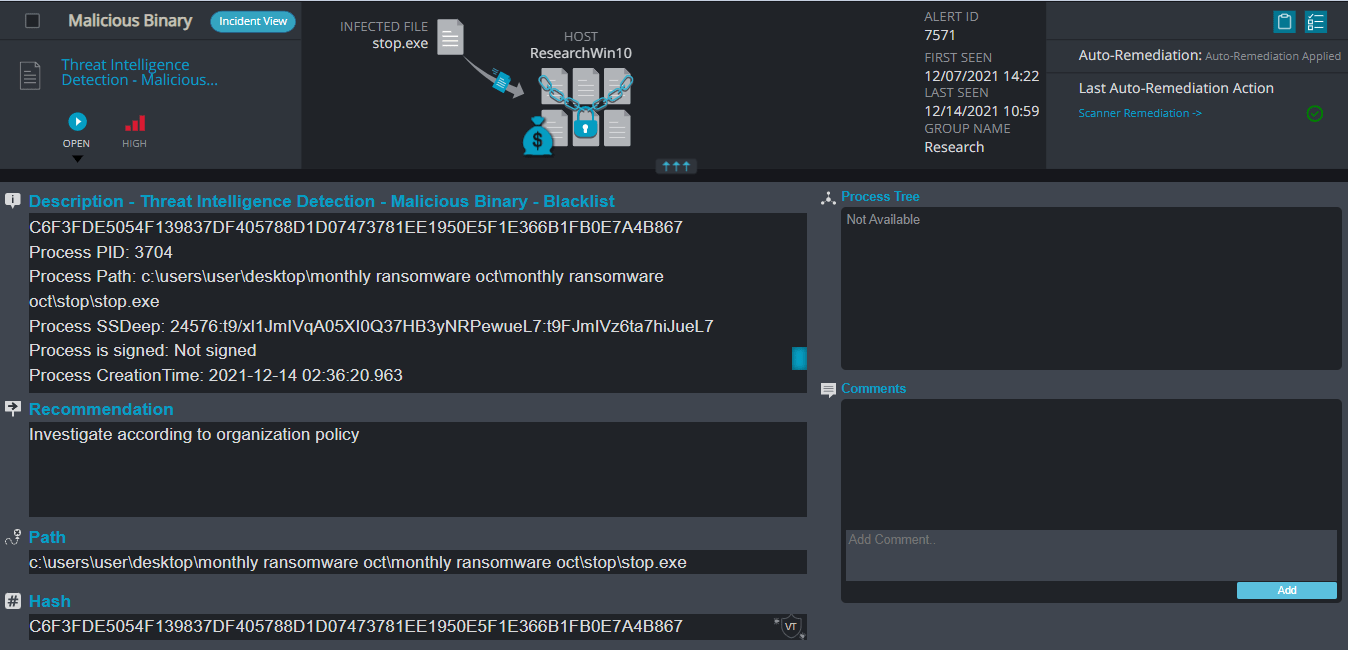
STOP ransomware renames the encrypted files with a .tisc extension for each file:
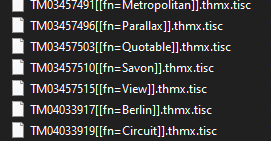
Once a computer’s files have been encrypted and renamed, it drops a note as a text (.txt) file named _readme.txt. In the text file it writes instructions on how to pay to get the encrypted files back.

- Observed since: Dec 2020
- Ransomware encryption method: RSA + AES.
- Ransomware extension: .poison
- Ransomware note: __RECOVER__FILES__.poison.txt
- Sample hash: 15464657cfae95a326426093c9e12daab54bd9f61c3bc63a2cf5abe975a0e278
Cynet 360 Detections:
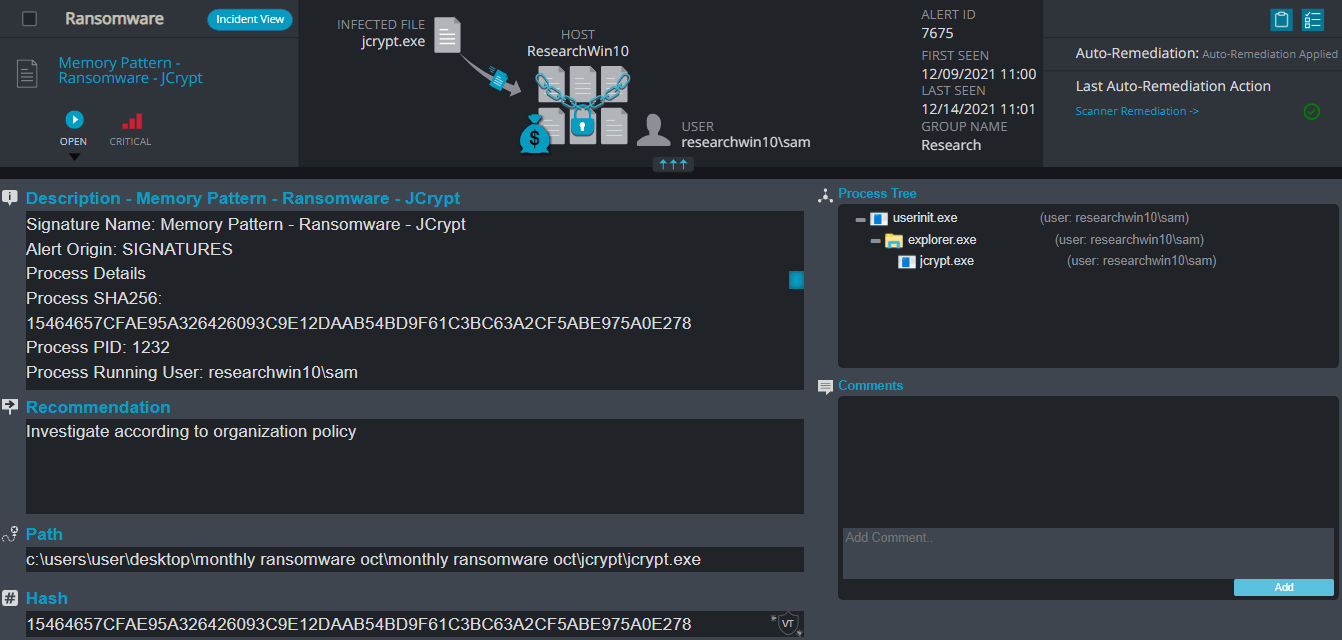
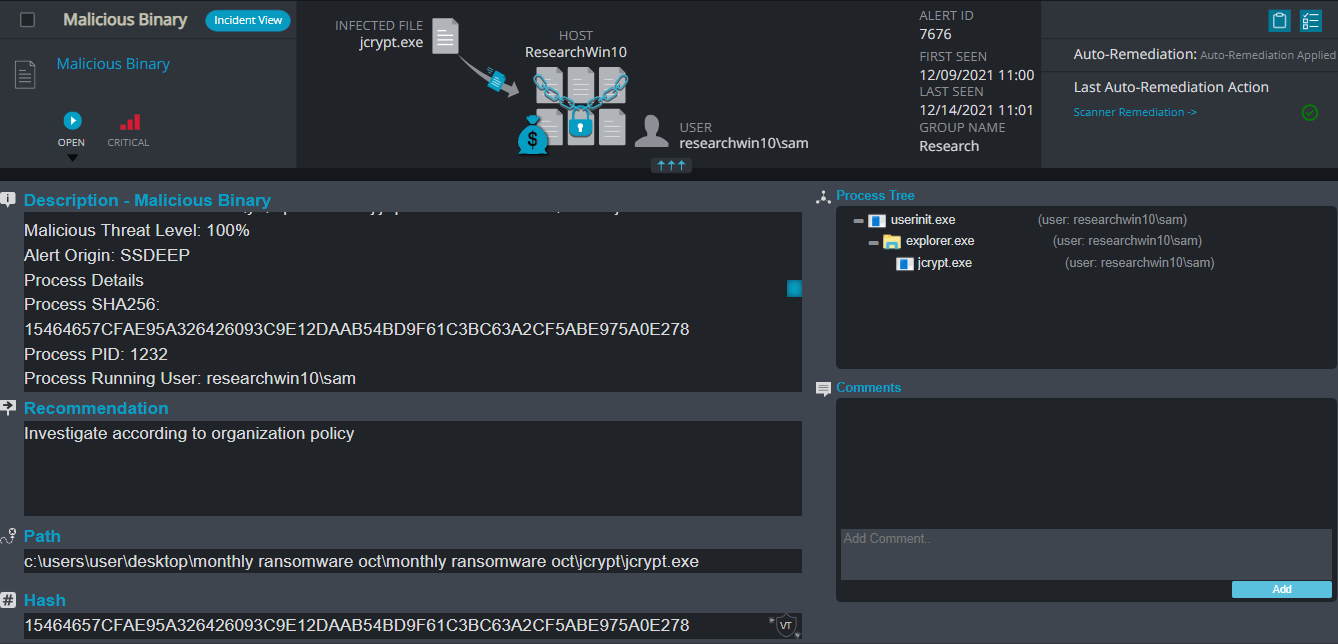
JCrypt Overview (change overview)
JCrypt ransomware, much like the recent variants that are based on the same Ransomware family, renames the encrypted files with .poison in the extension for each file:
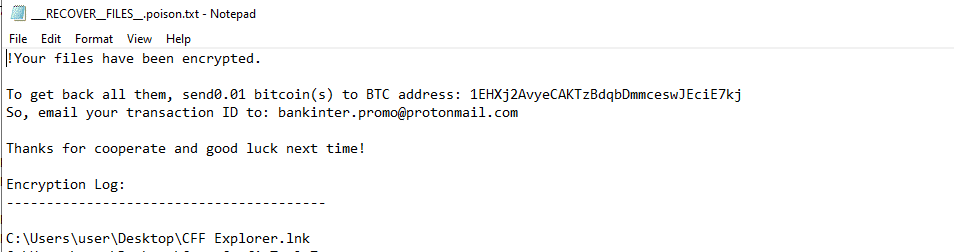
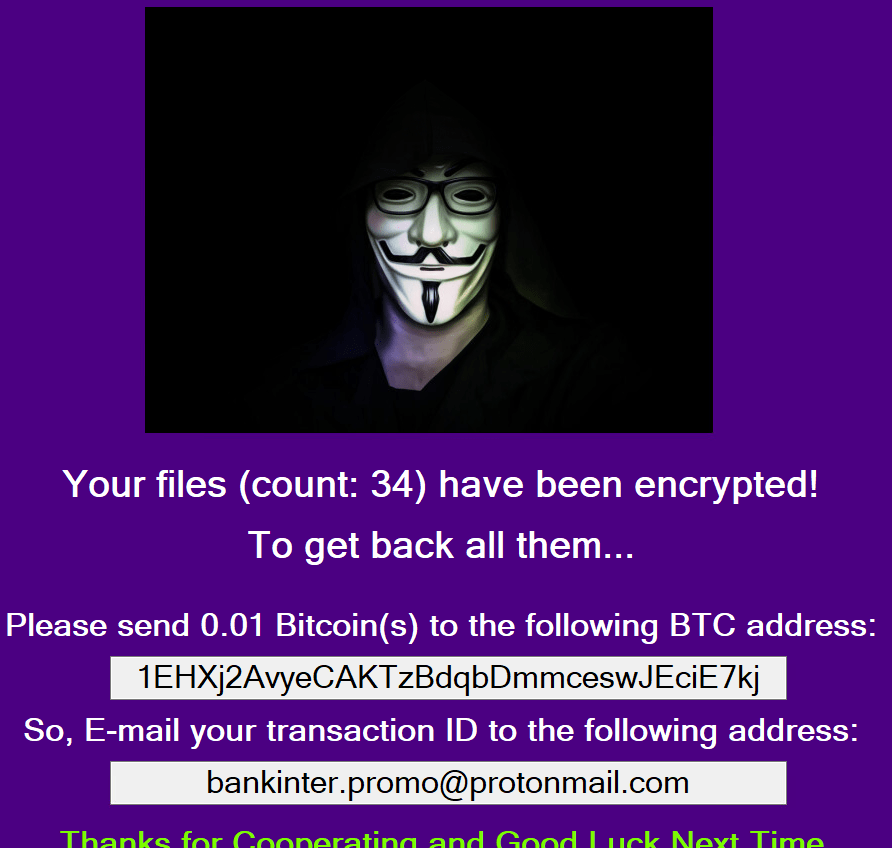
Once a computer’s files have been completely encrypted and renamed, it pops up a message with the ransomware note that contains the attacker’s Bitcoin and email address.
- Observed since: late 2021
- Ransomware encryption method: RSA + AES.
- Ransomware extension: .J3ster
- Ransomware note: J3ster ReadMe.txt
- Sample hash: 3ce01febbc3dcc8e5a653006332016d6086202480b14016da2916a9348b66f51
Cynet 360 Detections:
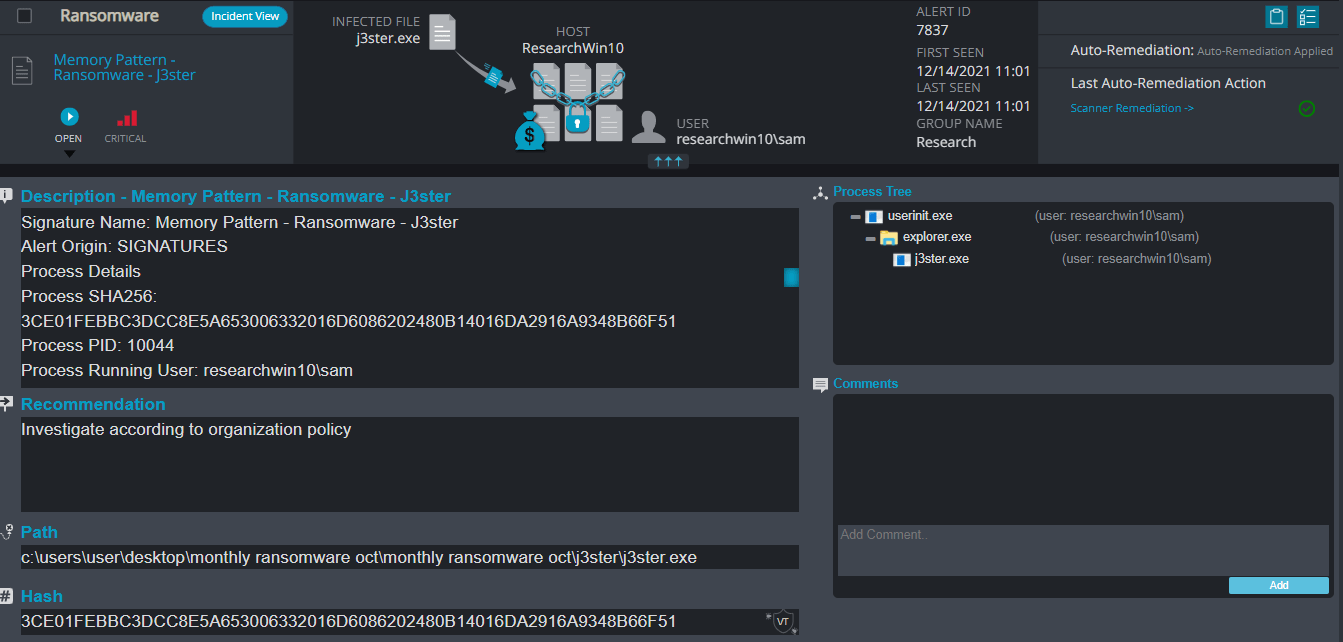
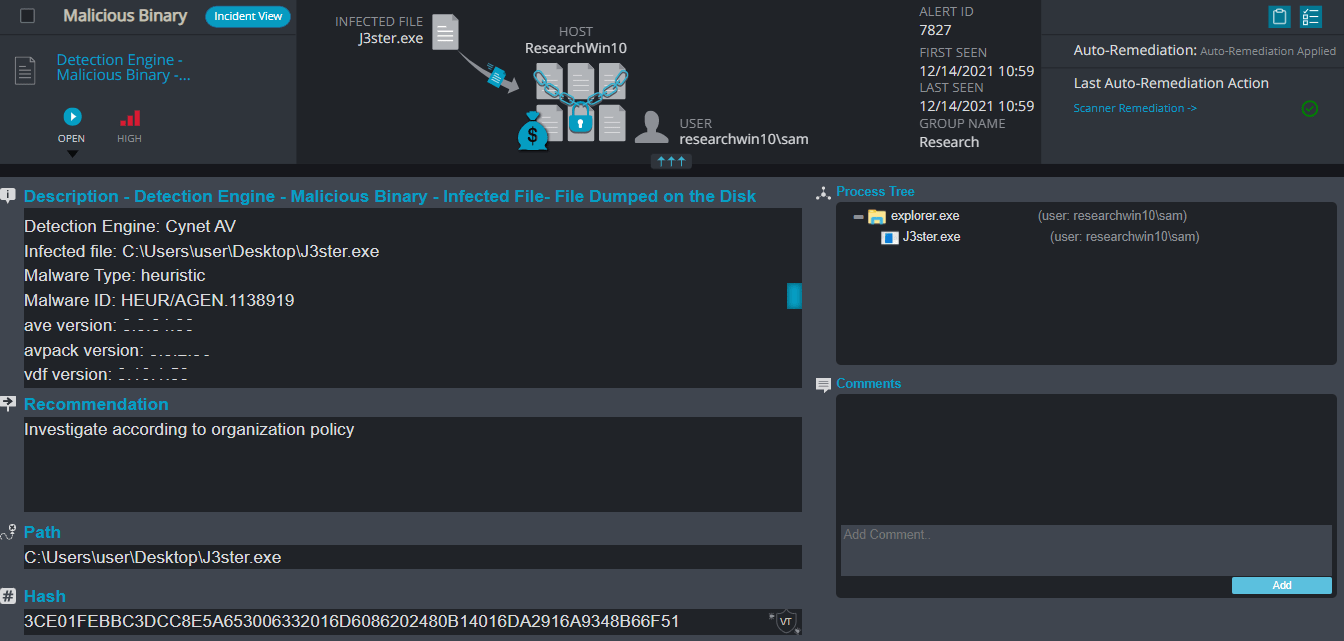
After execution, J3ster ransomware renames the encrypted files with .J3ster for each file:
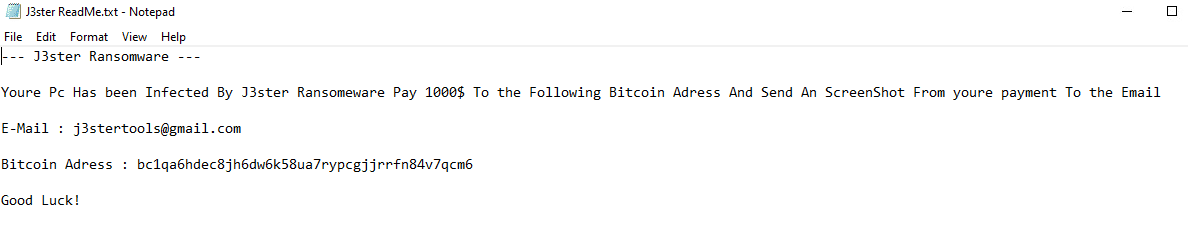
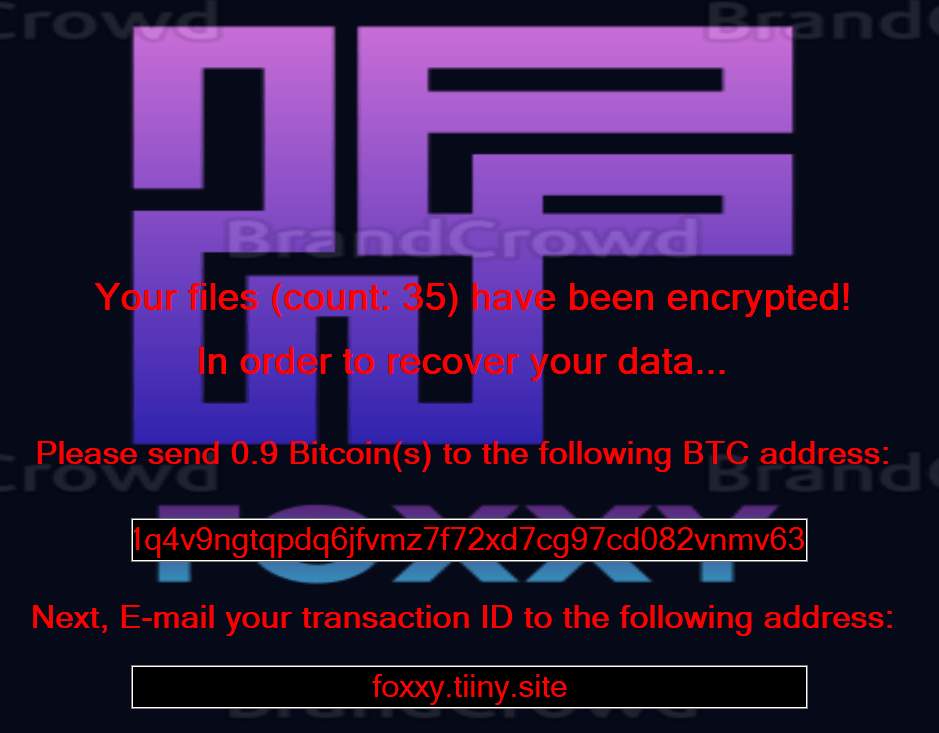
It also includes a demand for a ransom of $1000 in Bitcoin. The note contains the attacker’s Bitcoin address and the email, and the ransomware changes the background image:


- Observed since: Late 2021
- Ransomware encryption method: RSA + AES.
- Ransomware extension: .foxxy
- Ransomware note: __RECOVER__FILES__.foxxy.txt
- Sample hash: cc05003909a8020086f5a1620cc48254ff3bc1e0af8608bbfa810ed95fe75ca9
Cynet 360 Detections:
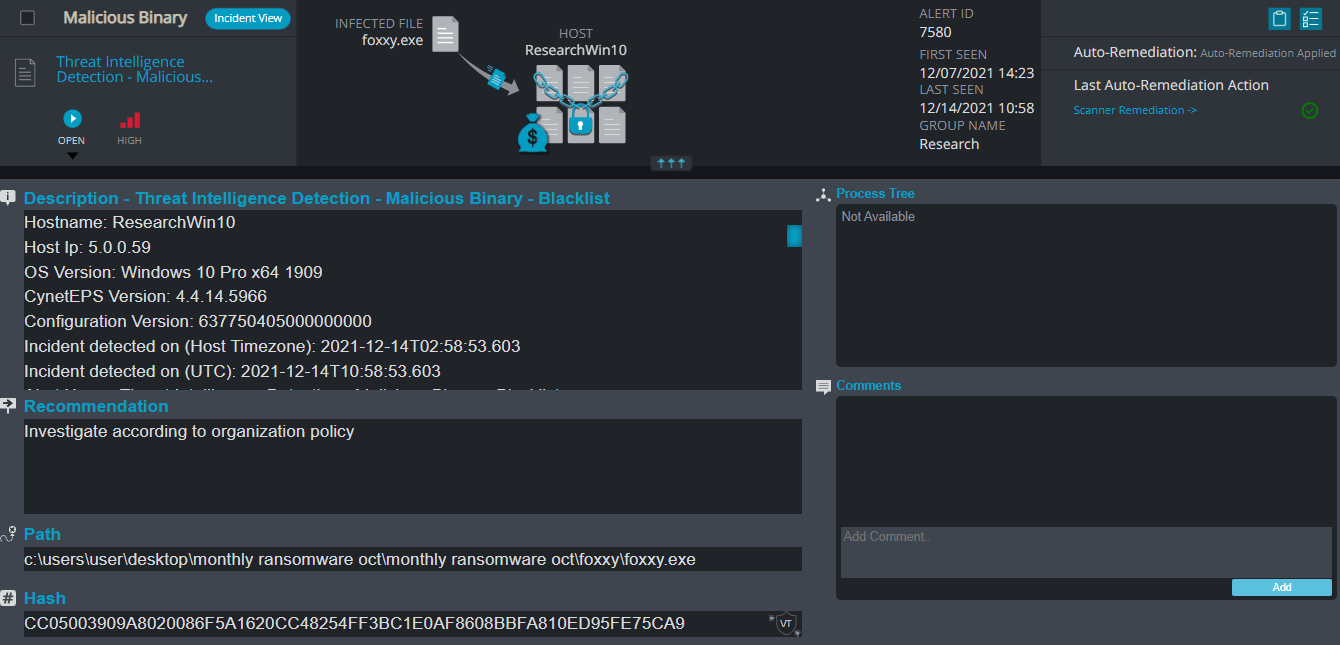
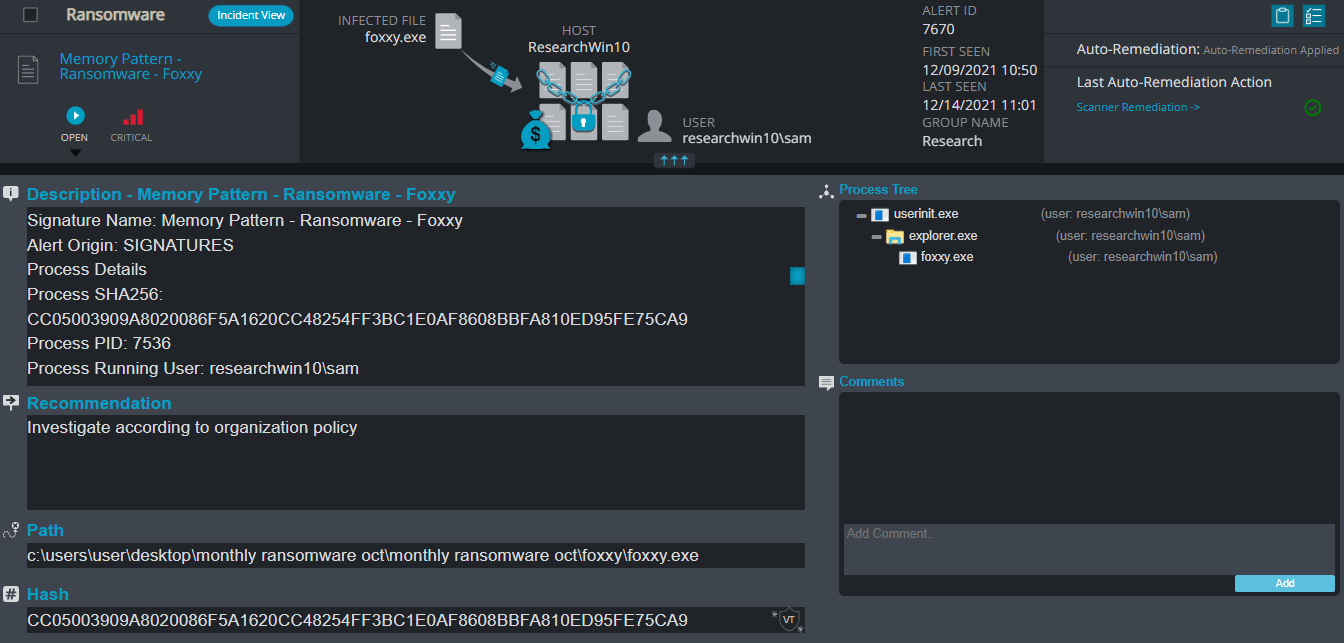
Foxxy Overview
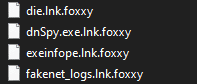
After execution, Foxxy ransomware renames the encrypted files with .foxxy in the extension for each file:
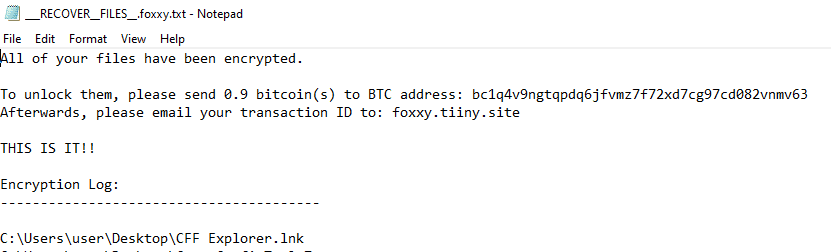
Once a computer’s files have been completely encrypted and renamed, it pops up a message with the ransomware note that contains the attacker’s Bitcoin and email address:
- Observed since: Early 2021
- Ransomware encryption method: RSA
- Ransomware extension: .WhiteHorse
- Ransomware note: #Decrypt#.txt
- Sample hash: 5378249a2b439e92691fb87751adc9fc4e2dea1792309d695b7f1d9c6887b09d
Cynet 360 Detections:
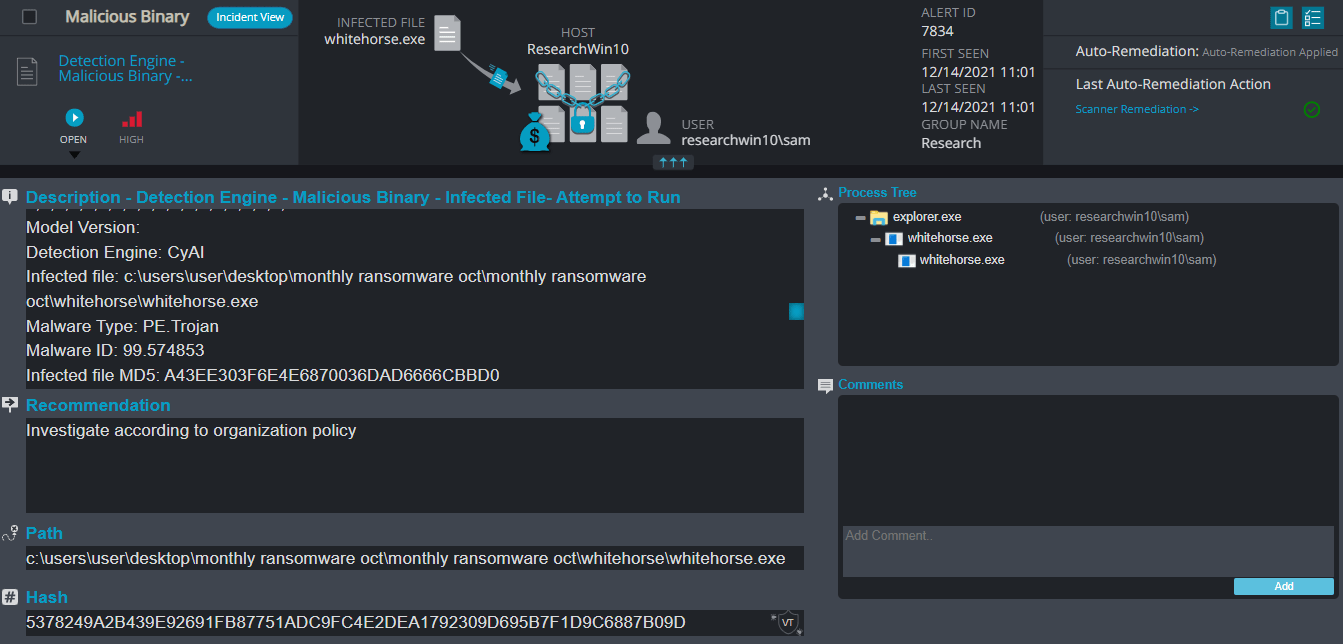
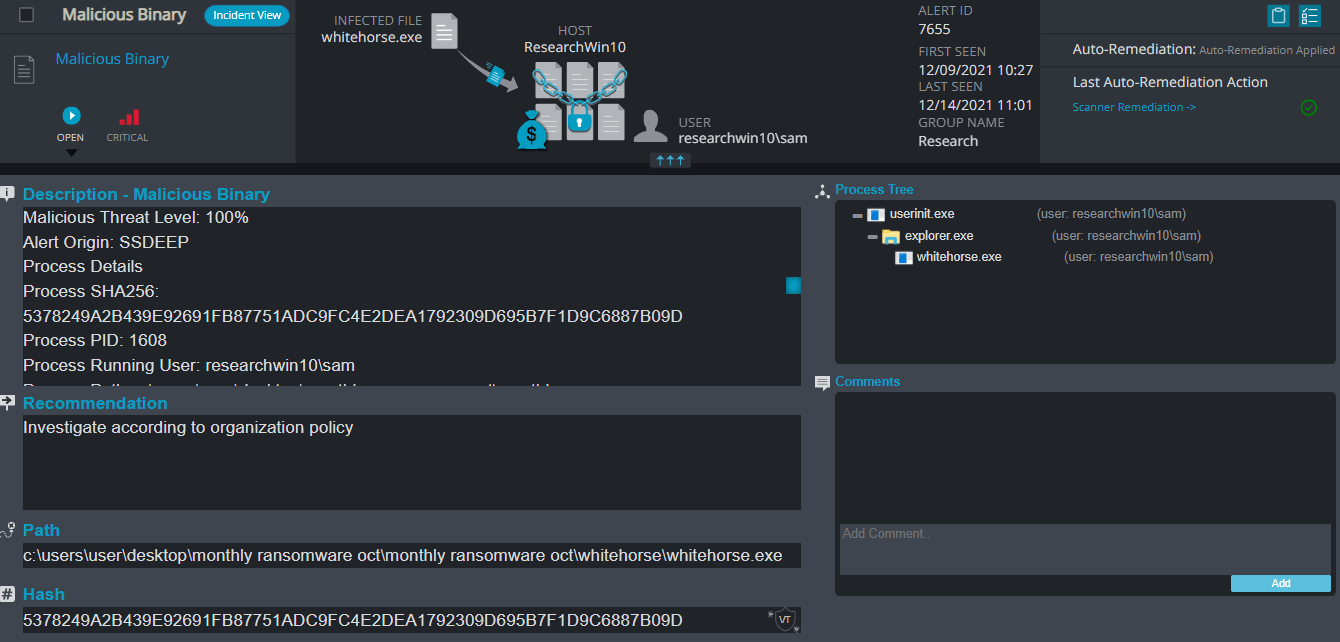
After execution, Whitehorse ransomware renames the encrypted files with .WhiteHorse in the extension for each file:
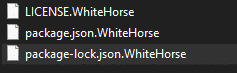
Once a computer’s files have been encrypted and renamed, it drops the ransomware note as a text file named #Decrypt#.txt in the victim’s encrypted folders, information on how to decrypt the files, and the attacker’s contact details.
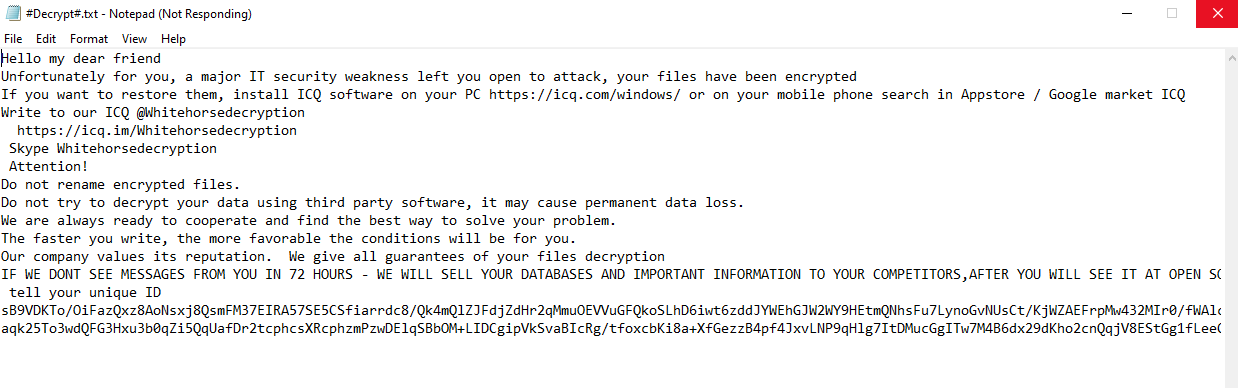

In addition, when trying to terminate the ransomware process, Whitehorse ransomware makes it impossible to use the PC, can’t open certain folders, access files and eventually, explorer.exe stop responding.
- Observed since: 2016
- Ransomware encryption method: RC4.
- Ransomware extension: .id-[A-Z0-9]{8}[email protected]
- Ransomware note:
- Sample hash: db0111038f5f8a362537694e72ee1b18f35a3d56beaca8284c8656624a966af4
Cynet 360 Detections:
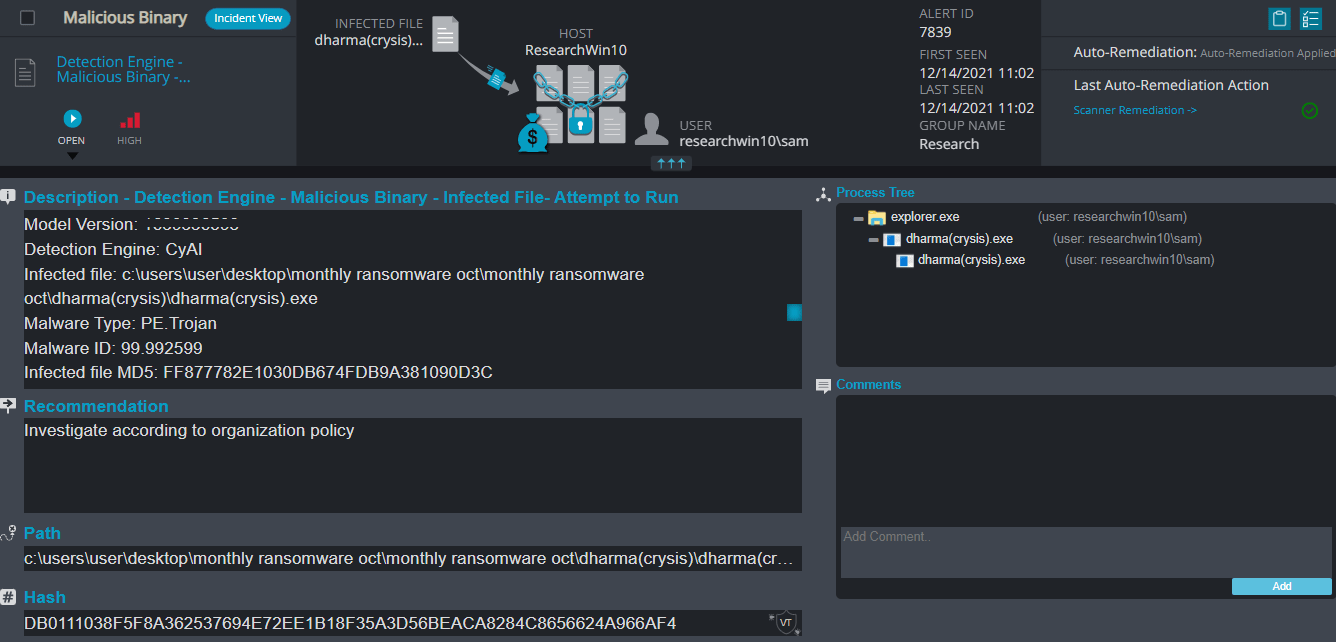
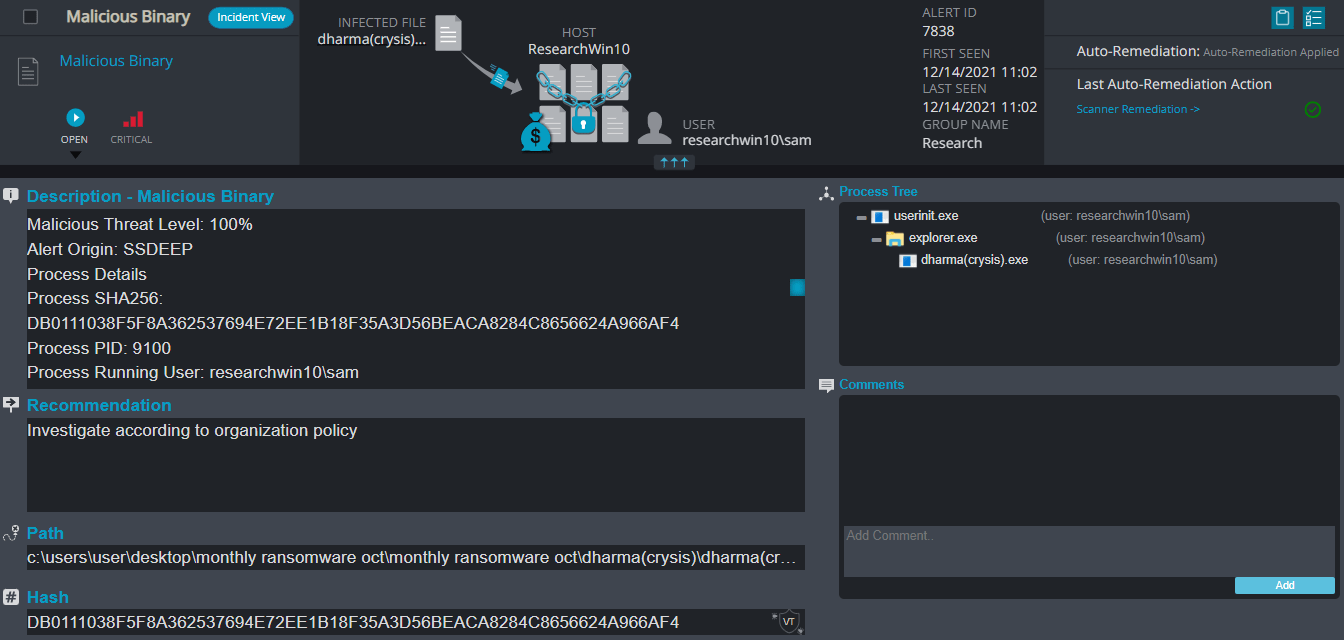
After execution, Dharma ransomware renames the encrypted files with “.id-[A-Z0-9]{8}[email protected]” in the extension for each file:
To contact the attackers, the user needs to send an email to the address in the new file extension for more details.
CYNET VARIOUS MECHANISMS
- AV/AI – This alert triggers when Cynet’s AV/AI engine detects a malicious file that was either dumped on the disk or executed
- Malicious Binary – This alert triggers when Cynet detects a file that is flagged as malicious in Cynet’s EPS (endpoint scanner) built-in threat intelligence database. This database contains only critical IoCs (such as IOCs of ransomware, hacking tools, etc.).
- Memory Pattern – This alert triggers when Cynet detects memory strings that are associated with Malware or with malicious files
- Ransomware Heuristic – This alert triggers when Cynet detects suspicious behavior which can be associated with Ransomware (such as changing file extensions to “.Lock”).
- Malicious Binary – Process Create Malicious File – This alert triggers when Cynet detects a process that creates a file that is either flagged as malicious in Cynet’s Threat Intelligence database, or associated with suspicious patterns (such as loaded to sensitive directories).
- Process Monitoring – This alert triggers when a process runs with certain parameters which can indicate suspicious activity (for example, a vssadmin with suspicious parameters such as delete shadow copies).
- Threat Intelligence Detection – Malicious Binary – This alert triggers when Cynet detects a file that is flagged as malicious in Cynet’s internal threat intelligence database.