Microsoft Defender for Endpoint: Architecture, Plans, Pros and Cons
What is Microsoft Defender for Endpoint?
Microsoft offers an enterprise-grade endpoint security platform that detects, investigates, and prevents advanced threats. It helps enterprises respond to threats quickly by employing several technologies built into Microsoft Azure and Windows 10.
Here are the technologies Microsoft Defender for Endpoint leverages to protect corporate environments:
- Endpoint behavioral sensors—collect and process behavioral signals directly from the Windows 10 operating system. These sensors send this information to an isolated and private cloud instance of Microsoft Defender for Endpoint.
- Cloud security analytics—Microsoft employs device learning and big data analytics technologies to translate behavioral signals into detections, insights, and recommended responses to threats.
- Threat intelligence—Microsoft threat hunters and security teams use threat intelligence gathered across the ecosystem and provided by partners to offer insights. Threat intelligence helps Defender for Endpoint identify attacker tactics, techniques, and procedures (TTPs) and generate alerts.
Microsoft Defender for Endpoint Architecture and Components
Microsoft Defender for Endpoint includes multiple layers of protection, continuous monitoring and response capabilities, while integrating with other Microsoft solutions, notably Microsoft Entra (formerly Azure AD). The following diagram illustrates Microsoft Defender for Endpoint architecture and integrations.
Microsoft Defender for Endpoint includes multiple layers of protection, continuous monitoring and response capabilities, while integrating with other Microsoft solutions, notably Microsoft Entra (formerly Azure AD). The following diagram illustrates Microsoft Defender for Endpoint architecture and integrations.
Source: Microsoft
Key concepts in Microsoft Defender for Endpoint:
- Administration portal: The Microsoft Defender portal is the central hub for monitoring and responding to alerts of potential advanced persistent threat (APT) activities or data breaches.
- Attack surface reduction: Helps reduce the attack surface by minimizing vulnerabilities and entry points that attackers can exploit. It includes capabilities like application control, network protection, and exploit protection to safeguard against various cyber threats.
- Endpoint detection and response (EDR): Provides near real-time, actionable insights into advanced attacks. EDR continuously monitors endpoints to detect suspicious activities and potential threats, enabling rapid response to mitigate risks.
- Behavioral blocking and containment: Identifies and stops threats based on their behaviors and process trees, even if the threat has already started executing.
- Automated investigation and response (AIR): Uses algorithms to automatically investigate alerts and take immediate actions to resolve breaches. This automation reduces the workload on security analysts and accelerates the remediation process.
- Advanced threat hunting: A proactive, query-based threat hunting tool that allows security teams to explore up to 30 days of raw data. This tool helps in identifying threat indicators and entities, enabling organizations to uncover and mitigate threats early.
- Threat analytics: Provides reports from Microsoft security researchers on the most relevant threats. These reports offer insights into emerging threats and guidance on how to track and respond to them.
Microsoft Defender for Endpoint uses the following operational workflow:
- Device onboarding: Devices are onboarded through supported management tools such as Microsoft Endpoint Manager (Intune), System Center Configuration Manager (SCCM), Group Policy, or scripts. This ensures that all devices are integrated into the Defender for Endpoint environment, allowing for consistent monitoring and protection.
- Signal data collection and response: Once devices are onboarded, they start providing and responding to signal data from Microsoft Defender for Endpoint. This signal data includes behavioral information from endpoint activities, which is crucial for detecting and analyzing potential threats in real time.
- Identity management with Microsoft Entra ID: Managed devices are joined and enrolled in Microsoft Entra ID (formerly known as Azure Active Directory). This integration facilitates unified identity management, ensuring that security policies and access controls are consistently applied across all devices.
- Synchronization of domain-joined devices: Domain-joined Windows devices are synchronized to Microsoft Entra ID using Microsoft Entra Connect. This synchronization keeps identity and access information up to date.
Management of alerts, investigations, and responses: Microsoft Defender XDR (Extended Detection and Response) manages all alerts, investigations, and responses. This centralized management platform provides a unified view of security incidents, enabling security teams to investigate and respond to threats. It also enables the integration and sharing of signals across various Microsoft security services.
Microsoft Defender for Endpoint Plan 1 and Plan 2
Microsoft Defender for Endpoint is available in two plans:
Defender for Endpoint Plan 1 Features
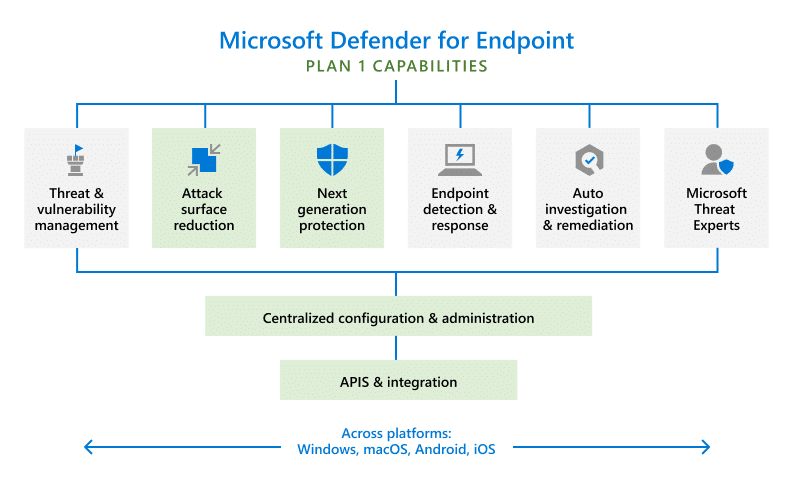
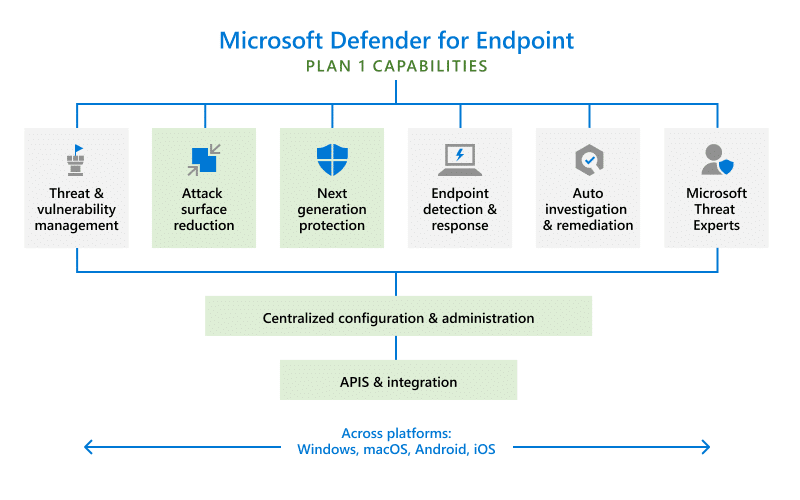
In the image below, the green boxes represent features of Defender for Endpoint Plan 1.
Image Source: Microsoft
Here are the capabilities provided by Defender for Endpoint Plan 1:
- Next-generation protection—provides antimalware and antivirus protection.
- Manual response actions—enables security professionals and teams to take specific actions. For example, they can send a file to quarantine when Defender detects threats.
- Attack surface reduction—for detecting zero-day attacks and hardening devices. It also provides granular access control for your endpoints.
- Centralized management and configuration—enables you to use the Microsoft 365 Defender portal and integration with the Microsoft Endpoint Manager.
- Protection for other platforms—helps you protect Windows, iOS, macOS, and Android devices.
Microsoft Defender for Endpoint (Plan 2) Features
Microsoft Defender for Endpoint (Plan 2) was previously called Defender for Endpoint.
Threat and Vulnerability Management
Here are threat vulnerability management capabilities offered by Plan 2:
- Identifies misconfigurations and vulnerabilities in real-time with sensors, with no need for periodic scans or agents deployed on endpoints.
- Prioritizes vulnerabilities in keeping with the threat landscape, sensitive data on vulnerable devices, detections within your organization, and enterprise context.
- Provides real-time protection.
- Fully cloud-based platform.
- Integrates with the Microsoft Intelligent Security Graph and application analytics knowledge base.
Related content: Read our guide to cloud endpoint protection.
Attack Surface Reduction
Attack surfaces include places where your organization is vulnerable to attacks and cyber threats. Defender for Endpoint can reduce attack surfaces on endpoints. These capabilities also include web and network protection, which regulate access to malicious domains, URLs, and IP addresses.
Next-Generation Protection
Next-generation protection refers to anti-malware capabilities that go beyond legacy antivirus, which was based on signature-based threat detection. Here are key next-generation protection features in Plan 2:
- Behavior-based, real-time, heuristic antivirus protection, including continuous scanning based on file and process behavior monitoring.
- Detects and blocks “unsafe applications”, which can cause damage to a system even if they are not strictly defined as malware.
- Provides cloud-delivered protection, including identification and blocking emerging and unknown threats.
Endpoint Detection and Response
Plan 2 provides full EDR features that facilitate rapid detection and response. This enables security analysts to prioritize alerts, achieve visibility into the entire scope of a breach, and respond to threats directly on the endpoint.
Based on the mindset of assuming a breach, this system collects behavioral cyber telemetry continuously. This information includes network activities, process information, deep optics into the memory manager and kernel, registry and file system modifications, user login activities, and more.
The EDR workflow is as follows:
- When a threat is identified, the system creates alerts, prompting the analyst to investigate.
- The system aggregates alerts attributed to the same attacker or the same attack techniques into an incident entity.
- Once the system has aggregated alerts in this way, analysts can collectively investigate and mitigate threats across multiple endpoints.
Data exploration and threat hunting
The system stores security incident data for six months, permitting an analyst to go back to the point in time when the attack occurred. The analysts may then pivot using different filters and views. This makes it possible to investigate and remediate threats by directly acting on the endpoints affected by an attack.
Automated Investigation and Remediation (AIR)
Here are key capabilities of Plan 2 automated investigation and remediation:
- Examines, alerts, and acts quickly to remedy breaches.
- Reduces the volume of alerts, permitting security operations to attend to more complex threats and high-value tasks.
- Provides an action center that tracks all remediation actions, including pending and completed actions, with the ability to approve, reject, or undo completed actions.
Microsoft Secure Score for Devices
Plan 2 includes a feature that dynamically analyzes the security status of an enterprise network. It discovers unprotected systems and undertakes appropriate actions to advance an organization’s security.
This score is visible on the threat and vulnerability management dashboard of the Microsoft 365 Defender portal. A higher score indicates that endpoints are more secure against cybersecurity threat attacks.
Here are the categories used to show the overall security configuration state of devices on the network:
- Applications
- Operating system
- Network
- Accounts
- Security controls
Microsoft Threat Experts
Microsoft Threat Expert provides Security Operation Centers (SOCs) with specialist-level analysis and monitoring. This managed threat hunting service helps your SOCs ensure that organizations do not overlook critical threats in their environments.
The Threat Experts service provides specialist-driven insights and data through access to specialists when needed, and targeted attack notifications to in-house security experts.
Microsoft Defender for Endpoint Best Practices
Here are some best practices to make the most of Defender for Endpoint.
Run Simulated Attacks on Devices
Simulated attacks help validate the effectiveness of your security configurations and prepares your team to respond to real-world threats. Use tools like Microsoft Attack Simulator or third-party solutions to create realistic attack scenarios.
These simulations can range from phishing attacks to more sophisticated threats, allowing your security team to practice detecting and responding to incidents. Regular simulations ensure that your defenses are up-to-date and your team is ready to handle actual security breaches.
Create Notification Rules for Onboarding and Offboarding
These notification rules help maintain visibility and control over your network. Configure alerts in the Microsoft 365 Defender portal to notify administrators when devices are added or removed. This practice ensures that every device is properly monitored and protected from the moment it joins the network.
Offboarding notifications are equally important to confirm that devices no longer in use are appropriately disconnected, reducing the risk of unauthorized access or data breaches.
Manage Endpoint Security Policies with Microsoft Intune
Microsoft Intune allows centralized management of endpoint security policies, providing protection across all devices. Set up policies for device compliance, app protection, and conditional access to enforce security standards.
Regularly review and update these policies to adapt to evolving threats and organizational needs. Intune integration with Defender for Endpoint enables seamless policy enforcement and monitoring, ensuring that security measures are consistently applied.
Integrate with Microsoft Defender for Cloud
Integrating Defender for Endpoint with Microsoft Defender for Cloud extends protection to your cloud resources. This integration provides unified security management and advanced threat protection across hybrid environments.
By leveraging Defender for Cloud, you gain visibility into security posture, identify vulnerabilities, and receive actionable recommendations to strengthen your defenses. The combined capabilities of endpoint and cloud protection ensure a cohesive security strategy for on-premises and cloud assets.
Microsoft Defender for Endpoint Pros and Cons
Here are some of the key strengths and weaknesses of the Microsoft Defender for Endpoint solution.
Pros of Microsoft Defender of Endpoint
- Basic edition comes free with all Windows endpoints.
- Broad endpoint compatibility – including Windows 10, Windows Server, Linux, macOS, iOS, and Android.
- Mapped against MITRE ATT&CK knowledge base, able to detect indicators of compromise (IoC) based or MITRE definitions.
- Leverages data from billions of signals gathered from Office 365 applications.
Cons of Microsoft Defender of Endpoint
- Web filtering only supported on Windows
- On Linux, the endpoint agent has a relatively high memory footprint
- Anti malware protection is not highly customizable
- Some users have deployment challenges outside Windows environments. In particular, older macOS systems require multiple steps to deploy MDE.
Endpoint Protection - Prevention, Detection and Protection with Cynet
Cynet is a security solution that includes a complete Endpoint Protection Platform (EPP), with built-in EDR security, a Next-Generation Antivirus (NGAV) , and automated incident response. Cynet makes it easier to adopt a modern security toolset by offering an “all in one” security model: Cynet 360 goes beyond endpoint protection, offering network analytics , UEBA and deception technology.
Cynet’s platform includes:
- NGAV—blocks malware, exploits, LOLBins, Macros, malicious scripts, and other known and unknown malicious payloads.
- Zero-day protection—uses User and Entity Behavior Analytics (UEBA) to detect suspicious activity and block unknown threats.
- Monitoring and control—asset management, endpoint vulnerability assessments and application control, with auditing, logging and monitoring.
- Response orchestration—automated playbooks and remote manual action for remediating endpoints, networks and user accounts affected by an attack.
- Deception technology—lures attackers to a supposedly vulnerable honeypot, mitigating damage and gathering useful intelligence about attack techniques.
- Network analytics—identifying lateral movement, suspicious connections and unusual logins.
Learn more about Cynet’s All-in-One cybersecurity platform.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response