Rhysida: the ransomware gang strikes again
Since emerging in May 2023, Rhysida has rapidly risen as a ransomware threat, targeting various sectors in regions around the world. As a ransomware-as-a-service (RaaS) provider, Rhysida offers ransomware to other cybercriminals in exchange for a cut of their ransom profits. Last month, Rhysida perpetrated a devastating cyberattack against the British Library, one of the world’s largest and most prestigious libraries.
The Rhysida attackers exploited a vulnerability in the British Library’s VPN software, which allowed them to bypass a firewall and access the internal network.
Once they gained access to the network, according to a CISA advisory from November 15, the Rhysida gang performed LoLBins techniques. By using these built-in utilities or legitimate applications, they were able to carry out their malicious activities while evading detection. They used:
- PowerShell to run scripts and commands such as “Whoami.exe” and “ipconfig.exe” to discover information about the compromised system and network, such as the username, domain name, IP address and more
- exe to execute processes remotely. Rhysida actors heavily leveraged this tool for lateral movement and remote execution.
- exe to identify logged-in users and perform reconnaissance on network accounts within the victim environment
- exe to modify registry keys
- exe to cover their tracks by clearing Windows event logs — including system, application, and security logs
As a final stage, the attackers deployed the Rhysida ransomware and encrypted millions of the library’s files. They used a “double extortion” technique, demanding a ransom payment of 20 bitcoins (about $590,000) to restore the encrypted data and threatening to publish the sensitive exfiltrated data online unless paid.
The United Kingdom’s national library refused to pay the ransom and later confirmed that some of the personal data had appeared for sale online.
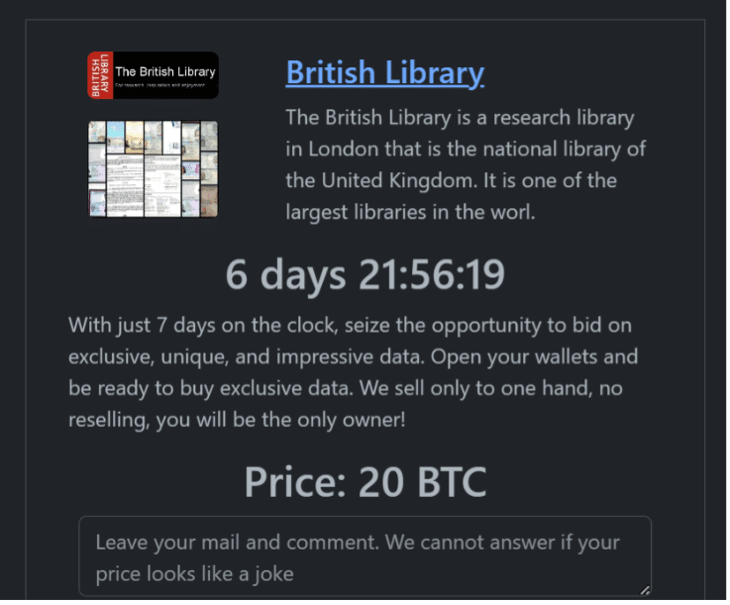
“Open your wallets and be ready to buy exclusive data. We sell only to one hand, no reselling, you will be the only owner!”
Who is Rhysida?
Rhysida’s origin and identity are unknown, but some clues suggest that they may be based in Russia, or in the Commonwealth of Independent States, based on the language and time zone of its communications with victims. For example, their ransomware software contains code snippets and comments in Russian, and their ransom notes and leak site use Russian words and phrases. They also avoid attacking organizations in Russia or other former Soviet countries. Rhysida is believed to have links to the Vice Society ransomware group, which was active in 2021 and targeted the education sector. It was even suggested that Rhysida may be using the Vice Society’s ransomware kit or that some of its members may have joined Rhysida after Vice Society stopped operating.
Their main activity is to launch ransomware attacks on a global scale, targeting a diverse range of sectors including education, government, manufacturing, and technology, but with a particular focus on healthcare and public health. Their intercontinental operations have affected organizations in Europe, North and South America, Asia, and Australia.
The Rhysida gang has not only targeted the British Library, but also launched several other high-profile attacks on government and healthcare institutions around the world. Some of their previous victims include:
- The Chilean Army: In May 2023, Rhysida hacked the Chilean Army’s website and email system, encrypting its data and demanding a ransom of 50 Bitcoin (about $1.9m). Rhysida also leaked some of the data on its leak site, including military documents and personal information of soldiers and officers.
- Prospect Medical Holdings: In August 2023, Rhysida attacked the U.S. hospital group, encrypting its data and demanding a ransom. Rhysida also threatened to leak the data of more than 200,000 patients and employees, including 500,000 Social Security numbers, corporate documents, and patient records. The group said it would sell the data for 50 Bitcoin (about $1.9m) on its leak site, where it posted samples of the data and started an auction.
- Kuwait Ministry of Health: In July 2023, Rhysida hacked the Kuwaiti health ministry, encrypting its data and demanding a ransom of 50 bitcoin (about $1.9m). Rhysida also leaked some of the data on its leak site, including medical records and personal information of patients and staff.
How to stop Rhysida?
CISA and the Federal Bureau of Investigation (FBI) have released a joint Cybersecurity Advisory to inform the public about the Rhysida ransomware and its indicators of compromise (IOCs), detection methods, and tactics, techniques, and procedures (TTPs). The federal agencies are also providing assistance to victims and guidance to stop Rhysida ransomware attacks.
Rhysida actors are known for using phishing emails, VPN software and the ZeroLogon vulnerability (CVE-2020-1472) as their initial access vectors. To stay protected, these three steps are recommended:
- Watch out for phishing attacks and unfamiliar emails.
- Use multi-factor authentication (MFA) for VPN access.
- Apply the Zerologon patch released by Microsoft. (For more information about the Zerologon vulnerability, read this analysis).
Cynet customers running the “Best Practice” configuration are protected from the post-exploitation activities of the Rhysida gang by multiple rules and mechanisms.