Securing Your Organization’s Network on a Shoestring
In this blog post, we will discuss how to protect your resource-constrained organization’s endpoints, networks, files and users without going bankrupt or losing sleep.
The Problem
Security is complicated, expensive and time consuming. Worse, nearly 80% of resource-constrained businesses ONLY deploy antivirus and firewalls while hardly spending on other defenses. Meanwhile, the threatscape continues to degenerate: 60% of resource-constrained firms say attacks are becoming more severe and more sophisticated.
High Costs
In 2017, cyber attacks cost small and medium-sized businesses an average of $2,235,000.
Fragile Targets
Fifty-eight percent of malware attack victims are categorized as small to medium businesses.
Attacks Go Undetected
There are 400 new threats per minute and 70% go undetected.
Lack of Response
88% of organizations handle only 25 or less of the critical events they encounter per day.
The Result
To face the evolving threatscape, large enterprises buy, integrate and deploy multiple products to build a defense-in-depth strategy. But most resource-constrained companies can’t afford and aren’t staffed to do the same.
So How Can Resource-Constrained firms Complement Their AV and Firewall Without Breaking the Bank?
Option 1
Purchase another point solution
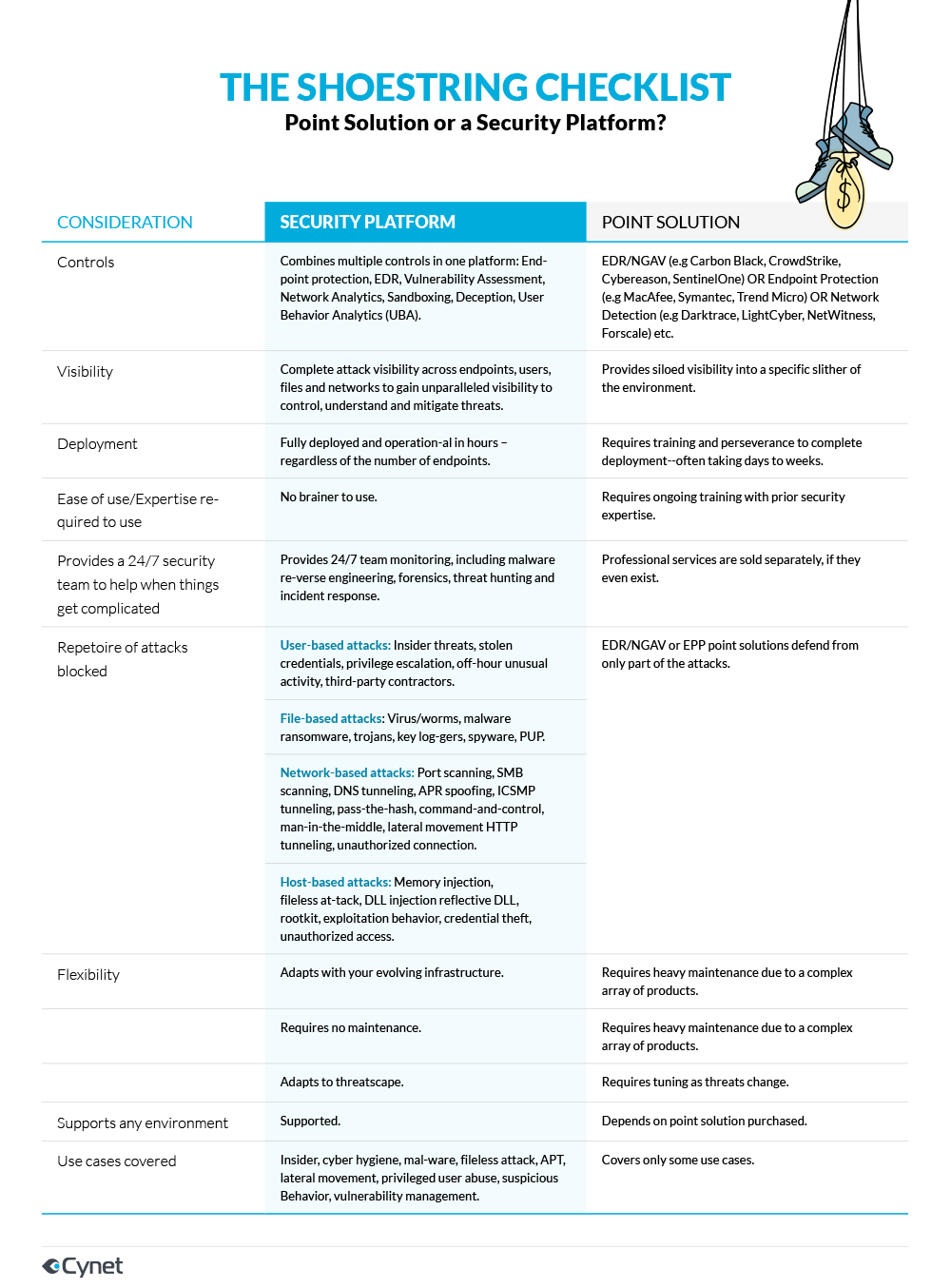
Organizations can choose to deploy one or multiple point solutions on the market to solve a specific problem. This approach, however, is not only very expensive and requires a large team of security analysts but is also not purpose-built to address cyber risk in a holistic way. Existing security point tools flag threats and anomalies but fail to look at the organization as a whole. Today’s attacker takes a multi-pronged approach across network and endpoint—leaving resource constrained firms vulnerable.
Option 2
Complement their AV with a security platform
A true platform understands the high volume of activities that take place each day and correlates them to determine a firm’s intrinsic risk—without integration, deployment and maintenance overhead. Further, a security platform provides a robust suite of security controls, as well a team of security experts on 24/7 standby. This expertise is crucial at most critical moments in the event of a breach as well as to perform forensics or threat hunting.