Achieved 100% protection in 2024
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
SIEM (Security Information and Event Management) is a security technology that provides real-time analysis of logs and alerts generated by security tools, applications, and network hardware. It assists organizations in identifying, monitoring, recording, and analyzing security events or incidents within their IT environment. SIEM systems aggregate and examine log data—everything from Syslog messages, network and traffic data, to DNS records and endpoint system reports—to support threat detection, compliance, and security incident management.
By centralizing data storage and analysis, SIEM systems provide a consolidated view of the security posture of an organization’s IT infrastructure. They allow for the proactive management of network security through the collection and correlation of logs. This approach helps detect and respond to security threats swiftly, enhancing the overall security resilience of organizations.
This is part of an extensive series of guides about data breach.
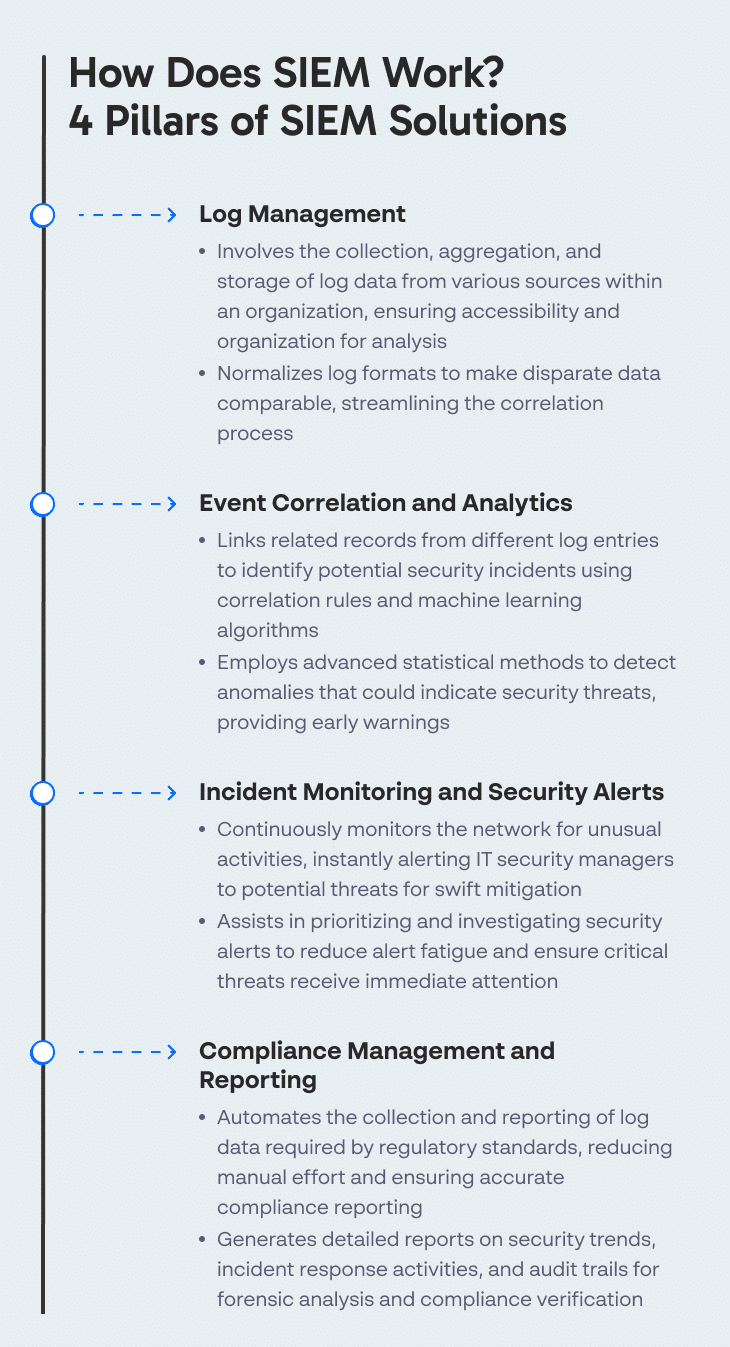
Log management is crucial in SIEM architecture; it involves the collection, aggregation, and storage of log data from various sources within an organization’s IT ecosystem. This process ensures that the data remains accessible and organized for analysis. By managing logs, SIEM solutions help organizations maintain a comprehensive record of activity, which is critical for understanding the context of security incidents and for meeting regulatory compliance requirements.
Efficient log management entails the normalization of log formats, which makes disparate data comparable and analyzable. SIEM systems transform logs from different systems into a common format to streamline the correlation process.
Event correlation in SIEM involves linking related records from different log entries to identify potential security incidents. By applying correlation rules, analyzing patterns, and applying machine learning algorithms, SIEM tools automate the detection of activities that might indicate a compromise. For example, multiple failed login attempts followed by a successful login from an unusual location might be combined into a single security event. This helps in distinguishing real threats from false positives, optimizing the alerting process.
Event analytics further enhance SIEM capabilities by employing advanced statistical methods and machine learning techniques to analyze behavior patterns across the network. This proactive approach allows detecting anomalies that could elude traditional detection methods, providing an early warning system for potential security threats.
SIEM systems continuously monitor the network for unusual activities that could suggest security incidents. By leveraging integrated real-time data monitoring and complex event correlation, these systems instantly alert IT security managers about potential threats, enabling swift mitigation actions.
Post detection, SIEM tools also assist in the prioritization and investigation of security alerts. This reduces alert fatigue—a common challenge in security operations centers (SOCs)—and ensures that the most critical threats receive immediate attention. Timely intervention is crucial in managing and mitigating breaches effectively.
SIEM facilitates compliance management by automating the collection and reporting of log data required by regulatory standards like HIPAA, PCI-DSS, GDPR, and more. This automation significantly reduces the manual effort and potential human error, ensuring accurate and consistent compliance reporting.
Additionally, SIEM systems generate detailed reports that provide insights into security trends, incident response activities, and audit trails for forensic analysis. These reports are vital for audits and for making informed decisions about security policies and processes. They also offer proof of compliance to regulators and stakeholders, demonstrating an organization’s commitment to security best practices.
Learn more in our detailed guide to SIEM solutions.
Security Information and Event Management (SIEM) and Security Operations Centers (SOC) are both crucial elements in modern cybersecurity frameworks. SIEM provides the tools and software solutions for logging and analyzing security data, while SOC refers to the team and facilities dedicated to continuous monitoring and analysis of an organization’s security posture. Essentially, SIEM is a component that facilitates the operational processes of a SOC.
A SOC utilizes SIEM tools to collect, analyze, and respond to cybersecurity incidents. The efficiency of a SOC, therefore, heavily depends on the effectiveness of its SIEM solutions. However, SIEM software can be implemented without a dedicated SOC, and likewise, a SOC might utilize different tools aside from SIEM.
Tips From the Expert
In my experience, here are tips that can help you better leverage SIEM solutions for security and threat management:
The central dashboard is a central feature of SIEM tools, providing a unified view of all collected security data. This dashboard is crucial for system administrators to quickly assess and interpret a diverse set of information sources, from logs to real-time alerts. The ability to customize dashboards according to specific security or operational needs is one of the major strengths of SIEM systems.
Moreover, the real-time data visualization offered by these dashboards helps in identifying trends and potential threats swiftly. This makes it easier for security teams to act based on current insights, streamlining the decision-making process during a security incident.
SIEM systems enhance security by monitoring user activities across the network. This monitoring helps in detecting suspicious behaviors, such as unauthorized access attempts or deviations from typical usage patterns, which might indicate a security threat or a breach. By maintaining comprehensive logs of user actions, SIEM aids in forensic analysis and helps determine the scope and impact of a security incident.
Additionally, user activity monitoring is crucial for enforcing corporate policies and regulatory requirements. By ensuring that user actions are consistently recorded and auditable, SIEM systems help organizations uphold security standards and protect sensitive data against internal threats.
Threat intelligence is a key component of SIEM, providing context-rich information about emerging or existing threats. This information typically encompasses details about threat actors, the mechanisms they employ, and the vulnerabilities they exploit. Integrating threat intelligence feeds into SIEM systems enriches the data analysis, enabling more precise detection of sophisticated attacks and offering actionable insights for proactive defense strategies.
Furthermore, regular updates from diverse threat intelligence sources ensure that the SIEM system can adapt to a changing threat landscape, identifying new threat actors and attack patterns.
Advanced analytics and machine learning are at the forefront of enhancing SIEM solutions by enabling the identification of complex patterns and predictive analysis. Machine learning algorithms can analyze vast amounts of data at high speed, learning from historical trends to identify deviations indicative of potential threats. This capability not only increases the accuracy of threat detection but also reduces false positives.
Applying advanced analytics to SIEM processes involves parsing through and making sense of massive data sets to discern subtle correlations that might elude human analysts. This approach significantly aids in preemptive threat detection and proactive security measures.
Learn more in our detailed guide to siem cyber security.
Advantages of SIEM systems include:
Disadvantages of SIEM systems include:
Learn more in our detailed guide to elastic siem.
Splunk Enterprise Security is a SIEM solution that provides deep visibility into security data by ingesting, normalizing, and analyzing information from various sources at scale. It enhances operational efficiency and improves threat detection by integrating assistive AI capabilities, ensuring that security teams can respond to incidents with accurate and context-rich information.
Features of Splunk Enterprise Security include:
Source: Splunk
IBM QRadar Suite is a threat detection and response system with SIEM at its core. It optimizes the detection, investigation, and management of cybersecurity threats using artificial intelligence (AI) and automation. The solution integrates security functionalities such as security information and event management (SIEM), and security orchestration, automation, and response (SOAR).
Features of IBM QRadar Suite include:
Source: IBM
Elastic Security for SIEM & Security Analytics is an open SIEM solution that improves security operations by leveraging the big data capabilities of the Elastic Stack. It enhances threat detection, investigation, and response by providing deep visibility across hosts and utilizing generative AI to boost team productivity. It can handle up to petabytes of security data.
Features of Elastic Security for SIEM & Security Analytics include:
Source: Elastic
OpenText ArcSight Enterprise Security Manager (ESM) is a scalable SIEM platform designed for real-time threat detection and response. It integrates a robust correlation engine and native Security Orchestration, Automation, and Response (SOAR), enabling security analysts to quickly detect, react, and manage cybersecurity threats. It can be used for large scale environments, with the ability to process over 100,000 events per second.
Features of OpenText ArcSight Enterprise Security Manager include:
Source: OpenText
A clear understanding of the implementation scope is vital when deploying SIEM systems. It involves identifying the data sources, security tools, and organizational processes that will integrate with the SIEM. A thorough scope definition helps in designing a focused and effective implementation strategy that addresses specific security needs without overcomplicating the solutions.
Additionally, defining the scope aids in resource allocation, ensuring that the necessary tools and personnel are available to manage the SIEM system effectively. This preliminary step is crucial for setting realistic expectations and achieving measurable security improvements.
Identifying compliance requirements is an essential step in the SIEM implementation process. This involves understanding which regulatory standards apply to your organization and ensuring the SIEM solution can effectively support these requirements through adequate data processing, reporting, and archiving capabilities.
Fine-tuning correlation rules is crucial for the effectiveness of SIEM systems. This process involves customizing the rules according to specific security needs and operational context to improve threat detection accuracy and reduce false positives. Regular reviews and updates of correlation rules in response to evolving security landscapes are necessary to maintain their relevance and effectiveness.
Regular tuning of SIEM configurations is necessary to adapt to the continuously changing security environment. This includes updating rules, improving alert settings, and refining the system’s response strategies to better align with current threats. Ongoing maintenance ensures that the SIEM system remains effective over time, providing consistent and reliable security monitoring.
Thorough documentation and regular practice of incident response plans enhance an organization’s preparedness for dealing with potential security breaches. SIEM systems play a crucial role in this by providing the necessary logs and insights to inform and refine response strategies. Practicing these plans in simulation exercises helps identify gaps in the response workflow, allowing timely rectifications before real incidents occur.
Cynet provides the world’s first Autonomous Breach Protection platform that natively integrates endpoint, network and user attack prevention/detection of XDR with log management and analysis of CLM and automated investigation and remediation capabilities of SOAR, backed by a 24/7 world-class MDR service.
End to end, fully automated breach protection is now within reach of any organization, regardless of security team size and skill level. Most smaller businesses find that Centralized Log Management (CLM) is fully sufficient for their needs while far more affordable and usable than SIEM solutions.
Cynet can be deployed across thousands of endpoints in less than two hours. It can be immediately used to uncover advanced threats and then perform automatic or manual remediation, disrupt malicious activity and minimize damage caused by attacks.
Get a free trial of Cynet and experience the world’s only integrated XDR, CLM, SOAR and MDR solution.
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of data breach.
Authored by NetApp
Authored by Faddom
Search results for: