Static Analysis: EARTH GRASS Ransomware
A new ransomware variant named “EARTH GRASS” recently surfaced in the wild. It masquerades as a legitimate Microsoft application to trick users into its execution. When initiated, EARTH GRASS performs actions to ensure that encryption of the host will be complete and uninterrupted, as well as locally irreversible, by deleting and terminating local backup files and services on the host.
A ransom note from the attacker demands payment in crypto currency in exchange for the decryption of files. It is important to note that complying with the threat actor’s demands will not necessarily remedy the situation and may incentivize further similar attacks by the same and/or additional attackers
For more, you can read a dynamic analysis of EARTH GRASS or see how Cynet stops the threat in this step-by-step breakdown.
Through a static analysis of this malware and its strings, we can understand its functionality. Let’s get started!
Static Analysis
The file properties show that the file is masquerading as a legitimate Windows OneDrive executable:
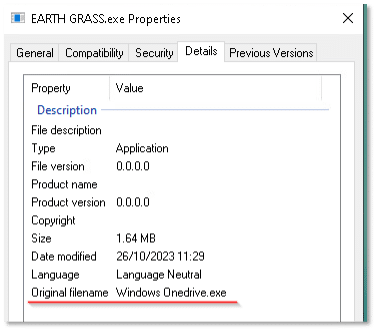
Reviewing the file’s strings uncovers numerous indicators that shed light on several potential capabilities and intentions.
The following strings suggest that the file, once executed, will attempt to delete any available backup images on the host, as well as terminate backup services. This, no doubt, is to cause as much impact as possible:
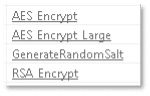
The file may also employ cryptography functions imported from the native Microsoft.NET framework library “mscoree.dll”:
The following strings suggest that the file may attempt to create a registry Run key, most likely to create persistence on the host:
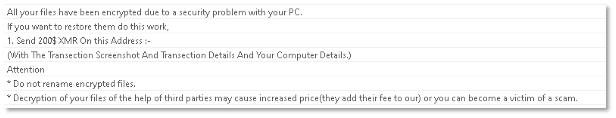
Additional strings appear to be related to a ransom note, as evidenced by the file’s name and apparent contents:
During analysis, a suspicious base64 encoded string was detected:
Decoding the string from base64 reveals what seems to be a .jpg image file code:
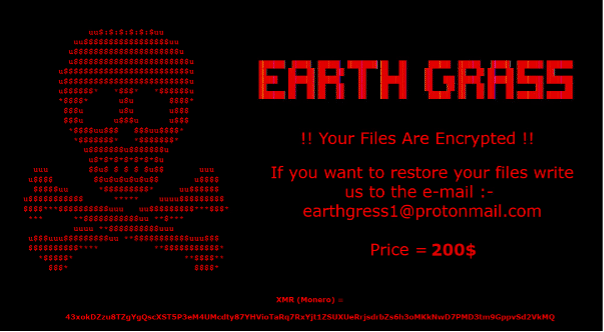
Rendering the file code results in the following image:
This interesting string also suggests the possible creation of executable files: