CyOps Threat Alert: OpenSSL Vulnerability
By Asher Davitadi, Sr. CyOps Analyst
On November 1st 2022, the OpenSSL project team released a new toolkit version: OpenSSL 3.0.7.
The new version was released to address mainly two email address buffer overflow vulnerabilities in the OpenSSL toolkit reported in mid-October 2022.
In their security advisory, the team indicated that OpenSSL 3.0.0 up to and including version 3.0.6 are vulnerable to DDOS and even RCE if set to verify X.509 certificates from untrusted sources. This means a malicious actor could implement a maliciously crafted email address in the untrusted X.509 certificate to exploit the vulnerability.
As many operating systems and applications use the OpenSSL toolkit, the Dutch NCSC released an overview of applications that have the toolkit built in. The overview indicates whether they’re affected or otherwise.
Report with Cynet Vulnerability Assessment
If you suspect a vulnerable application (like those listed in the NCSC-NL overview) is installed in your environment, use Cynet’s Vulnerability Assessment Reports. These assessments provide two different ways to report.
First, we can set an Unauthorized Applications profile to report on known vulnerable applications. Thanks to the Dutch NCSC overview, we know VMware Tools for guest VM is indicated as vulnerable at its latest version:
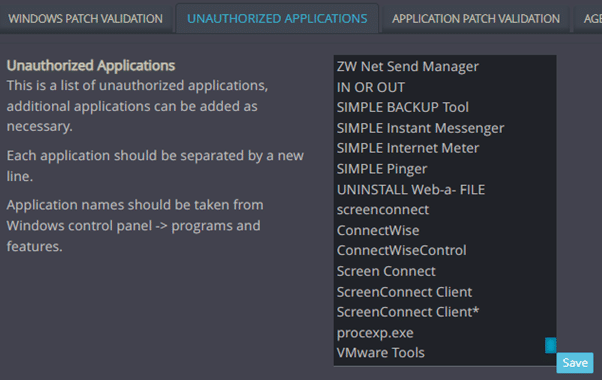
To report this application, enter Cynet settings, select the “Vulnerability Management” tab, and then “Unauthorized applications.”
Follow the instructions on the menu and add VMware Tools to the list (case sensitive):
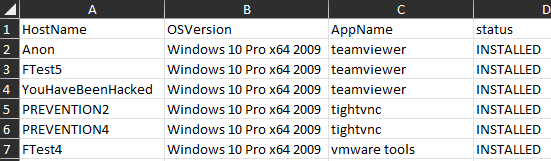
VMware Tools as seen in Windows, Apps & features menu:
Cynet VA – Unauthorized Applications report:
For applications with old vulnerable versions, Cynet’s Vulnerability Assessment Reports has the Application Patch Validation feature to report on the outdated applications you suspect is installed in your environment.
If you’d like to review the OpenSSL file occurrences scanned in your environment, use Cynet Forensics to search and list them. You can even create a file policy to open informative alerts for new OpenSSL occurrences in your environment.
To list OpenSSL file occurrences, open the Forensics page at Cynet console.
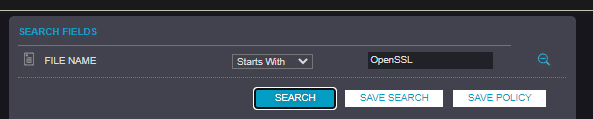
Under files, open the advanced search and set the search fields to
Filename: OpenSSL.
Click search to reveal the results (please take note of the last seen value of each occurrence, indicating relevancy):
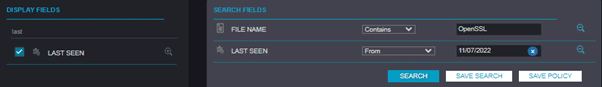
To trigger and open a new informative alert for each new occurrence of OpenSSL to your previously created search, please add the display field “Last seen” with “From” and set it to today’s date. This will open alerts only for new occurrences, filtering out old ones:
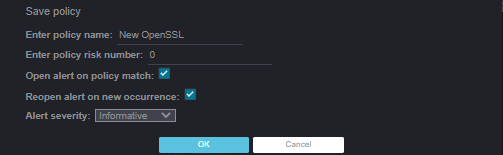
Once your fields are set, click “Save Policy” and fill in a policy (alert) name. Enable “Open alert on policy match” and “Reopen alert on new occurrence”. Select alert severity as “informative” and click OK to save it:
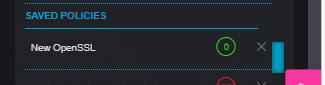
The new policy can be viewed in the “Saved Policies” list.
3 tips to keep your organization safe
The vast amount of use cases for the OpenSSL toolkit leads to many applications being vulnerable or at least untested.
To stay resilient, we recommend you:
- Setup Cynet as shown above to assist you in vulnerability management and alerting.
- Validate and confirm that all OpenSSL occurrences or dependent applications found are using version 3.0.7.
- Push to update to the latest versions or temporarily disable all applications that use OpenSSL versions 3.0.0 – 3.0.6.
Have questions about this vulnerability?
You can contact our CyOps team directly at:
CyOps Mailbox – [email protected]
Israel: +972 72-3369736
UK: +44 2032 909051
US: +1 (347) 474-0