In this article
- What is an Incident Response Retainer Service?
- What is Included in an Incident Response and Data Forensics Service?
- The Main Benefits of Having an Incident Response Retainer
- Criteria for Choosing an Incident Response Service Provider
- Incident Response Team: Build or Buy?
- Cynet’s 24/7 Incident Response Team
Incident Response Retainer: Getting Your Money’s Worth
When disaster strikes, it’s best to be prepared. An incident response retainer is like an insurance policy—it gives you additional resources to deal with a devastating cyber attack. You can hire an outsourced incident response service provider and have their experts on call to help you respond to a cyber incident with a guaranteed Service Level Agreement (SLA).
Read on to understand what you should expect to get in an incident response retainer, including the option of a no-cost retainer, and whether it makes sense to build an in-house incident response operation.
What is an Incident Response Retainer Service?
An Incident Response Retainer (IRR) is a service agreement that allows organizations to get external help with cybersecurity incidents.
IRRs are provided by data forensics and incident response (DFIR) specialists and service providers, and also by vendors offering incident response tools, who also have in-house incident response teams. When purchasing a service from a tool vendor, you will typically receive access to their technology as well as incident response services.
There are two main types of incident response retainers:
- No-cost retainer – an on-demand agreement with a vendor or service provider that specifies how they will help the organization respond to an incident, if and when an incident occurs. The agreement specifies a service level agreement (SLA), the nature of services provided, a procedure for declaring incidents, and a cost per incident, which is paid only if the service provider actually renders services.
- Prepaid retainer – an incident response agreement in which the organization pre-pays the service provider for a certain number of hours, typically per month or per quarter, which can be used to respond to cyber incidents, with an agreed SLA. If the hours are not used in full, the service provider will typically offer other valuable security services, such as penetration testing or security education for the organization’s staff.
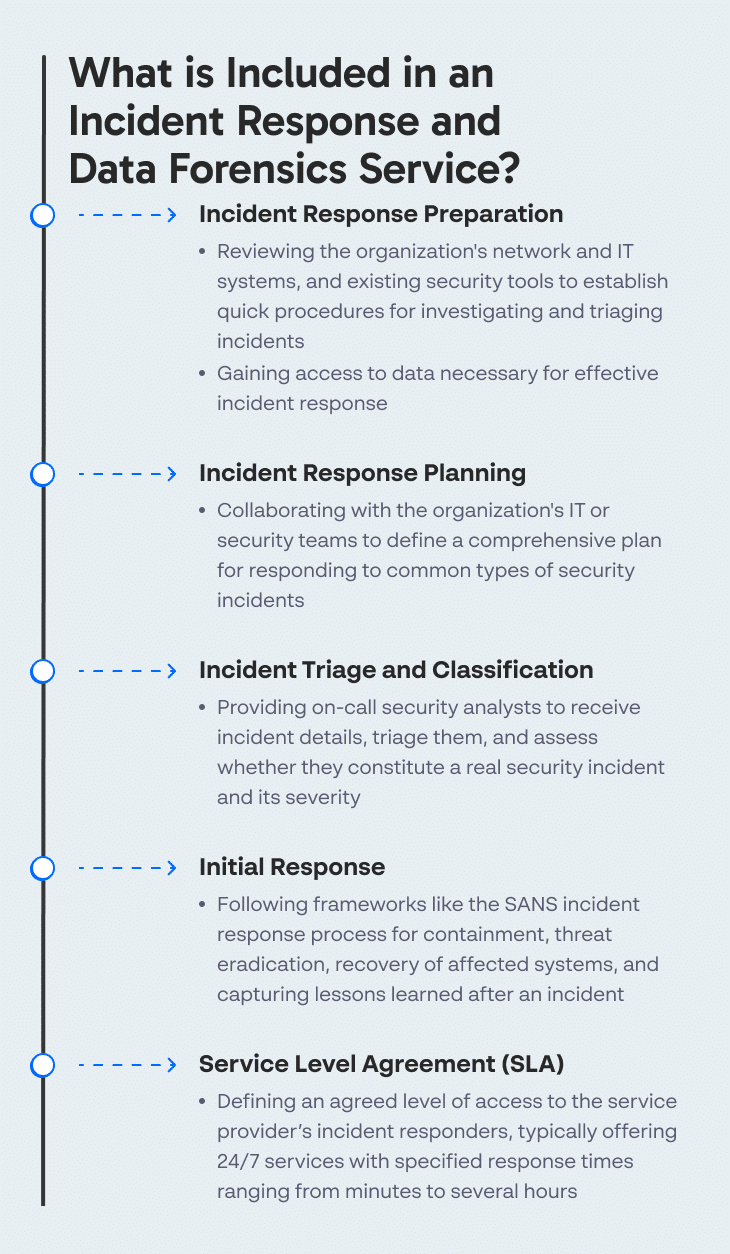
What is Included in an Incident Response and Data Forensics Service?
A DFIR service provider or tool vendor will typically provide the following elements in an IRR service:
- Incident response preparation—reviewing the organization’s network, IT systems, and existing security tools, gaining access to data, and establishing quick procedures for investigating and triaging incidents.
- Incident response planning—defining a plan, together with the organization’s IT or security teams, for jointly responding to common types of security incidents.
- Incident triage and classification—having a security analyst on call at the service provider to receive details of the incident, triage it, and help determine if it is a real security incident and its severity.
- Initial response—response will typically follow a framework like the SANS incident response process: after the incident has been identified, the service provider will perform containment, eradication of the threat, recovery of affected systems, and lessons learned.
- SLA—the agreement will provide an agreed level of access to the service provider’s incident responders. Most services are offered 24/7, with a specified time period, ranging from minutes to several hours, allowed to transpire until the incident response process begins.
The Main Benefits of Having an Incident Response Retainer
An Incident Response retainer provides organizations with the confidence and assurance that they will get effective, quick, and expert cybersecurity support if and when a cyber incident occurs. With an incident response retainer, security teams gain:
- Faster Response Times – A retainer assures that the incident response can immediately operate to contain, respond, and mitigate the attack. Rather than wasting time on procurement, getting to know the environment, and communicating playbooks, the team can jump straight into action. This will likely minimize the blast radius of the attack, help get business operations back to normal quickly, and reduce stress among security and leadership.
- Access to Elite Expertise – Incident response teams are experts in their field. They’ve analyzed and dealt with multiple incidents, including complex ransomware and malware. A retainer provides access to these expert incident responders and forensic analysts, ensuring the response is professional and quick with minimal disruption.
- Cost Predictability – Cyber incidents can be very expensive. This includes downtime, reputational damage, customer notification requirements, potential regulatory fines, potential ransom, emergency response efforts, legal and compliance costs, forensic investigations, and more. An incident response retainer helps bring predictability to some of these expenses by locking in pricing, prioritizing support, and minimizing the need for last-minute, high-cost interventions. In addition, it can come with proactive services (like tabletop exercises or threat hunting), helping minimize the financial impact in case of an incident.
- Proactive Preparedness – Most retainers include preventive services like security assessments, playbook development, and training. This helps boost readiness and strengthen the security posture before any breach occurs. It also ensures smoother collaboration if one does.
- Regulatory and Legal Readiness – On top of business disruptions, a breach also brings regulatory scrutiny. Incident response teams help address these needs by reporting according to legal timelines, preserving forensic evidence as required by law, and managing communications to minimize liability.
Criteria for Choosing an Incident Response Service Provider
Your incident response provider is your most important partner in case of a cyber attack. So how can you ensure you’re choosing the right one? Take into account the following criteria:
- Choose a provider with a proven history of handling security incidents, both complex and simplistic, zero-days and known threats.
- Ensure round-the-clock availability and SLAs that fit your needs and risk appetite.
- Ensure the provider has experience in your specific sector. This is especially important if your sector has unique needs (e.g, OT) or if you are strictly regulated (e.g, finance or healthcare).
- Ensure experience in your company size. An enterprise attack is not the same as an attack on an SME.
- Ensure experience in your type of environment. A cloud environment is different from an on-premises one.
- Check that the provider has the knowledge and ability to perform deep-dive forensics and root-cause analysis to understand how the breach occurred.
- Make sure the vendor has access to global threat feeds and real-time intelligence and tracks them for identifying threats.
- If you need tabletop exercises, red/blue teaming, or adversary simulation, check whether hours can be converted to these services.
- Ensure the vendor knows how to meet compliance regulations, like evidence collection and reporting.
- Ask to see the vendor’s playbooks and ensure they cover all your needs: from technical (e.g, covering all environments) to communications (e.g, executive briefings) to scope (e.g, including post-incident reporting).
Most importantly, ensure you feel comfortable with the team. If an attack occurs, you need streamlined communication and trust to power through.
Incident Response Team: Build or Buy?
Many organizations are considering whether to build in-house incident response capabilities or rely on external services. There are two main aspects to this question:
- People—The individuals who respond to incidents are DFIR experts who can perform in-depth data forensics, identify and triage incidents, mitigate threats, and recover systems.
- Technology—There are multiple layers of security tools that can assist with incident response, including tools for network and traffic analysis, vulnerability scanning, security information and event management (SIEM), endpoint detection and response (EDR), and security orchestration, automation, and response (SOAR).
Build vs buy is not a black-and-white decision—most organizations will choose to build some in-house incident response capabilities and also rely on external services, at least for severe or high-profile incidents.
We recommend, at a minimum, building the following capabilities in-house:
- At least one DFIR expert in-house—They can help the organization prepare for incidents and actively hunt for threats even when there is no visible sign of an attack.
- Basic tooling for tracking and alerting on security events—you’ll need an infrastructure that can collect logs from IT systems, endpoints, and security tools and raise alerts on suspicious activity. IRR services will not build this for you.
- Automated incident response—put in place an automated incident response system that activates security playbooks in response to common attack scenarios. This can help respond to many day-to-day incidents without the expense and overhead of activating your external IRR service.
Tips From Expert
In my experience, here are tips that can help you better leverage incident response retainers:
- Leverage the retainer for proactive services
Utilize unused hours in prepaid retainers for proactive services like threat hunting or red-teaming, which can reveal gaps in your defenses before an attack occurs. - Integrate response playbooks with IR provider
Share your organization’s internal incident response playbooks with the retainer provider to ensure they align with your operational processes and reduce friction during a real incident. - Negotiate incident categorization and SLA tiers
When establishing SLAs, clarify what constitutes “critical” vs. “non-critical” incidents to avoid delays. Negotiate response times based on severity to ensure your high-priority issues get swift attention. - Request continuous knowledge transfer
Ensure your in-house team receives ongoing knowledge transfer from the IR team post-incident reviews. This will improve internal capabilities and empower your team for future incidents. - Opt for retainer providers with post-incident analytics
Choose providers that offer post-incident analytics and trend analysis. This insight helps you identify recurring vulnerabilities and assess the evolving threat landscape specific to your environment.
These tips will help ensure your incident response retainer is a strategic asset rather than just a reactive tool.
Cynet’s 24/7 Incident Response Team
Cynet offers a holistic security solution that analyses network and endpoint data, raises alerts, and protects against a wide range of known and zero-day threats. Cynet provides an outsourced incident response team that can provide organizations with professional security staff who can execute a fast, effective incident response process.
The Cynet team can deploy the Cynet security platform in a matter of minutes across hundreds to thousands of endpoints. They can then scan, analyse, identify and remediate threats before damage is done. Our incident response service includes:
- 24/7 incident response—including identification, containment, eradication and recovery
- Deep forensic investigations—collecting data to identify the scope of an attack and who is responsible
- Threat hunting—exploring security data to proactively discover advanced threats
- Malware analysis—analyzing malware in a sandbox to determine its characteristics and how to remediate it
Contact us for immediate help
For emergency assistance from our security experts, call us at +1 (347) 474-0048 or complete this form.
Need an incident response retainer?
Cynet is a trusted partner that analyzes network and endpoint data, raises alerts, and protects against a wide range of known and zero-day threats. Cynet provides CyOps, an outsourced incident response team on call 24/7/365 to respond to critical incidents quickly and effectively.
Learn more about Cynet’s incident response services.
FAQs:
An Incident Response Retainer gives organizations immediate access to cybersecurity experts when a breach or attack occurs. This drastically reduces response time, limits damage, and helps control the chaos during high-stress events. Without a retainer, companies may struggle to find qualified help in a crisis, delaying containment and investigation.
Threat detection identifies anomalies, suspicious behavior, or known attack signatures before they escalate. Once a threat is detected, it triggers the incident process: triage, containment, and investigation. The tighter the integration between detection and response, the faster and more effective the mitigation.
Choose an Incident Response service provider based on their expertise with your use cases, their SLAs, their support for your tech stack, and their ability to align with regulatory requirements. Plus, take into account your ability to trust them and easily communicate with them.
This depends on the environment and industry. But at minimum, an incident plan should be reviewed annually. Ideally, it should be updated after any major change (e.g., mergers, new tech deployments) or following an incident. Tabletop exercises or simulations should be run 1–2 times per year, and any gaps discovered should be incorporated into the updated plan.
Cyber Risk Management sets the priorities and frameworks that guide the incident response process. It helps determine what assets are most business-critical, what threats are most relevant, and how much risk the business is willing to accept. This ensures that the incident team focuses on protecting what’s most valuable and aligns its actions with business objectives.
Small businesses are increasingly targeted by attackers because they often lack internal security staff or robust defenses. A retainer gives them access to expert help without the cost of a full-time team.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response