Recent Escalations in Cyberattacks in Italy Prove the Coronavirus Impact on Cybersecurity – Acting as a Warning for CISOs Worldwide
The global Coronavirus epidemic impacts economies worldwide, creating a new reality in which many employees are working from home, forcing organizations to allow mass remote connections to internal work resources. Cynet not only shares with the public new insights on how threat actors are maliciously leveraging this situation, based on threat data from our customers we have aggregated and analyzed, but also has launched a dedicated offering to assist organizations in this challenging time.
We see two main trends:
- Attempts to capture employee remote credential
- Weaponized emails.
While the threat data is taken from our install in Italy, the events of the last several weeks show us that other countries will soon follow suit in respect to the increasing Coronavirus spread. We advise CISOs and other security decision makers to take this data into account in order to be better prepared for what we anticipate is going to rapidly become the new threat landscape.
Remote User Credential Theft
The rationale behind the increase in these attacks is simple – mass working over remote connection equals mass remote login activity, mostly over private insecure machines with user accounts that have never done so before, making remote login credentials an easy target for attackers.
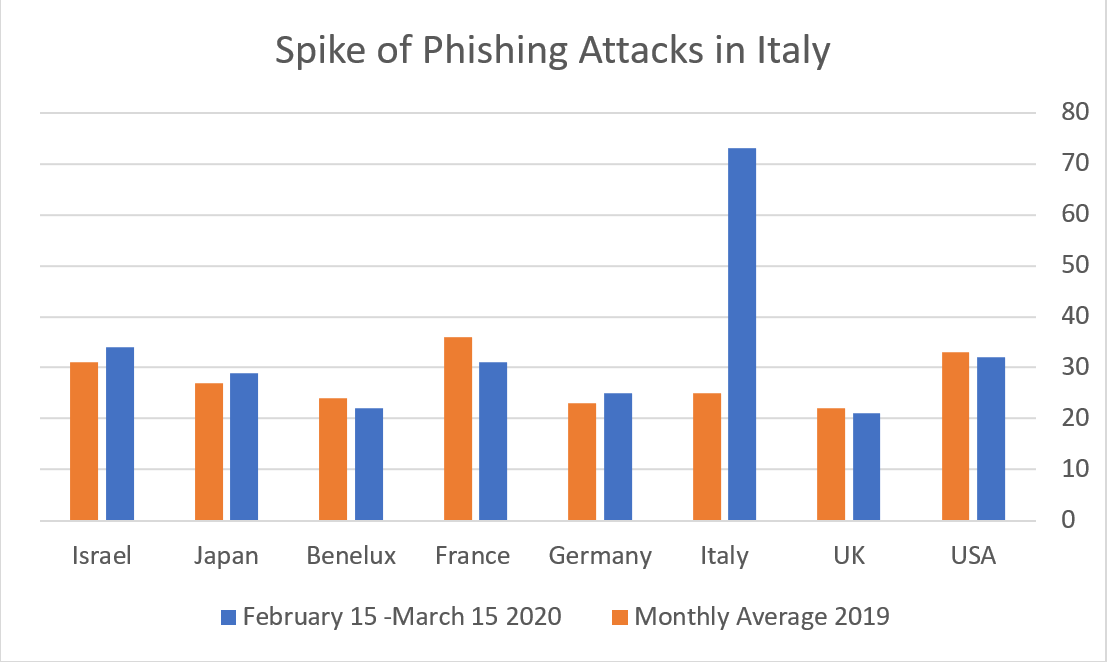
The following chart shows the spike in Phishing attacks in Italy over the last month in comparison with other territories:
In addition, we have spotted a similar increase in detected anomalous logins to our Italian customers’ environments:
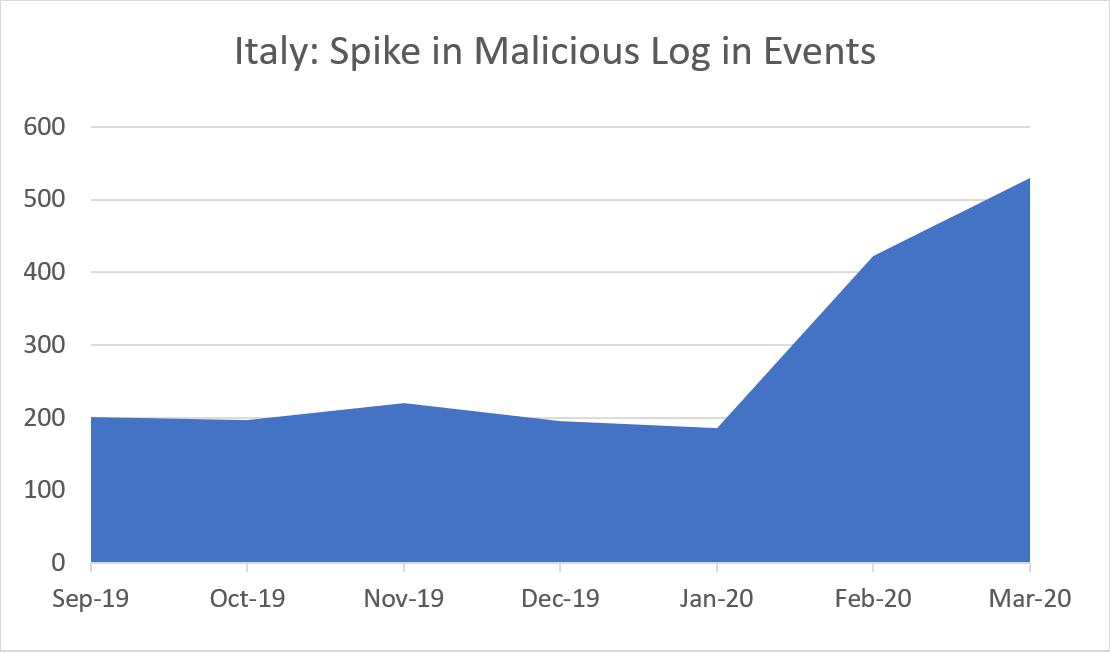 Further review of the graphs reveals a closer relationship between them, indicating that they are both indeed related to remote credential theft.
Further review of the graphs reveals a closer relationship between them, indicating that they are both indeed related to remote credential theft.
Weaponized Email Attacks
Working from home typically takes place on personal devices, that in most cases lack protection.
The following graph shows a spike in weaponized email attacks:
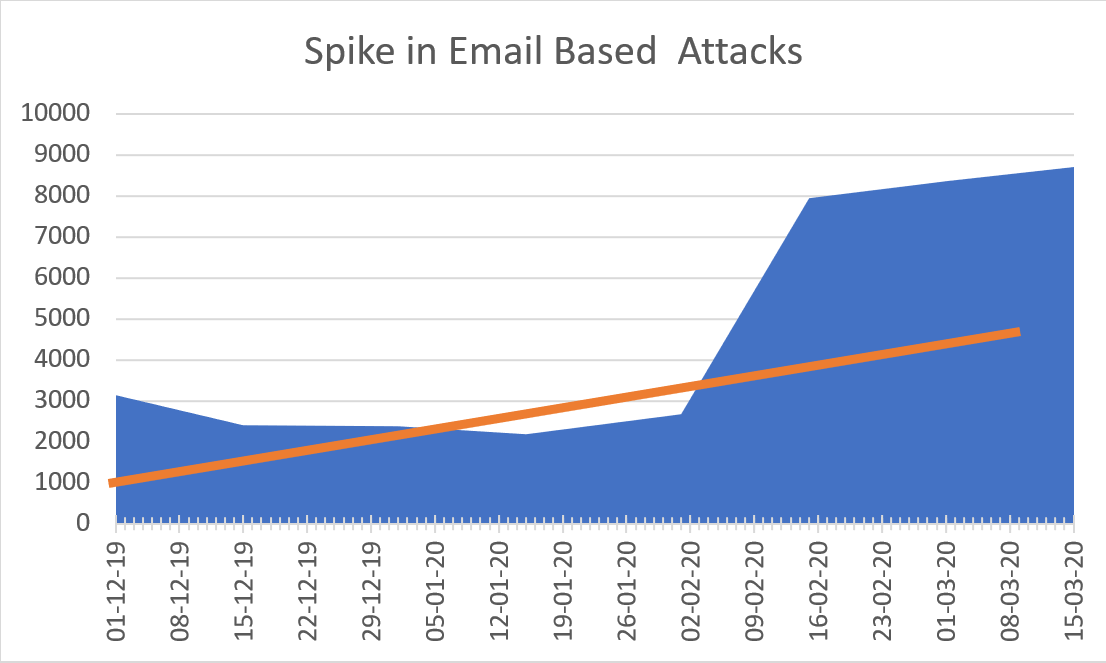
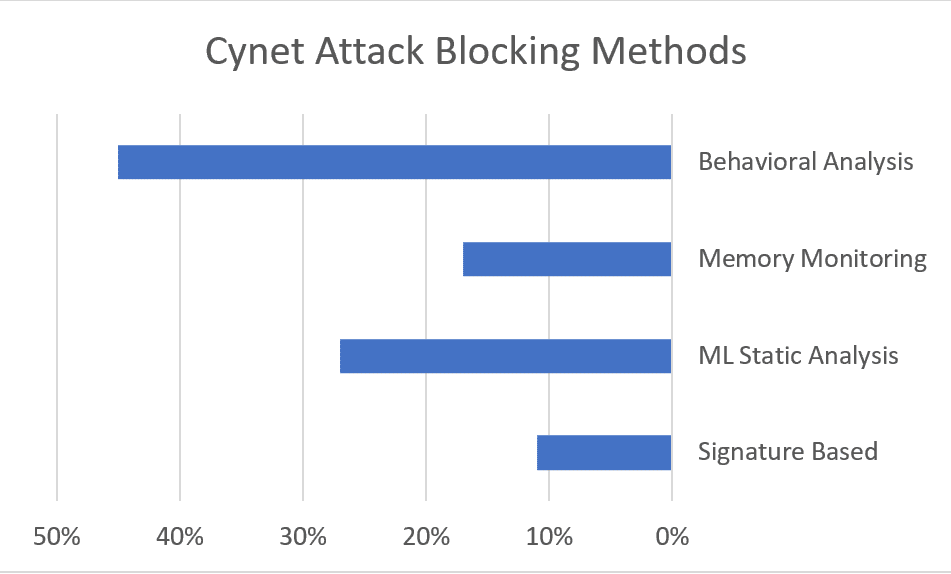
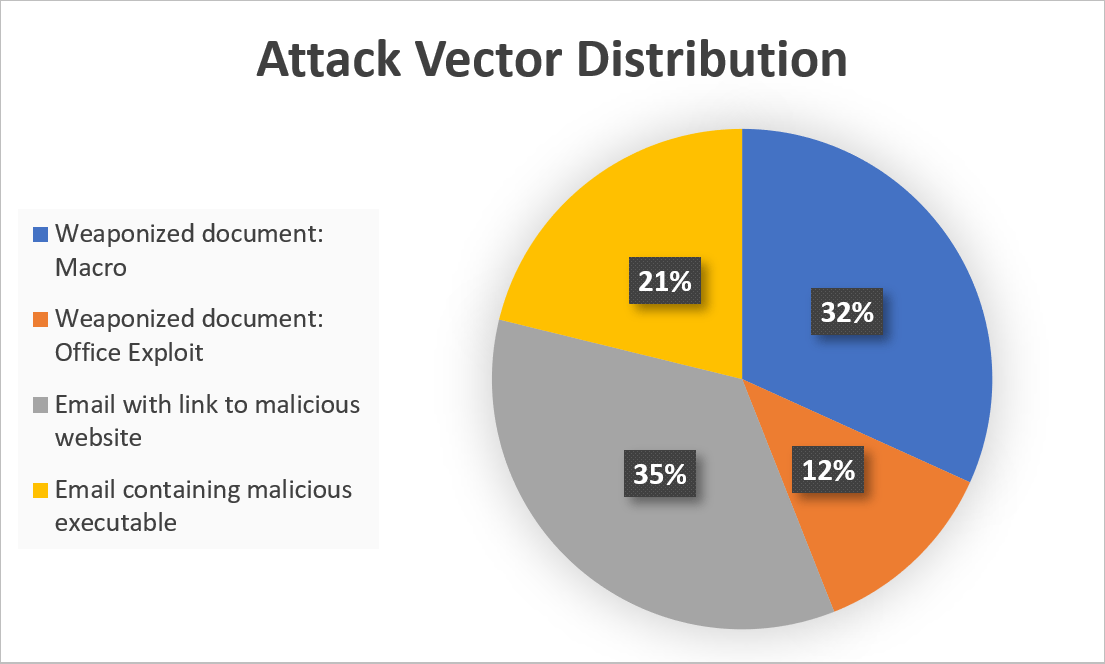
When examining the attacks deeper, we can see that only 21% include an explicit link that downloads and executes a malicious file. The vast majority are more advanced and include weaponized documents or links to malicious websites:
 It is also interesting to see that only 11% were blocked based on their signatures alone. The rest have successfully bypassed the signature layer protection and were blocked by Cynet 360’s more sophisticated malware protection mechanism:
It is also interesting to see that only 11% were blocked based on their signatures alone. The rest have successfully bypassed the signature layer protection and were blocked by Cynet 360’s more sophisticated malware protection mechanism:
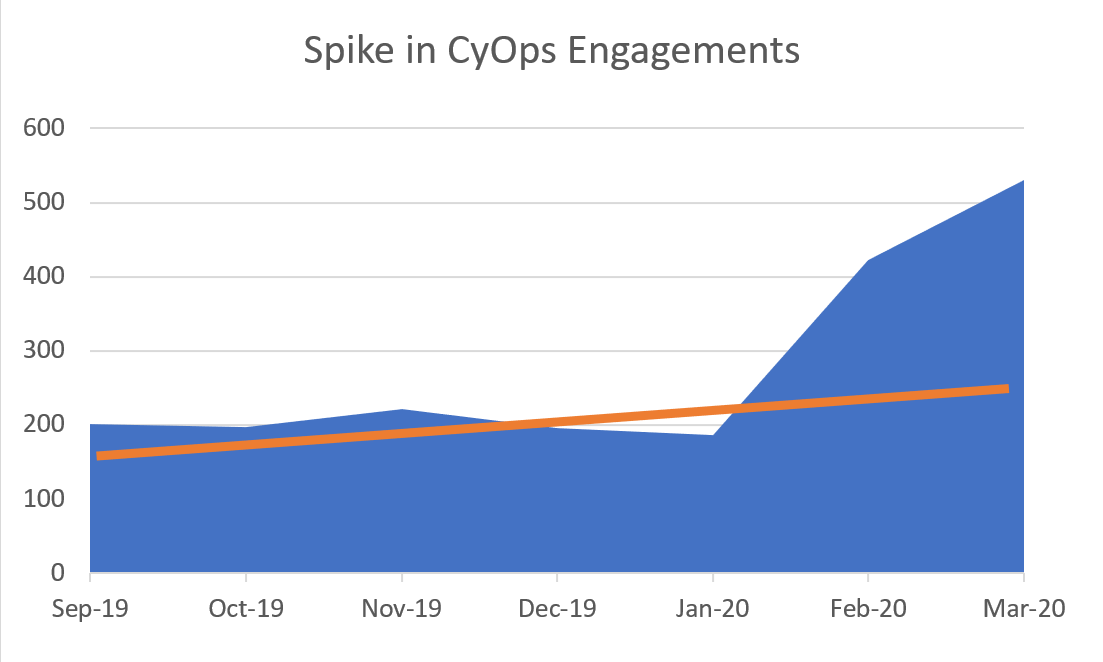
Working Remotely Impairs the Security Team’s Efficiency
In the course of the recent weeks the engagement volume with CyOps, Cynet’s MDR services, far exceeded the average level. Following an active reach out, we discovered that this increase is due to difficulties security teams experience due to quarantined team members, pushing them to need more of CyOps’s expertise.
Cynet 360’s New Offering
As a breach protection platform, Cynet introduces a dedicated offering tailored to the new Coronavirus related cyber risks.
- For both existing and new customers, Cynet will allow, free of charge (for a period of 6 months), the deployment of its product, Cynet 360, on personal computers used by employees working from home.
- Cynet massively adds staff to CyOps, its MDR services team, to be able to cover for companies with reduced security staff because of the Coronavirus.
Check out Cynet’s offering here