Two ScreenConnect exploits emerge. What security leaders need to know.
Two new CVEs (nicknamed “SlashAndGrab”) affecting ScreenConnect software were disclosed on February 21st.
A remote support and remote access software developed by ConnectWise Inc., ScreenConnect allows users to remotely access and control computers, servers, and other devices over the internet. I.T. professionals, help desk technicians, and support teams use ScreenConnect to troubleshoot technical issue and provide remote assistance such as:
- Remote control.
- File transfer.
- Chat and collaboration tools.
- Session recording etc.
The first vulnerability, CVE-2024-1709, pertains to authentication bypass. The second, CVE-2024-1708, relates to the risk of Remote Code Execution through a path-traversal vulnerability.
Cynet partners and customers are fully protected against both vulnerabilities, CVE-2024-1709 and CVE-2024-1708, due to multiple detection and response mechanisms within Cynet’s all-in-one cybersecurity solution.
Stay Ahead of Threats: Schedule Your Cynet Demo
Don’t wait for the next exploit. Cynet defends against the ‘SlashAndGrab’ CVEs affecting ScreenConnect.
Book a demo now and stay one step ahead in your security game.
CVE-2024-1709: Authentication Bypass
The exploitation involves exploiting an oddity in .NET where extra path components can be added to a URL without causing access to be denied.
Attackers could request the URL for the setup wizard (SetupWizard.aspx) but add extra information after it (like ” SetupWizard.aspx /maliciousFile”).
It is important to note that the setup wizard sets up the first admin user and installs a license on the system upon initial setup.
Once done with this step it will entirely replace the internal user database, removing all existing local users except for the one selected in the setup wizard.
This vulnerability is possible because of how .NET handles URLs. Additional path components are allowed to be appended to a legitimate URL without causing the request to fail. These extra components are then passed to the application through properties like Request.FilePath, Request.PathInfo and Request.Path, which only checks if the strings match “/SetupWizard.aspx”
Even in instances where ScreenConnect was already set up securely, this method could trick the system into granting access to the setup wizard.
CVE-2024-1708: Path-Traversal Vulnerability
Also known as directory traversal or directory climbing, path traversal vulnerabilities are a type of security flaw that occurs when an attacker can manipulate inputs related to file paths to access files or directories outside of the intended directory structure. This can lead to unauthorized access to sensitive files or data on the server.
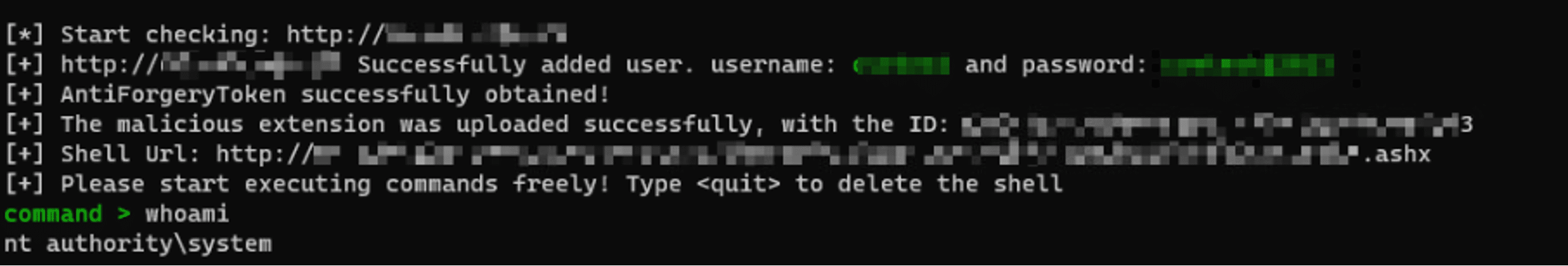
For this vulnerability, the attacker can write files in the root directory of the “App_Extensions” folder, adding malicious extensions that could potentially write files anywhere within the “C:\Program Files (x86)\ScreenConnect\App_Extensions” directory, rather than being restricted to their designated extension subdirectories.
After gaining administrator access through the authentication bypass, attackers can execute arbitrary code using the typical Extensions feature set.
Which versions of ScreenConnect are vulnerable?
ConnectWise has identified that all versions of ScreenConnect prior to 23.9.8 are susceptible to these issues, which do not have associated CVE identifiers. It is recommended that customers with on-premises installations of ScreenConnect urgently update to version 23.9.8, following the advice provided by ConnectWise: ScreenConnect Security Fix
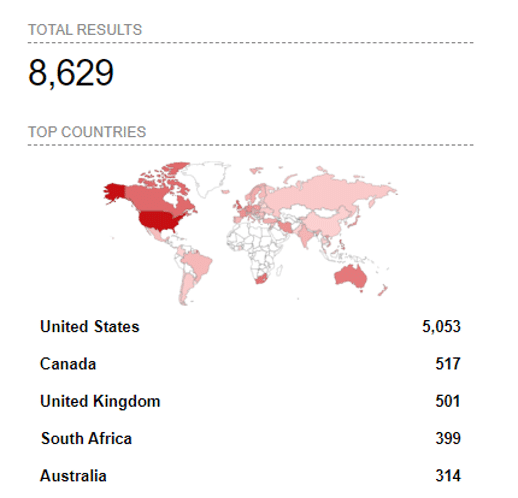
Shodan Report for ScreenConnect Servers
Over 8,500 servers are connected and running versions of ScreenConnect that are vulnerable.
ScreenConnect IOC
- 155.133.5.15
- 155.133.5.14
- 118.69.65.60
How Cynet prevents ScreenConnect exploitations
Cynet has multiple detection and mechanisms to block remote code execution (RCE).
The all-in-one cybersecurity solution automatically detects and prevents any post-exploitations based on CVE-2024-1709 or CVE-2024-1708. Cynet can also establish policies for any version of Screenconnect that is below 23.9.8 and monitor them accordingly.
For even more levels of security, CyOps, Cynet’s research team, is working around the clock to enhance detection logic and capabilities against the ScreenConnect vulnerabilities.
CyOps continuously monitors adversary activities, day and night. Their expert analysts are available on-demand — 24x7x365 — to support all questions or concerns Cynet partners or customers might have.
Protect Your Business from Vulnerabilities with Cynet
Don’t wait for the next exploit. Cynet defends against the ‘SlashAndGrab’ CVEs affecting ScreenConnect.
Book a demo now and stay one step ahead in your security game.