Incident Response Platform: The Road to Automating IR
Incident response services are a growing priority at organizations, and technology platforms are essential to making incident response efficient and effective. Incident response platforms help security teams quickly identify and investigate incidents, manage their work on a case until closure, and automate incident response tasks to provide a faster response.
Need an incident response platform?
Cynet Response Orchestration, part of the Cynet All-in-One cybersecurity platform, can automate your incident response policy. Define automated playbooks with pre-set or custom remediation actions for multiple attack scenarios. Cynet also helps detect known and zero-day threats to ensure you only implement a manual response when necessary.
Learn more about Cynet Security Automation and Orchestration.
What are Incident Response Platforms?
An incident response platform is a software system that guides, assists and automates incident response. Incident response services provide three key capabilities:
- Supporting analyst workflows—helping security analysts collaborate around a security incident, by providing case management. Case management allows analysts to open a case for a security incident, collect data from their investigation and save it as part of the case, prioritize cases, and share data with other analysts.
- Intelligence and analytics—helping security teams collect security event data by integrating with Security Information and Event Management (SIEM) and other tools, triage it, add context to create event timelines, and combine it with threat intelligence to identify security incidents with minimal effort.
- Security automation—automating responses using security playbooks. These are automated workflows that the platform can run when a specific security incident is detected. Incident response playbooks can be very effective at reducing response time, and can help save time for security teams.
Learn more about incident response platforms in our in-depth guide: Incident Response Retainer: Getting Your Money’s Worth
Features of Incident Response Platforms
Below is a summary of features provided by incident response platforms across three primary functional areas.
| Supporting analyst workflows | Intelligence and analytics | Security automation |
|
|
|
What is SOAR?
Gartner defines Security Orchestration, Automation and Response (SOAR) as a new category of security tools that can collect threat data from multiple sources, triage security events, and automatically respond to a large variety of security incidents. Make sure that your incident response platform of choice supports SOAR capabilities.
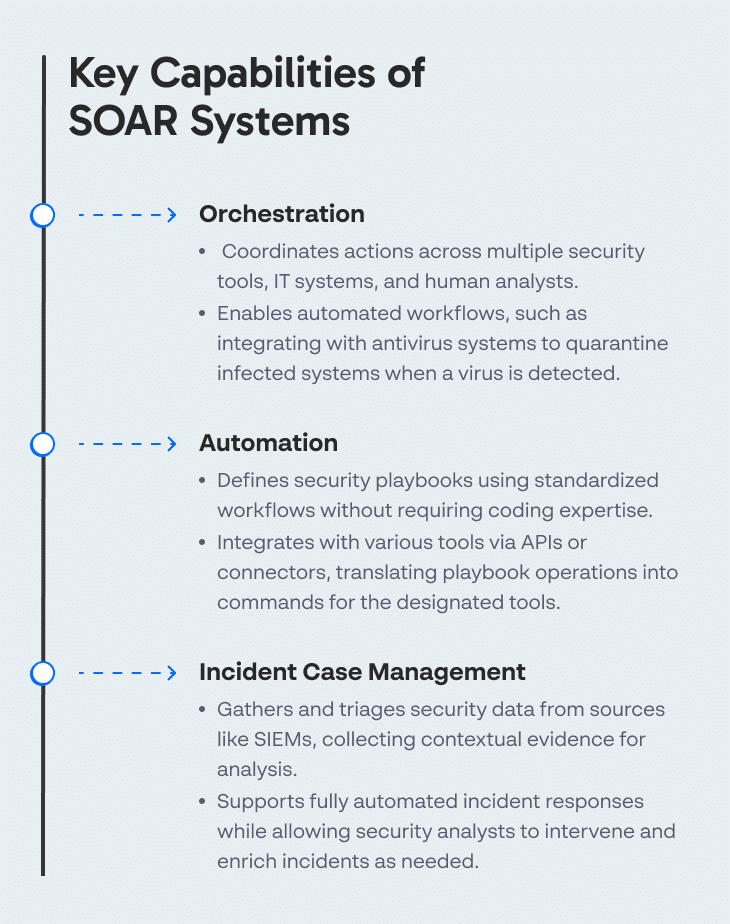
Gartner defines the following key capabilities for SOAR systems:
Orchestration
The ability to coordinate actions across multiple security tools, IT systems and human analysts. This is required for many types of automated response workflows—for example if a virus is detected in a spam email, there is also a need to integrate with antivirus systems on endpoints, identify infected systems and quarantine them.
Automation
The ability to define security playbooks using standardized workflows or steps. Security analysts should be able to define automated workflows without being experts in the specific tools being automated, and without having to write code or scripts. The SOAR system should integrate with a large variety of tools via APIs or connectors, and translate standard security playbook operations to commands performed on the designated tools.
Incident case management
The ability to gather security data from a SIEM or other sources, triage it, collect contextual evidence, and allow security teams to add information from their own investigations. A SOAR tool supports fully automated incident response and allows security analysts to step in at any stage of the process to make decisions or enrich the incident with additional data.
Tips From Expert
In my experience, here are tips that can help you better implement and maximize incident response platforms:
- Prioritize high-impact playbook automation
Focus your automation efforts on high-impact incidents such as ransomware or credential theft. Automating responses for these scenarios can drastically reduce the time to contain critical threats and minimize damage. - Incorporate contextual incident enrichment
Leverage your SOAR platform to automatically enrich incidents with contextual data (e.g., user behavior or asset criticality). This prioritization can help analysts focus on the most impactful incidents, reducing response time. - Automate incident evidence collection
Automate the collection and storage of forensic evidence (logs, memory dumps, etc.) within your incident response platform. This supports faster investigations and ensures compliance with legal and regulatory requirements. - Use playbook simulations for validation
Before deploying new automated playbooks, run simulations to validate their effectiveness. This helps catch potential errors and fine-tune response steps in a controlled environment without risking live assets. - Build layered automation with decision points
Structure playbooks with automated steps that include decision points for human intervention when needed. This layered approach balances speed and control, giving analysts oversight during complex incidents.
A Process for Automating Incident Response
Automation is extremely important to building a scalable, efficient incident response system. However, implementing an incident response platform with automation capabilities is not enough. Take a gradual approach to automating your incident response processes:
1. Build your first playbooks around manual actions
Automating external tools can be risky. The automation itself may not work as expected, and it is reliant on those tools being available and functioning currently. Build your first playbooks using manual tasks analysts can easily perform to respond to an incident. Practice those processes on real events to see they are really effective. This paves the way to automating these processes, in part or in whole.
2. Continually assess and refine the process
After every security incident, investigate what worked and what didn’t, and fine-tune your processes. Gradually, identify steps that can be easily automated using your incident response platform and integrated tools. As you automate these steps, continue monitoring the relevant processes to see they are running as expected and incidents are mitigated effectively.
3. Develop playbook templates for iterative and scalable development
Finally, you will reach a high level of maturity, with multiple incident response processes tried and tested, with a high degree of automation. It will now be possible to create templates of processes for categories of IR processes, allowing analysts to start from a template and customize it to a new type of security incident. This allows reuse of common procedures to design an effective, automated response to all common incidents your organization faces.
Automated Incident Response with Cynet
Cynet provides a holistic solution for cybersecurity, including the Cynet Response Orchestration which can automate your incident response policy. Users can define automated playbooks, with pre-set or custom remediation actions for multiple attack scenarios. Cynet automated playbooks also help detect threats to ensure that you only implement a manual response when it is necessary.
Cynet Response Orchestration can address any threat that involves infected endpoints, malicious processes or files, attacker-controlled network traffic, or compromised user accounts.
Learn more about Cynet Response Orchestration.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response