Elastic SIEM: Features, Components, Pricing, and Quick UI Guide
What Is Elastic Security SIEM?
Elastic Security SIEM (Security Information and Event Management) is a product built on top of the Elastic Stack, which provides security insights and real-time threat detection. As a modern SIEM solution, it collects, normalizes, and analyzes data from various sources within an organization’s IT environment, such as logs, network traffic, and endpoint data.
The primary function of Elastic Security SIEM is to offer a centralized platform for monitoring and managing security events. It enhances an organization’s ability to detect unusual or potentially malicious activity quickly. Elastic SIEM provides advanced correlation techniques and machine learning algorithms that assess risk levels, spot anomalies, and prioritize alerts based on their potential security impact.
Technically, Elastic SIEM uses Beats, Elastic Endpoint and Logstash to integrate with data from the IT environment, Elasticsearch for data processing and indexing, while Kibana forms the basis of the Elastic SIEM application. Alongside these components, Elastic and its open source community provides “security content” in the form of security rules, attack patterns, and more.
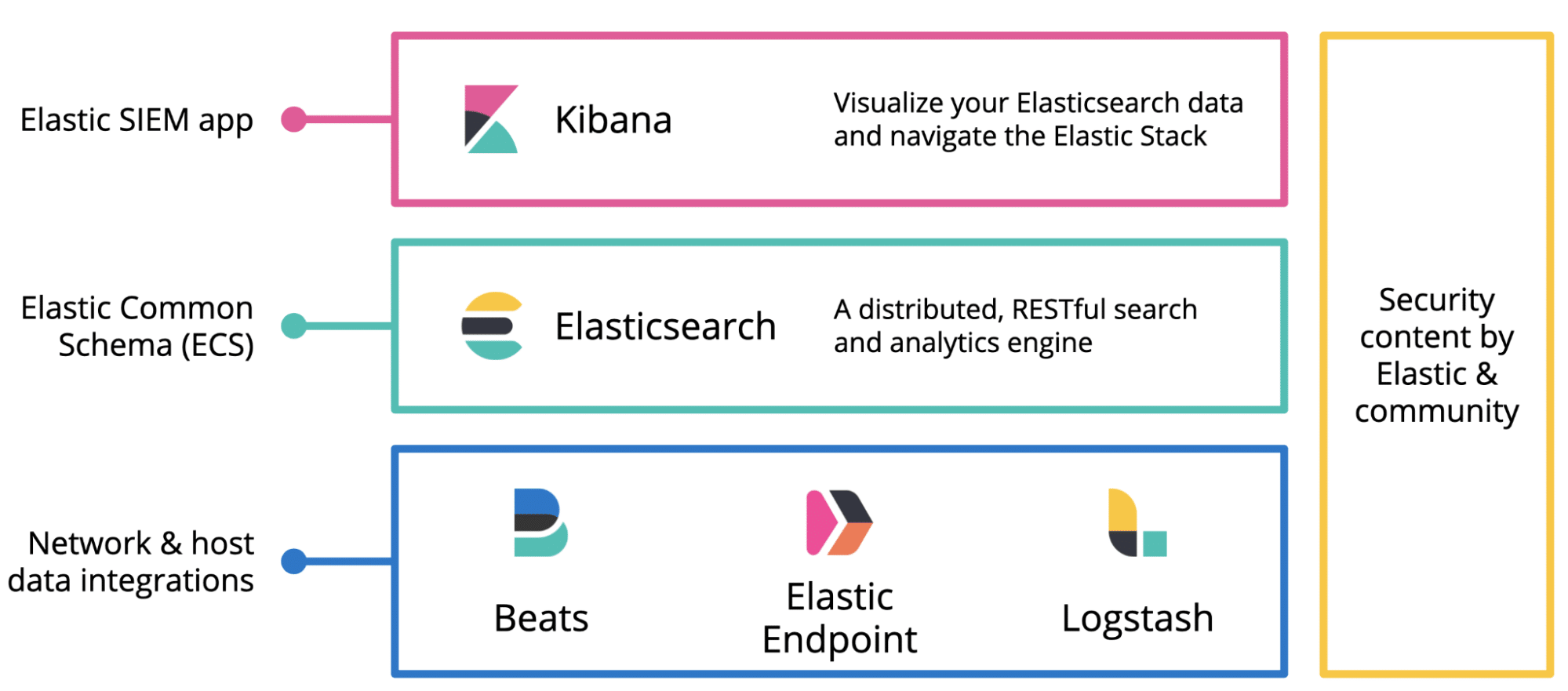
Source: Elastic
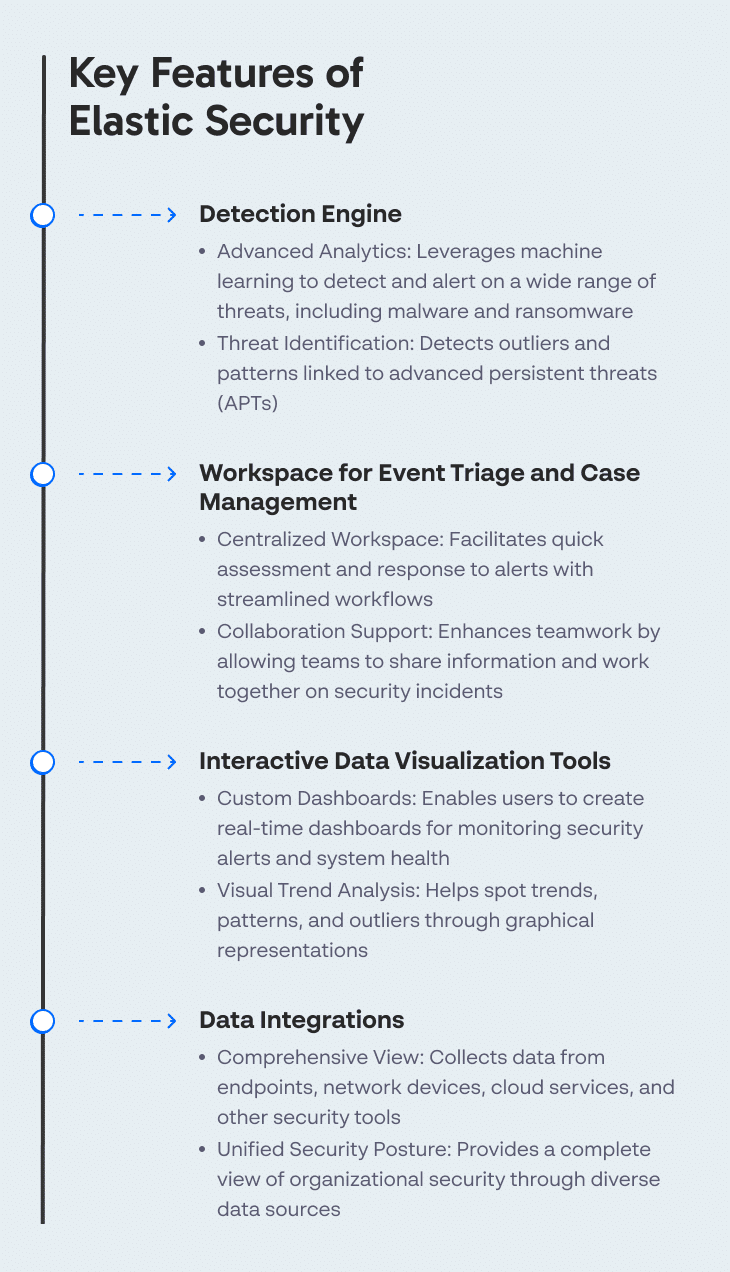
Key Features of Elastic Security
Elastic Security SIEM offers the following features:
- Detection engine: Identifies a wide range of threats, leveraging advanced analytics and machine learning to detect and alert on threats across an organization’s digital infrastructure. It also covers malware and ransomware, detecting outliers and patterns indicative of advanced persistent threats
- Workspace for event triage, investigation, and case management: Provides a centralized workspace that allows teams to quickly assess and respond to alerts, streamlining the steps from detection to resolution. The workspace supports collaboration, making it easier for teams to share information and work together on security issues.
- Interactive data visualization tools: Allows users to sift through security data, enabling the construction of custom dashboards that can display real-time data on security alerts and system health. Visual representations help in spotting trends, outliers, and patterns that might be missed in raw textual data logs.
- Integrations for collecting data from different sources: It can collect data from endpoints, network devices, cloud services, and other security tools, creating a comprehensive view of an organization’s security posture.
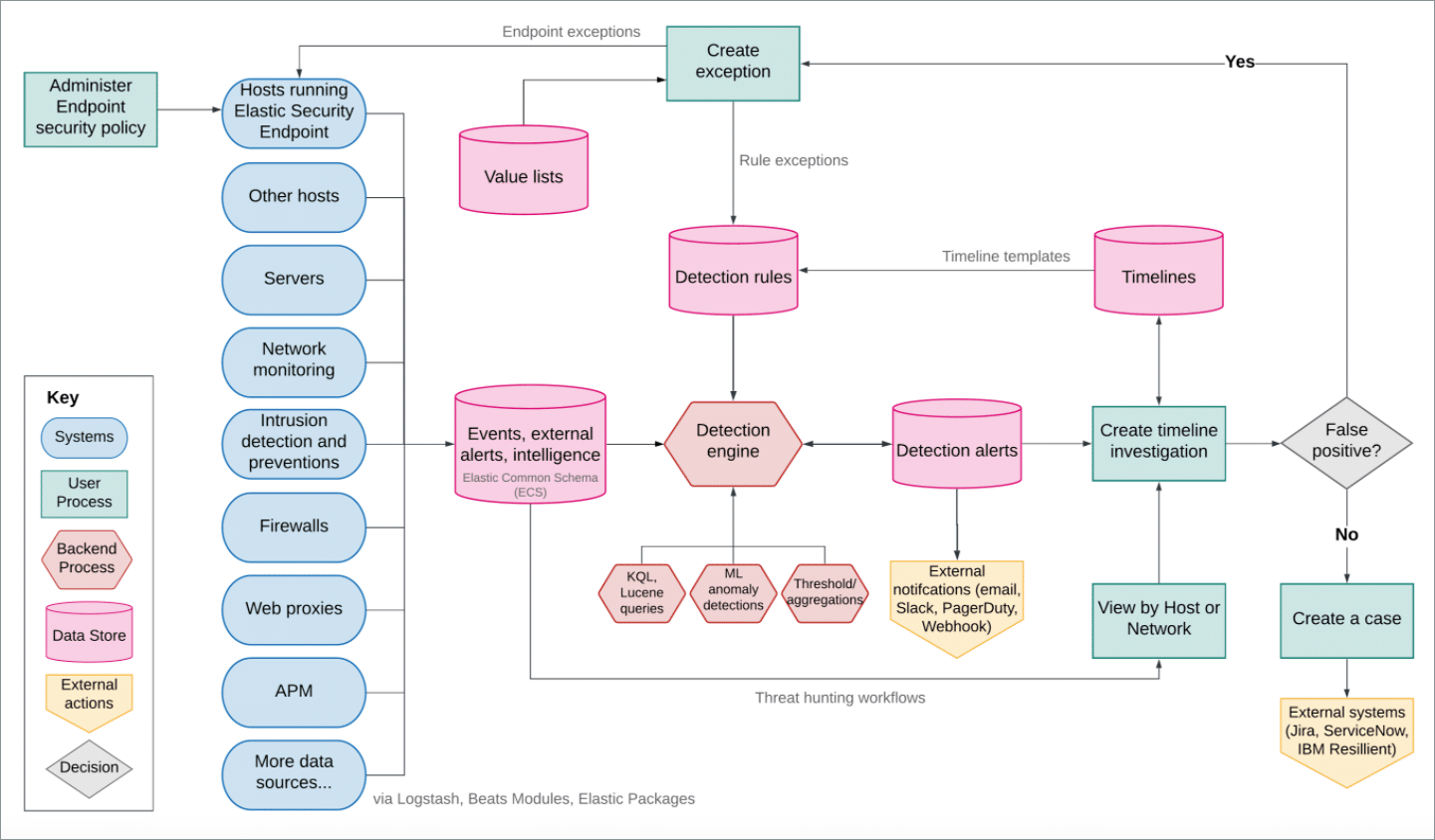
Elastic Security Components and Workflow
The workflow of Elastic Security is a well-defined process that manages and monitors security data across an organization’s digital environment. The system integrates data shipped from various hosts to Elasticsearch. This data transfer is facilitated by beat modules and the Elastic Endpoint Security agent.
Source:Elastic
Tips From Expert
In my experience, here are tips that can help you better maximize Elastic Security SIEM:
- Leverage unsupervised machine learning for zero-day attacks
Elastic’s machine learning models are powerful, but consider using unsupervised learning for anomaly detection when faced with unknown or novel threats. It can uncover patterns that traditional rule-based approaches might miss. - Regularly fine-tune alert thresholds
Don’t rely on default alert thresholds. Review the alerting patterns periodically, and adjust thresholds based on evolving threat landscapes and your environment’s typical activity levels to avoid alert fatigue or missed detections. - Integrate threat intelligence feeds
Beyond Elastic’s own threat intelligence, integrate third-party feeds to enhance detection capabilities. Use enrichment to associate events with indicators of compromise (IoCs) from trusted sources to increase contextual awareness. - Adopt a multi-tiered incident response strategy
Take advantage of Elastic’s case management and streamline the incident response process by creating layered playbooks for different severity levels. Automating certain responses for low-severity events will help prioritize more critical cases. - Visualize attack pathways with MITRE ATT&CK mappings
Use the MITRE ATT&CK framework built into Elastic SIEM to visualize attack chains across your environment. Map incidents to specific ATT&CK techniques, which can help identify not only what happened but potential next steps in an adversary’s strategy.
Data Collection and Integration
The Elastic Endpoint Security agent plays a crucial role in this architecture. It is primarily responsible for collecting a variety of events from the host systems, which include process, network, and file data. For Windows environments, it also captures DNS, registry, DLL and driver loads, and malware security detections. In Linux and macOS systems, the focus remains on process, network, and file activities.
Beat Modules
These are lightweight data shippers designed to collect and parse specific data sets efficiently. Beat modules are capable of handling data from common sources such as cloud services, operating system events, logs, and metrics. Their design ensures minimal overhead while maximizing the efficiency of data transmission and analysis.
Fleet Management
The Fleet app is used to install, manage, and oversee agents and their integrations on hosts. It simplifies the administration of security measures, ensuring that all components are updated and functioning correctly.
Elastic Security SIEM Pricing
Elastic Security SIEM provides a structured pricing model tailored to various organizational needs, focusing primarily on enhancing security features at each tier.
The prices below are starting prices, based on a cloud production configuration with 120 GB storage and 2 zones. Actual pricing is usage-based and depends on cloud instance type selected. For up-to-date pricing and more details refer to the official pricing page.
Standard Plan
Starting from $95 per month, the Standard plan serves as the foundational tier. It includes essential security features such as malware prevention and host data collection, centralized management of ingest agents, and basic alerting on security incidents within the Elastic Stack. This tier is suitable for organizations that are establishing their security operations.
Gold Plan
The Gold plan, starting from $109 per month, builds on the Standard tier by adding more sophisticated security capabilities. It includes reporting features, third-party alerting actions, and multi-stack monitoring, which allows for a broader overview of security events. Optimized workflows for incident response are also introduced at this level, enhancing the organization’s ability to manage and respond to security alerts more efficiently.
Platinum Plan
Starting from $125 per month, the Platinum plan extends the Gold offerings by incorporating advanced security features such as machine learning for anomaly detection. This tier enhances threat detection capabilities by using supervised learning to identify unusual patterns and potential threats. Additional security measures include enhanced Elastic Stack security features and cross-cluster replication, aimed at organizations requiring deeper insights and higher data redundancy.
Enterprise Plan
The top-tier Enterprise plan, starting from $175 per month, includes all the features of the Platinum plan with the addition of capabilities tailored for large-scale security needs. It offers searchable snapshots for secure, long-term data retention and supports the Elastic Maps Server for advanced data visualization. This plan is suitable for large enterprises or organizations with complex security requirements, offering extensive security monitoring and analytics capabilities to manage and mitigate potential security threats effectively.
Working with Elastic SIEM Application
Here’s an overview of how to use the Elastic SIEM application (also known as Elastic Security).
Search
The Elastic SIEM app provides a search functionality to manage alerts, events, and other crucial security data. Users can utilize the Kibana Query Language (KQL) by entering queries in the search bar prominently located at the top of every page within the app. This search feature is complemented by a default date/time filter set to “Today,” which can be adjusted to any desired time range according to the user’s needs.
To refine search results, there is an option to add a filter. Users can click on Add Filter, then specify the field, operator (e.g., “is not” or “is between”), and value. Additionally, to aid in recurring searches, there is an option to save the current KQL query and any applied filters by selecting Save saved query from the Saved query menu, then entering a name for this query before saving it.
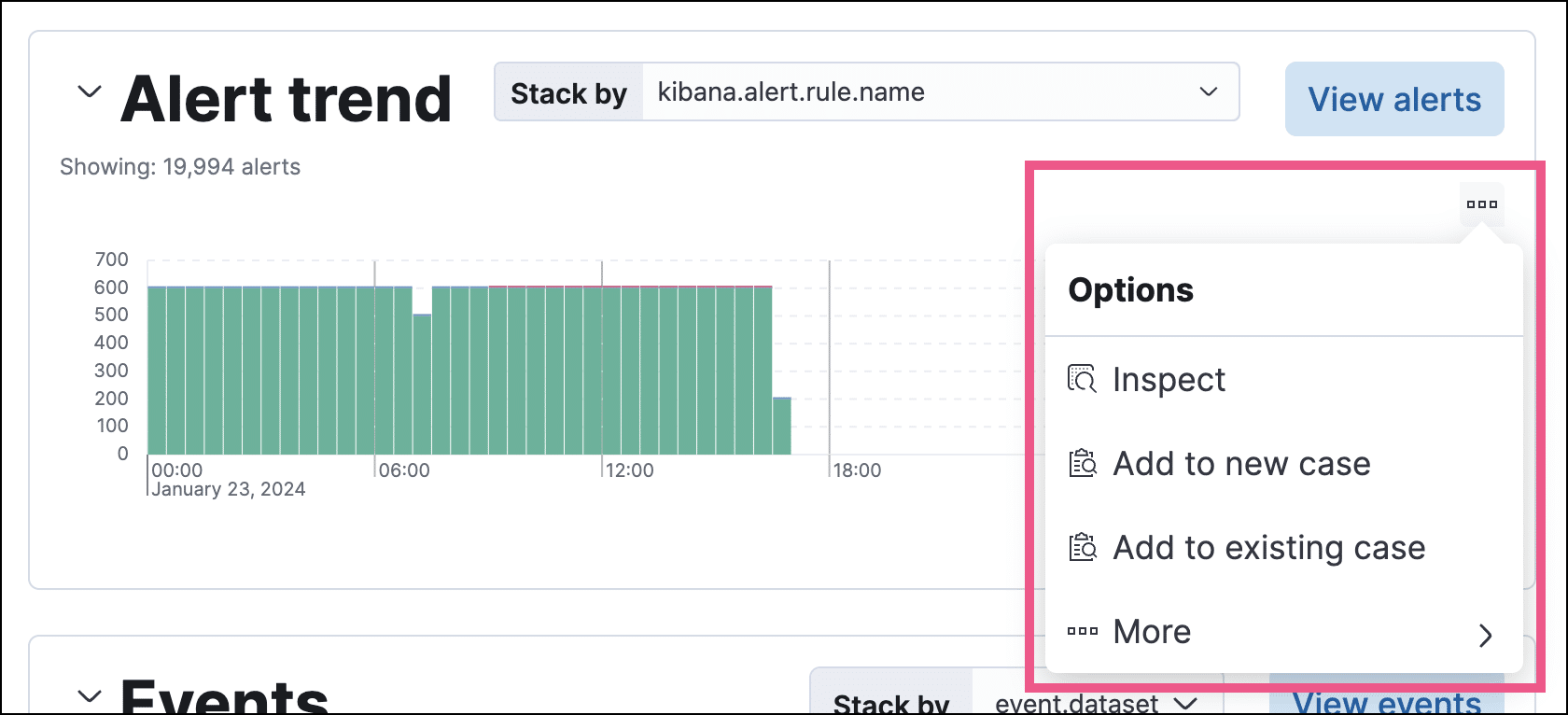
Visualization
Visualization within the Elastic SIEM app includes interactive histograms, graphs, and tables that often have a hovering Inspect button. This feature enables users to view the Elasticsearch queries used to retrieve data across the app. Other visualizations offer a three-dot menu icon which provides further actions like inspecting the visualization’s queries, adding it to a new or existing case, or opening it in Lens for customization.
Source: Elastic
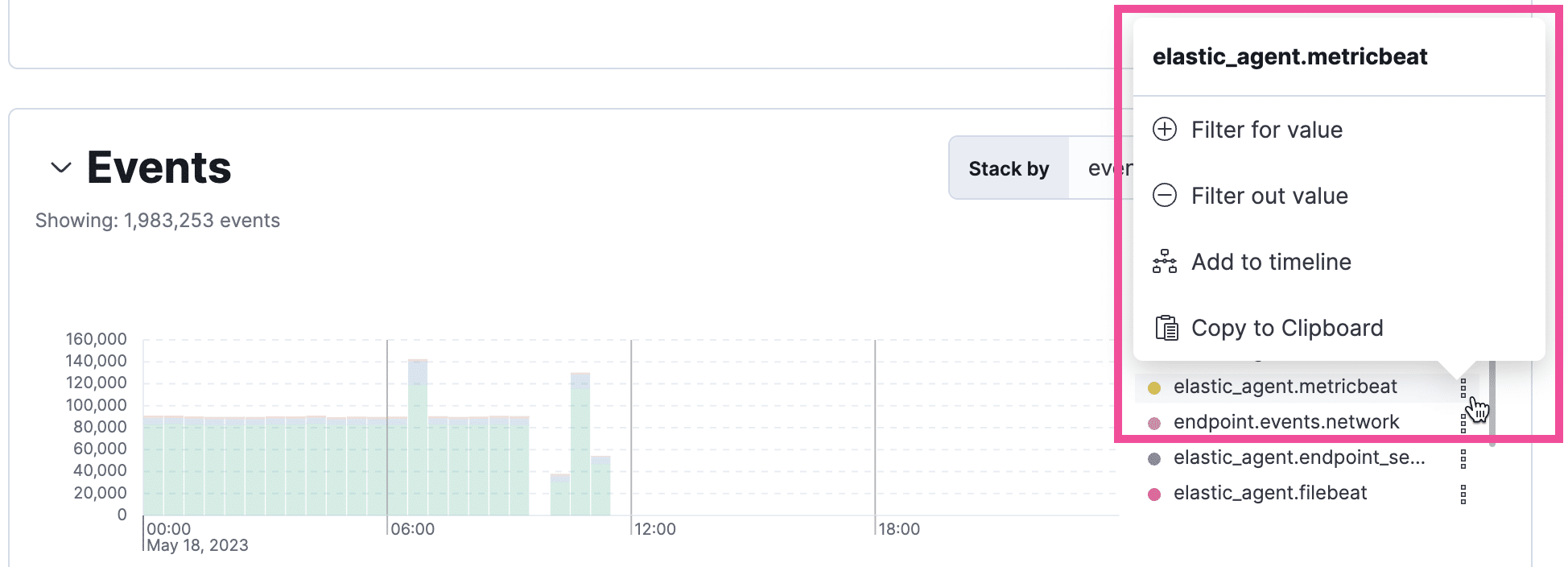
Inline Actions for Data Fields and Values
The app has many data fields and values that display inline actions when hovered over, allowing users to tailor their view or delve deeper based on the selected field or value. These actions include adding filters to include or exclude values, adding filters to the timeline, toggling columns in tables, and more. Some visualizations also allow these actions directly from the legend by clicking the options icon next to a value.
Source: Elastic
Other Pages in the Elastic SIEM App
The Elastic SIEM app includes several other pages with security capabilities, including:
- Dashboards
- Rules
- Benchmarks
- Shared Exception Lists
- MITRE ATT&CK® coverage
- Alerts
- Findings
- Cases
- Timelines
- Intelligence
- Explore
These sections are accessible through an organized and interactive interface that supports security analysts in efficiently managing and responding to security incidents.
Security Automation with Cynet
Cynet provides the world’s first Autonomous Breach Protection platform that natively integrates endpoint, network and user attack prevention/detection of XDR with log management and analysis of CLM and automated investigation and remediation capabilities of SOAR, backed by a 24/7 world-class MDR service.
End to end, fully automated breach protection is now within reach of any organization, regardless of security team size and skill level. Most smaller businesses find that Centralized Log Management (CLM) is fully sufficient for their needs while far more affordable and usable than SIEM solutions.
XDR Layer: End-to-End Prevention & Detection
- Endpoint protection—multilayered protection against malware, ransomware, exploits and fileless attacks.
- Network protection—protecting against scanning attacks, MITM, lateral movement and data exfiltration.
- User protection—preset behavior rules coupled with dynamic behavior profiling to detect malicious anomalies.
- Deception—wide array of network, user, file decoys to lure advanced attackers into revealing their hidden presence.
CLM Layer: Log Management and Analysis
- Ingest log data—collect all pertinent log data to uncover threats across your environment
- Data visualization—advanced, targeted data queries pinpoint precursors to cyberattacks and perform forensic analysis
- Threat hunting—uncover evidence of compromised endpoints, systems, and data such as anomalous privileged account activity and anomalous outbound traffic
- Regulatory compliance—generate reports for FISMA, GLBA, HIPAA, SOX, and PCI DSS, for example, that regulatory bodies require.
SOAR Layer: Response Automation
- Investigation—automated root cause and impact analysis.
- Findings—actionable conclusions on the attack’s origin and its affected entities.
- Remediation—elimination of malicious presence, activity and infrastructure across user, network and endpoint attacks.
- Visualization—intuitive flow layout of the attack and the automated response flow.
MDR Layer: Expert Monitoring and Oversight
- Alert monitoring—First line of defense against incoming alerts, prioritizing and notifying customers on critical events.
- Attack investigation—Detailed analysis reports on the attacks that targeted the customer.
- Proactive threat hunting—Search for malicious artifacts and IoC within the customer’s environment.
- Incident response guidance—Remote assistance in isolation and removal of malicious infrastructure, presence and activity.
Simple Deployment
Cynet can be deployed across thousands of endpoints in less than two hours. It can be immediately used to uncover advanced threats and then perform automatic or manual remediation, disrupt malicious activity and minimize damage caused by attacks.
Get a free trial of Cynet and experience the world’s only integrated XDR, CLM, SOAR and MDR solution.
Related Posts
Looking for a powerful, cost effective XDR solution?
- Full-Featured XDR, EDR, and NGAV
- Anti-Ransomware & Threat Hunting
- 24×7 Managed Detection and Response