Unauthorized Access: 5 Best Practices to Avoid the Next Data Breach
Unauthorized access occurs when individuals gain access to an organization’s networks, systems, applications, data, or devices without permission. This typically involves a network security breach that can compromise network integrity or lead to data loss. Common causes include weak passwords, phishing attacks, and inadequate physical security. To prevent unauthorized access, it’s essential to implement strong security measures such as robust password policies, multi-factor authentication, regular software updates, employee training on security awareness, and effective physical security practices.
This article delves into these best practices, offering actionable insights for organizations to enhance their security posture against unauthorized access.
What is Unauthorized Access?
Unauthorized access refers to individuals gaining access to an organization’s data, networks, endpoints, applications or devices, without permission. It is closely related to authentication – a process that verifies a user’s identity when they access a system. Broken, or misconfigured authentication mechanisms are a main cause of access by unauthorized parties.
Other common causes of unauthorized access
- Weak passwords selected by users, or passwords shared across services
- Social engineering attacks, primarily phishing, in which attackers send messages impersonating legitimate parties, often with the aim of stealing user credentials
- Compromised accounts – attackers often seek out a vulnerable system, compromise it, and use it to gain access to other, more secure systems
- Insider threats – a malicious insider can leverage their position to gain unauthorized access to company systems
- Zeus malware – uses botnets to gain unauthorized access to financial systems by stealing credentials, banking information and financial data
- Cobalt strike – a commercial penetration testing tool used to conduct spear-phishing and gain unauthorized access to systems
What is a Security Breach or Data Breach?
A security breach or data breach is a successful attempt by an attacker to gain unauthorized access to organizational systems. In 2018, in the USA alone, there were 1,244 publicly reported data breaches with a total of 446 million records lost.
Blocking unauthorized access plays a central role in preventing data breaches. However, a robust security program uses “defense in depth” – several layers of security defenses, in an attempt to mitigate attacks long before attackers reach a sensitive system. Additional layers of security include network protection, endpoint protection, and data protection.
A typical security breach happens in three stages:
- Research — the attacker searches for weaknesses or vulnerabilities in organizational systems, people, or processes.
- Network/Social attack — the attacker attempts to penetrate the network perimeter, either by evading network defenses or by using social engineering to trick individuals into providing access, data, or credentials.
- Exfiltration — once the attacker manages to gain access, they can steal valuable assets or cause damage at their entry point, and also perform lateral movement to gain access to additional, more valuable systems.
Immediate security risks posed by unauthorized access
- By gaining unauthorized access to organizational systems or user accounts, attackers can:
- Steal or destroy private data
- Steal money or goods by carrying out fraud
- Steal user identities
- Compromise systems and use them for illegitimate or criminal activity
- Sabotage organizational systems or deface websites
- Cause physical damage – by gaining access to connected devices
Long-term consequences of a successful data breach
- Damage to reputation and trust
- Disruption to business continuity
- Reduced financial valuation or share price
- Costs of damage control and breach investigation
- Fines imposed by governments or security standards
- Payment of damages to affected parties
- PR and communication costs
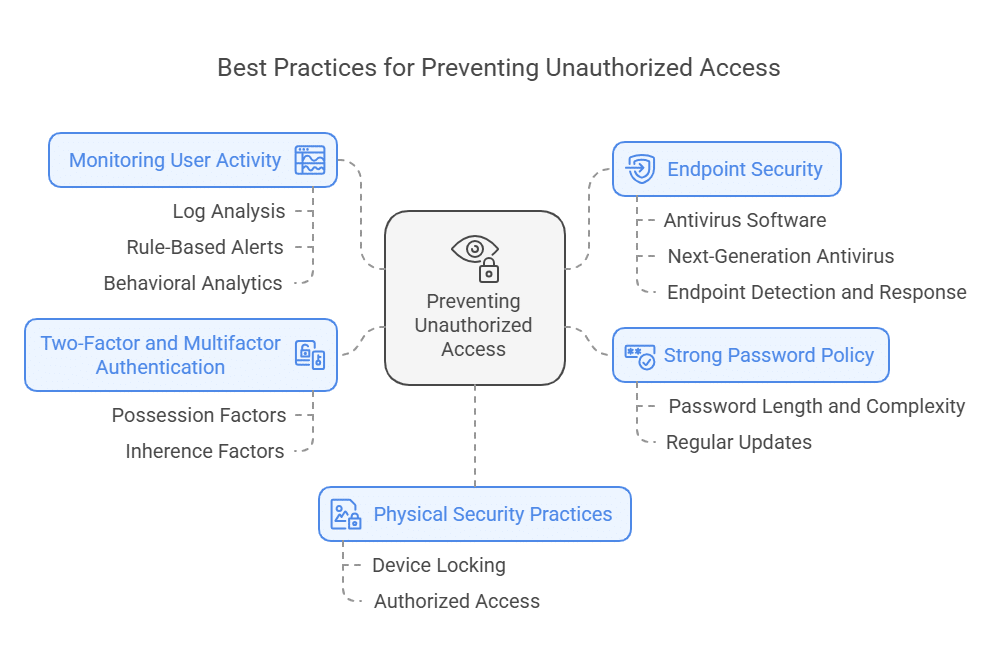
5 Best Practices to Prevent Unauthorized Access
Here are several ways your organization can improve the strength of authentication mechanisms and prevent access by unauthorized parties, whether internal or external.
1. Strong Password Policy
Enforce best practices for user passwords—force users to select long passwords including letters, numbers and special characters, and change passwords frequently. Educate users to avoid using terms that can be guessed in a brute force attack, inform them about routine password updating, and to tell them to avoid sharing passwords across systems.
Just setting a password policy may not be enough. Consider using tools—such as enterprise password management or Identity and Access Management (IAM)—to centrally manage user credentials and ensure they conform to security best practices.
2. Two Factor Authentication (2FA) and Multifactor Authentication
Credentials based on user names, passwords, answers to security questions, etc. are known more generally as knowledge-based security factors. Knowledge-based factors are an important authentication method, but they are inherently weak and easy to compromise.
One of the best ways to prevent unauthorized access in your organization is to supplement knowledge-based factors with additional authentication methods:
- Possession factors — authentication via objects possessed by the user. For example, a mobile phone, a security token or a physical card.
- Inherence factors — authentication via something the user is or has. This includes biometric authentication using fingerprints, iris scans or voice recognition.
3. Physical Security Practices
As important as cybersecurity is, don’t neglect physical security. Train users to always lock devices when walking away from their desks, and to avoid writing down passwords or leaving sensitive documents in the open. Have a clear policy about locking office doors and ensure only authorized parties can enter sensitive areas of your physical facility.
4. Monitoring User Activity
It is crucial to monitor what is happening with user accounts, to detect anomalous activity such as multiple login attempts, login at unusual hours, or login by users to systems or data they don’t usually access. There are several strategies for monitoring users and accounts:
- Log analysis — security analysts can gain visibility into logs of sensitive enterprise systems and uncover suspicious activity
- Rule-based alerts — security tools can alert security staff to suspicious activity patterns, such as multiple login attempts or incorrect login to sensitive systems
- Behavioral analytics — User and Event Behavioral Analytics (UEBA) monitors users and systems, establishes a baseline of normal activity, and detects any behavior that represents an anomaly and may be malicious.
Learn how Cynet provides a holistic security solution that offers UEBA user monitoring, together with comprehensive network monitoring and endpoint protection.
5. Endpoint Security
Historically, most security breaches were a result of penetrating the network perimeter. Today, many attacks circumvent network defences by directly targeting endpoints, such as employee workstations, servers, cloud instances. Installing antivirus on every endpoint is the most basic security measure.
Beyond antivirus, many organizations are deploying comprehensive endpoint protection measures that include:
- Next-generation antivirus (NGAV) – able to detect malware and other threats even if they don’t match known patterns or signatures
- Endpoint Detection and Response (EDR) – provides visibility and defensive measures on the endpoint itself, when attacks occur on endpoint devices
Tips From Expert
In my experience, here are tips that can help you better prevent unauthorized access and avoid data breaches:
- Adopt just-in-time (JIT) access controls
Implement JIT access, where users are granted elevated permissions only when necessary and for a limited time. This minimizes the risk of unauthorized access by ensuring that privileges are not left open and vulnerable. - Implement context-aware authentication
Use contextual factors such as location, device type, and time of access to add layers to your authentication process. For example, block access requests from unrecognized devices or unusual locations unless additional verification steps are completed. - Use deception technology to catch credential misuse
Deploy fake credentials within your environment that, when used, trigger alerts. This strategy helps identify unauthorized access attempts and allows you to respond before significant damage occurs. - Deploy endpoint detection with real-time response
Implement EDR solutions with automated real-time response capabilities that can instantly isolate compromised endpoints, kill malicious processes, and alert your security team to the breach, preventing further unauthorized access. - Leverage identity analytics to monitor access anomalies
Use identity analytics tools to monitor user access patterns across all systems. These tools can detect anomalies such as excessive login attempts, abnormal file access, or unauthorized privilege escalations, providing early warnings of potential breaches.
Protecting Against Unauthorized Access with Cynet
Cynet 360 is a holistic security solution that can help with three important aspects of unauthorized aspects – network security, endpoint security and behavioral analytics.
1. Network Analytics
Network analytics is essential to detect and prevent unauthorized access to your network.
The challenge — sophisticated attackers target an organization’s weak points. Following an initial endpoint compromise, the attacker looks to expand their reach and gain privileges and access to other resources in your environment. Their ultimate aim is to access your sensitive data and to transfer it to their premises. Key parts of these attack vectors can only be discovered via generated anomalous network traffic.
The solution — Cynet Network Analytics continuously monitors network traffic to trace and prevent malicious activity that is otherwise invisible, such as credential theft and data exfiltration.
2. Endpoint Protection and EDR
Unauthorized access to endpoints is a common cause of data breaches.
The challenge — attackers with strong motivation and good resources will eventually succeed to bypass the prevention measures in place. They will use several tools to silently work undetected until they achieve their desired outcome.
The solution — Cynet EDR continuously monitors the endpoints, so defenders can detect the active malicious presence and make swift and precise decisions on its impact and scope.
3. User and Event Behavioral Analytics
Behavioral analytics can help you detect anomalous activity on organizational systems or user accounts, which may indicate attempts at unauthorized access. It is also especially important to detect insider threats, which involve the misuse of legitimate user accounts.
The challenge — user identities are a prime target for attackers as they are central to resources throughout the organization. Attackers with clear objectives in mind might bypass detection, succeed in stealing user account credentials and use them for data access and lateral movement.
The solution — Cynet User Behavior Analysis monitors and profiles user activity continuously, to establish a legitimate behavioral baseline and detect anomalous activity that suggests compromise of user accounts.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response