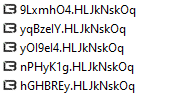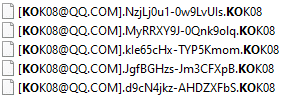July 2022 Ransomware Activity Report
Written by: Maor Huli
The ransomware introduced in July is:
- Loki
- BlueSky
- Babuk
- LockBit 3.0
- Matrix
EXECUTIVE SUMMARY
As an integral department in Cynet’s research team, Orion works around the clock to track threat intelligence resources, analyze payloads, and automate labs to protect our customers against the newest ransomware variants. In these monthly reports, Orion reviews the latest trends identified in Bleeping Computer — the most up-to-date website that summarizes the newest ransomware variants — and shares how Cynet detects against these threats.
CYNET 360 AutoXDR™ VS RANSOMWARE
Loki Ransomware
- Observed since: Late 2021
- Ransomware encryption method: AES + RSA
- Ransomware extension: .PayForKey
- Ransomware note: Restore-My-Files.txt
- Sample hash: f2522a56f9416eb701afc1773c08e9a3cc9143c8880954140e515f66a0028637
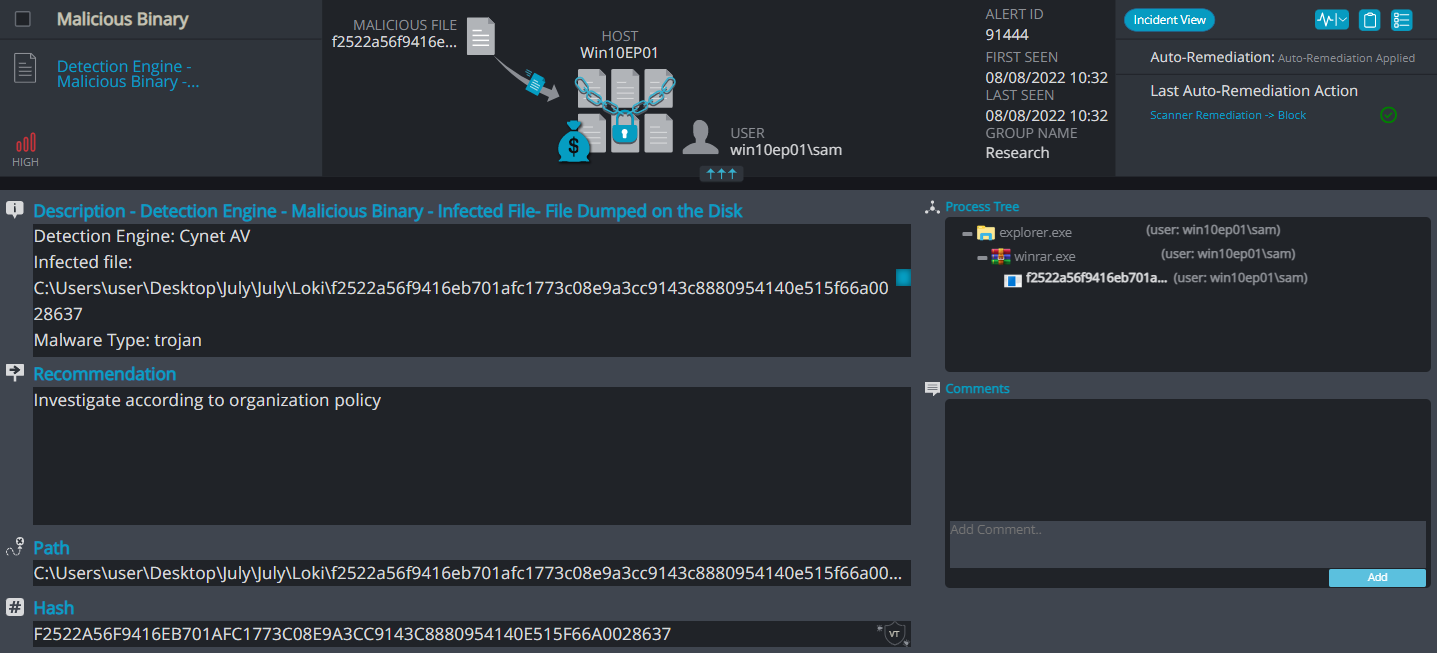
Cynet 360 AutoXDR™ Detections:
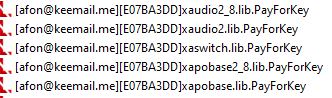
Loki ransomware renames the encrypted files with .PayForKey, along with the attacker’s email and the host ID in the extension.
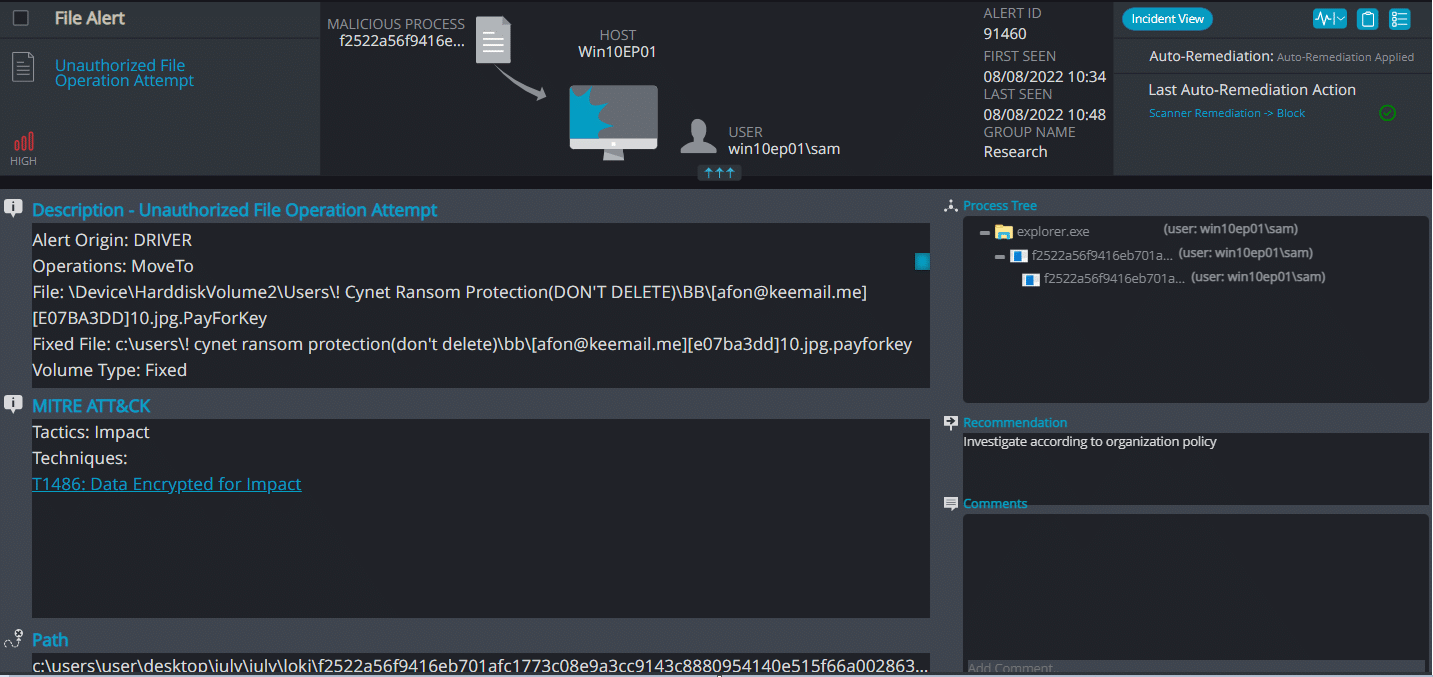
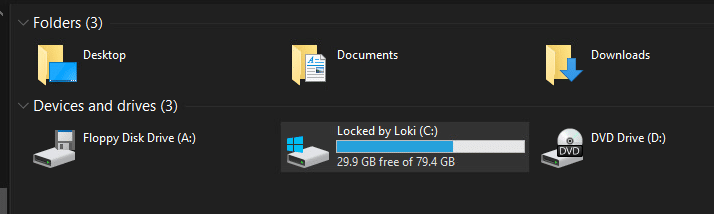
The ransomware also encrypts the entire Drive C: (the system drive):
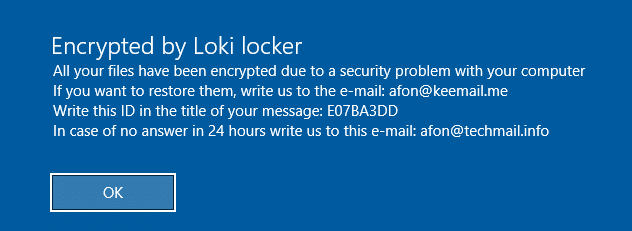
Eventually, it shuts down the computer and locks out the user until a payment:
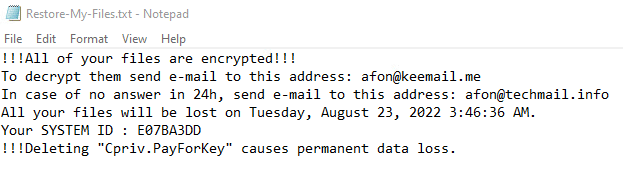
Once a computer’s files have been encrypted and renamed, it drops a note as Restore-My-Files.txt:
The ransomware note contains general information, warnings, and the attacker’s email address:
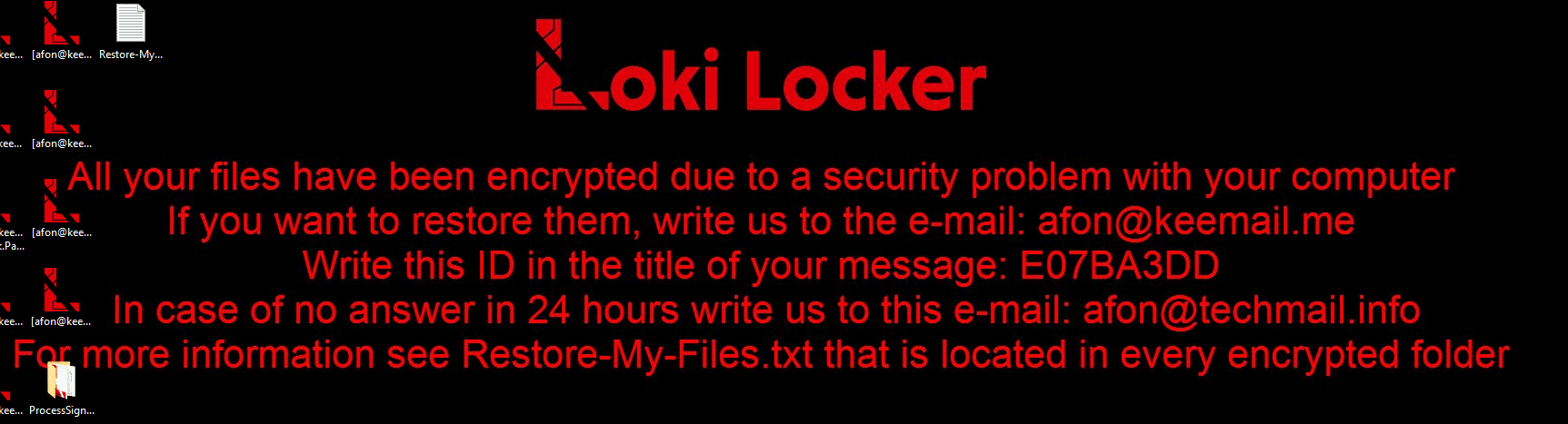
Before shutting down, the ransomware also changes the desktop background:
BlueSky Ransomware
- Observed since: 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .bluesky
- Ransomware note: # DECRYPT FILES BLUESKY #.txt | .html
- Sample hash: 3e035f2d7d30869ce53171ef5a0f761bfb9c14d94d9fe6da385e20b8d96dc2fb
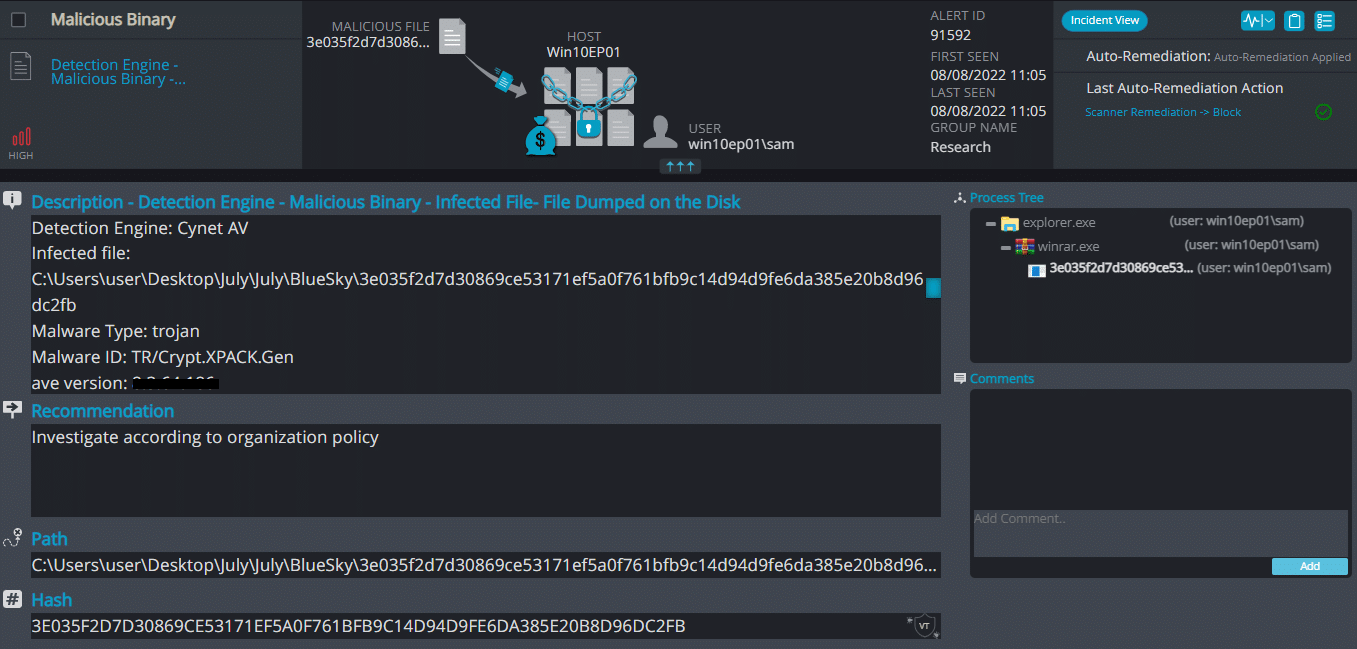
Cynet 360 AutoXDR™ Detections:
BlueSky ransomware renames the encrypted files with .bluesky in the extension:
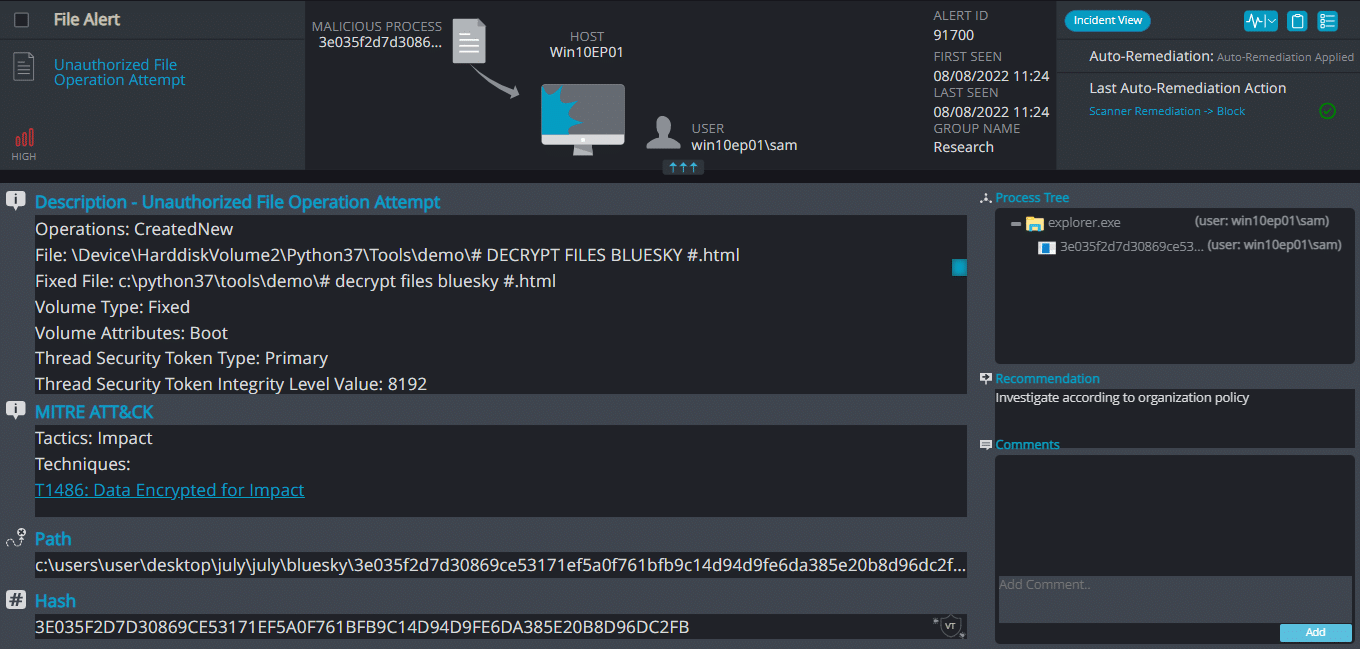
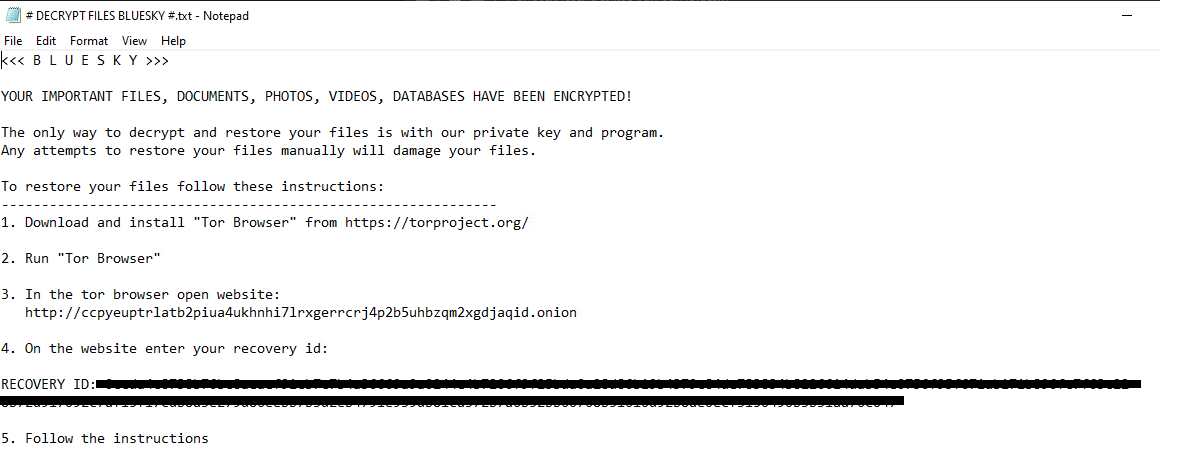
Once a computer’s files have been encrypted and renamed, it attempts to drop the ransomware note named # DECRYPT FILES BLUESKY #.txt | .html:
That ransomware note contains general information, warnings, and the attacker’s tor website:
Babuk Ransomware
- Observed since: Early 2021
- Ransomware encryption method: AES + RSA
- Ransomware extension: .again
- Ransomware note: How To Restore Your Files.txt
- Sample hash: 047a6c39806168e7e66b2ef2297b7019cc9e53364dc6b3ec3af830f9eea1f798
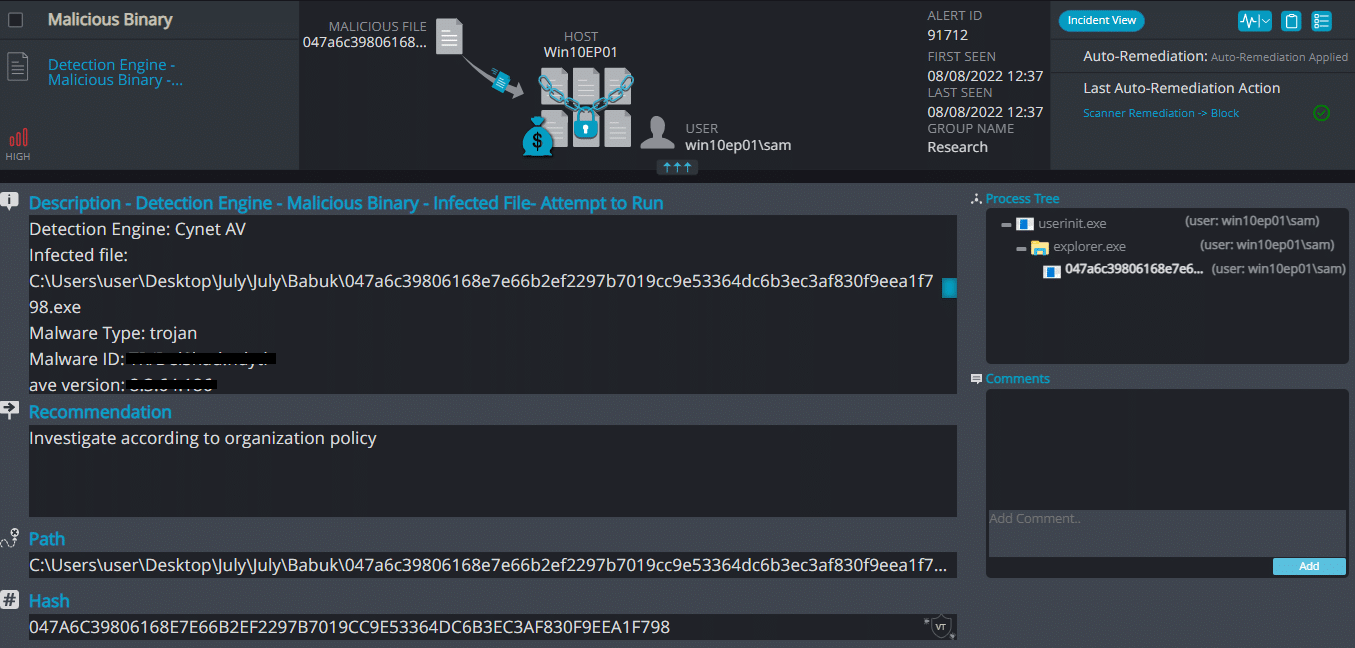
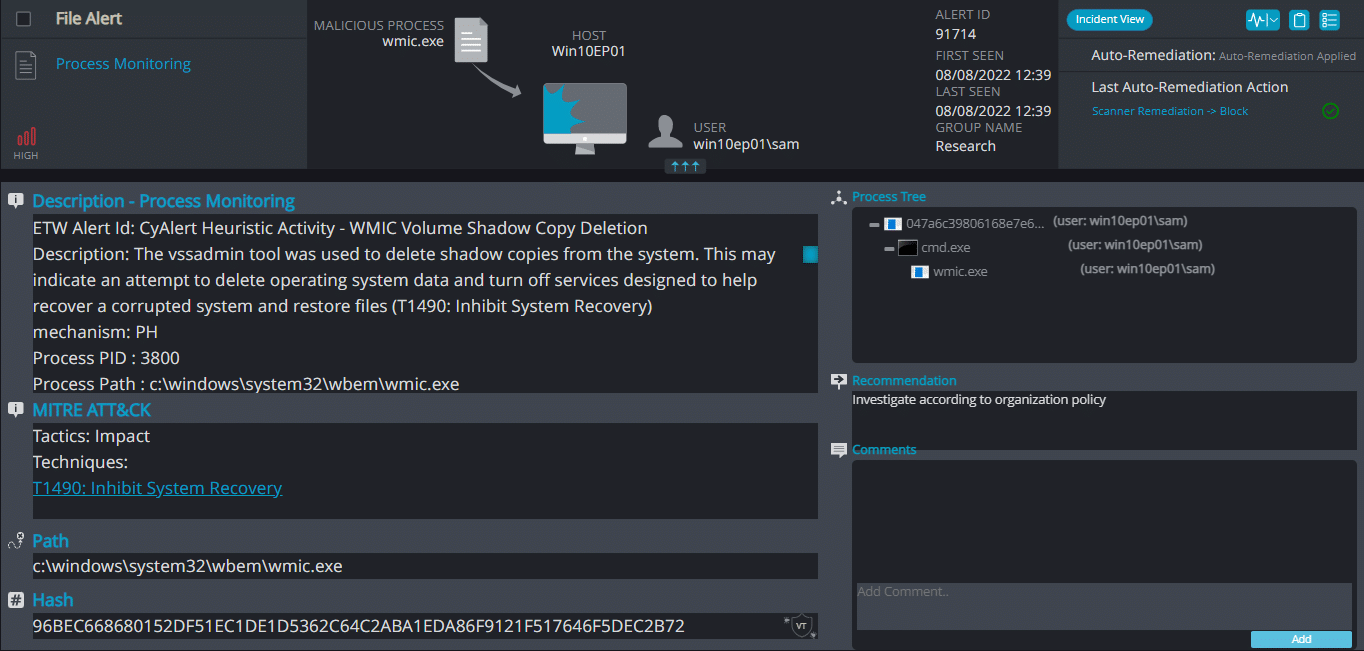
Cynet 360 AutoXDR™ Detections:
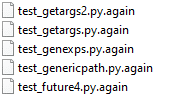
Babuk ransomware renames the encrypted files with .again in the extension:
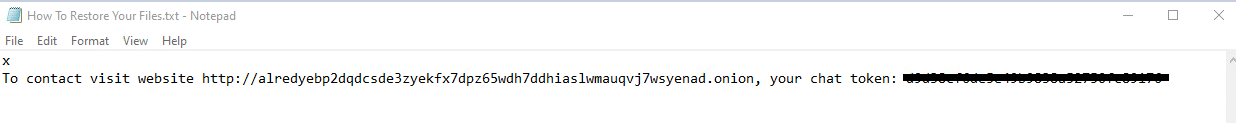
Once a computer’s files have been encrypted and renamed, it drops a note named: How To Restore Your Files.txt:
The ransom note contains only a tor website with a chat token to contact the attacker:
- Observed since: Mid 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .[a-zA-Z0-9]{9}
- Ransomware note: [a-zA-Z0-9]{9}.readme.txt
- Sample hash: 80e8defa5377018b093b5b90de0f2957f7062144c83a09a56bba1fe4eda932ce
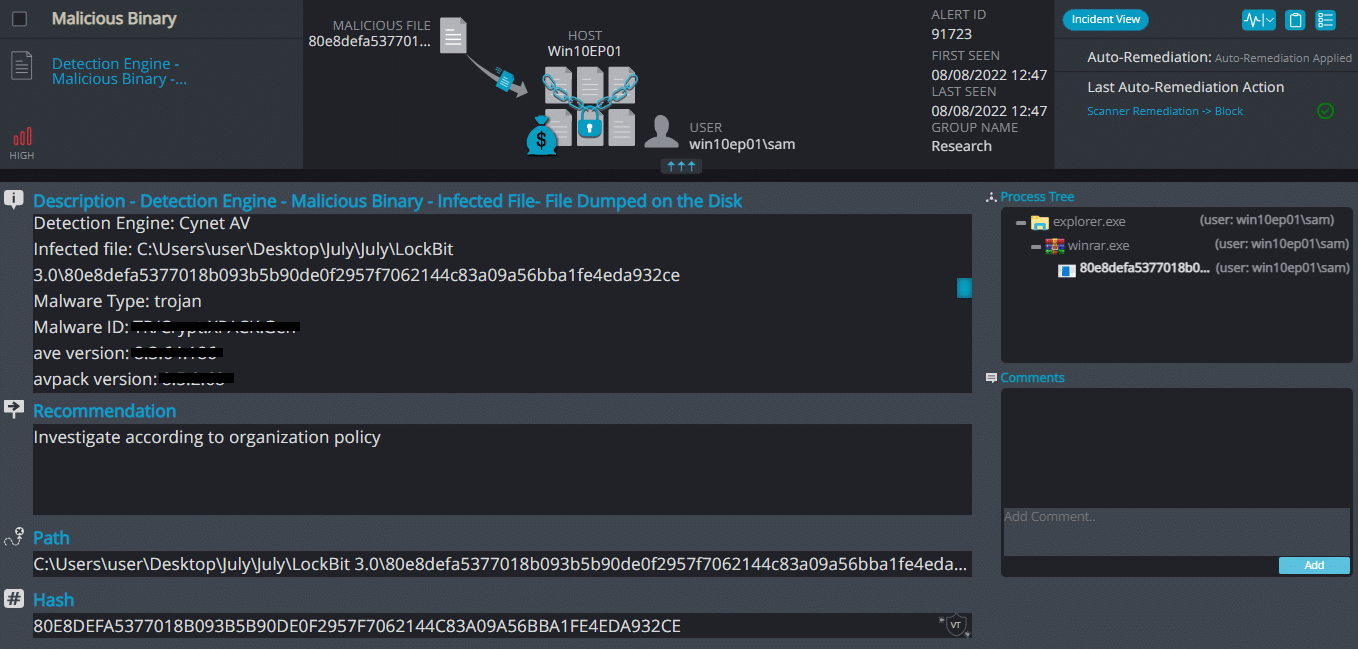
Cynet 360 AutoXDR™ Detections:
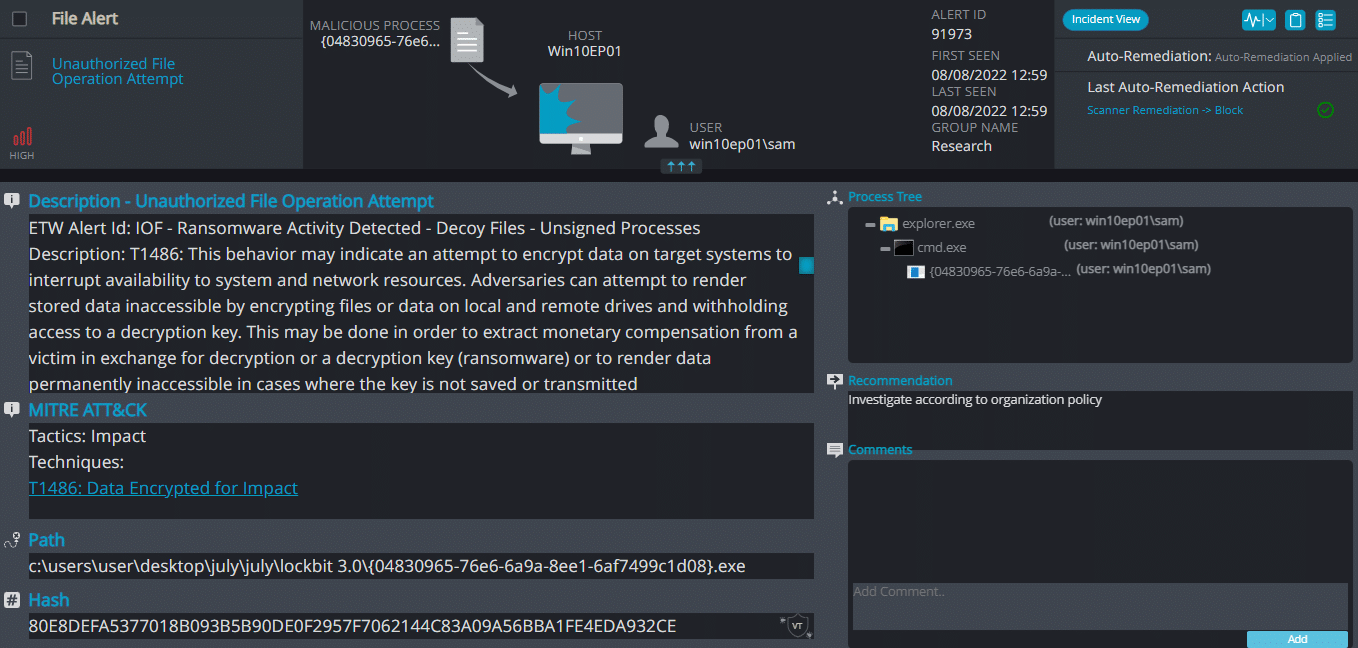
LockBit 3.0 needs to execute by a specific method for it to work,
The executable needs to be renamed to “{04830965-76E6-6A9A-8EE1-6AF7499C1D08}.exe” and needs to be executed with the following parameters:
“-k LocalServiceNetworkRestricted -pass db66023ab2abcb9957fb01ed50cdfa6a” via CMD or PowerShell:
LockBit 3.0 ransomware renames the encrypted files with .(9 characters) in the extension:
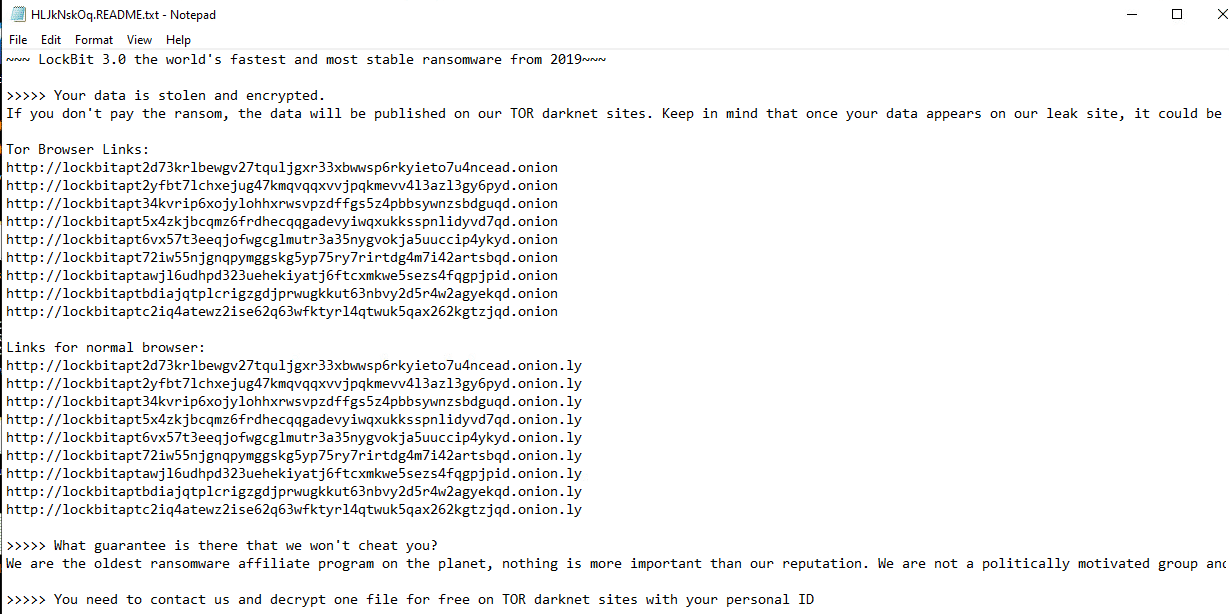
Once a computer’s files have been encrypted and renamed, it drops a note as (9 characters).readme.txt:
Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains general information, warnings, and several attacker’s links:
Matrix Ransomware
- Observed since: Late 2016
- Ransomware encryption method: AES + RSA
- Ransomware extension: .KOK08
- Ransomware note: !README_KOK08!.rtf
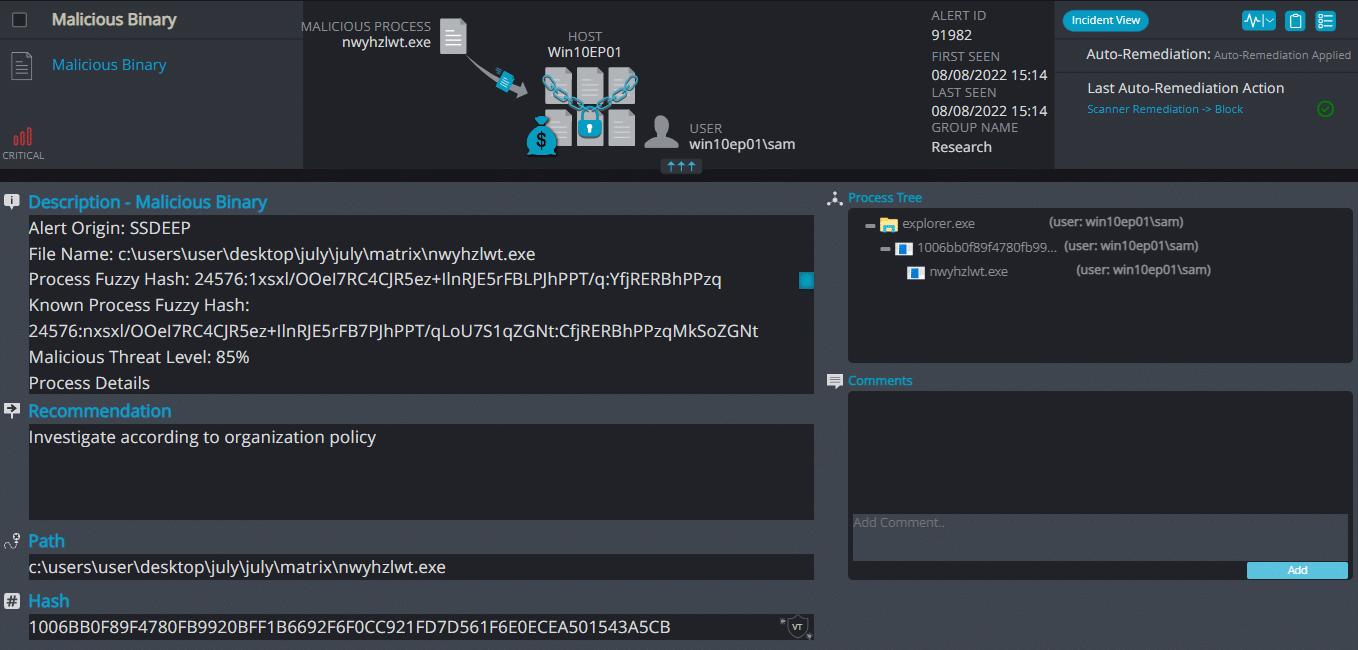
- Sample hash: 1006bb0f89f4780fb9920bff1b6692f6f0cc921fd7d561f6e0ecea501543a5cb
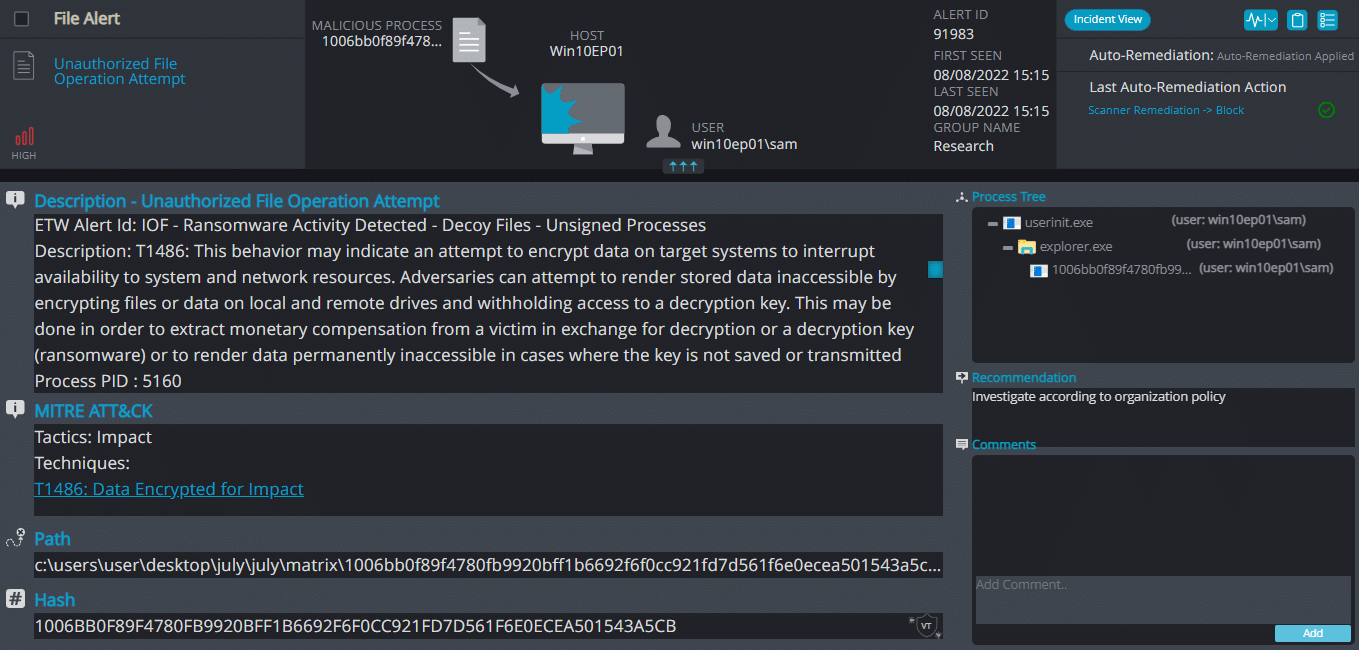
Cynet 360 AutoXDR™ Detections:
Matrix Overview
Matrix ransomware renames the encrypted files with .KOK08 in the extension:
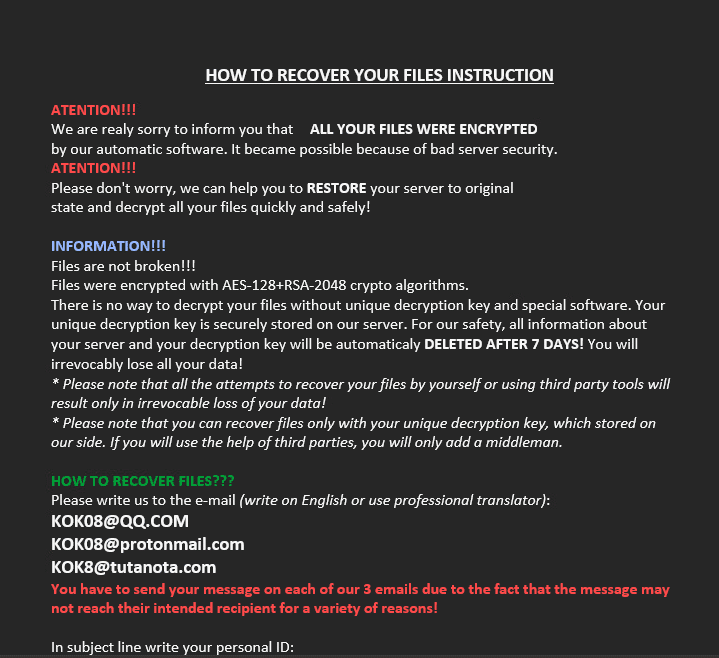
Once a computer’s files have been encrypted and renamed, it drops a note as !README_KOK08!.rtf:
Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains general information, warnings, and the attacker’s emails: