Malware Protection: 6 Technologies to Protect Your Organization
Malware is a business-critical threat, as it can steal sensitive information, gain unauthorized access, encrypt data, and cripple systems. Legacy antivirus tools are not effective against modern malware. In this guide, we break down the technologies and techniques that can help your organization detect, prevent, and respond to advanced malware attacks. Whether you’re in IT, security, or an MSSP, these are the tools you need in your malware protection stack today.
What Is Malware Protection?
Malware is a software program designed to perform malicious activities. Different types of malware have different capabilities, such as monitoring browser activity, granting remote access to a computing device, stealing sensitive information, and encrypting data in exchange for a ransom.
Many malware infections occur through social engineering methods, in which attackers coerce users into clicking links to malicious websites or opening malicious email attachments. Other ways in which malware infects devices include drive-by downloads (triggered without any user action on a compromised website), installation of seemingly benign programs that deploy malware, and exploitation of vulnerabilities in software and communication protocols.
Malware protection is the tools, technologies, and processes that prevent malware, protect against it, and remove it from systems and devices. The first generation of malware protection tools, available since the 1980s, is antivirus software. These tools use signature-based malware detection, where the tool blocks and removes software that matches known malware signatures.
On top of these, new technologies like next generation antivirus (NGAV) add several more layers of protection. They perform behavioral analysis, based on machine learning algorithms, which can help identify new malware that does not match any known signature.
What are the signs that a system may be infected with malware?
A system or device infected by malware operates differently than before. Below is a list of telltale signs that can be used to detect it. However, for some of these indicators, one sign alone doesn’t always mean malware. Therefore, it’s important to spot patterns or clusters of these indicators.
Potential malware indicators:
- Slow Performance – Applications and systems take longer to load than usual.
- Frequent Crashes or Freezes – Programs or the entire OS crash unexpectedly or lag without explanation.
- Unusual Pop-Ups or Ads – Intrusive ads appear, in and out of the browser.
- New or Unknown Programs – Unfamiliar software appears. Take notice, especially if it launches at startup or can’t be uninstalled easily.
- High Resource Usage – The CPU, memory, or disk usage spikes without any open applications.
- Excessive Hard Drive Activity – The drive light blinks constantly even when not using the machine.
- Strange Network Activity – Unexpected outbound connections occur, especially to unfamiliar IPs or foreign servers.
- Unauthorized Access or Activity – Unauthorized logins, account activity, file modifications, or emails or messages sent without user input.
- Browser Redirects or Changes – The homepage or search engine changes without permission, or browsing is redirected to unfamiliar sites.
- Disabled Security Tools – The antivirus or firewall is turned off or won’t update.
Related content: Read our guide to malware prevention, dll malware, redline stealer.
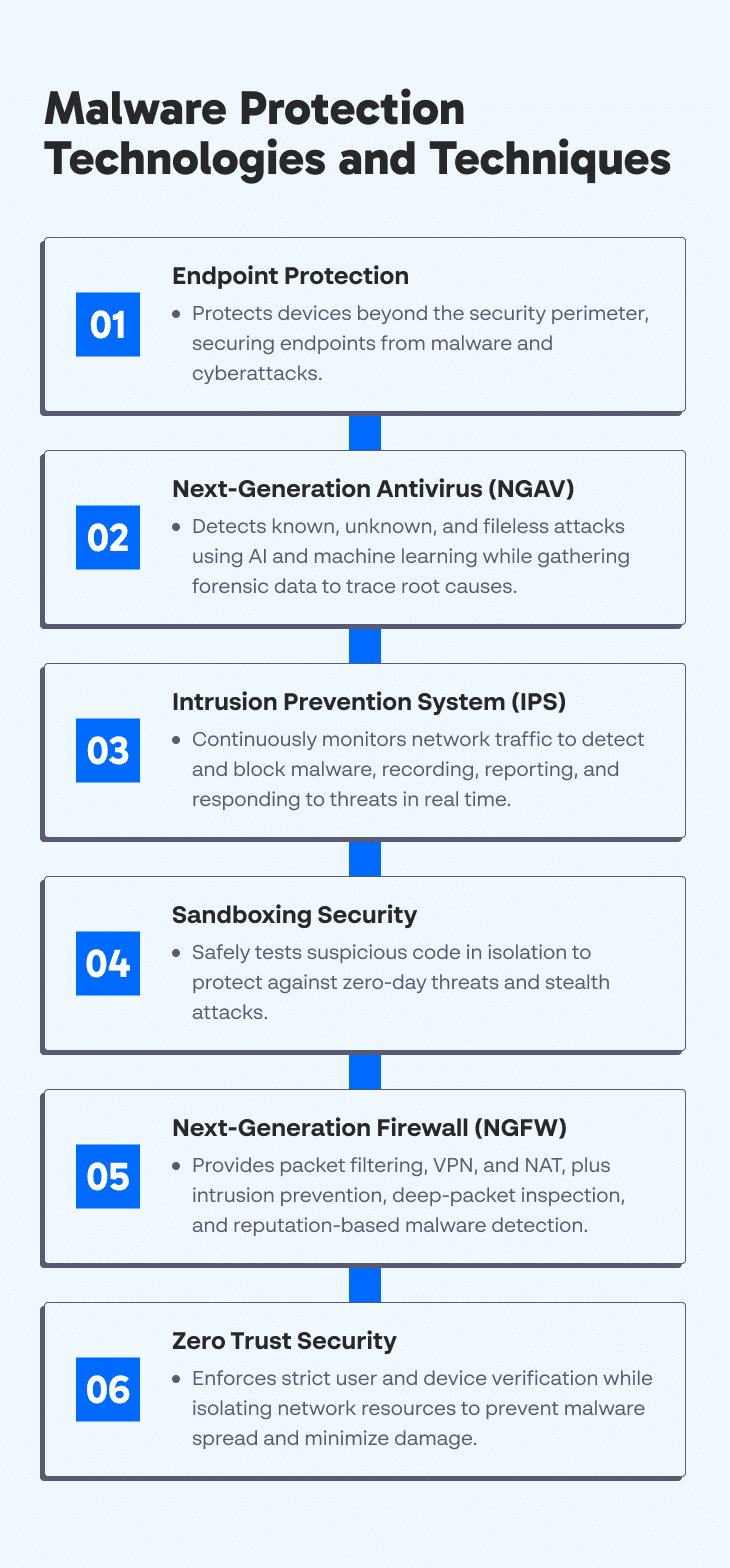
Malware Protection Technologies and Techniques
1. Endpoint Protection
Endpoint protection tools provide security coverage to prevent endpoint breaches and protect IT (IT) systems against endpoint threats, including malware infections and various cyberattacks.
Endpoint protection extends visibility into devices that are traditionally outside the security perimeter, such as personally-owned laptops and tablets used for work purposes, as well as company-owned servers and workstations.
Learn more in our detailed guide to sunburst attack and Emotet analysis.
2. NGAV
Next-Generation Antivirus (NGAV) solutions monitor and respond to attacker tactics, techniques, and procedures (TTPs) to help prevent both known and unknown threats. This technology was created to fill in the gaps left by traditional antivirus software that can only defend against known, file-based malware attacks.
NGAV technology offers a cloud-based, system-centric approach. It employs predictive analytics powered by machine learning (ML) and artificial intelligence (AI) in combination with threat intelligence to detect attacks, collect forensics data, and respond to threats. NGVA can identify fileless non-malware attacks, malicious behaviors, and malware, respond to threats, and collect endpoint data to determine the root cause.
3. Intrusion Prevention System (IPS)
An intrusion prevention system (IPS) continuously monitors network traffic to identify an ongoing malware infection or security breach. It can also perform response actions during specific cases that were pre-defined by the network administrator.
IPS continually monitors the network in real-time to quickly identify and respond to potential threats, performing prevention actions for observed events. It works by examining network traffic flows for malicious software. The technology identifies malicious activities, records detected threats, reports detected threats, and takes preventative actions to block the threat.
4. Sandboxing Security
Sandboxing security provides an additional layer of protection against security threats. It involves using a sandbox, an isolated environment mimicking end-user operating environments, to execute suspicious code.
A sandbox provides a safe environment that separates the threat from the host device or network. It is particularly useful when dealing with zero-day malware and stealth attacks, ensuring you can isolate and check these threats to prevent them from spreading.
5. Next-generation Firewall (NGFW)
A next-generation firewall (NGFW) enforces security policies to detect and block sophisticated attacks at the protocol, port, and application levels. You can implement this third-generation firewall technology in hardware or software.
Data traversing the Internet or a network is split into small pieces called packets. Firewalls inspect these packets because they contain content requesting to enter the network. The firewall is responsible for blocking or allowing packets, working to prevent malicious content, including malware, from entering the network.
NGFWs employ traditional firewall capabilities alongside new and improved features. Traditional capabilities include:
- Packet filtering
- Port address translation (PAT)
- Network address translation (NAT)
- Virtual private networks (VPNs)
- URL blocking
NGFW extends the above with quality of service (QoS) functionality and additional features, such as:
- Intrusion prevention
- Deep-packet inspection
- SSL and SSH inspection
- Application awareness
- Reputation-based malware detection
6. Zero Trust
The zero trust model is a security approach that removes implicit trust and enforces strict user and device authentication to protect the network. It helps provide strong protection against various attacks, including data theft and compromised credentials. Zero trust implementations often employ role-based policies to enforce strict authentication and authorization rules.
This model assumes that trusting individuals or devices can cause many vulnerabilities, as even authorized parties can become compromised. The network should never trust any user and require identity and device authentication throughout the network, and not only at the perimeter.
Implementing zero trust security typically involves using microsegmentation to separate network resources. Isolating resources helps contain threats within one microsegment of the network, preventing the threat from spreading to other areas. It minimizes the attack surface and reduces the scope of damage inflicted by an attack.
Zero trust helps create a more comprehensive defense against malware and ransomware attacks by providing extended monitoring and detection capabilities. Zero trust can significantly limit the ability of malware and ransomware to perform lateral movement and infect additional parts of a corporate network. In addition, since human error is often the root cause of a cyberattack, zero trust focuses on user identity and access management.
Learn more in our detailed guide to hafnium, squirrel waffle, quakbot.
Advanced Malware Protection vs. Traditional Antivirus: What’s the Difference?
Why Signature-based Tools are Not Enough
Traditional antivirus solutions detect malware by matching known code signatures to malware databases. These signature databases are continuously updated through threat intelligence feeds, community contributions, and inter-organizational sharing. This ongoing process ensures that antivirus engines can quickly recognize and block threats that align with known attack patterns, serving as an essential first layer of defense against common, well-understood threats.
However, while this method is fast and effective for threats that have already been cataloged, it completely misses:
- Zero-day threats and fileless malware
- Polymorphic malware that changes its signature
- Attacks that hide in memory or exploit trusted processes
Benefits of Behavior-based and AI-driven Anti-malware Systems
Advanced malware protection tools use machine learning and behavioral analysis to identify and stop threats, even if they’ve never been seen before. This complements signature-based malware protection. Here’s how it works:
- Behavioral detection monitors what programs do, not just what they are. Suspicious behavior like unusual encryption activity, registry changes, or privilege escalation gets flagged in real time.
- AI and machine learning models can predict whether a file is malicious based on patterns across millions of prior samples.
- Sandboxing and threat emulation allow systems to safely observe what happens when a file is executed, without risking the endpoint.
- Automated response mechanisms can isolate or remediate endpoints before an attack spreads.
7 Malware Protection Best Practices
After you deploy the best possible malware protection solutions, follow these best practices to better protect your organization against malware threats:
- Address vulnerabilities and misconfigurations—make sure both critical systems and user endpoints have the latest version of the operating system and software, and regularly deploy security updates and patches. Ensure all sensitive resources are protected by strong multi-factor authentication (MFA).
- Endpoint visibility—in a modern IT environment, corporate networks are accessed by many personal and unmanaged devices. It is important to implement tools that provide full visibility into the entire environment, detect anomalies, and alert on malicious activity anywhere on the network.
- Verify your data backup and recovery process—many types of malware, most notably ransomware, encrypt or destroy sensitive data. Backup is critical to avoid data loss. Ensure that your backup and restore processes are working properly and that backups are properly isolated from other systems to avoid malware from infecting them.
- Educate users—end users are the weakest link in the security chain for most organizations. Educate users about the threat of phishing and other social engineering techniques. Deploy email protection solutions, content filtering, and other tools that can help warn users when they are the subject of a social engineering attack.
- Network segmentation—it is critical to segment your network and create micro-perimeters against sensitive assets. This means that even if attackers compromise an endpoint by infecting it with malware, they cannot move laterally to infect other parts of the network.
- Restrict user and application permissions—follow the principle of least privilege, limiting the permissions assigned to an application or a specific user account on a device. Any entity on the network should only have permissions that are absolutely necessary to get its job done.
- Use threat intelligence—complementing antimalware and firewall solutions with threat intelligence feeds can help you detect attacks more effectively. It can also help identify that malware deployed on your network is communicating with command and control (C&C) servers by identifying the IP and domain of malicious traffic.
Learn more in our detailed guide to bladabindi, clipbanker, emotet analysis, defense evasion.
Tips From Expert
In my experience, here are tips that can help you better protect your environment from malware threats:
- Prioritize anomaly detection for rapid response. Implement user and entity behavior analytics (UEBA) to identify anomalous behavior that might signal a malware infection, especially those capable of bypassing signature-based detection. Look for deviations in network traffic, file access, or unusual system behavior.
- Use deception technology for malware diversion. Deploy honeypots and decoys within your network. These fake systems can attract malware, revealing attacks early before they can affect your production environment, and can also give you insights into attacker tactics.
- Apply a “memory protection” layer for fileless threats. Invest in tools that offer memory-based exploit protection, as modern malware often operates in-memory without leaving a file signature. This helps defend against sophisticated malware like fileless attacks, which traditional antivirus cannot detect.
- Incorporate threat hunting programs. Regularly conduct proactive threat hunting to search for dormant malware, particularly advanced persistent threats (APTs). This process can uncover malware that has evaded other defenses by analyzing logs, traffic patterns, and endpoint behavior.
- Deploy DNS security to block malicious communications. Use DNS-based security solutions to prevent devices from reaching command-and-control (C2) servers. DNS-layer defenses can disrupt malware communications and block further actions, such as data exfiltration or lateral movement.
What Should You Look For in a Malware Protection Tool?
When choosing a malware protection tool, the goal is to go beyond basic antivirus and find a solution that provides comprehensive, adaptive, and real-time defense. Here are the key capabilities and features to look for:
- Behavior-Based Detection – Signature-based detection is outdated on its own. You need a tool that can monitor app and endpoint behavior in real time and flag anomalies like unusual memory use, unauthorized file changes, unusual process requests, or privilege escalations. This will enable protection against known and zero-day exploits.
- Machine Learning & AI Capabilities – Advanced tools use AI to detect threats before signatures are available. This is done by analyzing millions of data points and identifying malicious patterns and behavior.
- Threat Intelligence – Choose a tool that incorporates real-time feeds from global threat intel sources. This ensures faster detection of emerging threats and zero-days.
- Multi-Layered Malware Prevention – Find a tool that provides a combination of measures, e.g, machine learning-based static file analysis, behavior monitoring, and threat intelligence (explained above), along with sandboxing and fuzzy hashing.
- Ransomware & Exploit Protection – The tool should actively block unauthorized encryption attempts, roll back files to pre-attack state (if compromised), and monitor vulnerable applications for exploit behavior.
- Automated Response & Containment – The best tools can isolate infected devices automatically, kill malicious processes in real time, and remediate without needing manual intervention every time. In addition, the tool should be able to prevent payloads from executing even if malware was downloaded, to prevent lateral movement.
- Kill Chain Detection and Visibility – The tool should be able to detect threats across the entire kill chain: endpoints, networks, the cloud, etc.
- Centralized Management & Visibility – For ease of use and governance, look for a tool that offers a single console for policy enforcement and dashboards.
Advanced Malware Protection with Cynet
The Cynet Advanced Threat Detection and Response platform provides protection against threats, including zero-day attacks, advanced persistent threats (APT), advanced malware, and trojans that can evade traditional signature-based security measures.
Block exploit-like behavior
Cynet monitors endpoints’ memory to discover behavioral patterns that are typical of an exploit such as an unusual process handle request. These patterns are common to the vast majority of exploits, whether known or new, and provide effective protection even from zero-day exploits.
Block exploit-derived malware
Cynet employs multi-layered malware protection that includes ML-based static analysis, sandboxing, and process behavior monitoring. In addition, they provide fuzzy hashing and threat intelligence. This ensures that even if a successful zero-day exploit establishes a connection with the attacker and downloads additional malware, Cynet will prevent this malware from running so no harm can be done.
Uncover hidden threats
Cynet uses an adversary-centric methodology to accurately detect threats throughout the attack chain. Cynet thinks like an adversary, detecting behaviors and indicators across endpoints, files, users, and networks. They provide a holistic account of the operation of an attack, irrespective of where the attack may try to penetrate.
Reduce noise and respond faster
Cynet uses a powerful correlation engine and provides its attack findings with near-zero false positives and is free from excessive noise. This simplifies the response for security teams so they can react to important incidents.
You can carry out automatic or manual remediation, so your security teams have a highly effective yet straightforward way to detect, disrupt, and respond to advanced threats before they have a chance to do damage.
Learn more about Cynet’s Endpoint Security Solution.
Learn more in our detailed guide to emotet malware, china chopper.
Learn More About Malware Protection
Zeus Malware: Variants, Methods and History
Zeus is one of the most dangerous and globally widespread network security threats. It has allowed attackers to obtain user credentials to financial systems, and actually steal funds from the bank accounts of millions of people.
Learn about the dangerous and globally-spread Zeus malware, which infects machines, steals financial credentials and illicitly transfers funds.
Read more: Zeus Malware: Variants, Methods and History
Malware Prevention: A Multi-Layered Approach
Malware, or “malicious software,” is a general term describing any program created to disrupt or unlawfully retrieve information from a computer system.
Get a modern definition of malware, examples of malware attacks, and 5 steps to creating a multi-layered security posture.
Read more: Malware Prevention: A Multi-Layered Approach
4 Malware Detection Techniques and Their Use in EPP and EDR
Threat actors employ malicious software, known as malware, to perform certain malicious activities. There are numerous types of malware, each deployed to achieve different objectives. For example, spyware aims to gather information from computing devices, trojans aim to gain a persistent hold on a computer system, and ransomware aims to encrypt information and extort its owners.
Learn about innovative static and behavioral malware detection techniques and how they are used in modern endpoint protection solutions.
Read more: 4 Malware Detection Techniques and Their Use in EPP and EDR
9 Types of Malware Attacks and What You Can Do About Them
Malware is a program or file that intentionally damages or grants unauthorized access to a computer system. In other cases malware is used to destroy or steal sensitive data. Malware can infect devices, operating systems, and networks. Depending on the type and purpose of the malware, infection can have different levels of impact on users, endpoints, and organizations.
Learn about the main types of malware attacks including ransomware, fileless attacks, trojans, and rootkits, and discover critical best practices to prevent them.
Read more 9 Types of Malware Attacks and What You Can Do About Them
See Additional Guides on Key Information Security Topics
MSSP Security
- [Guide] What Is an MSSP (Managed Security Service Provider)?
- [Guide] MSP vs. MSSP: Understanding The Difference
- [Product] Cynet for MSSPs | Cybersecurity Platform for Managed Security Service Providers
NIST Cybersecurity Framework
FAQs
The best protection comes from a layered security strategy. This means combining anti-malware tools with proactive user education, strong access controls, EDR regular patching, and network segmentation. In addition, use malware protection tools that leverage behavior-based and AI-driven defenses.
Modern anti-malware tools rely on heuristic analysis, behavioral monitoring, and AI models. Instead of waiting for a known virus signature, they look at how a file or process behaves (e.g., encrypting files, modifying system settings) and compare it to patterns seen in previous threats. Cloud-based threat intelligence and sandboxing also help these tools analyze suspicious activity in real time, even for threats that haven’t been publicly identified yet.
Daily scheduled scans are recommended, along with real-time protection that’s always running in the background. Full system scans can be scheduled weekly or bi-weekly, depending on device usage and sensitivity. For critical infrastructure or endpoints handling sensitive data, more frequent or continuous scanning may be warranted.
No system can offer 100% prevention, but strong anti-malware software significantly reduces the risk of ransomware attacks. Advanced tools can detect encryption attempts, isolate affected devices, and roll back files to a safe state.
If malware is detected, act fast. First, isolate the infected device(s) from the network to stop lateral spread. Then, run a full scan using updated anti-malware software and follow up with forensic tools or your EDR platform to understand the scope of the infection. Remove the malware, change any potentially compromised credentials, and notify relevant teams. Finally, patch vulnerabilities, restore from clean backups if needed, and document the incident for future prevention.
Anti-malware software should be updated automatically and continuously. Most vendors release signature updates multiple times a day, and behavior or AI model updates on a rolling basis. Make sure endpoints are connected to the internet and that auto-update settings are enabled. Delays can leave systems vulnerable to fast-moving threats or new variants that slip past outdated defenses.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response