In this article
- What is the Role of Cybersecurity in Compliance Efforts?
- Which Types of Data Can Be Subject to Compliance Requirements?
- Key Elements of Cybersecurity Compliance
- Major Cybersecurity Compliance Regulations and Standards
- 6 Steps to Achieving Compliance in Cybersecurity
- Common Challenges in Meeting Network Security Compliance
- Securing Your Business Against Cyber Risks with Cynet
Cybersecurity Compliance: 6 Steps to Security-Compliance Alignment
With the rise of data breaches, ransomware, and stricter global regulations, organizations must align their security programs with regulatory compliance standards. Failure to do so can result in significant financial penalties and damage to their reputation. In this guide, we’ll explore what cybersecurity compliance really means, why it matters, and outline six practical steps to help your business achieve alignment between security practices and compliance requirements.
What Is Cybersecurity Compliance and Why is it so Important?
Cybersecurity compliance in cybersecurity refers to adhering to the laws, regulations, standards, and guidelines designed to protect digital assets. These regulations are put in place to ensure that organizations implement the necessary security measures to safeguard sensitive information from unauthorized access, breaches, and other cyber threats. Compliance establishes a security baseline, ensuring that all entities within a given sector maintain consistent and sufficient levels of protection.
For organizations subject to regulations or binding industry standards, non-compliance can result in severe penalties, including fines, legal repercussions, and damage to an organization’s reputation. On the other hand, maintaining the industry standards demonstrates a commitment to protecting customer data, therefore enhancing trust, confidence and loyalty with clients, partners and other stakeholders.
What is the Role of Cybersecurity in Compliance Efforts?
Cybersecurity plays an important role in compliance efforts by providing the tools, technologies, and methodologies needed to meet regulatory requirements. Effective cybersecurity measures help organizations protect sensitive data, detect and respond to threats, and ensure the integrity and availability of critical systems. These measures include implementing firewalls, encryption, access controls, and regular security assessments, all of which are fundamental components of compliance frameworks.
Furthermore, cybersecurity supports compliance by enabling continuous monitoring and auditing of security practices. Regular assessments and audits help identify vulnerabilities and gaps in security controls, allowing organizations to address these issues promptly. This proactive approach ensures ongoing adherence to regulations and helps prevent potential breaches that could lead to non-compliance. By integrating robust cybersecurity practices into their compliance strategies, organizations can better protect their assets and maintain a strong security posture.
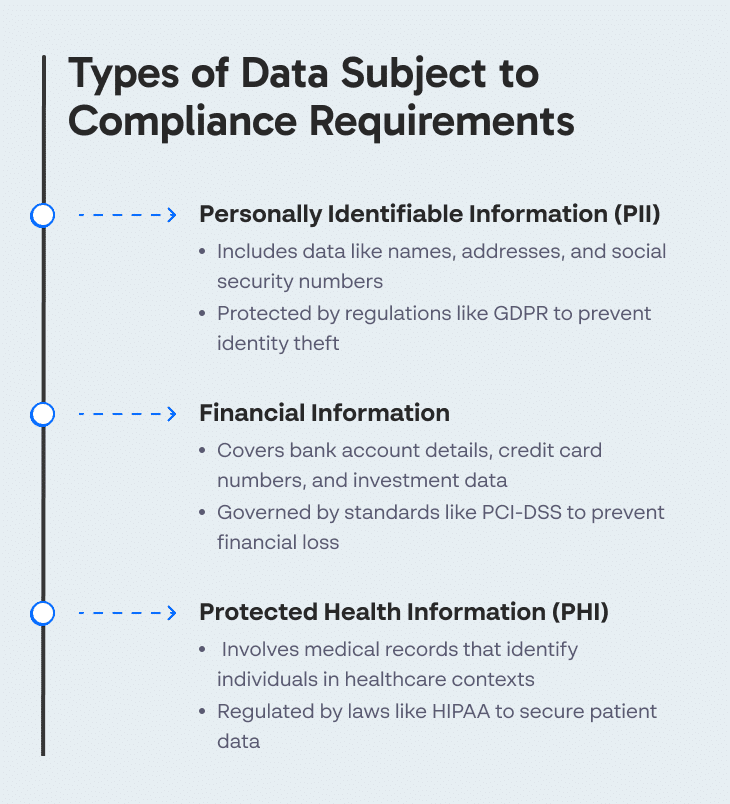
Which Types of Data Can Be Subject to Compliance Requirements?
The following types of data might be covered by data protection regulations and cybersecurity frameworks. Of course, the actual types of data subject to compliance requirements depends on the regulation or standard and the specifics of your organization.
Personally Identifiable Information (PII)
Personally Identifiable Information (PII) includes any data that might help identify an individual. Names, addresses, social security numbers, and email addresses are typical examples. Cybersecurity regulations such as the General Data Protection Regulation (GDPR) emphasize protecting PII due to its potential use in identity theft and fraud. Compromise of PII can lead to loss of privacy and financial damage to individuals.
Financial Information
Financial information includes sensitive data tied to an individual’s or organization’s finances, such as bank account numbers, credit card details, and investment portfolios. Regulations like PCI-DSS (Payment Card Industry Data Security Standard) set strict industry standards to protect this critical information. Exposure can lead to major financial losses, legal consequences, and a serious decline in consumer trust and brand reputation.
Protected Health Information
Protected Health Information (PHI) refers to any information in a medical record that can be employed to identify an individual and that was created, used, or disclosed in the course of providing a healthcare service. Regulations like HIPAA (Health Insurance Portability and Accountability Act) in the United States enforce the protection of PHI distinctly. Health organizations must maintain a high level of security and compliance to protect patient information.
Key Elements of Cybersecurity Compliance
What’s included in cybersecurity compliance? Generally speaking, complying with security regulations typically includes:
- Risk Assessment – Conducting assessments to identify and evaluate potential threats and vulnerabilities to systems, data, and infrastructure.
- Security Policies and Procedures – Define clear internal rules and guidelines for handling data, accessing systems, and responding to threats (incident response).
- Access Controls – Ensuring only authorized users have access to sensitive data and systems using methods like MFA and RBAC, and adhering to principles like least privilege and Just-in-Time access.
- Data Protection – Safeguarding data at rest and in transit through encryption, secure storage, and controlled data sharing.
- Incident Response Plan – Preparing and practicing a structured approach for detecting, responding to, and recovering from security incidents.
- Security Awareness Training – Regularly educating employees on cybersecurity risks, safe practices, and how to recognize threats like phishing.
- Regular Audits and Monitoring – Continuously monitoring systems and conducting audits to detect anomalies, misconfigurations, or violations.
- Supply Chain Security – Evaluating and monitoring the security posture of third-party partners and service providers.
- Compliance with Standards and Regulations – Aligning with frameworks like GDPR, HIPAA, ISO 27001, NIST, or SOC 2 based on your industry, geography, and client requests.
Common frameworks include:
- GDPR: A European regulation that governs how organizations collect, process, and protect personal data.
- HIPAA: A US regulation for safeguarding medical records and healthcare data.
- ISO 27001: An international standard for managing information security through policies, processes, and controls.
- NIST: A US framework providing guidelines and best practices for cybersecurity and risk management.
- SOC 2: An auditing standard that evaluates how well a company protects customer data across security, availability, processing, confidentiality, and privacy.
- Logging and Documentation – Maintaining detailed logs and documentation for auditing, to ensure traceability, support investigations, and prove compliance.
- Patch Management and Vulnerability Scanning – Regularly updating software and scanning systems to identify and fix known vulnerabilities.
Major Cybersecurity Compliance Regulations and Standards
GDPR
The GDPR is a regulation enforced by the European Union to protect data privacy across all member states. It applies to any organization operating within the EU, as well as those outside the region that offer goods or services to customers or businesses in the EU.
GDPR compliance requires organizations to be transparent about data collection, obtain user consent, and protect personal data from misuse. It is enforceable with penalties for violations, which can include fines of up to 4% of annual global turnover or €20 million, whichever is greater.
Cybersecurity requirements in the GDPR:
- Data protection by design and default: Organizations must integrate data protection measures into their processing activities from the outset. This includes minimizing the amount of data collected and ensuring that data is not accessible to unauthorized individuals.
- Encryption and pseudonymization: Personal data should be encrypted and pseudonymized where appropriate to protect it from unauthorized access or disclosure.
- Access controls: Implement strict access control measures to ensure that only authorized personnel can access personal data. This includes using multi-factor authentication and regularly reviewing access permissions.
- Regular testing and monitoring: Organizations are required to regularly test, assess, and evaluate the effectiveness of their technical and organizational measures for ensuring the security of processing.
- Incident response plan: Develop and maintain an incident response plan to detect, report, and respond to data breaches promptly. This includes notifying the relevant supervisory authority within 72 hours of becoming aware of a breach.
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) establishes standards to protect patient data in the U.S. It requires healthcare providers and their associates to protect the accessibility and integrity of protected health information.
Compliance involves implementing physical, network, and process security measures to keep medical information secure and private. Violations of HIPAA can result in civil and criminal penalties, ranging from monetary fines to, in severe cases, imprisonment, depending on the extent of the violation and the harm caused to individuals.
Cybersecurity requirements in HIPAA:
- Administrative safeguards: Implement policies and procedures to manage the selection, development, implementation, and maintenance of security measures to protect electronic protected health information (ePHI). This includes risk analysis and management, workforce training, and contingency planning.
- Physical safeguards: Establish physical measures to protect electronic information systems and related buildings and equipment from natural and environmental hazards, as well as unauthorized intrusion. This includes facility access controls, workstation security, and device and media controls.
- Technical safeguards: Use technology to protect ePHI and control access to it. This includes access controls, audit controls, integrity controls, and transmission security.
- Security management process: Identify and mitigate potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI. This involves conducting regular risk assessments and implementing security measures to reduce identified risks.
- Breach notification rule: Establish procedures for notifying affected individuals, the Secretary of Health and Human Services, and, in certain circumstances, the media in the event of a breach of unsecured ePHI.
FISMA
The Federal Information Security Management Act (FISMA) mandates federal agencies to develop, document, and implement an information security system. This involves categorizing information based on levels of impact on security breaches, conducting regular risk assessments, and ensuring data confidentiality, integrity, and availability.
Compliance with FISMA protects government information against threats and reduces the cost of security by ensuring proactive risk management. Non-compliance can often result in budgetary constraints until the agency meets the required standards.
Cybersecurity requirements in FISMA:
- Risk management framework: Develop a risk management framework that includes categorizing information systems, selecting and implementing security controls, assessing their effectiveness, and authorizing the systems for operation.
- Security controls: Implement a set of security controls from the NIST Special Publication 800-53, an information security standard by NIST for protecting federal information and systems.
- Continuous monitoring: Establish continuous monitoring processes to detect and respond to security incidents in real-time. This includes automated tools and techniques for continuous assessment and authorization.
- Incident response: Develop and implement incident response procedures to address security breaches promptly. This includes reporting incidents to the federal Cybersecurity and Infrastructure Security Agency (CISA).
- Security training and awareness: Provide regular security training and awareness programs for employees to ensure they understand their security responsibilities and how to protect federal information systems.
PCI-DSS
The Payment Card Industry Data Security Standard (PCI-DSS) is aimed at organizations that handle branded credit cards from major card issuers. The standard requires entities to manage and secure card data to prevent fraud and data breaches.
PCI-DSS compliance involves ongoing assessment, remediation, and reporting of security practices. Non-compliance can lead to fines ranging from $5,000 to $100,000 monthly until compliance issues are resolved. Upholding standards helps to protect cardholder data, reducing the overall risk to the payment ecosystem.
Cybersecurity requirements in the PCI-DSS:
- Build and maintain a secure network and systems: Install and maintain a firewall configuration to protect cardholder data and avoid using vendor-supplied defaults for system passwords and other security parameters.
- Protect cardholder data: Protect stored cardholder data through encryption and ensure the secure transmission of cardholder data across open, public networks.
- Maintain a vulnerability management program: Use and regularly update anti-virus software or programs and develop and maintain secure systems and applications.
- Implement strong access control measures: Restrict access to cardholder data by business need-to-know, identify and authenticate access to system components, and restrict physical access to cardholder data.
- Regularly monitor and test networks: Track and monitor all access to network resources and cardholder data, and regularly test security systems and processes.
ISO/IEC 27001
ISO/IEC 27001 is an international standard focusing on the management of information security and the establishment, implementation, maintenance, and continual improvement of an information security management system (ISMS). It proposes a risk-based approach to information security and includes detailed requirements.
Achieving ISO/IEC 27001 certification demonstrates that an organization has a reliable approach to managing information security. This can enhance customer and stakeholder trust, improve company reputation, and provide a competitive edge.
Cybersecurity requirements in ISO/IEC 27001:
- Information security policies: Develop and maintain comprehensive information security policies that guide the organization’s approach to managing and protecting information.
- Organization of information security: Establish a management framework to initiate and control the implementation of information security within the organization. This includes defining roles and responsibilities.
- Asset management: Identify, classify, and manage information assets to ensure their protection. This includes conducting regular inventories and assigning ownership of assets.
- Access control: Implement access control policies and procedures to ensure that only authorized individuals can access information. This includes user access management, user responsibilities, and system and application access control.
- Cryptography: Use cryptographic controls to protect the confidentiality, authenticity, and integrity of information. This includes managing cryptographic keys securely.
Tips From Expert
In my experience, here are tips that can help you better navigate compliance in cybersecurity:
- Use compliance as a competitive differentiator Leverage your organization’s compliance status in marketing and client relations. Being compliant with rigorous standards like ISO/IEC 27001 or GDPR can distinguish your organization from competitors, reassuring customers about your commitment to data security.
- Apply continuous compliance monitoring Implement tools that provide real-time compliance monitoring rather than relying solely on periodic audits. Continuous monitoring can help detect deviations from compliance requirements as they happen, allowing for immediate corrective action.
- Develop a cross-regulation compliance strategy For organizations subject to multiple regulatory frameworks, create a unified compliance strategy. Identify overlapping requirements across regulations like GDPR, HIPAA, and PCI-DSS, and streamline efforts to meet these through common controls and practices.
- Develop comprehensive data retention policies Establish clear policies for data retention and deletion in accordance with compliance regulations. This helps avoid penalties for over-retaining data and ensures that data is properly disposed of once it is no longer needed.
- Regularly update your incident response plan Ensure your incident response plan is continuously updated to reflect changes in compliance requirements and evolving threats. Regular drills and updates help keep the plan effective and compliant, reducing the risk of breaches and non-compliance penalties.
6 Steps to Achieving Compliance in Cybersecurity
Organizations can take the following steps to ensure their cybersecurity program supports compliance with relevant regulations.
1. Understand the Applicable Regulations
Organizations must fully understand the cybersecurity regulations that apply to their industry and the data types they handle. Each jurisdiction may have distinct laws that dictate particular data protection and security practices. Familiarity with these rules is important for building a compliance strategy that aligns with legal requirements.
With this knowledge, companies can ensure they are protecting their customer data while also remaining compliant with national and international laws. Violations of these regulations can result in hefty fines and severe reputational damage, making it essential to remain consistently informed about new regulations and updates.
2. Conduct a Compliance Gap Analysis
Conducting a compliance gap analysis involves evaluating existing security practices against the required compliance standards. Identifying the gaps helps the organization understand the areas that need improvement to meet regulatory requirements.
Once gaps are identified, organizations can work on a structured plan to address these issues, which often includes enhancing security measures and updating policies and procedures to align with compliance standards. This proactive approach ensures compliance and helps strengthen overall security.
3. Implement Security Controls
Organizations should install technical, administrative, and physical controls based on the results of their risk assessments and compliance gap analysis. Common security controls include firewalls, encryption, access control mechanisms, and regular security auditing.
These controls help prevent unauthorized access and data breaches, ensuring that sensitive information remains protected. Effective implementation of security measures is critical for both compliance and the overall security posture of an organization.
4. Develop an Incident Response Plan
Every organization must have an effective incident response plan in place to quickly react to security incidents and minimize their impact. These plans should detail the procedures for addressing breaches, including the immediate actions to control damage, notification processes, and steps to prevent future incidents.
A fast and thorough response limits the damage caused by breaches and demonstrates the organization’s commitment to safeguarding information. Regular updates and drills help maintain an effective incident response capability.
5. Regularly Monitor and Assess Security Events
Organizations must continuously monitor their IT environments and conduct regular audits to ensure that security controls are effective and compliance requirements are met. These assessments provide insights into the effectiveness of the current security measures and help identify any need for adjustments or improvements.
Ongoing evaluations also help detect vulnerabilities early, reducing the risk of significant security incidents and ensuring continuous compliance with cybersecurity regulations.
6. Provide Cybersecurity Training and Awareness
Educating employees about security policies, current cyber threats, and safe online behaviors is important for reducing human error and improving an organization’s overall security. Training should be regular, and the awareness program should be updated frequently to reflect new security practices and compliance requirements.
By fostering a culture of security awareness, organizations can improve their compliance stance and reduce the likelihood of breaches or compliance violations caused by employee mistakes.
Common Challenges in Meeting Network Security Compliance
As environments grow more complex, meeting network security compliance standards becomes more challenging. Organizations need to navigate compliance for a mesh of modern and legacy systems, managed devices and BYOD, and on-premises and cloud environments. Each type of IT component brings its own technical requirements and security risks. In addition, gaining holistic visibility and policy consistency requires time and technological know-how.
To address these challenges, organizations rely on a mix of tools. These include:
- SIEM (Security Information and Event Management) platforms, which aggregate and analyze logs for suspicious activity.
- Asset management tools that ensure every endpoint and server is tracked and secured.
- Data Loss Prevention (DLP) technologies that help prevent unauthorized access, sharing, or exfiltration of sensitive data.
Securing Your Business Against Cyber Risks with Cynet
Cynet is a platform that natively integrates the endpoint, network, and user attack prevention & detection of XDR with the automated investigation and remediation capabilities of SOAR, backed by a 24/7 world-class MDR service. End-to-end, fully automated breach protection is now within reach of any organization, regardless of security team size and skill level.
XDR Layer: End-to-End Prevention & Detection
- Endpoint protection: Multilayered protection against malware, ransomware, exploits, and fileless attacks
- Network protection: Protecting against scanning attacks, MITM, lateral movement, and data exfiltration
- User protection: Preset behavior rules coupled with dynamic behavior profiling to detect malicious anomalies
- Deception: Wide array of network, user, and file decoys to lure advanced attackers into revealing their hidden presence
SOAR Layer: Response Automation
- Investigation: Automated root cause and impact analysis
- Findings: Actionable conclusions on the attack’s origin and its affected entities
- Remediation: Elimination of malicious presence, activity, and infrastructure across user, network, and endpoint attacks
- Visualization: Intuitive flow layout of the attack and the automated response flow
MDR Layer: Expert Monitoring and Oversight
- Alert monitoring: First line of defense against incoming alerts, prioritizing and notifying customers on critical events
- Attack investigation: Detailed analysis reports on the attacks that targeted the customer
- Proactive threat hunting: Search for malicious artifacts and indicators of compromise (IoC) within the customer’s environment
- Incident response guidance-Remote assistance in isolation and removal of malicious infrastructure, presence, and activity
Simple Deployment
Cynet can be deployed across thousands of endpoints in less than two hours. It can be immediately used to uncover advanced threats and then perform automatic or manual remediation, disrupt malicious activity, and minimize damage caused by attacks.
Get a free trial of Cynet and experience the world’s only integrated XDR, SOAR, and MDR solution.
FAQs
Cybersecurity compliance refers to meeting specific regulatory or industry standards that dictate how organizations must secure their digital assets and sensitive data. Information security is broader. It encompasses the strategies, policies, and technologies used to protect data from unauthorized access, disruption, or destruction, regardless of regulation.
HIPAA applies to healthcare organizations in the US and governs the protection of patient health data. PCI DSS applies to any business handling credit card transactions and mandates strict controls around payment data. GDPR, the EU’s privacy law, sets rules for data protection and privacy for individuals in the EU and affects any organization handling EU citizens’ data.
Others include SOX (Sarbanes-Oxley) for publicly traded companies, ISO/IEC 27001 for establishing a robust information security management system, and NIST frameworks (such as NIST 800-53 and NIST CSF), which are widely adopted in government and critical infrastructure sectors.
Industries that handle sensitive data are the most heavily regulated. Healthcare, finance, and retail top the list due to the high risk of data breaches involving health records, financial transactions, or consumer data.
Non-compliance can lead to severe legal, financial, and reputational consequences. Regulatory bodies can impose fines, revoke licenses, or bring legal action against organizations that fail to meet standards. Organizations also risk losing customer trust, facing lawsuits from affected parties, or being disqualified from doing business in regulated markets.
Secure endpoints, implement MFA, encrypt data in transit and at rest, and use EDR/XDR. In addition, conduct employee security training, follow compliance checklists, and enforce clearly defined BYOD policies.
SIEM, asset management, DLP, IAM, compliance automation, EDR/XDR, and SOAR.
Annually, at a minimum. However, industries with high risk or rapidly changing threat landscapes need semi-annually or quarterly assessments. Plus, conduct assessments after major changes like cloud migrations, mergers, or incidents.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response