Top 8 Incident Response Plan Templates and Why You Should Automate Your Incident Response
When a security incident strikes, you want to be prepared. This means knowing how to respond in the most effective and efficient way, while minimizing the “blast radius” and making the right business decisions. This is where a solid incident response plan can help.
Incident response plan templates help shorten the process of creating an incident response plan while ensuring best practices are baked in. In this article, we’ll walk you through the best free templates available today and explain how automation can help speed the incident response process.
What Is an Incident Response Plan Template?
An incident response plan template is a pre-structured format you can use to create your organization’s incident response plan. An incident response plan helps organizations respond effectively when a security incident occurs. It is a detailed document outlining the necessary steps to take before, during, and after an incident to mitigate damage and recover swiftly.
An incident response plan provides a systematic approach to managing the aftermath of a security breach or cyber attack. It aims to handle the situation in a way that limits damage and reduces recovery time and costs. An incident response plan template makes it easier to create a template by providing a framework that allows you to learn from the experience of other organizations or security professionals.
By taking an existing incident response template and adapting it to the unique needs and circumstances of any organization, you can quickly create an effective incident response plan.
Components of an Incident Response Plan Template
Here are the key components typically included in an incident response plan template:
- Purpose and scope: This section defines why the plan is in place and the extent of its coverage. This can include preventing incidents, minimizing their impact, and recovering. The scope defines the types of incidents that the plan covers, the systems and data included, and the personnel who are part of the plan.
- Threat scenarios: This section identifies and describes the potential incidents that may affect the organization. Threat scenarios can include:
– Ransomware attacks
– Insider data theft
– Cloud configuration breaches
– Third-party vendor compromise
– Account takeover
– Natural disaster causing server outage
- Roles and responsibilities: This section outlines the stakeholders involved in the incident response process and their specific duties. These can include incident response team members, IT staff, management, and external entities.
- Incident response process: This section provides a step-by-step guide on how to respond to an incident, from detection and identification to containment for limiting the damage, eradication for removing the root cause, recovery for restoring normal operations, and post-incident review for future improvement.
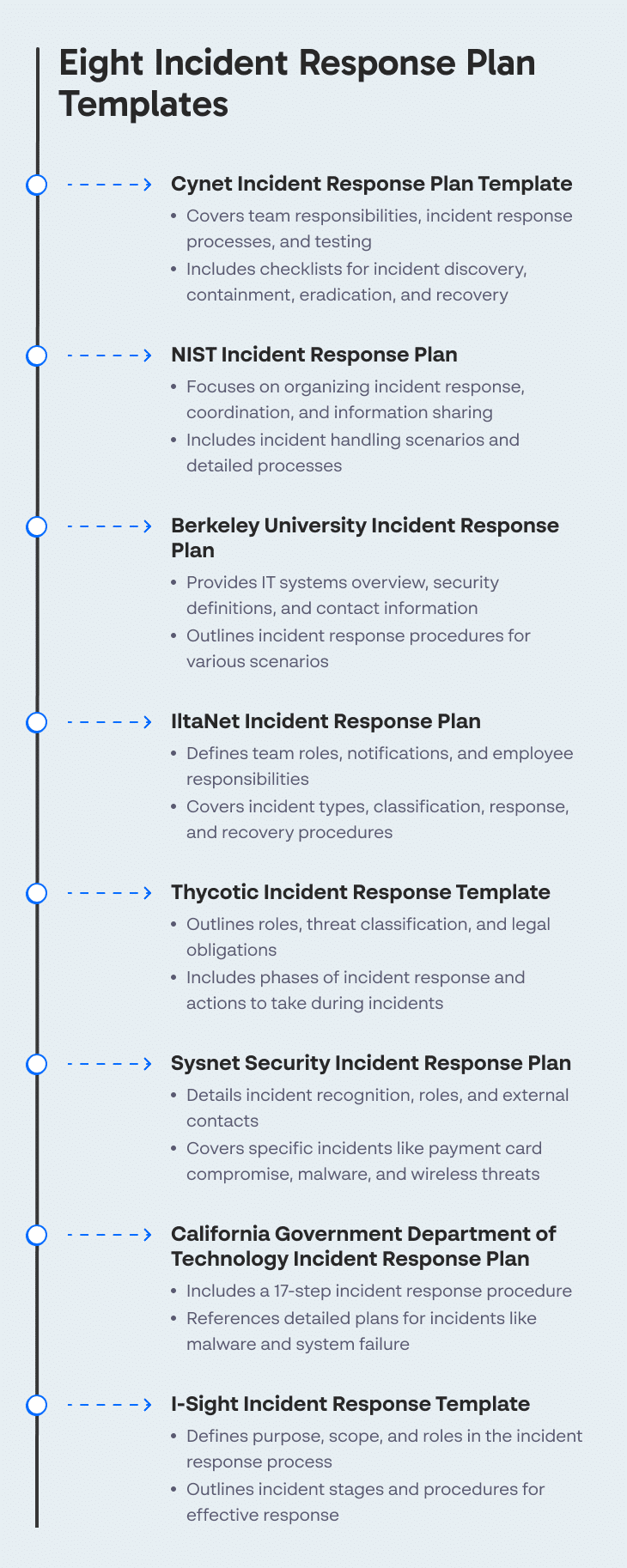
Eight Incident Response Plan Templates
When building your incident response plan, it is much easier to start with a template, remove parts that are less relevant for your organization, and fill in your details and processes. Below are several examples or templates you can download for free, which can give you a head start.
1. Cynet Incident Response Plan Template
Created by: Cynet
Pages: 16
Main sections:
- Incident Response Team Responsibilities
- Testing and Updates
- Incident Response Process Overview
- Incident response checklists: Incident Discovery and Confirmation, Containment and Continuity, Eradication, Recovery, Lessons Learned
- Overview of responsibilities per role
- Threat classification guide
- Compliance guide
2. NIST
Created by: National Institute of Standards and Technology
Pages: 79
Main sections:
- Organizing Incident Response
- Handling Incidents
- Coordination and Information Sharing
- Incident Handling Scenarios
Learn more about NIST incident response
3. Berkeley University
Created by: Berkeley University
Pages: 7
Main sections:
- IT systems overview
- Security definitions
- Contact people
- Incident response procedures
4. IltaNet Incident Response Plan
Created by: International Legal Technology Association
Pages: 5
Main sections:
- Incident response team
- Incident response notifications
- Employee responsibilities
- Types of incidents
- Definition of a security breach
- Classification procedure for potential incidents
- Response procedure
- Recovery
- Periodic testing and remediation
Download .ASHX file (gated, requires registration or login)
5. Thycotic Incident Response Plan Template
Created by: Thycotic
Pages: 19
Main sections:
- Roles, responsibilities, and contact info
- Threat classification
- Compliance and legal obligations
- Phases of incident response and actions taken.
Get .DOC file (requires registration)
6. Sysnet Security Incident Response Plan
Created by: Sysnet
Pages: 11
Main sections:
- How to recognize a security incident
- Roles and responsibilities
- External contacts
- Payment cards—what to do if compromised
- Incident response steps
- Report, investigate, inform
- Maintain continuity
- Resolve and recover
- Review
- Specific incident response types
- Malware
- Tampering with payment terminals
- Unauthorized wireless access points
- Loss of equipment
- Noncompliance with security policies
- Testing and periodic updates for IR plan
Get .DOC file (requires registration)
7. California Government Department of Technology Incident Response Plan
Created by: California Government Department of Technology
Pages: 4
Contents: 17-step incident response procedure, referencing more detailed plans for specific incident types such as malware, system failure, active intrusion attempt.
8. Case IQ Response Template
Created by: I-Sight
Pages: 6
Main sections:
- Purpose
- Scope
- Definitions and examples of incidents
- Roles & responsibilities
- Incident response stages and procedures
Best Practices for Creating an Incident Response Plan
Ready to build your own incident response plan? Here are the best practices we recommend following:
- Define Clear Roles and Responsibilities – Clearly assign roles so everyone knows what to do when an incident occurs. A RACI chart (Responsible, Accountable, Consulted, Informed) can help. It’s also recommended to assign backups for each role.
- Establish a Simple, Repeatable Process – Make your plan easy to follow even under pressure. Flowcharts, checklists, and playbooks can assist in breaking down responsibilities and tasks.
- Prioritize Threat Scenarios and Impact Levels – Not every incident is a “drop everything” situation. Define incident categories and escalation thresholds based on business impact (if you have a risk register, this can help). This helps teams respond proportionately without causing unnecessary panic or delays.
- Build and Maintain an Incident Communication Plan – Communication can streamline or severely disrupt a response effort. Create pre-approved templates for internal updates, external notifications, and regulatory disclosures.
- Include Third-Party and Contractor Considerations – Many incidents today involve and impact the software supply chain. Your plan should address how you’ll coordinate with external vendors during an incident, including who is responsible for what and under which SLAs.
- Document Legal and Compliance Requirements – Understand your notification deadlines for GDPR, HIPAA, SEC, or any other regulation. Create a clear checklist of legal obligations tied to different types of breaches and determine how they are enacted.
- Practice Regularly with Tabletop Exercises – An incident response plan is useless if no one knows how to use it. Run tabletop simulations at least twice a year, involving different teams and leadership. Focus on practicing technical mitigation, communication flow, and decision-making.
Why is Automated Incident Response Important?
Incident response templates and procedures are crucial, but they are not enough. In most organizations there is a critical shortage of security staff. It is impossible to review all alerts, not to mention investigate and respond to all security incidents. Statistics show that the average time to identify and remediate a breach is over 100 days.
To help address this problem, the security industry is developing tools to perform automated incident response. An automated tool can detect a security condition, and automatically execute an incident response playbook that can contain and mitigate the incident. For example, upon detecting traffic from the network to an unknown external IP, an incident playbook runs, adding a security rule to the firewall and blocking the traffic until further investigation.
By supplementing manual incident response with automated playbooks, organizations can reduce the burden on security teams, and respond to many more security incidents, faster and more effectively.
Tips From Expert
- Customize and Integrate: Ensure your IRP template aligns with your unique organizational environment and integrates seamlessly with existing security protocols.
- Regularly Update: Keep your IRP up-to-date to address evolving threats and changes in your IT infrastructure.
- Conduct Exercises: Validate your IRP through tabletop exercises to identify gaps and ensure your team is prepared.
- Automate Where Possible: Automate responses to common threats using playbooks, freeing up your security team for more complex issues.
- Measure and Improve: Incorporate metrics to track IRP effectiveness and use the data for continuous improvement and threat hunting.
Automated Incident Response with Cynet
Cynet provides a holistic solution for cybersecurity, including Cynet Response Orchestration (SOAR), which can automate your incident response. You define automated incident response playbooks, with pre-built remediation procedures for multiple attack scenarios. When an attack scenario occurs, the relevant playbook is automatically executed. Only if there is no matching playbook, the incident is pushed to the security team for a manual response.
Cynet Response Orchestration can address any threat that involves infected endpoints, malicious processes or files, attacker-controlled network traffic, or compromised user accounts.
Learn more about Cynet Response Orchestration.
FAQs
In the event of a cyberattack, data breach, or IT disruption, having a structured plan in place ensures that your team knows exactly what to do, who is responsible for what, and how to contain and recover from the incident. This minimizes damage, panic, stress, downtime, and data loss. Sometimes, an incident response plan is also a compliance requirement.
Start by selecting an incident response plan that aligns closely with your industry, size, and risk profile. Then, tailor it to your organization’s specific infrastructure, tools, and regulatory obligations. Involve stakeholders from IT, security, legal, HR, and executive leadership to ensure the plan is comprehensive and reflects real-world operational realities. Finally, conduct tabletop exercises regularly to reinforce familiarity and improve response time.
Small business templates tend to focus on simplicity, affordability, and scalability. They often provide basic structures with fewer personnel roles, lighter documentation, and less reliance on complex tools or third-party integrations. Enterprise-grade templates are far more granular and complex. They account for distributed teams, multiple departments, regulatory nuances, extensive IT infrastructure, and the need for automation and integration with existing security stacks.
An incident response plan is the overarching document that outlines your organization’s overall strategy and process for handling security incidents. A playbook dives into the “how” for specific incident types. For example, you might have separate playbooks for phishing, ransomware, insider threats, or data breaches.
Starting with a downloadable template is the better approach, especially for teams that are creating their first incident response plan or lack the in-house expertise to build one from the ground up. Then, invest in refining it to make it your own.
Your incident response plan should be reviewed and updated at least annually. More frequent updates are advisable if your organization is going through major changes. For example, if you adopt new technologies, restructure teams, onboard third-party vendors, or experience a significant incident, your plan should be immediately reassessed to reflect those changes.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response