CyOps Important Security Update – ProxyShell
CyOps Important Security Update – ProxyShell
Introduction
A new attack vector named ProxyShell was recently disclosed. ProxyShell is a Microsoft Exchange server vulnerability that provides an attacker with unauthenticated remote code execution (RCE) capabilities.
Microsoft Exchange Server is a mail and calendaring server that runs exclusively on Windows Server operating systems and is used by many organizations worldwide.
Microsoft released security updates for the ProxyShell vulnerabilities in April and May of 2021. However, many organizations still haven’t fully patched their Exchange servers and are still vulnerable to this attack.
Microsoft Exchange Server – The Holy Grail
In the last few months, there has been a trend of threat actors targeting Microsoft Exchange servers. Exchange servers are a critical entry point to an organization’s network – gaining a foothold in this component enables threat actors to easily infiltrate the inner network. Examples of this attack were recently published by Israeli press regarding Chinese cyber-attacks on the Israeli government, banks, and high-tech organizations by exploiting Microsoft Exchange servers. Exchange servers also hold personal and confidential data which can be used in several ways to gain profit.
Enterprises often use on-premises Exchange servers that, if left unpatched, can widen the attack surface. According to Shodan.io, 400,000 on-premise Exchange servers are open to the Internet, increasing the possibility of finding a vulnerable server which may lead to a successful exploit.
One of the most exploited Exchange vulnerabilities is ProxyLogon which was used by the HAFNIUM APT to deploy the China Chopper web shell and steal data from a compromised network. Following its disclosure, the ProxyLogon vulnerability was also used by other malicious threat actors for different purposes such as deploying ransomware and exfiltrating sensitive data.
ProxyShell – The New Old Friend
As part of the 2021 Black-Hat conference, Orange Tsai, a security researcher shared his discovery of the ProxyShell attack vector which is a combination of 3 vulnerabilities chained together to provide the attacker with an unauthenticated remote code execution (RCE). These chained vulnerabilities can be exploited remotely via Microsoft Exchange’s Client Access Service (CAS) which runs on port 443 in Internet Information Services (IIS).
-
- CVE-2021-34473 – Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2021-31207 – Microsoft Exchange Server Security Feature Bypass Vulnerability
- CVE-2021-34523 – Microsoft Exchange Server Elevation of Privilege Vulnerability
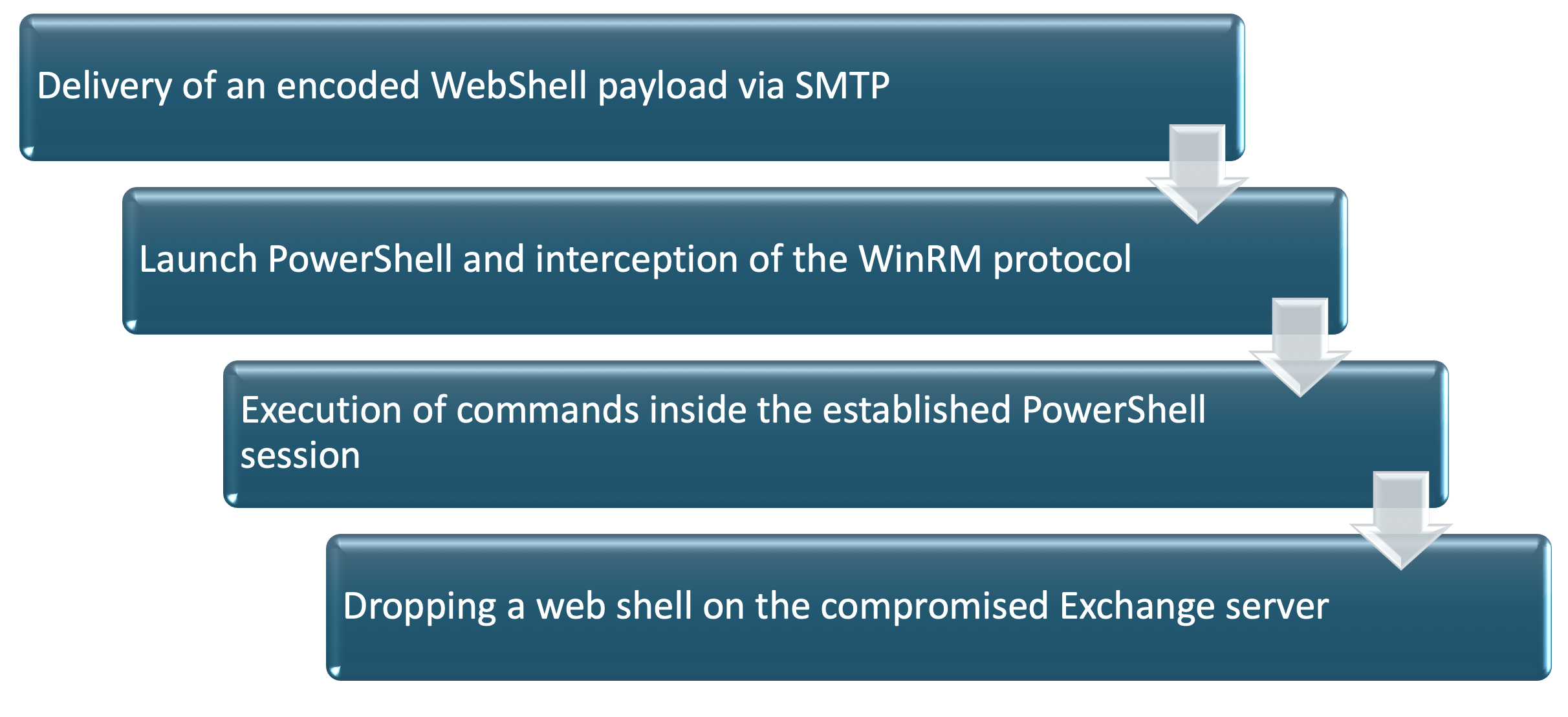
The attack is comprised of the following steps:
Technical analysis of the POC’s can be found in Orange Tsai’s Black-Hat presentation.
Cynet Protection and Recommendations
The Cynet Security Research team has already deployed new rules aimed to detect and prevent exploitation attempts of these vulnerabilities and is currently working on additional detections to increase the visibility around it.
We strongly advise all customers to install the latest security updates on their Exchange servers which can be found here.
The CyOps team monitors our customers’ environments 24/7 and will be in contact in case any indicators of this vulnerability are detected in your environment.
Contact Cynet CyOps
(Cynet Security Operations Center)
Cynet CyOps is available to clients for any issues 24/7, questions or comments related to Cynet 360. For additional information, you may contact us directly at:
CyOps Mailbox – [email protected]
CyOps Team Leader – [email protected]
CyOps Manager – shirang@cynet.com
Israel: +972 72-3369736
UK: +44 2032 909051
US : +1 (347) 474-0048