Self-Audit Guide: Cybersecurity Effectiveness for the Resource-Constrained Organization
A Primer for Moving Beyond AV and Firewalls:
The Problem – As software systems become more distributed and interactive with cloud services tightly woven into organizations’ architecture, defenders are left blind and impotent. Despite the endless parade of new security technologies – sandboxes, next gen firewalls, next generation antivirus, and so on – breaches continue as attackers bypass whatever the industry produces.
The bad guys continue to step-up their game. Just the growth of malware alone tells the story: The AV-TEST Institute registers over 250,000 new malicious programs every day. Eighty-two percent of malware disappears after one hour while just 70% of malware only exists once. It would take over 28-years just to detect the malware generated in a day.
Despite the billions in venture money that has poured into security startups, the majority of new vendors focus on larger enterprises with bigger budgets. Today, big companies with million-dollar cyber budgets assemble a comprehensive cyber defense strategy, including dozens of security solutions to block and mitigate a wide variety of attacks such as phishing, ransomware, DDoS, APT and so on.
But what do you do if you’re resource-constrained, without the benefit of full security staff? Regardless of size, basic disciplines exist that all companies should heed: The Fundamental Five.
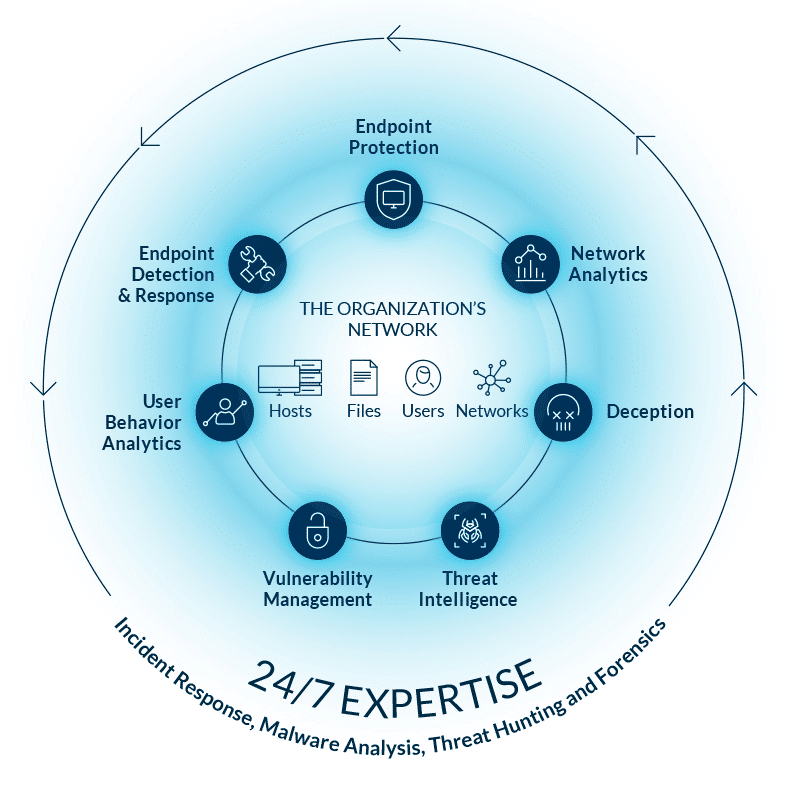
 What is Needed for an Effective Defense?
What is Needed for an Effective Defense?
The Way Forward
Effectively performing the Fundamental Five requires deploying many solutions (firewall, AV, SIEM, EDR, analytics, and more) operated by a security team with deep expertise. But for the resource-constrained organizations, this path is not viable due to high costs with few resources. Surveys show that resource constrained organizations rely mostly on firewalls (76%) and AV (81%)–but little else. Ideally, these organizations should leverage an all-in-one security solution – an integrated platform that combines essential controls and correlates intelligence across them to deliver a robust defense.
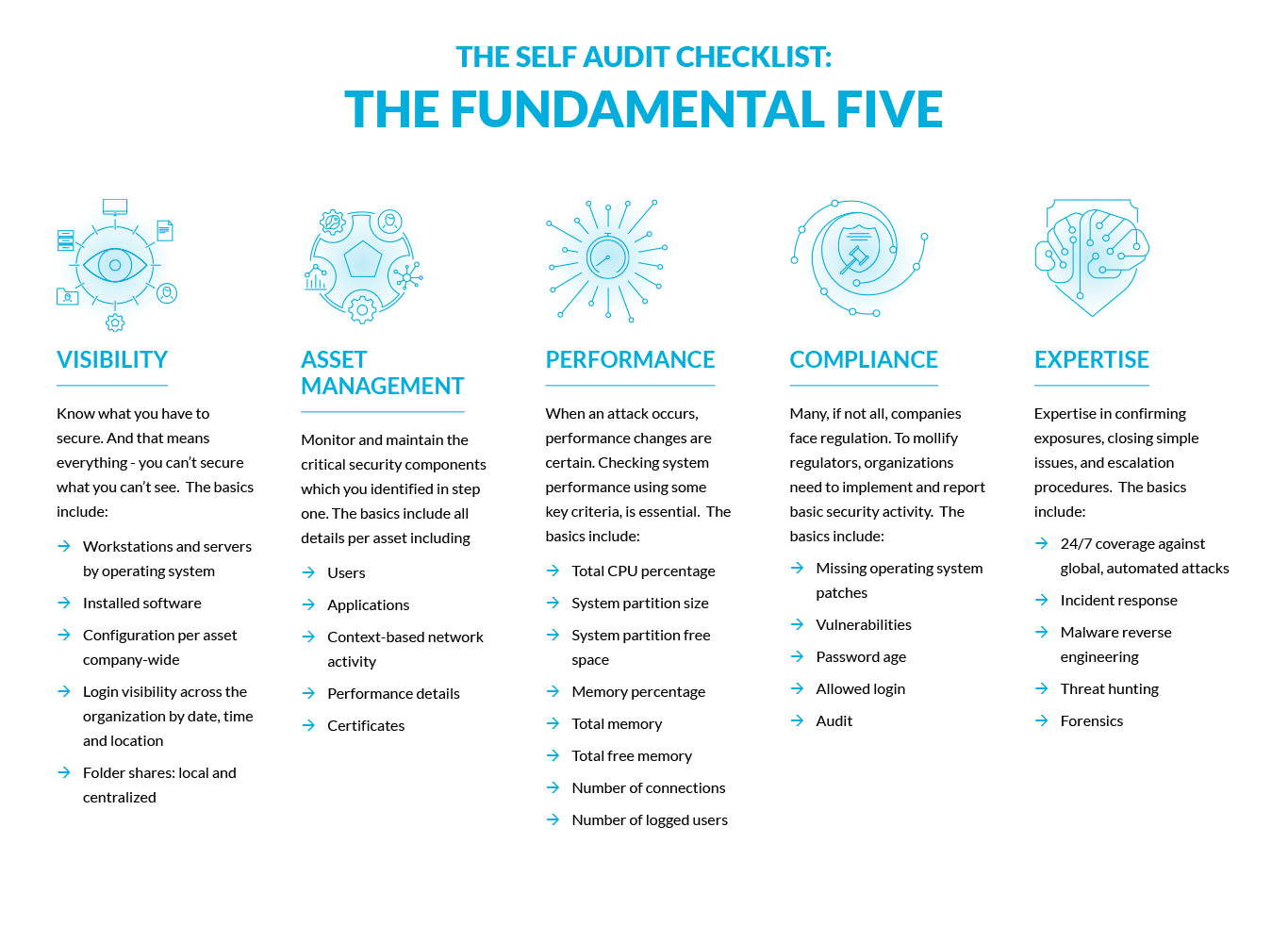 What is Needed for an Effective Defense?
What is Needed for an Effective Defense?